
An Overview on Conti Ransomware Leaks: Is This the End for Conti?
Along with Russia’s physical invasion of Ukraine on February 24th, 2022, Russia has targeted and attacked Ukraine in cyberspace. There has been a massive spike in cyberattacks parallel to physical aggression, affecting many Ukrainian organizations such as government ministries and state-owned banks. The cyber side of the war has been “bloody” so far because of the numerous critical DDoS attacks and new deadly war weapons such as the HermeticWiper and the Cyclops Blink malware.
Hacker Gangs in Politics: Joining the Cyber-Battlefield
Well-known hacker gangs worldwide did not stay silent during the cyberwar, some of which are choosing sides. The Anonymous group was the first one to choose, and they declared that they were siding with Ukraine in the cyberwar. Several Russian government websites went down slightly after they have announced their allegiance to Ukraine.
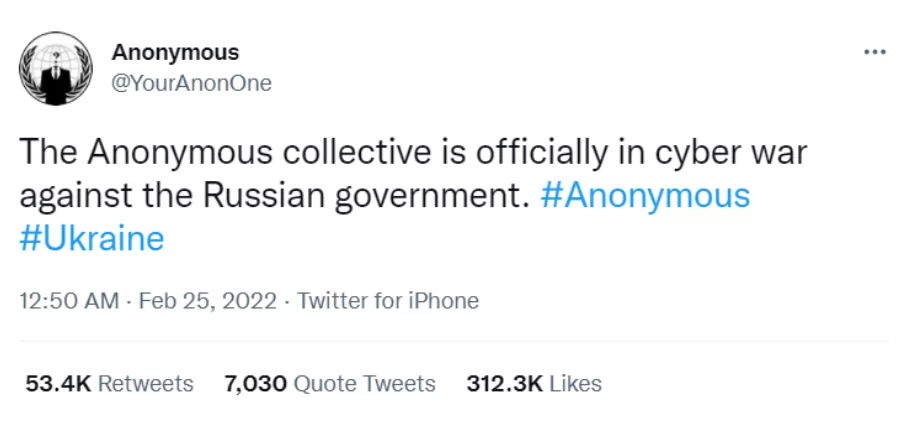
Not long after the Anonymous Group stated their allegiance, the Conti Ransomware group joined the cyberwar with a post on the gang’s dark web site, declaring their full support to the Russian government.
We can see from the post that Conti was ready to go to great lengths in defending Russia. It turns out, not every member of Conti was happy with the aggressive standpoint against Ukraine. Some members were clearly not siding with Russia in the cyber-warfare, so they were pretty upset about the situation, so upset that they betrayed their own organization. The internal conflict led to an event of utmost importance, Conti Leaks.
Conti’s Downfall Begins as Sensitive Data is Leaked
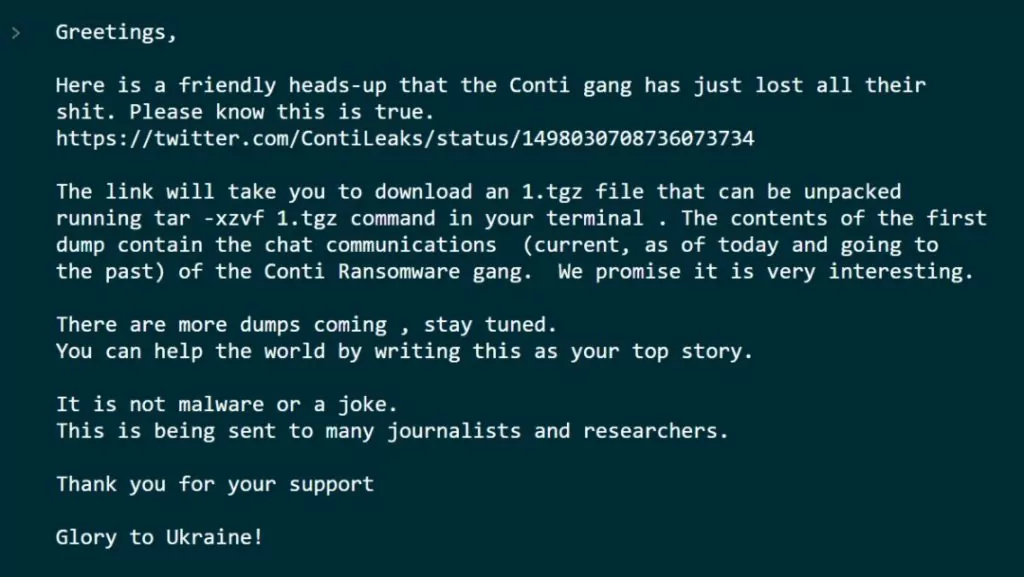
Shortly after the aggressive post on Conti’s leak site, on the same day, a Conti member siding with Ukraine began leaking sensitive data with the message “**** Russia, Glory to Ukraine!”. We can say that Conti’s aggressive standpoint was the reason for its downfall, not taking that some of its members might not 100% agree with siding with Russia into account. Below, you can see Conti Leaker’s message to the world along with the leaks.
