Dark Peep #9: The McFlurry Bandit
Welcome to “Dark Peep #9.” This edition takes you behind the scenes of the digital world, where every byte tells a story. Here, we uncover the ongoing sagas of cybercrime, where actions in the virtual world resonate profoundly in reality.
Our journey begins with an unfolding plot: the dark web marketplace, a notorious hub in the digital underworld, stands at a critical juncture. While rumors of its shutdown circulate, the reality is a tangled web of strategies and counter-moves. Rival factions are crafting intricate plans to dethrone this digital empire, setting the stage for a dramatic showdown in the world of cybercrime.

Fig. 1. Illustration of a threat actor wearing a mask is stealthily stealing data from a fast food chain’s computer system. (generated using OpenAI’s DALL-E)
Amid these serious and impactful narratives, there emerges a peculiar tale that has caught the eye of the digital community – the case of “The McFlurry Bandit.” Allegedly involved in the McDonald’s data breach, this situation has sparked a blend of concern and curiosity. While the breach’s nature is serious, whispers and light-hearted speculations surface about whether this enigmatic figure might have sought more than just data – perhaps even the secret recipe of the Big Mac’s sauce. It’s a reminder that even in the gravity of cybercrime, human curiosity and humor find their way.
As we navigate through these shadowy digital corridors, we invite you to look closer, to understand the intricate dance of power and anonymity that defines the online world. Here, in “Dark Peep #9,” we don’t just tell stories; we unveil the ongoing battles and alliances that shape our digital existence. Join us as we reveal the narratives that are writing the next chapter of the internet.
Anonymous Sudan’s Cyber Protest
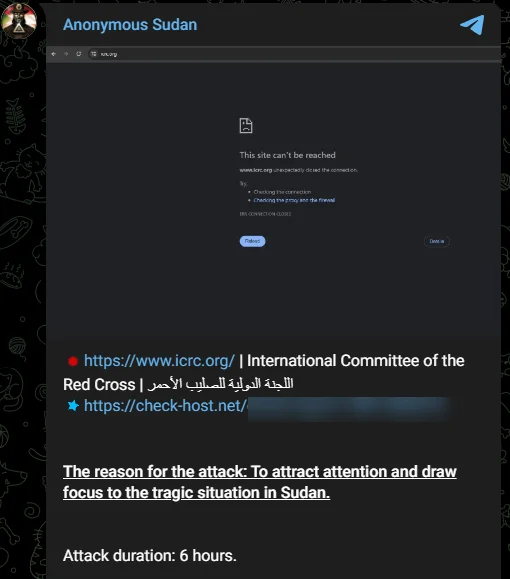
Fig. 2. Anonymous Sudan’s statement
Anonymous Sudan claimed to launch a DDoS attack on the International Committee of the Red Cross website to draw attention to the situation in Sudan. This cyber protest is an example of how hacktivism is increasingly used to draw global attention to regional crises.
Conti-Related Threat Actor’s Holiday Break
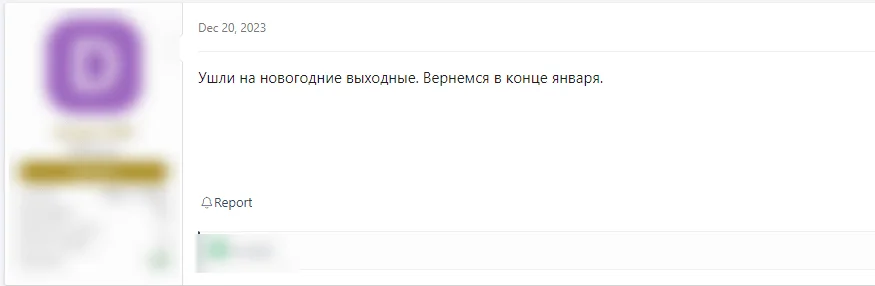
Fig. 3. Threat actors also go on vacation
In a rare pause, a threat actor associated with the notorious Conti ransomware group has announced a break for the new year, with plans to return at the end of January. While this break in cybercriminal activity does not offer a temporary respite in the cybersecurity world, cyber threat actors do take vacations.
