
Exploit of Romcom RAT's
The RomCom RAT is a malicious software program used by a threat actor to remotely control compromised systems, often by impersonating well-known brands and deploying fake versions of legitimate software through phishing campaigns.
| Domains | Source | Last Update |
|---|---|---|
| aaa.stage.16549040.dns.alleivice.com | SOCRadar | 2023-01-31 |
| teoresp.com | SOCRadar | 2023-01-31 |
| advanced-ip-scaner.com | SOCRadar | 2023-01-31 |
| tinheranter.com | SOCRadar | 2023-01-31 |
| optasko.com | SOCRadar | 2023-01-31 |
| cuba4ikm4jakjgmkeztyawtdgr2xymvy6nvgw5cglswg3si76icnqd.onion | SOCRadar | 2023-01-31 |
| witorophron.com | SOCRadar | 2023-01-31 |
| combinedresidency.org | SOCRadar | 2023-01-31 |
| leftthenhispar.ru | SOCRadar | 2023-01-31 |
| nastylgilast.com | SOCRadar | 2023-01-31 |
| thehentoftbet.ru | SOCRadar | 2023-01-31 |
| toftoflethens.com | SOCRadar | 2023-01-31 |
| notfiled.com | SOCRadar | 2023-01-31 |
| tycahatit.ru | SOCRadar | 2023-01-31 |
| kurvalarva.com | SOCRadar | 2023-01-31 |
| otinrofha.ru | SOCRadar | 2023-01-31 |
| babbedidndu.ru | SOCRadar | 2023-01-31 |
| you-supported.com | SOCRadar | 2023-01-31 |
| johntotrepwron.com | SOCRadar | 2023-01-31 |
| reninparwil.com | SOCRadar | 2023-01-31 |
| vu42i55fqimjx6koo7oqh3zzvy2xghqe7ot4h2ftcv2pimbauupjyqyd.onion | SOCRadar | 2023-01-31 |
| nagirlstylast.com | SOCRadar | 2023-01-31 |
| fabickng.ru | SOCRadar | 2023-01-31 |
| advanced-ip-scanners.com | SOCRadar | 2023-01-31 |
| torsketronand.ru | SOCRadar | 2023-01-31 |
| tandugolastsp.com | SOCRadar | 2023-01-31 |
| ningwitjohnno.ru | SOCRadar | 2023-01-31 |
| dgtlocean.com | SOCRadar | 2023-01-31 |
| 4qzm.com | SOCRadar | 2023-01-31 |
| facabeand.com | SOCRadar | 2023-01-31 |
| Hashes | Source | Last Update |
|---|---|---|
| 4de5d433af5701462517719ce097bb4c0e5676c9 | SOCRadar | 2023-01-31 |
| eaced2fcfdcbf3dca4dd77333aaab055345f3ab4 | SOCRadar | 2023-01-31 |
| 550f42c5b555893d171285dc8b15b4b5 | SOCRadar | 2023-01-31 |
| 3e3a7116eeadf99963077dc87680952cca87ff4fe60a552041a2def6b45cbeea | SOCRadar | 2023-01-31 |
| 4c32ef0836a0af7025e97c6253054bca | SOCRadar | 2023-01-31 |
| 05681ff7cae6b28f5714628a269caa5115da49c94737ce82ec09b4312e40fd26 | SOCRadar | 2023-01-31 |
| ac09cbfee4cf89d7b7a755c387e473249684f18aa699eb651d119d19e25bff34 | SOCRadar | 2023-01-31 |
| 3e6f9e73ca7bf856c3f5aeb44dc793ec4927b842 | SOCRadar | 2023-01-31 |