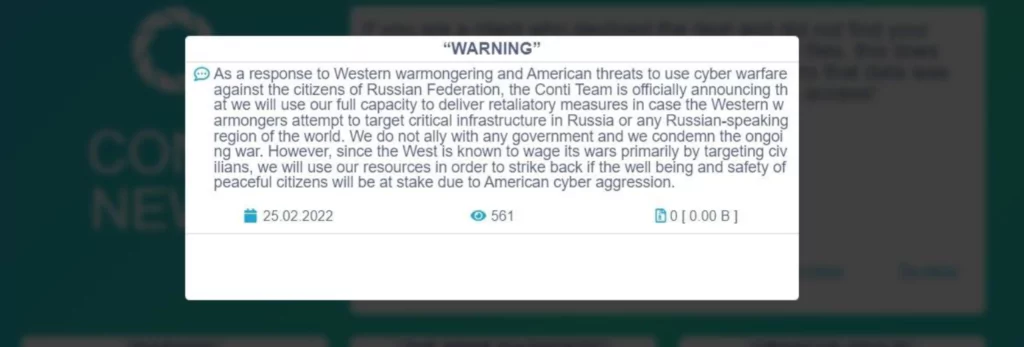
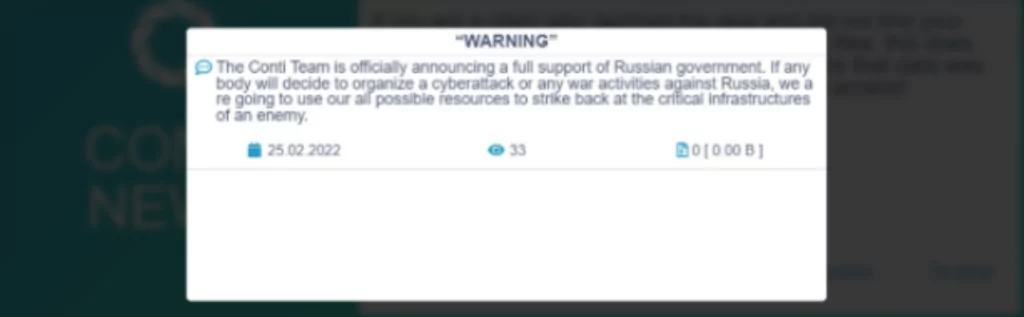
Conti has replaced its original aggressive post on the leak site with a more neutral one on the same day, noticing that they made a mistake. Unfortunately for Conti, it was too to mitigate the damage as the leakers were adamant about their choice.
The leaks are consistently coming in from a Twitter account, @ContiLeaks. Each day, we can see more sensitive data are being leaked about the notorious ransomware group. The Twitter account also posts tweets cursing the Russian government and supporting Ukraine.