Kingdom Market Shutdown

Fig. 4. Banner indicating seizure displayed on Kingdom Market (Source: vx-underground)
In a coordinated global operation, German authorities, with support from the U.S., Switzerland, Moldova, and Ukraine, have successfully dismantled the notorious dark web hub, ‘Kingdom Market.’ This infamous platform, a digital underworld den, was known for its extensive trade in narcotics and malware, catering to a vast network of tens of thousands of users. Initiated on December 16, 2023, this operation marks a significant blow to the dark web’s illegal commerce channels, showcasing the relentless pursuit of justice against such clandestine activities. Threat actors may think they’re stealthy, but there are Sherlocks in cybersecurity.
The Downfall of a Young Threat Actor

Fig. 5. Illustration of a threat actor is in a hospital under surveillance, in a style reminiscent of Grand Theft Auto (generated using OpenAI’s DALL-E)
Arion Kurtaj, an 18-year-old Oxford hacker affiliated with the infamous Lapsus$ gang, found his misdeeds caught up with him as he was sentenced to an indefinite hospital order. Despite his youth and challenges with severe autism, Kurtaj’s actions painted him as a digital villain of considerable threat. His cyber-attacks, targeting tech giants like Uber, Nvidia, and Rockstar Games, racked up nearly $10 million in damages. His most audacious act involved breaching Rockstar’s security, using only a hotel TV, an Amazon Firestick, and a mobile phone to leak 90 clips of the highly anticipated Grand Theft Auto 6. This continued defiance of the law, even under police watch, led to his containment in a secure facility, illustrating a stark example of cybercrime’s real-world consequences.
ALPHV Ransomware’s Counter Strike
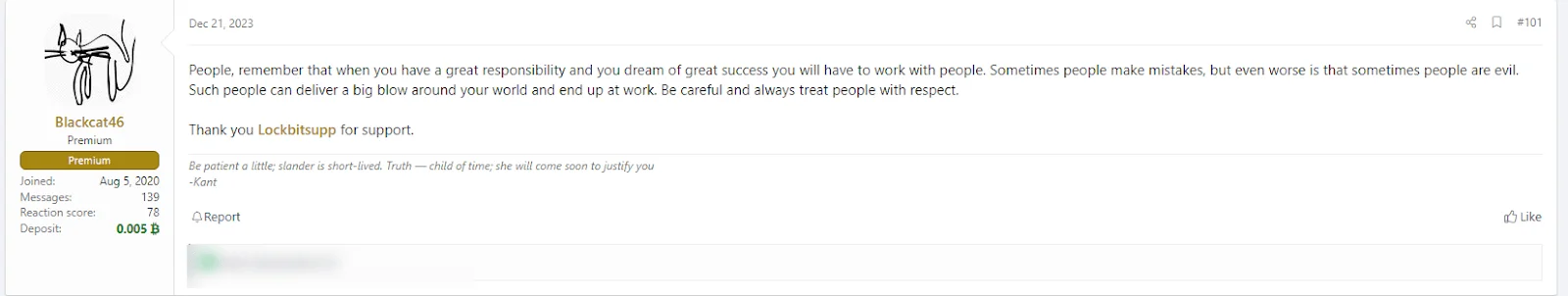
Fig. 6. First message in a series of forum comments between ALPHV and LockBit
The digital landscape witnessed a bold resurgence from ALPHV Ransomware, defying an F.B.I. takedown with remarkable agility. In a rare display of cyber-solidarity, the group’s leader openly thanked their rival, LockBit, for support, advocating a united front against law enforcement.
