OneDrive Pastejacking: The Sneaky Phishing and Downloader Campaign
OneDrive Pastejacking is a sneaky phishing and downloader campaign that targets users by injecting malicious commands during copy-paste operations. This attack deceives users into downloading harmful content to their systems. This type of attack exploits security vulnerabilities and can put your sensitive data at risk.
| Domains | Source | Last Update |
|---|---|---|
| clarify_27-May_202017.html | SOCRadar | 2024-08-27 |
| clarify_27-May_690357.html | SOCRadar | 2024-08-27 |
| Clarify_15-june_586190.html | SOCRadar | 2024-08-27 |
| Hashes | Source | Last Update |
|---|---|---|
| 763d557c3e4c57f7d6132a444a930386 | SOCRadar | 2024-08-27 |
| d6faa6bd1732517f260d94feb3cdbfc2 | SOCRadar | 2024-08-27 |
| 2df579460a76631836d108578af4caa5 | SOCRadar | 2024-08-27 |
| ef082ddcbf5c94f1da1d2026d36b6b3f | SOCRadar | 2024-08-27 |
| cf16271bfe826db5ef0c1a67433a619f | SOCRadar | 2024-08-27 |
| 1152103edc64ddee7ea4e07cd5dd78ae | SOCRadar | 2024-08-27 |
| C56b5f0201a3b3de53e561fe76912bfd | SOCRadar | 2024-08-27 |
| dfa96717b69fa69d264a60b9de36f078 | SOCRadar | 2024-08-27 |
| beb8a50f67424c3b70cb56fc8833d246 | SOCRadar | 2024-08-27 |
| 0852c3e7903dd3b1db6a6b232c33a25a | SOCRadar | 2024-08-27 |
| 04cdff477585cb0747ecd20052f03c2e | SOCRadar | 2024-08-27 |
| cac3c4005f952293b38302199494759a | SOCRadar | 2024-08-27 |
| deaf955bbf5d66db200e366ae3563eab | SOCRadar | 2024-08-27 |
| 328110e6c36cd70edac6bea395c40b18 | SOCRadar | 2024-08-27 |
| a1846e262d900f56f4a7d5f51100ec44 | SOCRadar | 2024-08-27 |
| 7133ae7dd452aa6469c85e236a59159e | SOCRadar | 2024-08-27 |
| e0768bce522927eb89f74750e09f2a1c | SOCRadar | 2024-08-27 |
| 404bd47f17d482e139e64d0106b8888d | SOCRadar | 2024-08-27 |
| b183269587055f35cb23d2d33ff3f5fa | SOCRadar | 2024-08-27 |
| d524addd18d8014d72abb9dd172e782d | SOCRadar | 2024-08-27 |
| 1ff108f1bfb39b21db5f1d4f7ad56bf2 | SOCRadar | 2024-08-27 |
| fca4c1908da892161bbf09f1437dade7 | SOCRadar | 2024-08-27 |
| 7f5c82eadbaadec6ba2b004fbafa9a31 | SOCRadar | 2024-08-27 |
| 363b4f9fdb1e2a5926037b207caecfe5 | SOCRadar | 2024-08-27 |
| 0e36cf2719295596da0c7ef10b11df15 | SOCRadar | 2024-08-27 |
| 4341f0372eda93afce82908014f420d9 | SOCRadar | 2024-08-27 |
| 253cdeabd5e429832f9bbd7f37dd0798 | SOCRadar | 2024-08-27 |
| 7a7d09b4bcd75bc7d7badd3c117596f7 | SOCRadar | 2024-08-27 |
| d0ad617ed1812822eebc9592d49a575c | SOCRadar | 2024-08-27 |
| 55cf60a640fc773a7c38de9c5e44da30 | SOCRadar | 2024-08-27 |
| ef9d05bb8a24bec1d94123c90b1268bb | SOCRadar | 2024-08-27 |
| eed2174f5b87d58b1b0baea0e509e141 | SOCRadar | 2024-08-27 |
| 30997b5e63297c58c4f9fe73c8c200ac | SOCRadar | 2024-08-27 |
| 1eda7707ef4e03f0b1ab6b6fb96757a6 | SOCRadar | 2024-08-27 |
| 96bb795d111717109fac22f8433c7e27 | SOCRadar | 2024-08-27 |
| Ipv4s | Source | Last Update |
|---|
| Cves | Source | Last Update |
|---|
| Emails | Source | Last Update |
|---|
| Domains | Insert Date |
|---|
Mitigations
REMEDIATION
Detection
CONCLUSION
The OneDrive Pastejacking campaign showcases the advanced methods used by cybercriminals, who rely on social engineering to take advantage of users' trust and emotions. By tricking users into fixing a fake DNS error, the attackers manage to execute malicious payloads through harmless-looking PowerShell commands. This campaign underscores the necessity for ongoing alertness, comprehensive cybersecurity education, and stringent security measures within corporate settings. It's crucial for organizations to proactively educate their staff and fortify their defenses to reduce the threats posed by these sophisticated phishing and downloader attacks. The worldwide impact of this campaign emphasizes the need for global cooperation and intelligence sharing to effectively address these persistent cyber threats. For more information on this and other campaigns, visit the SOCRadar Labs campaign page.
| File Name | Description | Actions |
|---|
| APT Name | Aliases | Target Countries | Source Countries | Total IOCs |
|---|
D-Link, a prominent networking hardware manufacturer, has issued a critical security advisory urging users to retire and replace several end-of-life VPN router models due to a severe remote code execution (RCE) vulnerability. The affected devices include all hardware revisions of DSR-150, DSR-150N, DSR-250, DSR-250N, DSR-500N, and DSR-1000N routers. The vulnerability, discovered by security researcher ‘delsploit,’ […]
The post Multiple D-Link End-of-Life Routers Vulnerabilities Let Attackers Execute Remote Code appeared first on Cyber Security News.