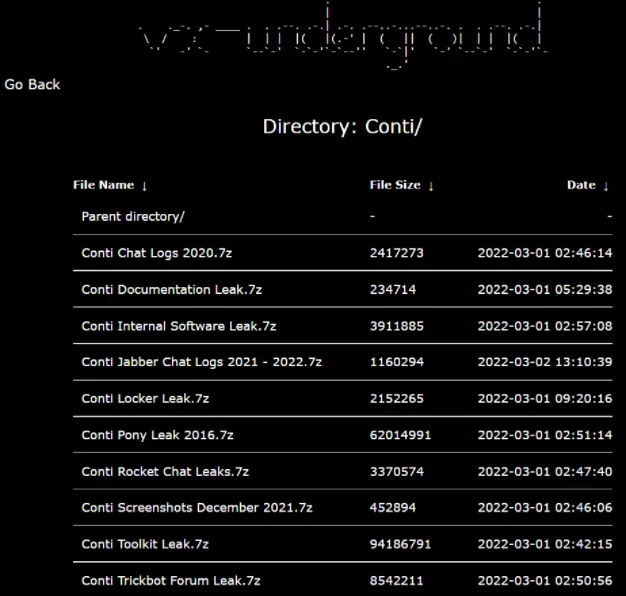
The malware source code and samples collection library vxunderground has been archiving each leak on their website, https://share.vx-underground.org/. You can access and download the Conti leaks from the archive. We suggest that downloading the files is done with caution since not all files are verified, there could be malicious files.
What’s in the Leaks?
We have compiled together and derived for you the most critical information the leaks include.
Chat Logs
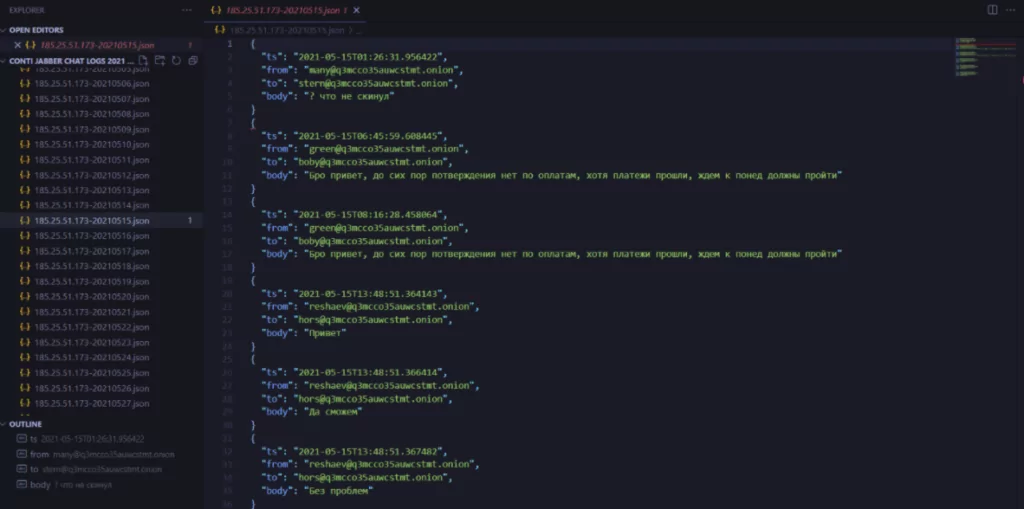
You can see chat logs in JSON format in the leaks starting from June 2020. There were 2103 JSON files in three different files containing chat logs. The logs were in Russian, but there are some people in the cyber community that translated all the logs to English.
