
How to Stop a DDoS Attack? (2023 Edition)
How to Stop a DDoS Attack? (2023 Edition) ...

How Easy Is It to Guess Fortune 500 Executives' Passwords?
How Easy Is It to Guess Fortune 500 Executives’ Passwords? Recently, many cyberattacks on large corporations have begun with acquiring credentials via multiple methods, particularly social ...

Secure Your Cloud Environment: 5 Best Practices
Secure Your Cloud Environment: 5 Best Practices With the increasing adoption of cloud computing, cloud security has become a major concern for businesses that rely on cloud-based services to...

Top 5 Vulnerabilities Routinely Exploited by Threat Actors in 2022
Top 5 Vulnerabilities Routinely Exploited by Threat Actors in 2022 By SOCRadar Research Day by day, it becomes harder to maintain a good security posture. Threat actors are at every corner, searching ...

Gartner Recognized SOCRadar as a DRPS Vendor in 2 Reports
Gartner Recognized SOCRadar as a DRPS Vendor in 2 Reports The digitalization process has become a norm in any business. Now, organizations’ assets are highly increased, and there are many things...
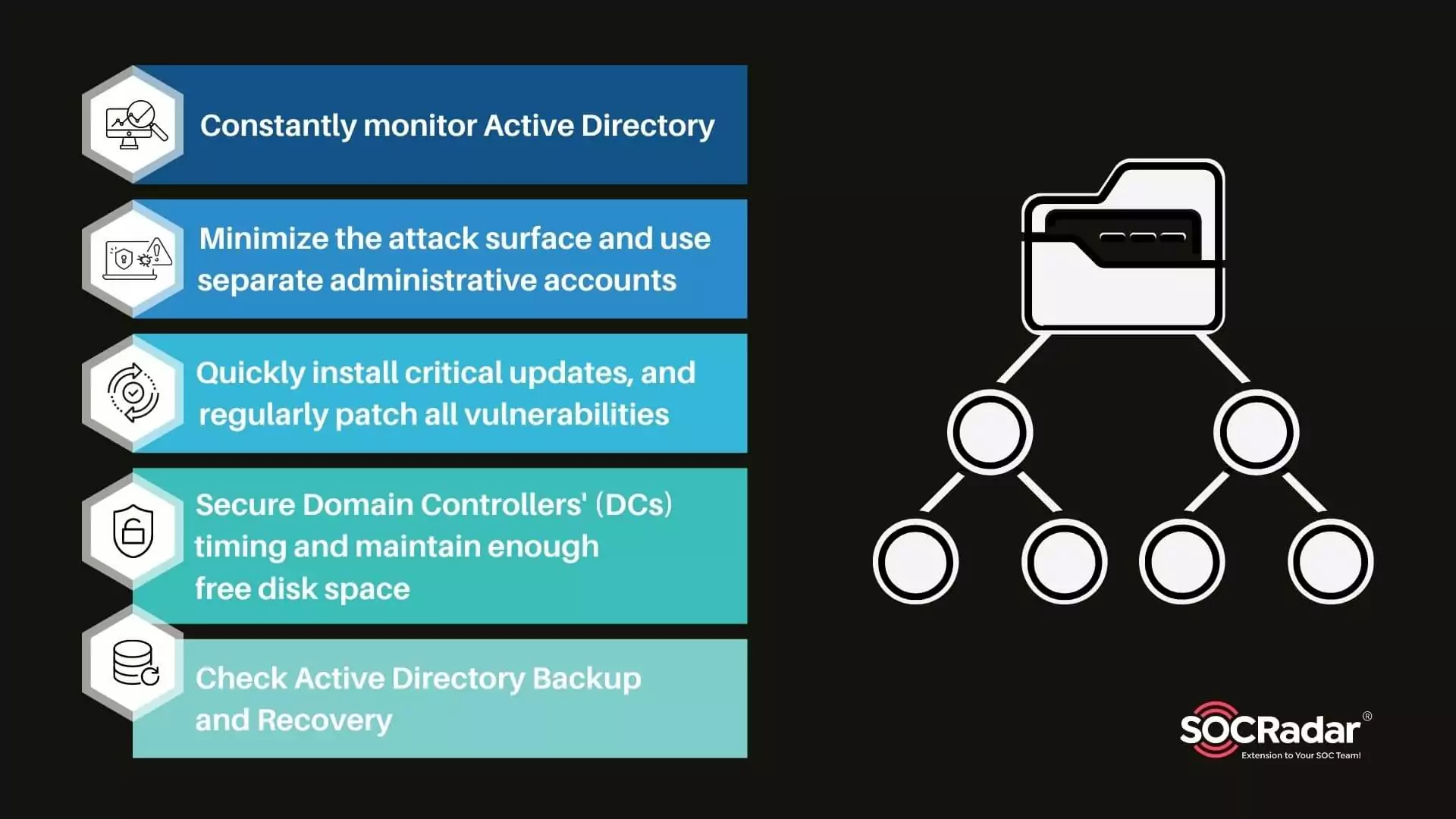
Security for Active Directory in 5 Steps
Security for Active Directory in 5 Steps Microsoft Windows directory service Active Directory (AD) enables IT administrators to manage permissions and restrict access to network resources. With this ...