| cf6ec2999b5d67df89a5350dfcff611d | SOCRadar | 2023-01-31 |
| de239ac43508c4fd4c9069a9b6a4a3f8 | SOCRadar | 2023-01-31 |
| 1b943afac4f476d523310b8e3afe7bca761b8cbaa9ea2b9f01237ca4652fc834 | SOCRadar | 2023-01-31 |
| b5d202456ac2ce7d1285b9c0e2e5b7ddc03da1cbca51b5da98d9ad72e7f773b8 | SOCRadar | 2023-01-31 |
| e80d80521238008bf6f429e072eaf6030c06e2d3123d03ea9b36f5a232a1ec90 | SOCRadar | 2023-01-31 |
| d907be57b5ef2af8a8b45d5f87aa4773 | SOCRadar | 2023-01-31 |
| f8144fa96c036a8204c7bc285e295f9cd2d1deb0379e39ee8a8414531104dc4a | SOCRadar | 2023-01-31 |
| 13ab5762ff5023163b1ca7c7749112b3673cd3db | SOCRadar | 2023-01-31 |
| a1649dec72c316587b10d92993aee1ec | SOCRadar | 2023-01-31 |
| a304497ff076348e098310f530779002a326c264 | SOCRadar | 2023-01-31 |
| f538b035c3de87f9f8294bec272c1182f90832a4e86db1e47cbb1ab26c9f3a0b | SOCRadar | 2023-01-31 |
| d1a84706767bfb802632a262912e95a8 | SOCRadar | 2023-01-31 |
| 10a5612044599128981cb41d71d7390c15e7a2a0c2848ad751c3da1cbec510a2 | SOCRadar | 2023-01-31 |
| 0afed8d1b7c36008de188c20d7f0e2283251a174261547aab7fb56e31d767666 | SOCRadar | 2023-01-31 |
| d0bbbc1866062f9a772776be6b7ef135d6c5e002 | SOCRadar | 2023-01-31 |
| 5f187393acdeb67e76126353c74b6080d3e6ccf28ae580658c670d8b6e4aacc1 | SOCRadar | 2023-01-31 |
| 02a733920c7e69469164316e3e96850d55fca9f5f9d19a241fad906466ec8ae8 | SOCRadar | 2023-01-31 |
| 3a8b7c1fe9bd9451c0a51e4122605efc98e7e4e13ed117139a13e4749e211ed0 | SOCRadar | 2023-01-31 |
| 2f93bf6feb96aa13973cb923abcf402d3d829cb6 | SOCRadar | 2023-01-31 |
| 04972228302e569da856e4fa45f679ed | SOCRadar | 2023-01-31 |
| 9959e90d255c0221e9754db53e321ab4c7434488 | SOCRadar | 2023-01-31 |
| 1817cc163482eb21308adbd43fb6be57fcb5ff11fd74b344469190bb48d8163b | SOCRadar | 2023-01-31 |
| f31620e7e22a30f408e5d683922f5029 | SOCRadar | 2023-01-31 |
| 1a21a1e626fd342e794bcc3b06981d2c | SOCRadar | 2023-01-31 |
| 9aa1f37517458d635eae4f9b43cb4770880ea0ee171e7e4ad155bbdee0cbe732 | SOCRadar | 2023-01-31 |
| 596eaef93bdcd00a3aedaf6ad6d46db4429eeba61219b7e01b1781ebbf6e321b | SOCRadar | 2023-01-31 |
| 3d4502066a338e19df58aa4936c37427feecce9ab8d43abff4a7367643ae39ce | SOCRadar | 2023-01-31 |
| 7e00bfb622072f53733074795ab581cf6d1a8b4fc269a50919dda6350209913c | SOCRadar | 2023-01-31 |
| db3b1f224aec1a7c58946d819d729d0903751d1867113aae5cca87e38c653cf4 | SOCRadar | 2023-01-31 |