You can reach the translated logs in here: https://github.com/tsale/translated_conti_leaked_comms
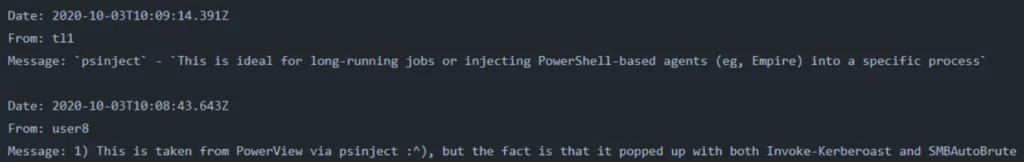
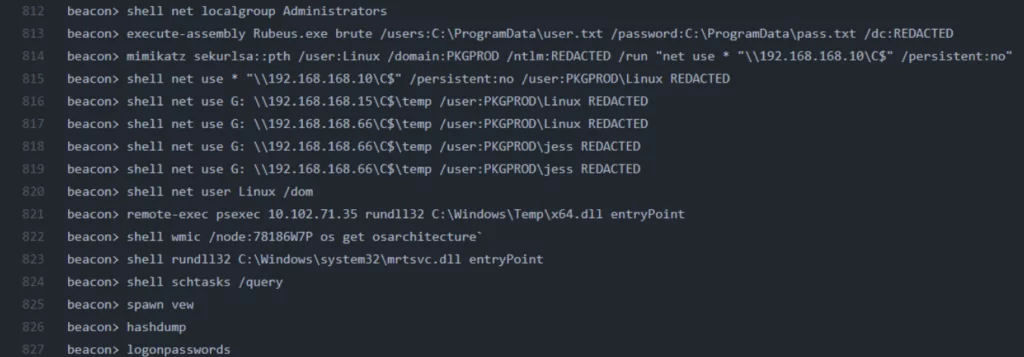
In multiple files, Conti members discuss TTPs to perform cyberattacks using Cobalt Strike. The mentioned tactics from the chat logs include active directory enumeration with AdFind, brute force attacks with SMBAutoBrute and kerberoasting, SQL Database enumeration with sqlcmd, pass-the-hash attacks with Mimikatz, and many more.
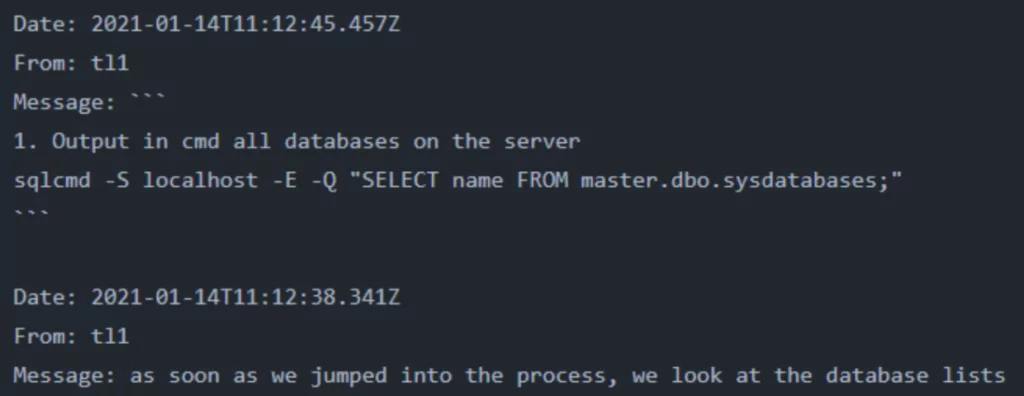
You can reach Cobalt Strike commands and LOLbins Conti used from here:
https://github.com/soufianetahiri/ContiLeaks/blob/main/cobaltsrike_lolbins
Training Files and Videos
The leaks also include internal training files and training videos designed to produce more hackers working for Conti.
Internal Software
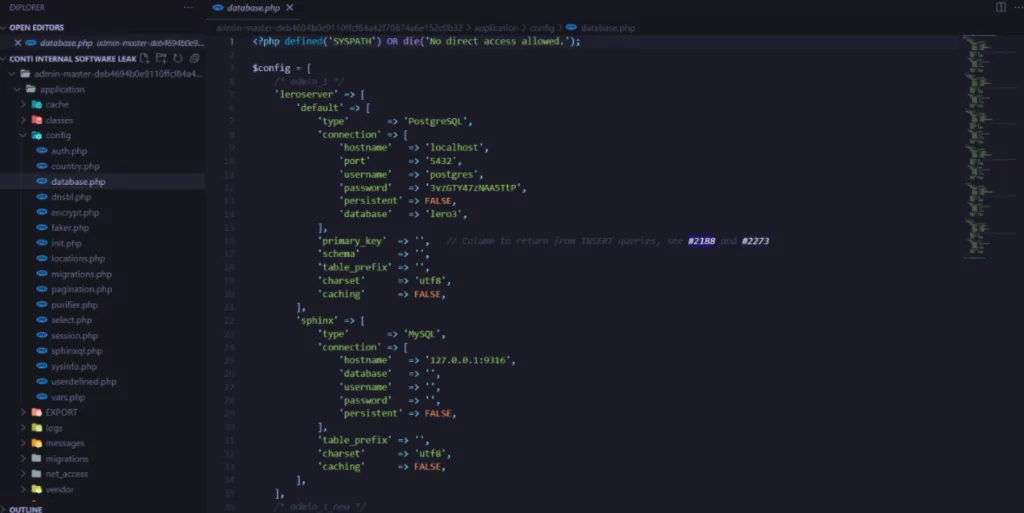
In a folder inside the leaks, we can see several git repositories of internal software used by Conti (Even the threat actors use version-control software!). Most of the code inside this folder was written in PHP, and most folders include open-source software used by Conti.