Cyb3r Drag0nz’s Temporary Retreat
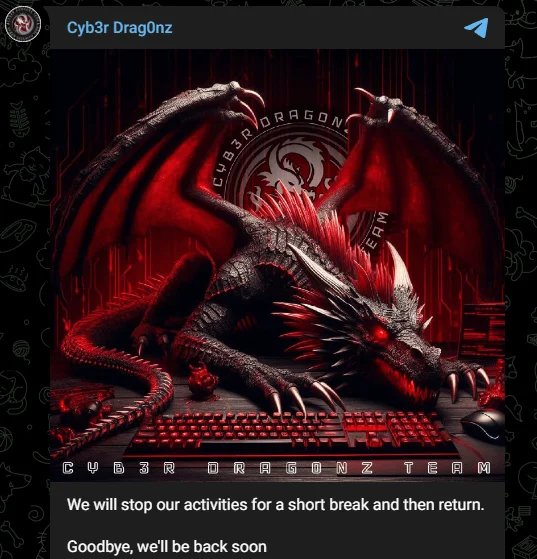
Fig. 7. threat group’s break announcement
In an intriguing turn of events, the Cyb3r Drag0nz threat group announced a temporary cessation of their activities. The group’s message, shared on their Telegram channel, simply stated, “We will stop our activities for a short break and then return. Goodbye, we’ll be back soon.” This pause in operations raises questions about the motivations and plans of the group. Such breaks, whether for strategic repositioning, evading law enforcement, or internal restructuring, are not uncommon in hacktivist circles and often precede significant shifts in tactics or targets.
KillNet’s Dark Lottery
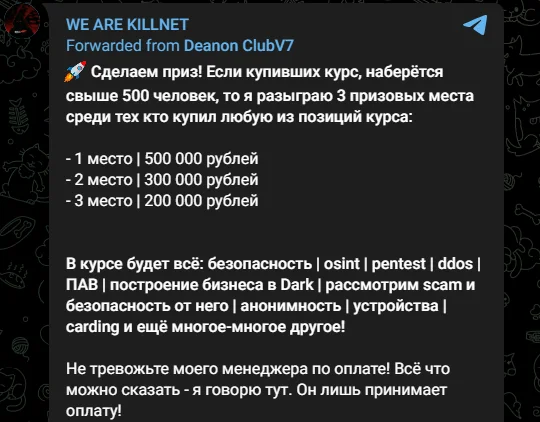
Fig. 8. KillNet’s statement
KillNet, making waves in the cybercrime arena, recently shared an unusual post on their Telegram channel. They announced a lucrative contest to incentivize participation in their comprehensive course, covering various topics from security and pen-testing to the intricacies of operating on the dark web.
The competition promises substantial cash prizes for three lucky participants, with the condition of reaching a threshold of 500 course purchases. This initiative highlights KillNet’s efforts to expand its influence. It reflects a growing trend where cybercriminal groups venture into education and knowledge-sharing in their domains, blending traditional business models with the clandestine nature of their operations.
Deanon Club’s Threat or Announcement?
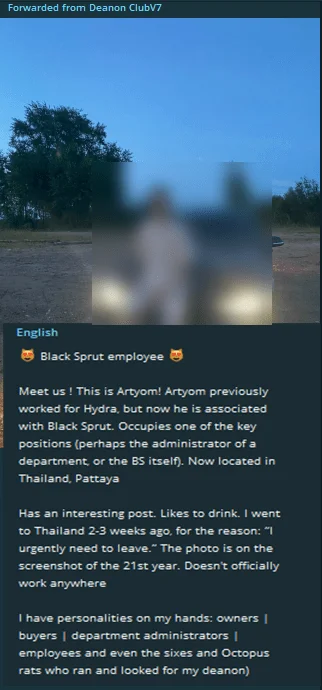
Fig. 9. Threatening announcement by cyber-crime group
In a striking development on the dark web, Deanon Club made waves with an announcement on KillNet’s Telegram channel that toes the line between a simple update and a veiled threat. According to the threat group’s message, They’ve spotlighted Artyom, who has shifted allegiances from Hydra to Black Sprut and recently moved to Thailand under mysterious circumstances described as “urgently need to leave.”
This move, coupled with Deanon Club’s ambitious declaration of aiming for dark web market dominance—and predicting the downfall of major players like Kraken and BlackSprout in mere months—signals a potentially seismic shift in the underworld’s power dynamics. This narrative unfolds like a plot straight out of a thriller, where allegiances are as fluid as the identities hiding behind the screen, making the dark web’s future all the more unpredictable.