| e0d89c88378dcb1b6c9ce2d2820f8d773613402998b8dcdb024858010dec72ed | SOCRadar | 2023-01-31 |
| ee2f71faced3f5b5b202c7576f0f52b9 | SOCRadar | 2023-01-31 |
| cb933f1c913144a8ca6cfcfd913d6d28 | SOCRadar | 2023-01-31 |
| 61971d3cbf88d6658e5209de443e212100afc8f033057d9a4e79000f6f0f7cc4 | SOCRadar | 2023-01-31 |
| 4e4eca58b896bdb6db260f21edc7760a | SOCRadar | 2023-01-31 |
| 542d144a73322a30ceabb002851515a80611bf6c | SOCRadar | 2023-01-31 |
| 99c7cad7032ec5add3a21582a64bb149 | SOCRadar | 2023-01-31 |
| 5f5c18e98e5c8a5a50a1e122221f61dd | SOCRadar | 2023-01-31 |
| 67fe9e515686c2d8cf7eeab0c37a04426599352c | SOCRadar | 2023-01-31 |
| 9f61259c966f34d89b70af92b430ae40dd5f1314ee6640d16e0b7b0f4f385738 | SOCRadar | 2023-01-31 |
| 33fe4c6f5e7803bc0b9d977abd8b816712cbf300 | SOCRadar | 2023-01-31 |
| 0f385cc69a93abeaf84994e7887cb173e889d309a515b55b2205805bdfe468a3 | SOCRadar | 2023-01-31 |
| a2511c5c2839bfbdf9c0f84f415d5eae168456e5d3f77f1becdbcd69fba4daa4 | SOCRadar | 2023-01-31 |
| d5dab3f20d47bf4ca4910949015844d660e99ca9 | SOCRadar | 2023-01-31 |
| 141b2190f51397dbd0dfde0e3904b264c91b6f81febc823ff0c33da980b69944 | SOCRadar | 2023-01-31 |
| 952b34f6370294c5a0bb122febfaa80612fef1f32eddd48a3d0556c4286b7474 | SOCRadar | 2023-01-31 |
| d1ff26ea3d2d2ced4b7e76d971a60533817048d7 | SOCRadar | 2023-01-31 |
| 1807549af1c8fdc5b04c564f4026e41790c554f339514d326f8b55cb7b9b4f79 | SOCRadar | 2023-01-31 |
| 08eb4366fc0722696edb03981f00778701266a2e57c40cd2e9d765bf8b0a34d0 | SOCRadar | 2023-01-31 |
| a7c207b9b83648f69d6387780b1168e2f1eabd23ae6e162dd700ae8112f8b96c | SOCRadar | 2023-01-31 |
| 6310a2063687800559ae9d65cff21b0a | SOCRadar | 2023-01-31 |
| 01242b35b6def71e42cc985e97d618e2fabd616b16d23f7081d575364d09ca74 | SOCRadar | 2023-01-31 |
| 2eb3ef8a7a2c498e87f3820510752043b20cbe35b0cbd9af3f69e8b8fe482676 | SOCRadar | 2023-01-31 |
| f5db51115fa0c910262828d0943171d640b4748e51c9a140d06ea81ae6ea1710 | SOCRadar | 2023-01-31 |
| 7b6f996cc1ad4b5e131e7bf9b1c33253 | SOCRadar | 2023-01-31 |
| 23cea76078dd3829bd2b7e00f2bfe2ad | SOCRadar | 2023-01-31 |
| 7c003b4f8b3c0ab0c3f8cb933e93d301 | SOCRadar | 2023-01-31 |
| c9d3b29e0b7662dafc6a1839ad54a6fb | SOCRadar | 2023-01-31 |
| 8e64bacaf40110547b334eadcb0792bdc891d7ae298fbfff1367125797b6036b | SOCRadar | 2023-01-31 |
| b9afe016dbdba389000b01ce7645e7eea1b0a50827cded1cbaa48fbc715197bb | SOCRadar | 2023-01-31 |
| 0c2ffed470e954d2bf22807ba52c1ffd1ecce15779c0afdf15c292e3444cf674 | SOCRadar | 2023-01-31 |