Screenshots
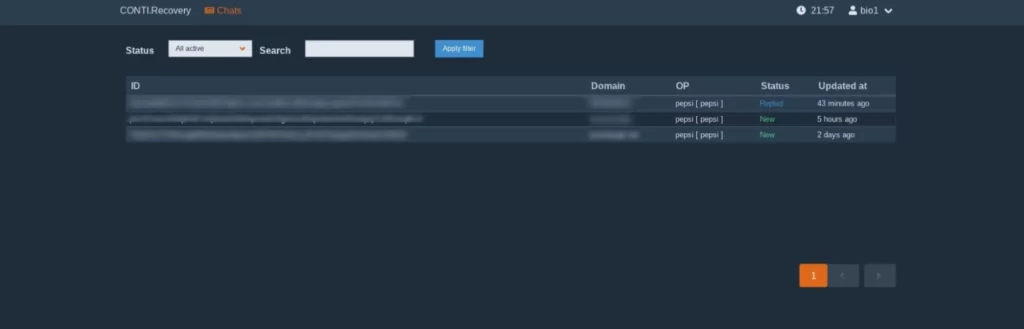
The leaks also include multiple screenshots from Conti’s operations. Below, you can see a screenshot from Conti’s Cobalt Strike panel and a screenshot from Conti’s recovery chat panel.
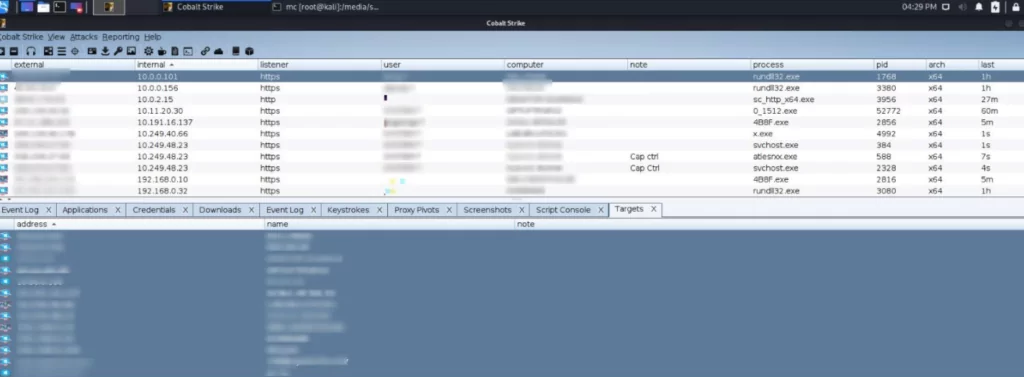
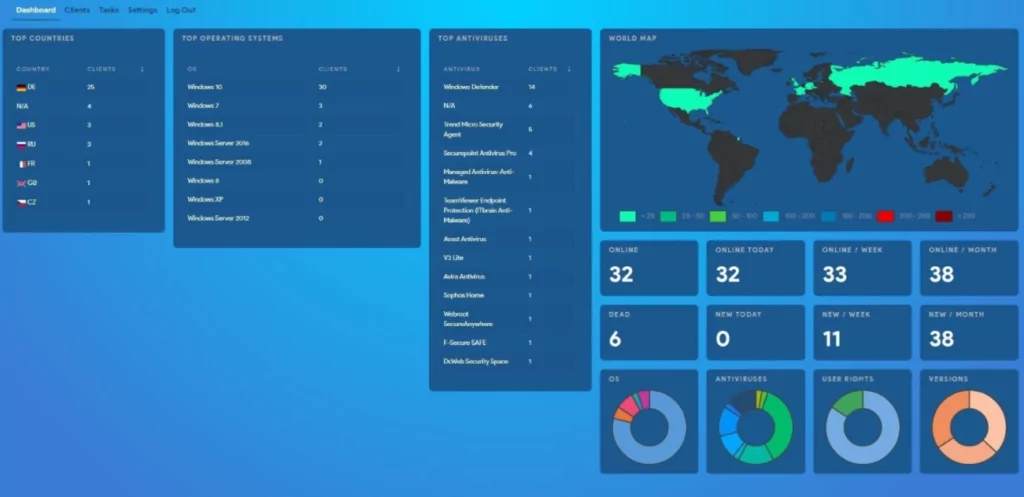
In addition, the leaks also had another interesting screenshot, including a web panel that was never seen before. The panel shows that Conti actively tracks top antiviruses used by its victims and the victims’ operating systems. The lesson to be learned is keeping the software you are using up to date and patching vulnerabilities is crucial since Conti tracks which software you use. If they find an unpatched vulnerability, they will exploit it.