Executive Summary
The Cybersecurity and Infrastructure Security Agency (CISA) conducted a red team assessment (RTA) at the request of a critical infrastructure organization. During RTAs, CISA’s red team simulates real-world malicious cyber operations to assess an organization’s cybersecurity detection and response capabilities. In coordination with the assessed organization, CISA is releasing this Cybersecurity Advisory to detail the red team’s activity—including their tactics, techniques, and procedures (TTPs) and associated network defense activity. Additionally, the advisory contains lessons learned and key findings from the assessment to provide recommendations to network defenders and software manufacturers for improving their organizations’ and customers’ cybersecurity posture.
Within this assessment, the red team (also referred to as ‘the team’) gained initial access through a web shell left from a third party’s previous security assessment. The red team proceeded to move through the demilitarized zone (DMZ) and into the network to fully compromise the organization’s domain and several sensitive business system (SBS) targets. The assessed organization discovered evidence of the red team’s initial activity but failed to act promptly regarding the malicious network traffic through its DMZ or challenge much of the red team’s presence in the organization’s Windows environment.
The red team was able to compromise the domain and SBSs of the organization as it lacked sufficient controls to detect and respond to their activities. The red team’s findings illuminate lessons learned for network defenders and software manufacturers about how to respond to and reduce risk.
- Lesson Learned: The assessed organization had insufficient technical controls to prevent and detect malicious activity. The organization relied too heavily on host-based endpoint detection and response (EDR) solutions and did not implement sufficient network layer protections.
- Lesson Learned: The organization’s staff require continuous training, support, and resources to implement secure software configurations and detect malicious activity. Staff need to continuously enhance their technical competency, gain additional institutional knowledge of their systems, and ensure they are provided sufficient resources by management to have the conditions to succeed in protecting their networks.
- Lesson Learned: The organization’s leadership minimized the business risk of known attack vectors for the organization. Leadership deprioritized the treatment of a vulnerability their own cybersecurity team identified, and in their risk-based decision-making, miscalculated the potential impact and likelihood of its exploitation.
To reduce risk of similar malicious cyber activity, CISA encourages critical infrastructure organizations to apply the recommendations in the Mitigations section of this advisory to ensure security processes and procedures are up to date, effective, and enable timely detection and mitigation of malicious activity.
This document illustrates the outsized burden and costs of compensating for insecure software and hardware borne by critical infrastructure owners and operators. The expectation that owners and operators should maintain the requisite sophisticated cyber defense skills creates undue risk. Technology manufacturers must assume responsibility for product security. Recognizing that insecure software contributes to these identified issues, CISA urges software manufacturers to embrace Secure by Design principles and implement the recommendations in the Mitigations section of this advisory, including those listed below:
- Embed security into product architecture throughout the entire software development lifecycle (SDLC).
- Eliminate default passwords.
- Mandate MFA, ideally phishing-resistant MFA, for privileged users and make MFA a default, rather than opt-in, feature.
Download the PDF version of this report:
INTRODUCTION
CISA has authority to—upon request—provide analyses, expertise, and other technical assistance to critical infrastructure owners and operators and provide operational and timely technical assistance to federal and non-federal entities with respect to cybersecurity risks. (See generally 6 U.S.C. §§ 652[c][5], 659[c][6]). The target organization for this assessment was a critical infrastructure organization in the United States. After receiving a request for an RTA from the organization and coordinating the high-level details of the engagement, CISA conducted the RTA over approximately a three-month period.
During RTAs, a CISA red team simulates real-world threat actors to assess an organization’s cybersecurity detection and response capabilities. During Phase I, the red team attempts to gain and maintain persistent access to an organization’s enterprise network, avoid detection, evade defenses, and access SBSs. During Phase II, the red team attempts to trigger a security response from the organization’s people, processes, and/or technology.
Drafted in coordination with the assessed organization, this advisory details the red team’s activity and TTPs, associated network defense activity, and lessons learned to provide network defenders with recommendations for improving an organization’s cybersecurity posture. The advisory also provides recommendations for software manufacturers to harden their customer networks against malicious activity and reduce the likelihood of domain compromise.
TECHNICAL DETAILS
Note: This advisory uses the MITRE ATT&CK® Matrix for Enterprise framework, version 16. See Appendix: MITRE ATT&CK Tactics and Techniques for a table of the red team’s activity mapped to MITRE ATT&CK tactics and techniques.
Phase I: Red Team Cyber Threat Activity
Overview
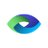
The CISA red team operated without prior knowledge of the organization’s technology assets and began the assessment by conducting open source research on the target organization to gain information about its network [T1590], defensive tools [T1590.006], and employees [T1589.003]. The red team designed spearphishing campaigns [T1566] tailored to employees most likely to communicate with external parties. The phishing attempts were ultimately unsuccessful—targets ran the payloads [T1204], but their execution did not result in the red team gaining access into the network.
After the failed spearphishing campaigns, the red team continued external reconnaissance of the network [T1595] and discovered a web shell [T1505.003] left from a previous Vulnerability Disclosure Program (VDP). The red team used this for initial access [TA0001] and immediately reported it to the organization’s trusted agents (TAs). The red team leveraged that access to escalate privileges [TA0004] on the host, discover credential material on a misconfigured Network File System (NFS) share [T1552.001], and move from a DMZ to the internal network [TA0008].
With access to the internal network, the red team gained further access to several SBSs. The red team leveraged a certificate for client authentication [T1649] they discovered on the NFS share to compromise a system configured for Unconstrained Delegation. This allowed the red team to acquire a ticket granting ticket (TGT) for a domain controller [T1558.001], used to further compromise the domain. The red team leveraged this level of access to exploit SBS targets provided by the organization’s TAs.