Danger Lurking in GitHub Repositories
Danger Lurking in GitHub Repositories By SOCRadar Research GitHub is a system that has become the world’s largest source code repository, used by %90 of Fortune 100 companies and 94 million...

What is Password Analyzer?
What is Password Analyzer? A password strength checker is an online application that assesses the security of a user’s password in real-time by analyzing its grammar and highlighting possible vulnerab...

Vulnerability Management Best Practices
Vulnerability Management Best Practices Every day, new vulnerabilities emerge, and multiplying proliferating vulnerabilities throughout today’s complex technology contexts yield a never-ending risk ha...

How Should CISOs Prepare on the Current Cyberthreat Landscape?
How Should CISOs Prepare on the Current Cyberthreat Landscape? Recent research by John Sakellariadis for the Atlantic Council delves deeper into the emergence of ransomware over the past ten...

Top Critical Vulnerabilities Used by Ransomware Groups
Top Critical Vulnerabilities Used by Ransomware Groups As ransomware attacks have grown in popularity recently, researchers have begun compiling an easy-to-follow list of vulnerabilities exploited by ...

A New Rising Social Engineering Trend: Callback Phishing
A New Rising Social Engineering Trend: Callback Phishing Callback phishing emerged as a hybrid social engineering technique that combines phishing and vishing. The phishing technique used to steal sen...

MFA Bypass Techniques: How Does it Work?
MFA Bypass Techniques: How Does it Work? Identification and authentication are the first phase of verification in the login processes of Information Systems. Malicious threat actors use various method...
Cloud Security Module: Minimize Risk of Misconfigured Buckets
Cloud Security Module: Minimize Risk of Misconfigured Buckets Not long ago, there were discussions about whether organizations should migrate to the cloud. The future has come, and almost all dig...

Better Protect Your Mobile App with SOCRadar MAS Module
Better Protect Your Mobile App with SOCRadar MAS Module Threat actors use all kinds of methods to achieve their malicious goals. Mobile apps are among the most popular targets for attackers lately. Ta...
![SOCRadar® Cyber Intelligence Inc. | What is Data Loss Prevention (DLP)? [Ultimate Guide]](https://socradar.io/wp-content/uploads/2022/10/what-is-data-loss-prevention-dlp-ultimate-guide.png)
What is Data Loss Prevention (DLP)? [Ultimate Guide]
What is Data Loss Prevention (DLP)? [Ultimate Guide] Data loss prevention (DLP) prohibits users on a business network from transferring sensitive data outside of the network. DLP systems assist networ...

Recent Attack Types Against Cloud Infrastructures
Recent Attack Types Against Cloud Infrastructures ...
How XDR Powers Rapid Attack Detection and Response
How XDR Powers Rapid Attack Detection and Response A McKinsey article states that today’s organizations are expected to suffer from three major trends for the next three to five years. These trends ca...

What is Account Takeover and How to Prevent It?
What is Account Takeover and How to Prevent It? ...

What is Malvertising & How to Stop Ad Malware?
What is Malvertising & How to Stop Ad Malware? ...



