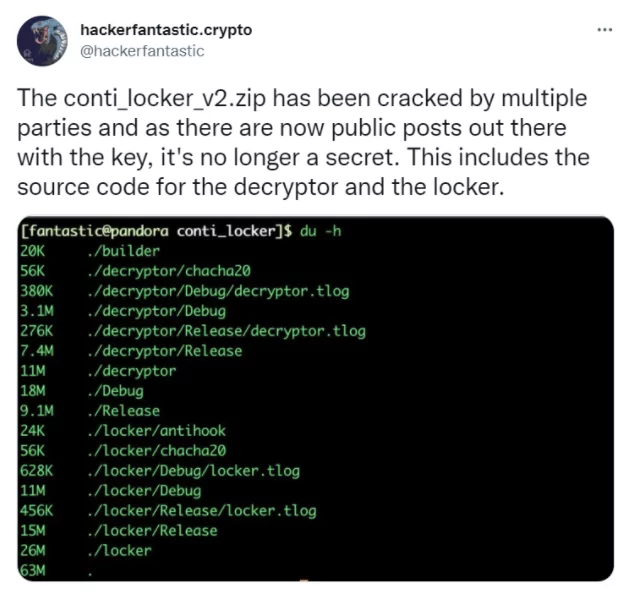
Conti Locker and Decryptor
Most importantly, Conti Locker and Decryptor software were leaked. The leaks were initially encrypted, but people in the cyber community decrypted the leaks and gave the decryption key. We can see that the encryption is done with a variant of ChaCha20 encryption algorithms from the file.
Unfortunately for the previous victims of Conti, the locker and the decryptor software do not mean that they can decrypt their files without the decryption keys. The locker is responsible for encrypting the data and creating decryption keys, whereas the decryptor software is responsible for decrypting the data using decryption keys. Other than private test keys, no decryption keys were found in the leak files.
Bitcoin Addresses
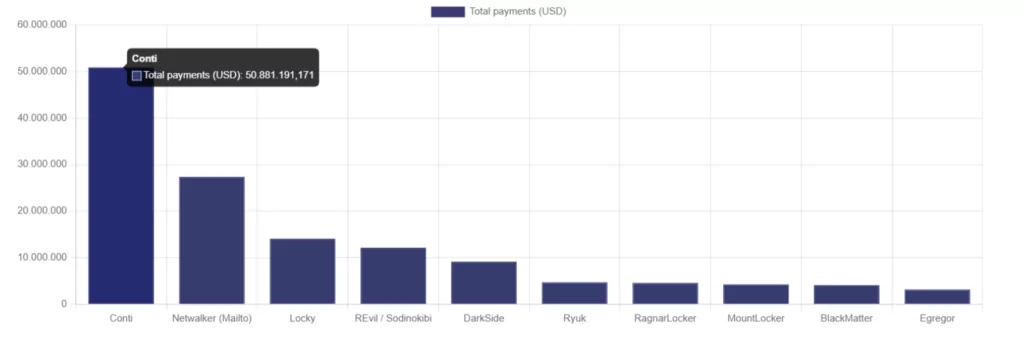
Multiple bitcoin addresses Conti uses to receive ransom payments were found in the leak files.