The assessed organization detected much of the red team’s activity in their Linux infrastructure after CISA alerted them via other channels to the vulnerability the red team used for initial access. Once given an official notification of a vulnerability, the organization’s network defenders began mitigating the vulnerability. Network defenders removed the site hosting the web shell from the public internet but did not take the server itself offline. A week later, network defenders officially declared an incident once they determined the web shell was used to breach the internal network. For several weeks, network defenders terminated much of the red team’s access until the team maintained implants on only four hosts. Network defenders successfully delayed the red team from accessing many SBSs that required additional positioning, forcing the red team to spend time refortifying their access in the network. Despite these actions, the red team was still able to access a subset of SBSs. Eventually, the red team and TAs decided that the network defenders would stand down to allow the red team to continue its operations in a monitoring mode. In monitoring mode, network defenders would report what they observed of the red team’s access, but not continue to block and terminate it.
See Figure 1 for a timeline of the red team’s activity with key points access. See the following sections for additional details, including the red team’s TTPs.
Initial Access
Following an unsuccessful spearphishing campaign, the red team gained initial access to the target by exploiting an internet-facing Linux web server [T1190] discovered through reconnaissance [TA0043] of the organization’s external internet protocol (IP) space [T1590.005].
The red team first conducted open source research [T1593] to identify information about the organization’s network, including the tools used to protect the network and potential targets for spearphishing. The red team looked for email addresses [T1589.002] and names to infer email addresses from the organization’s email syntax (discovered during reconnaissance). Following this action, the red team sent tailored spearphishing emails to 13 targets [T1566.002]. Of these 13 targets, one user responded and executed two malicious payloads [T1204.002]. However, the payloads failed to bypass a previously undiscovered technical control employed by the victim organization, preventing the red team’s first attempt to gain initial access.
To find an alternate pathway for initial access, the red team conducted reconnaissance with several publicly available tools, such as Shodan and Censys, to discover accessible devices and services on the internet [T1596.005]. The red team identified an old and unpatched service with a known XML External Entity (XXE) vulnerability and leveraged a public proof of concept to deploy a web shell. The associated product had an exposed endpoint—one that system administrators should typically block from the public internet—that allowed the red team to discover a preexisting web shell on the organization’s Linux web server. The preexisting web shell allowed the red team to run arbitrary commands on the server [T1059] as a user (WEBUSER1). Using the web shell, the red team identified an open internal proxy server [T1016] to send outbound communications to the internet via Hypertext Transfer Protocol Secure (HTTPS). The red team then downloaded [T1105] and executed a Sliver payload that utilized this proxy to establish command and control (C2) over this host, calling back to their infrastructure [TA0011].
Note: Because the web shell and unpatched vulnerability allowed actors to easily gain initial access to the organization, the CISA red team determined this was a critical vulnerability. CISA reported both the vulnerability and the web shell to the organization in an official vulnerability notification so the organization could remediate both issues. Following this notification, the victim organization initiated threat hunting activities, detecting some of the red team’s activity. The TAs determined that network defenders had previously identified and reported the vulnerability but did not remediate it. Further, the TAs found that network defenders were unaware of the web shell and believed it was likely leftover from prior VDP activity. See the Defense Evasion and Victim Network Defense Activities section for more information.
Linux Infrastructure Compromise
Local Privilege Escalation and Credential Access
The red team then moved laterally from the web server to the organization’s internal network using valid accounts [T1078] as the DMZ was not properly segmented from the organization’s internal domain.
The red team acquired credentials [TA0006] by first escalating privileges on the web server. The team discovered that WEBUSER1 had excessive sudo rights, allowing them to run some commands as root commands without a password. They used these elevated rights to deploy a new callback with root access [T1548.003].
With root access to the web server, the team had full access to the organization’s directories and files on a NFS share with no_root_squash enabled. If no_root_squash is used, remote root users can read and change any file on the shared file system and leave a trojan horse [T1080] for other users to inadvertently execute. On Linux operating systems this option is disabled by default, yet the organization enabled it to accommodate several legacy systems. The organization’s decision to enable the no_root_squash option allowed the red team to read all the files on the NFS share once it escalated its privileges on a single host with the NFS share mounted. This NFS share hosted the home directories of hundreds of Linux users—many of which had privileged access to one or more servers—and was auto-mounted when those users logged into Linux hosts in the environment.
The red team used its escalated privileges to search for private certificate files, Secure Shell (SSH) private keys, passwords, bash command histories [T1552.003], and other sensitive data across all user files on the NFS share [T1039]. The team initially obtained 61 private SSH keys [T1552.004] and a file containing valid cleartext domain credentials (DOMAINUSER1) that the team used to authenticate to the organization’s domain [T1078.002].
Linux Command and Control
In the organization’s Linux environment, the red team leveraged HTTPS connections for C2 [T1071.001]. Most of the Linux systems could not directly access the internet, but the red team circumvented this by leveraging an open internal HTTPS proxy [T1090.001] for their traffic.
Lateral Movement and Persistence
The red team’s acquisition of SSH private keys generated for user and service accounts facilitated unrestricted lateral movement to other Linux hosts [T1021.004]. This acquisition included two highly privileged accounts with root access to hundreds of servers. Within one week of initial access, the team moved to multiple Linux servers and established persistence [TA0003] on four. The team used a different persistence mechanism on each Linux host, so network defenders would be less likely to discover the red team’s presence on all four hosts. The team temporarily backdoored several scripts run at boot time to maintain persistence [T1037], ensuring the original versions of the scripts were re-enabled once the team successfully achieved persistence. Some of the team’s techniques included modifying preexisting scripts run by the cron utility [T1053.003] and ifup-post scripts [T1037.003].
Of note, the team gained root access to an SBS-adjacent infrastructure management server that ran Ansible Tower. Access to this Ansible Tower system [T1072] provided easy access to multiple SBSs. The team discovered a root SSH private key on the host, which allowed the team to move to six SBSs across six different sensitive IP ranges. A week after the team provided screenshots of root access to the SBSs to the TAs, the TAs deconflicted the red team’s access to the Ansible Tower system that network defenders discovered. The organization detected the compromise by observing abnormal usage of the root SSH private key. The root SSH private key was used to log into multiple hosts at times and for durations outside of preestablished baselines. In a real compromise, the organization would have had to shut down the server, significantly impacting business operations.