The Alleged McDonald’s Data Breach and The McFlurry Bandit
A new development in corporate cybersecurity emerged with the reported breach of McDonald’s data. The revelation came through BreachForums, where a user named ‘euphoria’ claimed extensive access to the company’s internal data. The breach allegedly includes sensitive fields such as OrgName, Username, and bank logs, suggesting a significant penetration into McDonald’s systems.
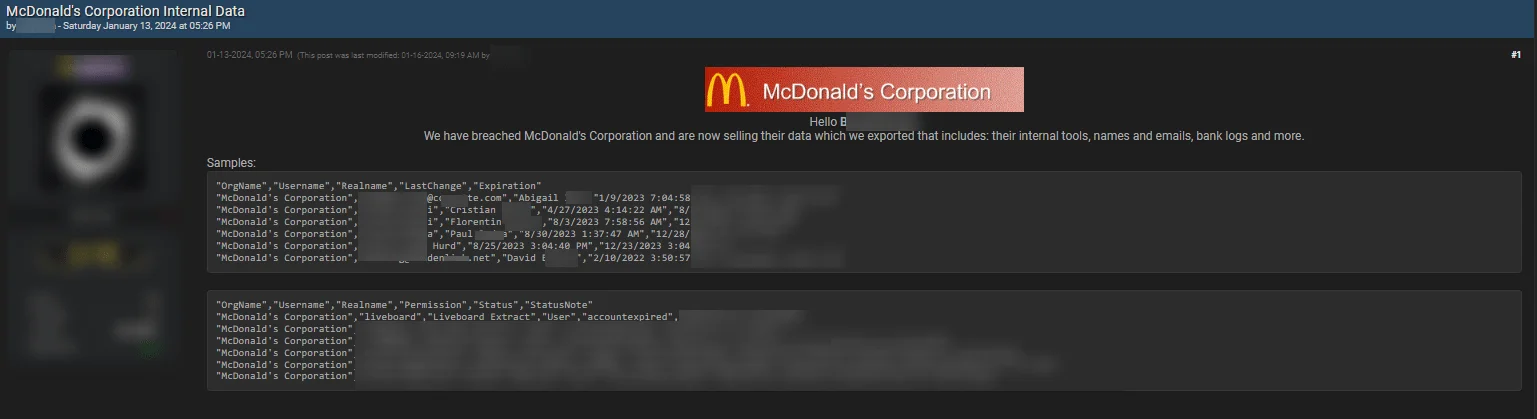
Fig. 10. Threat actor claims to have hacked McDonald’s
Notably, this breach involves critical information, extending to internal tools and bank logs, highlighting a severe lapse in McDonald’s security measures. The modus operandi of ‘euphoria,’ seemingly looking for private deals rather than public exposure or ransom, indicates a potential shift in cybercriminal tactics.
The breach’s seriousness is compounded by the alleged access to McDonald’s private source code from their GitHub repository. The online community is abuzz with speculations, some even linking this breach to a threat actor humorously known as “the McFlurry Bandit,” previously mentioned by vx-underground on Twitter.
GhostLocker V2: The Phantom Upgrade
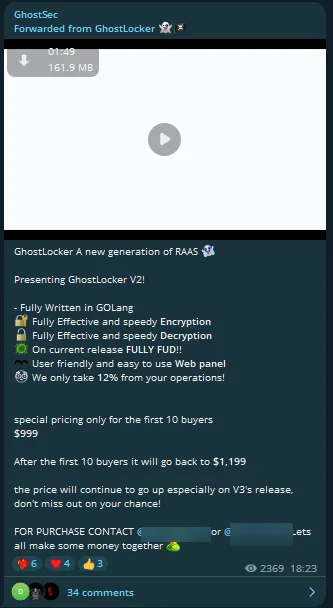
Fig. 11. GhostLocker V2 release
In the latest update from the dark web’s notorious GhostSec, they’ve unveiled GhostLocker V2, a sinister evolution in their Ransomware as a Service (RaaS) offerings. While it appears to lack entirely new features, significant upgrades have been made to its Fully Undetectable (FUD) capabilities and the user interface of its web panel. They emphasize that prices will continue to rise, especially with the release of V3, urging interested parties not to miss out.