Thanks to the open-source crowdfunded ransomware tracker ransomwhe.re and the discovered Bitcoin addresses from the leak, we can see and track the transactions Conti has received throughout its operations. Conti has approximately received 50 million US dollars in ransom, and that’s only the tip of the iceberg, the amount we can see and calculate.
Is This The End For Conti?
With the leaks coming in every day and providing us the details of how the notorious ransomware group Conti works, we can say that the cyber community has gained more insight into preventing Conti from breaching networks. The cyber community knows which tools they use, which vulnerability they exploit, or which attack they launch. However, is this all of Conti’s TTPs and capability? Assuming it is not is the best course of action we can take, the invisible part of the iceberg is still yet to unravel.
These leaks will not be able to take Conti down permanently but will slow Conti’s operations and weaken their organization. There’s a chance that they will close down Conti and build a brand new organization with a new name but still operating as a ransomware group.
IOCs
You can reach all the IOCs found from the Conti leak files below compiled together by SOCRadar’s analysts.
Conti’s MITRE Mappings
| Initial Access | |
| T1566 | Phishing |
| T1190 | Exploit Public-Facing Application |
| Execution | |
| T1106 | Execution through API |
| T1059.003 | Command and scripting interpreter: Windows command shell |
| T1047 | Windows Management Instrumentation |
| T1204 | User execution |
| T1053.005 | Scheduled task/job: scheduled task |
| Persistence | |
| T1053.005 | Scheduled task/job: Scheduled task |
| Privilege Escalation | |
| T1078.002 | Valid accounts: domain accounts |
| T1083 | File and directory discovery |
| T1018 | Remote system discovery |
| T1057 | Process discovery |
| T1016 | System network configuration discovery |
| T1069.002 | Permission groups discovery: domain groups |
| T1082 | System information discovery |
| T1033 | System owner/user discovery |
| T1012 | Query registry |
| T1063 | Security software discovery |
| Credential Access | |
| T1003 | OS credential dumping |
| T1555 | Credentials from password stores |
| T1552 | Unsecured credentials |
| Lateral Movement | |
| T1570 | Lateral tool transfer |
| T1021.002 | Remote services: SMB/Windows admin shares |
| Defense Evasion | |
| T1562.001 | Impair defenses: disable or modify tools |
| T1140 | Deobfuscate/Decode files or information |
| T1055 | Process injection |
| Command and Control | |
| T1071 | Application Layer Protocol |
| T1219 | Remote access software |
| Exfiltration | |
| T1567.002 | Exfiltration over web service: exfiltration to cloud storage |
| Impact | |
| T1486 | Data encrypted for impact |
| T1489 | Service stop |
| T1490 | Inhibit system recovery |
Source: TrendMicro
Suggestions and Mitigations
Now that we have taken a peek at Conti’s operations, we have more insight into their TTPs. Conti actively exploits legacy vulnerabilities such as ZeroLogon, EternalBlue (ms17-10), Log4J, and many more. SOCRadar’s analysts suggest you upgrade software your company uses to the latest release to stop cyberattacks exploiting unpatched vulnerabilities.
The cyber community has collected all the CVEs (vulnerabilities) discussed in Conti’s leaked chat logs. Below, you can access the CVEs Conti members have actively discussed within their organization. SOCRadar’s analysts suggest you scan your organization’s infrastructure to detect possible vulnerable endpoints to prevent potential cyberattacks.
https://pastebin.com/raw/pv1mDGYC
Thanks to the leaks, we now have access to various IOCs of Conti, such as IP addresses, tor domains, and e-mail addresses. To prevent Conti affiliates from accessing your organization’s endpoints, we suggest integrating IOCs shared by SOCRadar into your SIEM, XDR, and EDR systems.
Lastly, we have seen that Conti commonly utilizes brute force attacks to access credentials used to gain access into their victims’ network. We suggest you train your employees to upgrade your security posture to the next level, educating them to use strong, unique passwords.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access



