Windows Domain Controller Compromise
Approximately two weeks after gaining initial access, the red team compromised a Windows domain controller. This compromise allowed the team to move laterally to all domain-joined Windows hosts within the organization.
To first gain situational awareness about the organization’s environment, the red team exfiltrated Active Directory (AD) information [TA0010] from a compromised Linux host that had network access to a Domain Controller (DC). The team queried Lightweight Directory Access Protocol (Over SSL)—(LDAPS)—to collect information about users [T1087.002], computers [T1018], groups [T1069.002], access control lists (ACL), organizational units (OU), and group policy objects (GPO) [T1615]. Unfortunately, the organization did not have detections to monitor for anomalous LDAP traffic. A non-privileged user querying LDAP from the organization’s Linux domain should have alerted network defenders.
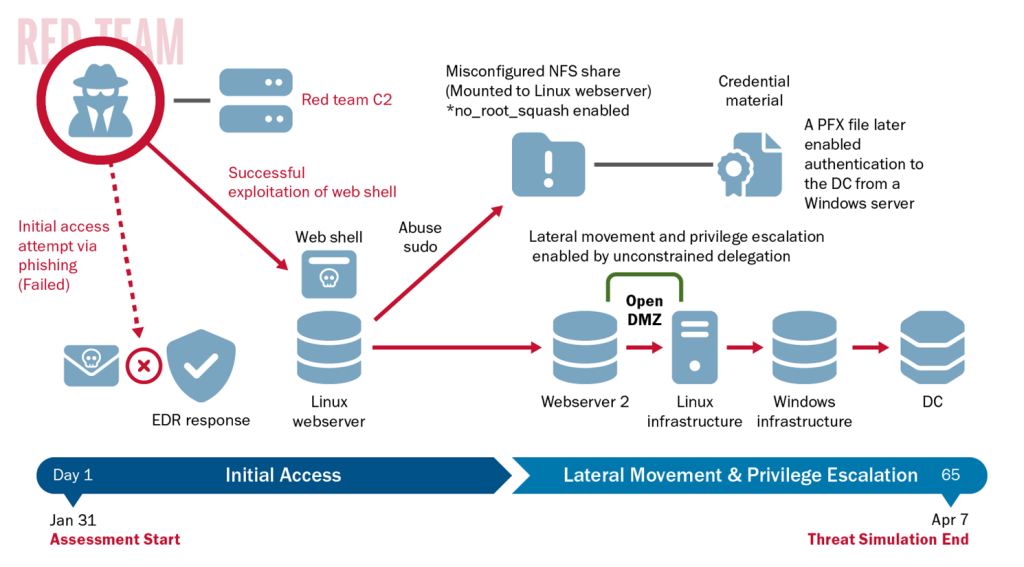
The red team observed a total of 42 hosts in AD that were not DCs, but had Unconstrained Delegation enabled. Hosts with Unconstrained Delegation enabled store the Kerberos TGTs of any user that authenticates to them. With sufficient privileges, an actor can obtain those tickets and impersonate associated users. A compromise of any of these hosts could lead to the escalation of privileges within the domain. Network defenders should work with system administrators to determine whether Unconstrained Delegation is necessary for their systems and limit the number of systems with Unconstrained Delegation unnecessarily enabled.
The red team observed insufficient network segmentation between the organization’s Linux and Windows domains. This allowed for Server Message Block (SMB) and Kerberos traffic to a DC and a domain server with Unconstrained Delegation enabled (UDHOST). The team discovered an unprotected Personal Information Exchange (.pfx) file on the NFS home share that they believed was for UDHOST based on its naming convention.
Equipped with the .pfx file, the red team used Rubeus—an open source toolset for Kerberos interaction and abuses—to acquire a TGT and New Technology Local Area Network Manager (NTLM) hash for UDHOST from the DC. The team then used the TGT to abuse the Server-for-User-to-Self (S4U2Self) Kerberos extension to gain administrative access to UDHOST.
The red team leveraged this administrative access to upload a modified version of Rubeus in monitor mode to capture incoming tickets [T1040] on UDHOST with Rubeus’ /monitor command. Next, the team ran DFSCoerce.py to force the domain controller to authenticate to UDHOST [T1187]. The team then downloaded the captured tickets from UDHOST.
With the DC’s TGT, the team used Domain Controller Sync (DCSync) through their Linux tunnels to acquire the hash of several privileged accounts—including domain, enterprise, and server administrators—and the critical krbtgt account [T1003.006].
Gaining access to AD is not unusual for most of CISA’s Red Team engagements, but it is rare to find network defenders who can secure and monitor it quickly and effectively.
Once the team harvested the credentials needed, they moved laterally to nearly any system in the Windows domain (see Figure 2) through the following steps (hereafter, this combination of techniques is referred to as the “Preferred Lateral Movement Technique”):
- The team either forged a golden ticket using the
krbtgthash or requested a valid TGT using the hashes they exfiltrated for a specific account before loading the ticket into their session for additional authentication. - The team dropped an inflated Dynamic Link Library (DLL) file associated with legitimate scheduled tasks on the organization’s domain.
- When the scheduled task executed on its own or through the red team’s prompting, the DLL hijack launched a C2 implant.
