
Phishing Links in Browsers: Identifying Red Flags and Staying Safe
According to the FBI’s Internet Crime Report, scams resulted in over $12 billion in losses in 2023 alone, demonstrating how this digital threat continues to evolve and challenge organizations. Modern phishing attacks have become remarkably sophisticated, employing advanced social engineering tactics and nearly perfect replicas of legitimate websites that can deceive even experienced professionals.
As cyber criminals refine their techniques, they increasingly exploit web browsers to execute their schemes. These attacks now utilize complex methods like homograph attacks, where seemingly identical URLs contain hidden character substitutions, and sophisticated domain spoofing that can bypass traditional security measures. The days of obvious spelling errors and suspicious sender addresses are behind us; today’s threats require a far more nuanced approach to detection.
This reality makes browser-based security awareness more critical than ever. While email filters and corporate firewalls provide essential protection, the final line of defense often comes down to individual users recognizing subtle warning signs within their browsers. Understanding these indicators isn’t just about protecting personal information—it’s about safeguarding entire organizations from data breaches, financial fraud, and reputational damage that often begin with a single clicked link.

A fisherman collecting credit cards, Generated by ImageFx
The Evolution of Phishing Tactics
The landscape of phishing attacks has undergone a dramatic transformation over the past decade. While early phishing attempts relied primarily on mass-distributed emails with obvious grammatical errors and suspicious attachments, modern attacks demonstrate a level of sophistication that can deceive even security professionals.
Today’s threat actors have moved beyond creating standalone fraudulent websites, instead exploiting trusted domains through subtle but effective techniques. By compromising legitimate subdomains or leveraging URL shorteners from reputable services, attackers can bypass traditional security measures that rely on domain reputation. This exploitation of trusted infrastructure presents a significant challenge for both users and security tools, as the traditional indicators of suspicious activity become increasingly difficult to detect.
The technical sophistication of these attacks is further enhanced by the use of legitimate SSL certificates, which provide the familiar padlock icon in browsers that users have been trained to trust. Attackers frequently obtain these certificates for deceptive domain names that closely mimic legitimate services, creating a false sense of security for potential victims.
The increasing complexity of these attacks underscores the importance of understanding not just what to look for, but how modern phishing operations function at a fundamental level.
Common Signs of Phishing
Visual Red Flags
In today’s digital landscape, browsers serve as our primary defense against sophisticated phishing attempts. Understanding the visual indicators that modern browsers provide is essential for secure browsing. These indicators, when properly interpreted, can alert users to potential threats before sensitive information is compromised.
Domain name irregularities present one of the most critical areas for secure browsing. Modern phishing attacks frequently employ homograph attacks, where similar-looking characters replace legitimate ones. For instance, attackers might substitute the Latin letter ‘a’ with a Cyrillic character that appears nearly identical, or use Cyrillic letter ‘e’ in place of the Latin letter ‘e’ for a phishing link. Additionally, typosquatting techniques target common misspellings of popular domains, such as ‘goggle.com’ or ‘microsfot.com’, making it crucial to examine URLs with particular attention to spelling and character composition to prevent from phishing.

Homograph Domains vs Legitimate Domains, Source
SSL certificate information provides another layer of security verification that warrants careful attention. While the presence of a padlock icon indicates an encrypted connection, it doesn’t guarantee website legitimacy. Modern browsers display detailed certificate information when users click the padlock icon, revealing crucial details about the certificate issuer and the organization it was issued to. Mismatches between the organization name and the expected website owner, or certificates issued by unusual authorities, should immediately raise concerns.
URL structures and redirect chains represent another area where vigilance is essential. Legitimate websites typically maintain straightforward URL structures, while phishing sites often employ complex redirect chains or unusual parameters to obscure their true nature. Modern browsers highlight the primary domain in the address bar, but users should remain attentive to unusual subdomains or long strings of random characters that might indicate a compromised or malicious site.
Understanding these visual indicators empowers users to make informed decisions about website legitimacy and develop their secure browsing practices. As phishing techniques continue to evolve, maintaining awareness of these browser-based security indicators becomes increasingly crucial for protecting personal and organizational data.