| ab1ed31825763c481f54bd8a94d73777 | SOCRadar | 2023-01-31 |
| 1f842f84750048bb44843c277edeaa8469697e97c4dbf8dc571ec552266bec9f | SOCRadar | 2023-01-31 |
| 86ed4544eeca78dc64881a916fe1e1f73dc17f7b | SOCRadar | 2023-01-31 |
| 250cb957728dba0f3ae2c1c1e9bae241 | SOCRadar | 2023-01-31 |
| 8b8dff5d30802fd79b76ee1531e7d050184a07570201ef1cd83a7bb8fa627cb0 | SOCRadar | 2023-01-31 |
| 1d142c36c6cdd393fe543a6b7782f25a9cbafca17a1cfa0f3fc0f5a9431dbf3f | SOCRadar | 2023-01-31 |
| d1ea4f54c19d332b01553fa8e9a838c2a4dabfb1 | SOCRadar | 2023-01-31 |
| 8284421bbb94f3c37f94899cdcd19afd | SOCRadar | 2023-01-31 |
| b160bd46b6efc6d79bfb76cf3eeacca2300050248969decba139e9e1cbeebf53 | SOCRadar | 2023-01-31 |
| 3252965013ec861567510d54a97446610edba5da88648466de6b3145266386d9 | SOCRadar | 2023-01-31 |
| 236f5de8620a6255f9003d054f08574b | SOCRadar | 2023-01-31 |
| 4fc9202ff84ef84b8c5e6140b66ac3d04570daf886a7f1ae31661ade882f963e | SOCRadar | 2023-01-31 |
| 068117b406940ac510ed59efd1d7c7651f645a31bd70db6de16aba12c055aae6 | SOCRadar | 2023-01-31 |
| 79d6b1b6b1ecb446b0f49772bf4da63fcec6f6bfc7c2e1f4924cb7acbb3b4f53 | SOCRadar | 2023-01-31 |
| 8a3d71c668574ad6e7406d3227ba5adc5a230dd3057edddc4d0ec5f8134d76c3 | SOCRadar | 2023-01-31 |
| 867d41458d94e985f6b3e2bae1dfb75e14cbc57f | SOCRadar | 2023-01-31 |
| 62d99110a03c33157a2c844ed5ddec11 | SOCRadar | 2023-01-31 |
| 0d5e3483299242bf504bd3780487f66f2ec4f48a7b38baa6c6bc8ba16e4fb605 | SOCRadar | 2023-01-31 |
| 01971269ca3083f292f6978511b51a0f90eb1ddb | SOCRadar | 2023-01-31 |
| 2896c334f4ef21aec24596ae13f9b692 | SOCRadar | 2023-01-31 |
| bff4dd37febd5465e0091d9ea68006be475c0191bd8c7a79a44fbf4b99544ef1 | SOCRadar | 2023-01-31 |
| 4306c5d152cdd86f3506f91633ef3ae7d8cf0dd25f3e37bec43423c4742f4c42 | SOCRadar | 2023-01-31 |
| f1103e627311e73d5f29e877243e7ca203292f9419303c661aec57745eb4f26c | SOCRadar | 2023-01-31 |
| 8a06c836c05537fcd8c600141073132d28e1172d | SOCRadar | 2023-01-31 |
| 6d5ca42906c60caa7d3e0564b011d20b87b175cbd9d44a96673b46a82b07df68 | SOCRadar | 2023-01-31 |
| 7d82030186936aa9fb21256d9593d992 | SOCRadar | 2023-01-31 |
| f7013ce417fcba0f36c4b9bf5f8f6e0e2b14d6ed33ff4d384c892773508e932e | SOCRadar | 2023-01-31 |
| 03c835b684b21ded9a4ab285e4f686a3 | SOCRadar | 2023-01-31 |
| 8bebb8830366bd649c488903ef8f4e166965276d | SOCRadar | 2023-01-31 |
| c646199a9799b6158de419b1b7e36b46c7b7413d6c35bfffaeaa8700b2dcc427 | SOCRadar | 2023-01-31 |