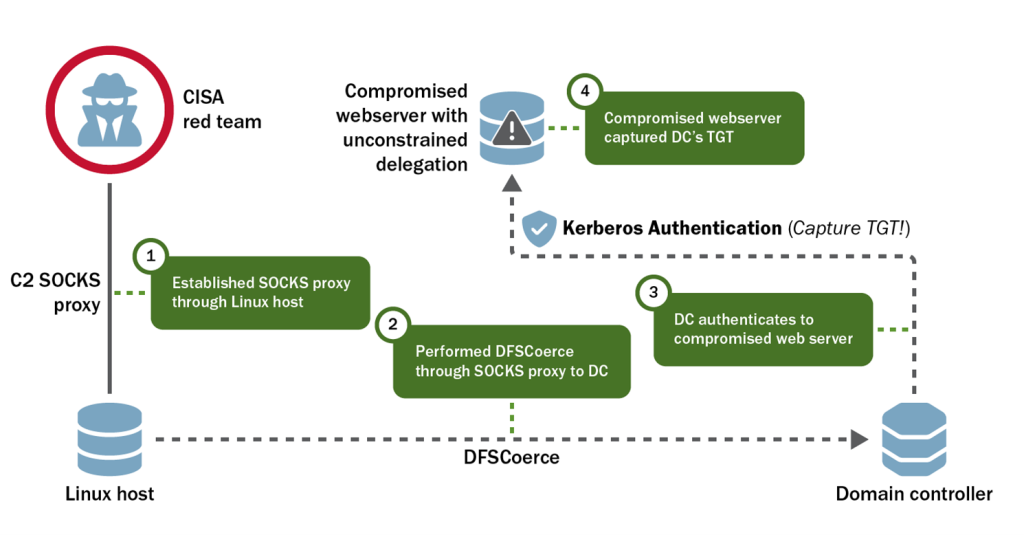
Windows Command and Control
The red team initially established C2 on a workstation over HTTPS before connecting to servers over SMB [T1071.002] in the organization’s Windows environment. To connect to certain SBSs later in its activity, the team again relied on HTTPS for C2.
Post-Exploitation Activity: Gaining Access to SBSs
After the red team gained persistent access to Linux and Windows systems across the organization’s networks, the team began post-exploitation activities and attempted to access SBSs. The TAs provided a scope of the organization’s Classless Inter-Domain Routing (CIDR) ranges that contained SBSs. The team gained root access to multiple Linux servers in these ranges. The TAs then instructed the red team to exploit its list of primary targets: admin workstations and network ranges that included OT networks. The team only achieved access to the first two targets and did not find a path to the OT networks. While the team was able to affect the integrity of data derived from OT devices and applications, it was unable to find and access the organization’s internal network where the OT devices resided.
To gain access to the SBSs, the team first gained access to Microsoft System Center Configuration Manager (SCCM) servers, which managed most of the domain’s Windows systems. To access the SCCM servers, the team leveraged their AD data to identify administrators [T1087] of these targets. One of the users they previously acquired credentials for via DCSync was an administrator on the SCCM servers. The red team then used the Preferred Lateral Movement Technique to eventually authenticate to the SCCM servers. See Figure 3.
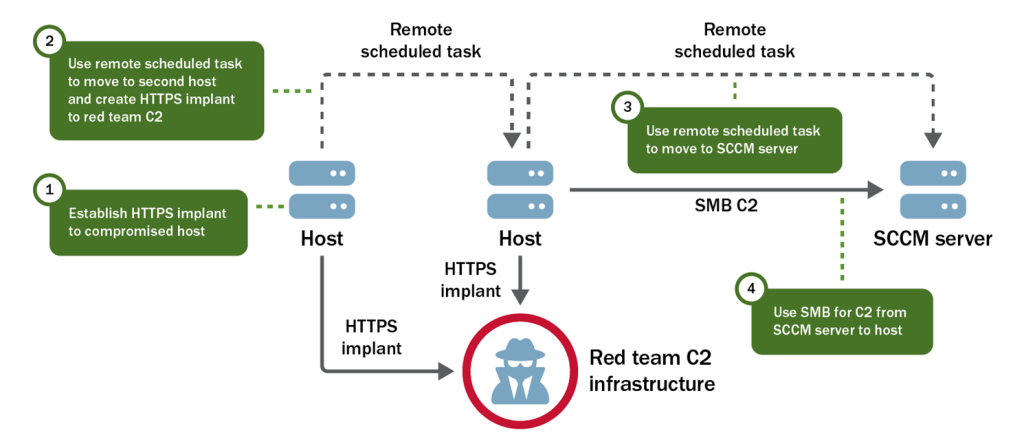
Admin Workstations
The first specific set of SBS targets provided by the TAs were admin workstations. These systems are used across various sensitive networks external to, or inaccessible from, the internal network where the team already had access. Normally, authorized personnel leverage these administrator workstations to perform administrator functions. CISA’s red team targeted these systems in the hopes that an authorized—but unwitting—user would move the tainted system to another network, resulting in a callback from the sensitive target network.
The red team reviewed AD data to identify these administrator systems. Through their review, the team discovered a subset of Windows workstations that could be identified with a prefix and determined a group likely to have administrative rights to the workstations.
With access to the SCCM server, the red team utilized their Preferred Lateral Movement Technique to gain access to each admin workstation target (see Figure 4).
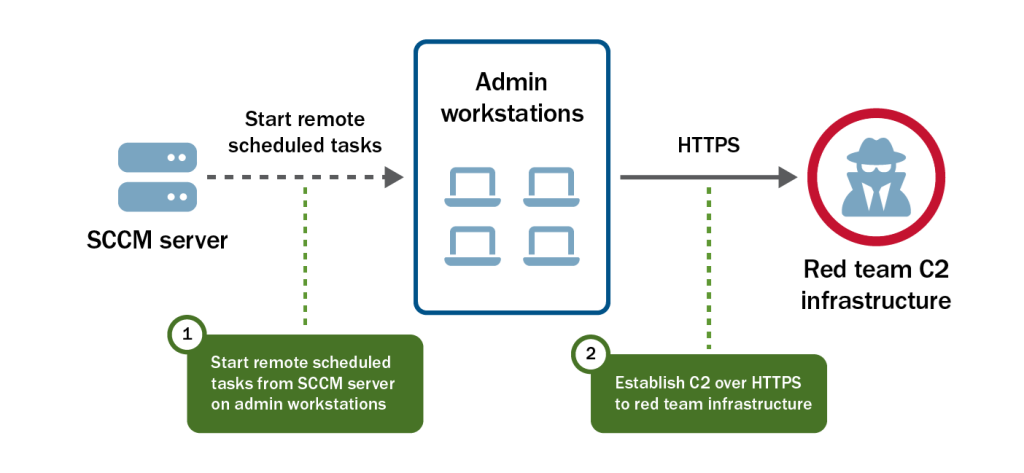
The red team maintained access to these systems for several weeks, periodically checking where they were communicating from to determine if they had moved to another network. Eventually, the team lost access to these systems without a deconfliction. To the best of the red team’s knowledge, these systems either did not move to new networks or, if they did, those systems no longer had the ability to communicate with red team’s C2 infrastructure.