Tools for Phishing Prevention
Preventing from phishing attacks requires a comprehensive approach that combines technical configurations with mindful secure browsing habits. Organizations and individuals can significantly reduce the chance of clicking phishing links by implementing robust security practices and verification procedures.
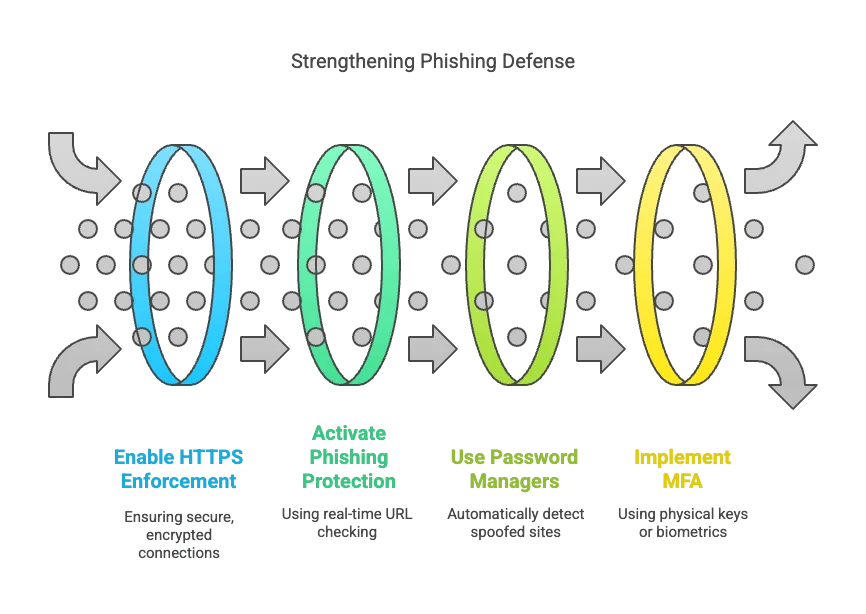
Necessary Security Practices and Verification Procedures for Secure Browsing
Other than these practices, there are several tools and services available that can help you prevent phishing attempts, identify malicious links and are generally helpful for secure browsing practices. These tools use a variety of methods—ranging from checking against known blacklists and analyzing URL behavior to crowd-sourced reputation data—to determine whether a link is a phishing link or not. Here are some widely used options:
- VirusTotal: Aggregates scans from numerous antivirus engines and URL reputation services. You can submit a URL to see if any engines flag it as malicious.
- Google Safe Browsing: This service maintains a list of dangerous websites and is integrated into many browsers to warn users when they attempt to visit suspicious sites.
- PhishTank: A community-driven database that collects and verifies phishing links. Users can check if a particular link is a phishing link.
- URLVoid: Provides a reputation report on a website by checking against multiple databases and blacklists.
- URLScan.io: Analyzes websites by capturing screenshots and monitoring network activity to detect malicious behavior.
- Web of Trust (WOT): Uses crowd-sourced reviews and ratings to give an overview of a website’s reputation and safety.
- Norton Safe Web / McAfee SiteAdvisor: These tools offer safety ratings and warnings about websites based on their analysis and user feedback.
- SOCRadar Free SOC Tools: SOCRadar Free SOC Tools is a comprehensive set of SOC tools offering a suite of specialized services designed to protect your digital environment. Their IP Reputation service checks whether your IP or IP block appears on any blacklists, while Phishing Radar proactively generates domain-related keywords to scour databases for signs of spoofing and phishing. Complementing these, the Email Security Grader performs both passive and active evaluations against cyber attack techniques, and the Email Threat Analyzer swiftly determines the legitimacy of suspicious emails.
Conclusion
The effectiveness of these security practices relies heavily on consistent application and regular updates to account for emerging threats. Organizations should establish clear protocols for reviewing and updating their security practices, ensuring that all stakeholders understand their role in maintaining a secure browsing environment. Regular security awareness training should reinforce these practices, helping users develop the habits necessary for identifying and avoiding increasingly sophisticated phishing attempts.


