| 246dfe16a9248d7fb90993f6f28b0ebe87964ffd2dcdb13105096cde025ca614 | SOCRadar | 2023-01-31 |
| 6345ac3f61b9f4ce64e82d3896baf1fa | SOCRadar | 2023-01-31 |
| 2841848ef59dfe7137e15119e4c9ce5e873e3607 | SOCRadar | 2023-01-31 |
| 25a089f2082a5fcb0f4c1a12724a5521 | SOCRadar | 2023-01-31 |
| ba83831700a73661f99d38d7505b5646 | SOCRadar | 2023-01-31 |
| 5d304ea1a9f3c8fbe147a74b64f3390e848ba04a | SOCRadar | 2023-01-31 |
| 241ce8af441db2d61f3eb7852f434642739a6cc3 | SOCRadar | 2023-01-31 |
| 0cf6399db55d40bc790a399c6bbded375f5a278dc57a143e4b21ea3f402f551f | SOCRadar | 2023-01-31 |
| 4b5eefa1727b97b6f773be3937a8cc390f0434ddc2f01dc24b68b690fafbcc93 | SOCRadar | 2023-01-31 |
| 88d13669a994d2e04ec0a9940f07ab8aab8563eb845a9c13f2b0fec497df5b17 | SOCRadar | 2023-01-31 |
| 571f8db67d463ae80098edc7a1a0cad59153ce6592e42d370a45df46f18a4ad8 | SOCRadar | 2023-01-31 |
| 9b546bd99272cf4689194d698c830a2510194722 | SOCRadar | 2023-01-31 |
| 209ffbc8ba1e93167bca9b67e0ad3561c065595d | SOCRadar | 2023-01-31 |
| b14341b1ffe9e2730394b9066c6829b4e2f59a4234765ae2e97cfc6d4593730a | SOCRadar | 2023-01-31 |
| 25ebe54beb3c422ccd2d90aa8ae89087f71b0bed | SOCRadar | 2023-01-31 |
| 72a60d799ae9e4f0a3443a2f96fb4896 | SOCRadar | 2023-01-31 |
| abe9635adbfee2d2fbaea140625c49abe3baa29c44fb53a65a9cda02121583ee | SOCRadar | 2023-01-31 |
| aa3f37a75d3ba2ee74955c06eb308ad0cd6bca2e | SOCRadar | 2023-01-31 |
| 5cd95b34782ca5acf8a34d9dc184cb880a19b6edcaf4a4553fa0619b597c2f50 | SOCRadar | 2023-01-31 |
| 74fbf3cc44dd070bd5cb87ca2eed03e1bbeec4fec644a25621052f0a73abbe84 | SOCRadar | 2023-01-31 |
| a7172aef66bb12e1bb40a557bb41e607 | SOCRadar | 2023-01-31 |
| a17c21b909c56d93d978014e63fb06926eaea8e7 | SOCRadar | 2023-01-31 |
| 857f28b8fe31cf5db6d45d909547b151a66532951f26cda5f3320d2d4461b583 | SOCRadar | 2023-01-31 |
| f869e8fbd8aa1f037ad862cf6e8bbbf797ff49556fb100f2197be4ee196a89ae | SOCRadar | 2023-01-31 |
| bd270853db17f94c2b8e4bd9fa089756a147ed45cbc44d6c2b0c78f361978906 | SOCRadar | 2023-01-31 |
| af4523186fe4a5e2833bbbe14939d8c3bd352a47a2f77592d8adcb569621ce02 | SOCRadar | 2023-01-31 |
| 310afba59ab8e1bda3ef750a64bf39133e15c89e8c7cf4ac65ee463b26b136ba | SOCRadar | 2023-01-31 |
| 3fe1a3aaca999a5db936843c9bdfea14 | SOCRadar | 2023-01-31 |
| 9d3b268416d3fab4322cc916d32e0b2e8fa0de370acd686873d1522306124fd2 | SOCRadar | 2023-01-31 |