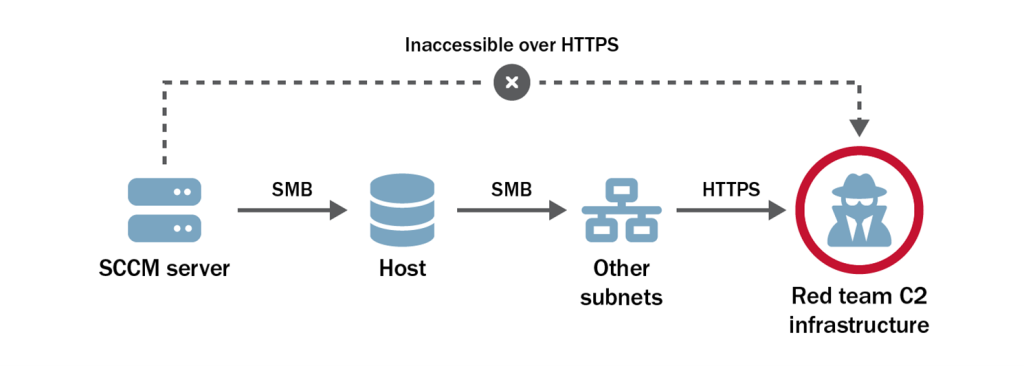
Additional Host and Other Subnets
After compromising admin workstations, the red team requested that the TAs prioritize additional systems or IP ranges. The TAs provided four CIDR ranges to target:
- A corporate DMZ that contained a mixture of systems and other subnets.
- A second subnet.
- A third subnet.
- An internal network that contained OT devices.
Access to the corporate DMZ was necessary to reach the second and third ranges, and the red team hoped that gaining access to these would facilitate access to the fourth range.
The red team followed a familiar playbook to gain access to these SBSs from another SCCM server. First, the team performed reverse DNS lookups [T1596.001] on IP addresses within the ranges the TAs provided. They then scanned SMB port 445/TCP [T1046] from a previously compromised SCCM server to discover Windows hosts it could access on the corporate DMZ. The team discovered the server could connect to a host within the target IP range and that the system was running an outdated version of Windows Server 2012 R2. The default configuration of Windows Server 2012 R2 allows unprivileged users to query the group membership of local administrator groups. The red team discovered a user account [T1069] by querying the Windows Server 2012 R2 target that was in a database administrator group. The team leveraged its Preferred Lateral Movement Technique to authenticate to the target as that user, then repeated that technique to access a database. This database receives information from OT devices used to feed monitoring dashboards, information which factors into the organization’s decision-making process [T1213].
The new host had several active connections to systems in the internal ranges of the second and third subnets. Reverse domain name system (DNS) lookup requests for these hosts failed to return any results. However, the systems were also running Windows Server 2012 R2. The red team used Windows API calls to NetLocalGroupEnum and NetLocalGroupGetMembers to query local groups [T1069.001], revealing the system names for these targets as a result. The red team performed their Preferred Lateral Movement Technique to gain access to these hosts in the second and third provided network ranges.
With access to these subnets, the red team began exploring a path to systems on a private subnet where OT devices resided but failed to locate a path to that fourth subnet.
Corporate Workstations of Critical Infrastructure Administrators and Operators
Next, the red team targeted the corporate workstations of the administrators and operators of the organization’s critical infrastructure. Because the team lacked knowledge of the organization’s OT devices and failed to discover a path to the private subnet where they resided, they instead tried to locate users that interacted with human machine interfaces (HMI). Access to such users could enable the team to access the HMI, which serves as a dashboard for OT.
The red team leveraged its AD data once again, combining this data with user information from SCCM to identify targets by job role and their primary workstation. Then the team targeted the desktop of a critical infrastructure administrator, the workstation of another critical infrastructure administrator, and the workstations of three critical infrastructure operators spread across two geographically disparate sites.
The AD data revealed users in a group that were administrators of all the targets. The red team then repeated their Preferred Lateral Movement Technique and identified a logged-in user connected to a “System Status and Alarm Monitoring” interface. The team discovered credentials to the interface in the user’s home directory, proxied through the system, and accessed the HMI interface over HTTP. The team did not pursue further activity involving the interface because their remaining assessment time was limited. Additionally, they did not discover a way to compromise the underlying OT devices.
Command and Control
The team used third-party owned and operated infrastructure and services [T1583] throughout its assessment, including in certain cases for command and control (C2). The tools that the red team obtained included [T1588.002]:
- Sliver, Mythic, Cobalt Strike, and other commercial C2 frameworks.
- The team maintained multiple command and control servers hosted by several cloud vendors. They configured each server with a different domain and used the servers for communication with compromised hosts. These servers retained all assessment data.
- Two commercially available cloud-computing platforms.
- The team used these platforms to create flexible and dynamic redirect servers to send traffic to the team’s servers [T1090.002]. Redirecting servers make it difficult for defenders to attribute assessment activities to the backend team servers. The redirectors use HTTPS reverse proxies to redirect C2 traffic between the target organization’s network and the team servers. The team encrypted all data in transit [T1573] and secured all data at rest through a VPN with multifactor authentication.
- Content delivery network (CDN) services.