BreachForums Admin’s Downfall

Fig. 12. Illustration of an individual under house arrest required to stay away from computers. (generated using OpenAI’s DALL-E)
Conor Brian Fitzpatrick, known as “Pompompurin” in the cyber realm, has faced a significant legal reckoning. As the former administrator of the infamous BreachForums, Fitzpatrick has been sentenced to 20 years of supervised release. This sentence comes after his arrest in January 2023 and subsequent violation of parole terms. The Eastern District of Virginia’s US District Court has imposed stringent restrictions on Fitzpatrick, including two years of home arrest with GPS tracking and a one-year internet ban.
BlackSec’s New Era as SparrowCorp
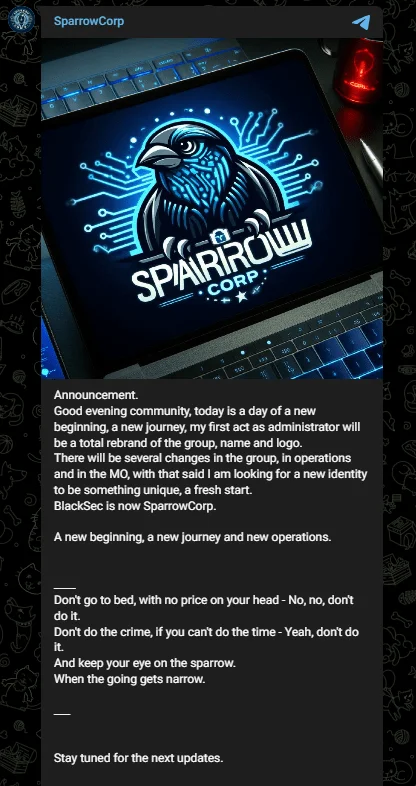
Fig. 13. BlackSec’s rebranding announcement
BlackSec, under new leadership from USDoD, rebrands as SparrowCorp. This change signals a fresh direction for the group, promising operational and structural shifts. USDoD’s inaugural message pledges to uphold and expand BlackSec’s legacy while distancing from former associates, including the ‘five families.’
Conclusion
As this edition of Dark Peep concludes, we see the Dark Web’s dynamics shifting constantly. Each story we explore highlights the digital realm as a space for relentless change and adaptation. Here, cyber threats and defenses intricately and critically fluctuate.
SOCRadar’s Dark Web modules play a crucial role in navigating these waters. These tools go beyond mere monitoring to understand the nuanced layers of the cyber underworld. Organizations using SOCRadar delve into the dark web’s complexities, unearthing insights from its murky depths. SOCRadar’s true power lies in its ability to unveil the hidden and illuminate the unknown.
SOCRadar Dark Web Monitoring
Imagine a kaleidoscope where each turn presents an unexpected, complex pattern. Similarly, SOCRadar’s modules uncover patterns of emerging threats, evolving tactics, and hidden vulnerabilities in the dark web’s chaos. This foresight is vital in cybersecurity, as forewarning equates to forearming.
Moreover, SOCRadar’s Source Code Leak Monitoring module operates like a diligent detective, thoroughly examining the web of GitHub repositories and beyond. This vigilant surveillance covers other public repositories, safeguarding sensitive data. It provides a critical defense line by detecting potential exposures, from misplaced API keys to confidential code snippets.
SOCRadar Threat Actor/Malware
In closing, this edition of Dark Peep starkly reminds us of the ever-changing nature of cyber threats. It underscores the importance of tools like SOCRadar’s Dark Web modules, which anticipate threats, not just respond to them. As we gear up for the future, we must equip ourselves with the knowledge and tools to navigate and master the unpredictable tides of the cyber world.