| 75b55bb34dac9d02740b9ad6b6820360 | SOCRadar | 2023-01-31 |
| fd87ca28899823b37b2c239fbbd236c555bcab7768d67203f86d37ede19dd975 | SOCRadar | 2023-01-31 |
| ecefd9bb8b3783a81ab934b44eb3d84df5e58f0289f089ef6760264352cf878a | SOCRadar | 2023-01-31 |
| a839b2a598fc598044f9814873d7fc84 | SOCRadar | 2023-01-31 |
| 09e04ba053edcf4ca38541cbd735568945a5948d | SOCRadar | 2023-01-31 |
| Ipv4s | Source | Last Update |
|---|---|---|
| 37.44.253.21 | SOCRadar | 2023-01-31 |
| 217.79.43.148 | SOCRadar | 2023-01-31 |
| 79.141.169.220 | SOCRadar | 2023-01-31 |
| 31.184.198.111 | SOCRadar | 2023-01-31 |
| 204.13.164.118 | SOCRadar | 2023-01-31 |
| 192.137.100.96 | SOCRadar | 2023-01-31 |
| 154.35.175.225 | SOCRadar | 2023-01-31 |
| 222.252.53.33 | SOCRadar | 2023-01-31 |
| 64.52.169.174 | SOCRadar | 2023-01-31 |
| 216.45.55.3 | SOCRadar | 2023-01-31 |
| 31.184.198.84 | SOCRadar | 2023-01-31 |
| 31.184.198.90 | SOCRadar | 2023-01-31 |
| 141.98.87.124 | SOCRadar | 2023-01-31 |
| 159.203.70.39 | SOCRadar | 2023-01-31 |
| 37.120.193.123 | SOCRadar | 2023-01-31 |
| 31.44.184.84 | SOCRadar | 2023-01-31 |
| 31.184.198.74 | SOCRadar | 2023-01-31 |
| 185.153.199.168 | SOCRadar | 2023-01-31 |
| 69.30.232.138 | SOCRadar | 2023-01-31 |
| 62.210.54.235 | SOCRadar | 2023-01-31 |
| 64.235.39.82 | SOCRadar | 2023-01-31 |
| 107.189.10.143 | SOCRadar | 2023-01-31 |
| 185.153.199.163 | SOCRadar | 2023-01-31 |
| 128.31.0.39 | SOCRadar | 2023-01-31 |
| 131.188.40.189 | SOCRadar | 2023-01-31 |
| 37.120.247.39 | SOCRadar | 2023-01-31 |
| 103.27.203.197 | SOCRadar | 2023-01-31 |
| 38.108.119.121 | SOCRadar | 2023-01-31 |
| 31.184.198.82 | SOCRadar | 2023-01-31 |
| 31.44.184.100 | SOCRadar | 2023-01-31 |
| 92.222.172.39 | SOCRadar | 2023-01-31 |
| 192.137.101.205 | SOCRadar | 2023-01-31 |
| 209.76.253.84 | SOCRadar | 2023-01-31 |
| 157.245.70.127 | SOCRadar | 2023-01-31 |
| 31.184.198.80 | SOCRadar | 2023-01-31 |
| 104.238.134.63 | SOCRadar | 2023-01-31 |
| 209.127.187.245 | SOCRadar | 2023-01-31 |
| 86.59.21.38 | SOCRadar | 2023-01-31 |
| 216.45.55.30 | SOCRadar | 2023-01-31 |
| 84.17.52.135 | SOCRadar | 2023-01-31 |
| 185.153.199.164 | SOCRadar | 2023-01-31 |
| 194.109.206.212 | SOCRadar | 2023-01-31 |
| 31.184.198.83 | SOCRadar | 2023-01-31 |
| 108.170.31.115 | SOCRadar | 2023-01-31 |
| 199.58.81.140 | SOCRadar | 2023-01-31 |
| 185.153.199.169 | SOCRadar | 2023-01-31 |
| 149.255.35.131 | SOCRadar | 2023-01-31 |