- This technique leverages CDNs associated with high-reputation domains, causing malicious traffic to appear directed towards a reputational domain. However, it is redirected to red team-controlled servers. This allows the team to obfuscate some of their C2 traffic.
The team used domain fronting [T1090.004] to disguise outbound traffic, diversifying communications between the domains and the persistent beacons. This technique (which also leverages CDNs) allows the beacon to appear to connect to third-party domains but instead connects to the team’s redirect server.
Defense Evasion and Victim Network Defense Activities
Most of the encounters between the red team and network defenders occurred in the organization’s Linux environment. The red team leveraged Linux tradecraft in an attempt to evade network defenses. In response, network defenders’ threat hunting activities identified some of the team’s presence in their Linux environment. To evade defenses, the red team reordered the process identifier (PID) of its executable processes to appear closer to the kernel and minimize the team’s likelihood of detection. The team also modified its processes [T1055] by changing their names in memory and at execution. In addition, they used Python scripts [T1059.006] run in memory [T1620] to avoid on-disk detection. Some of the red team’s Linux persistence techniques included modifying preexisting scripts run by the cron utility and creating backdoors through ifup-post scripts and .bashrc. Network defenders ultimately identified the team’s backdoor in .bashrc [T1546.004].
Defenders also successfully detected anomalous activity on their Ansible Tower host and other systems in their Linux environment. The defenders actively analyzed NetFlow data, which helped them identify the red team’s persistence and lateral movement. To mitigate the impact of the red team’s tactics, network defenders would have needed to shut down a critical server as part of their incident response activities. A shut down would have resulted in downtime for hundreds of systems, including SBSs.
The organization’s EDR solutions largely failed to protect the organization. EDR detected only a few of the red team’s payloads in the organization’s Windows and Linux environments. In the instance the EDR protected the organization from the initial phishing payload, it generated an alert that network defenders neither read nor responded to. The red team excelled in bypassing EDR solutions by avoiding the use of basic “known-bad” detections the tools would capture. The team also inflated its file sizes above the upload threshold of the organization’s EDR [T1027.001]. In addition, the organization completely lacked any EDR solution in a legacy environment. As such, the red team’s persistence there went undetected throughout the assessment.
Network defenders failed to detect red team activity in the organization’s Windows environment due to a lack of proper identity management. Specifically, network defenders failed to detect and respond to the red team’s S4U2Self, asktgs, dcsync, and golden ticket activity. Had the organization monitored for unusual activity involving AD and Kerberos, they would have detected more red team activity.
Lastly, there were significant deficiencies in the organization’s DMZ that should have detected traffic into the organization’s internal network over the ports used by SMB and LDAPS. Network defenders never properly implemented an intrusion detection system (IDS) or intrusion prevention system (IPS) to monitor the DMZ at the network level. This lack of implementation resulted in a failure to detect malicious network traffic through their DMZ. Further, the red team was able to move laterally through the DMZ because there was an open internal proxy with internet access that enabled the team’s C2.
Phase II: Red Team Measurable Events Activity
The red team executed 13 measurable events designed to provoke a response from the people, processes, and technology defending the organization’s network. The red team did not have full visibility into the organization’s responses to these events and lacked the support of a white team to help assess the organization’s responses. See Table 1 for a description of the events, the organization’s actual response, and key takeaways.
| Measurable Event | Description | MITRE ATT&CK Technique(s) | Organization’s Reported Reactions | Key Takeaways |
|---|---|---|---|---|
| Internal Port Scan | Launches a scan from inside the network from a previously gained workstation to enumerate ports on target workstation, server, and domain controller system(s). | Network Service Discovery [T1046] | Identified an AD enumeration tool and temporarily blocked access to one C2 domain, which resulted in the red team temporarily losing access to six SCCM servers. | The organization did not report identifying the port scan. In addition, with proper network segmentation, the scan’s target hosts should not have been able to communicate. |
| Comprehensive Active Directory and Host Enumeration | Performs AD enumeration by querying all domain objects from the DC and enumerates trust relationships within the AD Forest, user accounts, and current session information from every domain computer (workstation and server). |
Domain Trust Discovery [T1482] Account Discovery: Domain Account [T1087.002] System Owner/User Discovery [T1033] Remote System Discovery [T1018] |
Identified an AD enumeration tool and temporarily blocked access to one C2 domain, which resulted in the red team temporarily losing access to six SCCM servers. | The organization did not report identifying the port scan. In addition, with proper network segmentation, the scan’s target hosts should not have been able to communicate. |
| Data Exfiltration – 1 GB of Data | Sends a large amount (1GB) of mock sensitive information to an external host. | Exfiltration Over Alternative Protocol [T1048] | A proxy likely blocked 1GB of data exfiltration during the red team’s first attempt. However, the team’s second attempt was successful when they exfiltrated the data in 100MB blocks. Hours after the data exfiltration, the organization blocked the domain used for C2 and removed access to the compromised host. | Organizations should implement web proxies that contain data threshold restrictions. Furthermore, network defenders need to manually analyze proxy data to determine whether there is legitimate outbound traffic or potentially malicious data exfiltration. |
| Malicious Traffic Generation- Workstation to External Host | Establishes a session that originates from a target workstation system directly to an external host over a clear text protocol, such as HTTP. | Application Layer Protocol [T1071] | The organization blocked access to the host and the C2 domains the red team used. | The organization blocked the malicious traffic at the network level but did not appear to identify the source workstation. |
| Active Directory Account Lockout | Locks out several administrative AD accounts in rapid succession. | Account Access Removal [T1531] | The organization’s password policy locked out the AD accounts. However, within minutes the accounts reopened, likely due to a group policy and/or an automated response. | There was no identified active response from the organization. Organizations should monitor AD account activity in Windows event logs against baselines to detect anomalous and potentially malicious activity. |
| Local Admin User Account Creation (workstation) | Creates a local administrator account on a target workstation system. |
Create Account: Local Account [T1136.001] Account Manipulation [T1098] |