| 31.184.194.42 | SOCRadar | 2023-01-31 |
| 170.39.212.69 | SOCRadar | 2023-01-31 |
| 193.34.167.17 | SOCRadar | 2023-01-31 |
| 195.54.160.149 | SOCRadar | 2023-01-31 |
| 45.32.229.66 | SOCRadar | 2023-01-31 |
| 193.23.244.244 | SOCRadar | 2023-01-31 |
| 213.32.39.43 | SOCRadar | 2023-01-31 |
| 45.91.83.176 | SOCRadar | 2023-01-31 |
| 45.164.21.13 | SOCRadar | 2023-01-31 |
| 31.184.198.86 | SOCRadar | 2023-01-31 |
| 185.153.199.162 | SOCRadar | 2023-01-31 |
| 31.184.192.44 | SOCRadar | 2023-01-31 |
| 45.86.162.34 | SOCRadar | 2023-01-31 |
| 31.44.184.82 | SOCRadar | 2023-01-31 |
| 46.17.106.230 | SOCRadar | 2023-01-31 |
| 212.192.241.230 | SOCRadar | 2023-01-31 |
| 31.184.198.85 | SOCRadar | 2023-01-31 |
| 192.137.101.46 | SOCRadar | 2023-01-31 |
| 92.222.172.172 | SOCRadar | 2023-01-31 |
| 94.103.9.79 | SOCRadar | 2023-01-31 |
| 185.153.199.176 | SOCRadar | 2023-01-31 |
| 23.227.198.246 | SOCRadar | 2023-01-31 |
| 103.114.163.197 | SOCRadar | 2023-01-31 |
| 167.71.175.165 | SOCRadar | 2023-01-31 |
| 31.184.199.82 | SOCRadar | 2023-01-31 |
| 171.25.193.9 | SOCRadar | 2023-01-31 |
| 104.217.8.100 | SOCRadar | 2023-01-31 |
| 192.137.100.98 | SOCRadar | 2023-01-31 |
| 144.172.83.13 | SOCRadar | 2023-01-31 |
| Cves | Source | Last Update |
|---|---|---|
| CVE-2022-24521 | SOCRadar | 2023-01-31 |
| CVE-2020-1472 | SOCRadar | 2023-01-31 |
| Emails | Source | Last Update |
|---|---|---|
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| [email protected] | SOCRadar | 2023-01-31 |
| Domains | Insert Date |
|---|
MITRE ATT&CK TECHNIQUES
Cuba ransomware actors use the ATT&CK techniques listed in Table 6. Note: For details on TTPs listed in the table, see FBI Flash Indicators of Compromise Associated with Cuba Ransomware.
Resource Development | ||
Technique Title | ID | Use |
Compromise Infrastructure: Domains | Cuba ransomware actors use compromised networks to conduct their operations. | |
Initial Access | ||
Technique Title | ID | Use |
Valid Accounts | Cuba ransomware actors have been known to use compromised credentials to get into a victim’s network. | |
External Remote Services | Cuba ransomware actors may leverage external-facing remote services to gain initial access to a victim’s network. | |
Exploit Public-Facing Application | Cuba ransomware actors are known to exploit vulnerabilities in public-facing systems. | |
Phishing | Cuba ransomware actors have sent phishing emails to obtain initial access to systems. | |
Execution | ||
Technique Title | ID | Use |
Command and Scripting Interpreter: PowerShell | Cuba ransomware actors have used PowerShell to escalate privileges. | |
Software Deployment Tools | Cuba ransomware actors use Hancitor as a tool to spread malicious files throughout a victim’s network. | |
Privilege Escalation | ||
Technique Title | ID | Use |
Exploitation for Privilege Escalation | Cuba ransomware actors have exploited ZeroLogon to gain administrator privileges. | |
Defense Evasion | ||
Technique Title | ID | Use |
Impair Defenses: Disable or Modify Tools | Cuba ransomware actors leveraged a loader that disables security tools within the victim network. | |
Lateral Movement | ||
Technique Title | ID | Use |
Remote Services Session: RDP Hijacking | Cuba ransomware actors used RDP sessions to move laterally. | |
Credential Access | ||
Technique Title | ID | Use |
Credential Dumping: LSASS Memory | Cuba ransomware actors use LSASS memory to retrieve stored compromised credentials. | |
Steal or Forge Kerberos Tickets: Kerberoasting | Cuba ransomware actors used the Kerberoasting technique to identify service accounts linked to active directory. | |
Command and Control | ||
Technique Title | ID | Use |
Proxy: Manipulate Command and Control Communications | Industrial Spy ransomware actors use HTTP/HTTPS proxy via a C2 server to direct traffic to avoid direct connection. | |
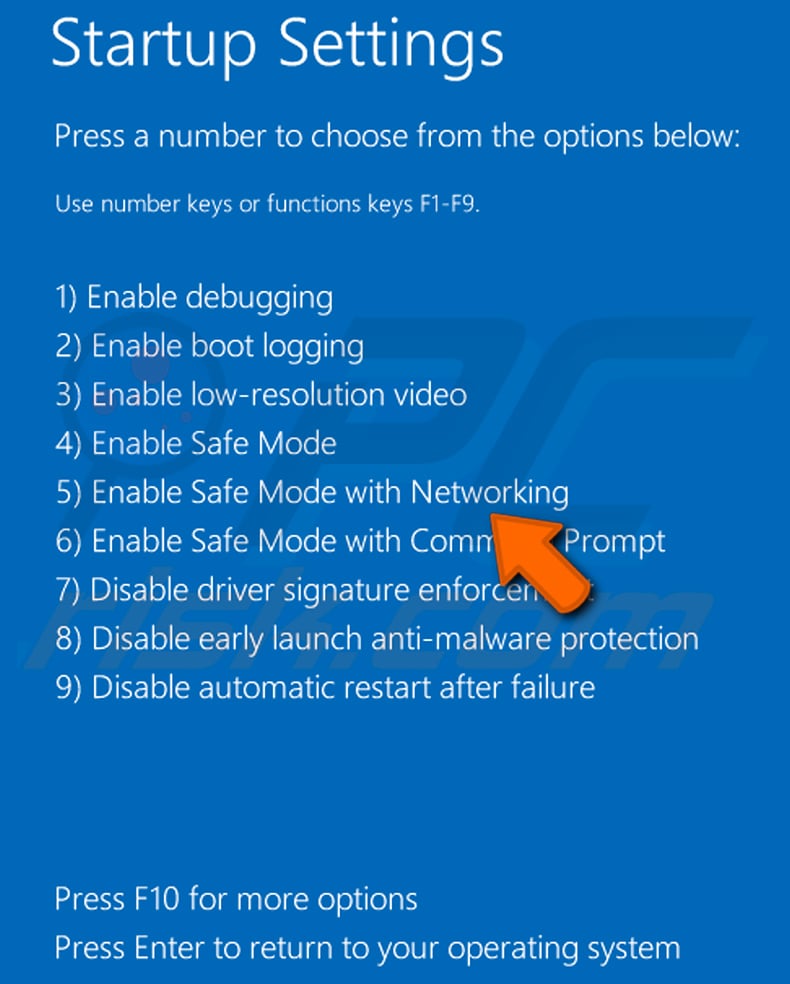
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
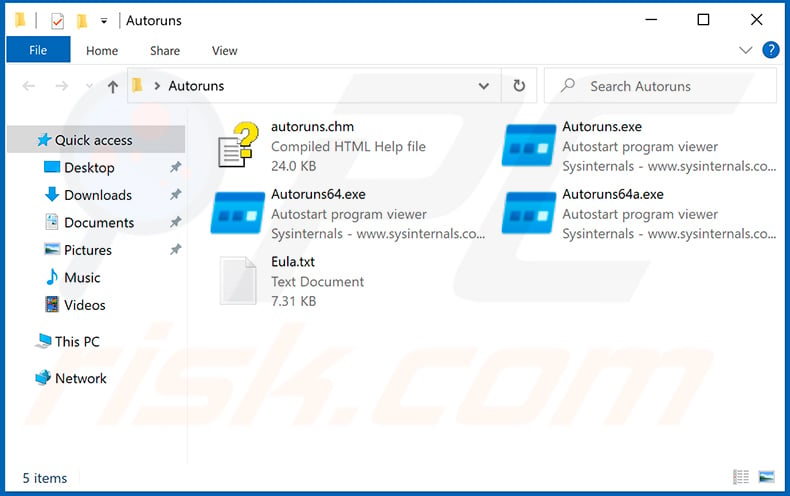
Extract the downloaded archive and run the Autoruns.exe file.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
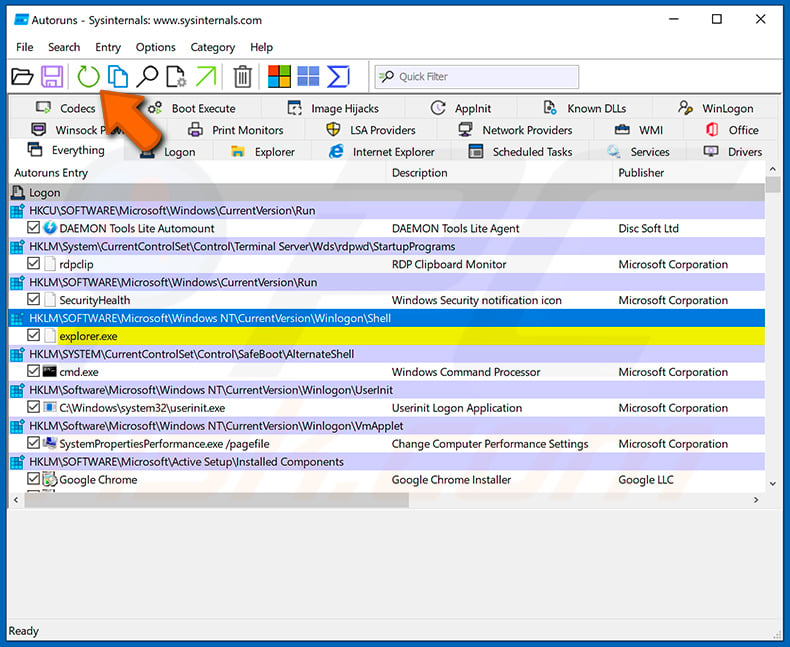
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
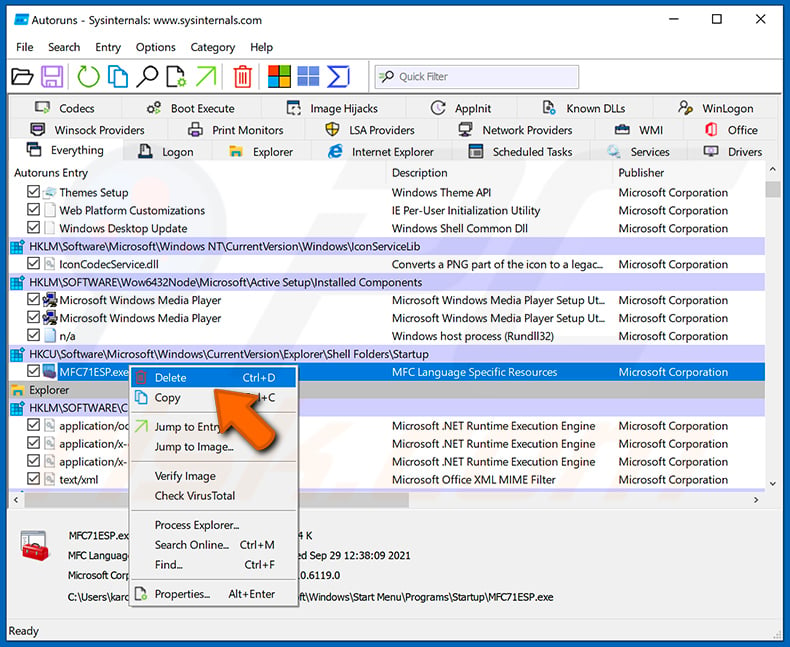
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
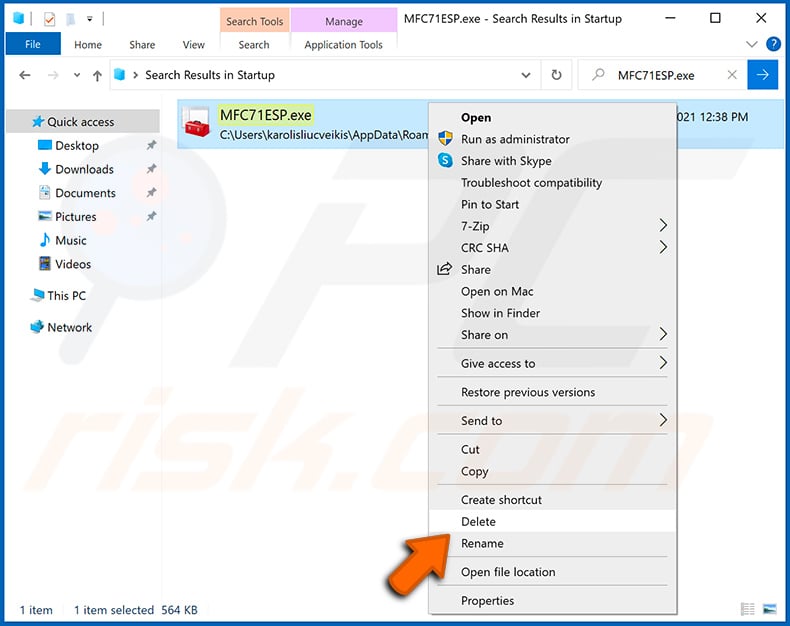
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
| File Name | Description | Actions |
|---|---|---|
| 0408-Threat-ReportV17.pdf | DELIVERING ACTIONABLE AND CONTEXTUALIZED INTELLIGENCE TO INCREASE CYBER RESILIENCE |
| APT Name | Aliases | Target Countries | Source Countries | Total IOCs |
|---|---|---|---|---|
| RomCom |
Storm-0978
|
|
None |
1066
|








