An automated response removed the account from local administrator’s group but did not delete it. | Despite group policy objects removing the account, there were no detections for the activity. |
| Local Admin User Account Creation (server) | Creates a local administrator account on a target server system. |
Create Account: Local Account [T1136.001] Account Manipulation [T1098] |
An automated response removed the account from local Administrator’s group but did not delete it. | Despite group policy objects removing the account, there were no detections for the activity. |
| Active Directory Account Creation | Creates AD accounts and add them to domain admins group |
Create Account: Domain Account [T1136.002] Account Manipulation [T1098] |
An alert existed for this action but was disabled at the time the original event was triggered, thus it was undetected. After coordination between the TAs and red team revealed this lapse, the alert was enabled, the red team performed the action once again, and this time, TAs provided a screenshot of the alert from their monitoring dashboards. | Detection tools are only useful when network defenders tune them appropriately and effectively monitor alerts. At first, the organization missed an opportunity to respond to a tool that should have produced a true positive alert because it was misconfigured. |
| Domain Admin Lateral Movement—Workstation to Domain Controller and Workstation to Workstation | Compromises a Domain Admin account and uses it to run PSExec on multiple workstations and domain controllers. |
System Services: Service Execution [T1569.002] Remote Services: SMB/Windows Admin Shares [T1021.002] |
None identified. | Detect malicious use of standard tools like PSExec that malicious cyber actors may use for lateral movement by monitoring Windows logs for anomalous activity. In addition, organizations should look for abnormal communications between workstations. |
| Malicious Traffic Generation- Domain Controller to External Host | Establishes a session that originates from a target domain controller system directly to an external host over a clear text protocol, such as HTTP. | Application Layer Protocol [T1071] | None identified. | DCs should never connect directly to an external host over HTTP. The organization failed to detect and respond to this. |
| Trigger Host-Based Protection- Domain Controller | Uploads and executes a well-known (e.g., with a signature) malicious file to a target DC system to generate host-based alerts. | Ingress Tool Transfer [T1105] | Malicious file was removed by host-based endpoint protection system. | Host based detection tools can be helpful in detecting known IOCs. However, organizations should focus on detecting anomalous behavior by monitoring their networks and hosts against good baselines. The blocking of this well-known tool on a DC should trigger an urgent investigation. |
| Ransomware Simulation |
Executes simulated ransomware on multiple workstation systems to simulate a ransomware attack. Note: This technique does not encrypt files on the target system. |
N/A | Two out of nine users reported the event to defensive staff who identified all hosts that executed the ransomware. Five users likely rebooted their systems when observing the ransomware, one logged off and on, one closed the ransomware application repeatedly and continued working, one locked their screen, and another user exited the ransomware process after two hours. | Security awareness training should provide employees effective tools on how to respond to ransomware activity. |
LESSONS LEARNED AND KEY FINDINGS
The red team noted the following lessons learned relevant to all organizations generated from the security assessment of the organization’s network. These findings contributed to the team’s ability to gain persistent access across the organization’s network. See the Mitigations section for recommendations on how to mitigate these findings.
Lesson Learned: Insufficient Technical Controls
The assessed organization had insufficient technical controls to prevent and detect malicious activity. The organization relied too heavily on host-based EDR solutions and did not implement sufficient network layer protections.
- Finding #1: The organization’s perimeter network was not adequately firewalled from its internal network, which allowed the red team a path through the DMZ to internal networks. A properly configured network should block access to a path from the DMZ to other internal networks.
- Finding #2: The organization was too reliant on its host-based tools and lacked network layer protections, such as well-configured web proxies or intrusion prevention systems (IPS). The organization’s EDR solutions also failed to catch all the red team’s payloads. Below is a list of some of the higher risk activities conducted by the team that were opportunities for detection:
- Phishing;
- Kerberoasting;
- Generation and use of golden tickets;
- S4U2self abuse;
- Anomalous LDAP traffic;
- Anomalous NFS enumeration;
- Unconstrained Delegation server compromise;
- DCSync;
- Anomalous account usage during lateral movement;
- Anomalous outbound network traffic;
- Anomalous outbound SSH connections to the team’s cloud servers from workstations; and
- Use of proxy servers from hosts intended to be restricted from internet access.
- Finding #3: The organization had insufficient host monitoring in a legacy environment. The organization had hosts with a legacy operating system without a local EDR solution, which allowed the red team to persist for several months on the hosts undetected.
Lesson Learned: Continuous Training, Support, and Resources
The organization’s staff requires continuous training, support, and resources to implement secure software configurations and detect malicious activity. Staff need to continuously enhance their technical competency, gain additional institutional knowledge of their systems, and ensure are provided sufficient resources by management to adequately protect their networks.
- Finding #4: The organization had multiple systems configured insecurely. This allowed the red team to compromise, maintain persistence, and further exploit those systems (i.e., access credentials, elevate privileges, and move laterally). Insecure system configurations included:
- Default server configurations. The organization used default configurations for hosts with Windows Server 2012 R2, which allows unprivileged users to query membership of local administrator groups. This enabled the red team to identify several standard user accounts with administrative access.
Note: By default, NFS shares change the root user to thenfsnobodyuser, an unprivileged user account. In this way, users with local root access are prevented from gaining root level access over the mounted NFS share. Here, the organization deviated from the secure by default configuration and implemented theno_root_squashoption to support a few legacy systems instead. This deviation from the default allowed the red team to escalate their privileges over the domain. - Hosts with
Unconstrained Delegationenabled unnecessarily. Hosts withUnconstrained Delegationenabled will store the Kerberos TGTs of all users that authenticate to that host. This affords threat actors the opportunity to steal TGTs, including the TGT for a domain controller, and use them to escalate their privileges over the domain. - Insecure Account Configuration. The organization had an account running a Linux webserver with excessive privileges. The entry for that user in the
sudoersfile—which controls user rights—contained paths with wildcards where that user had write access, allowing the team to escalate privileges.
Note: This file should only contain specific paths to executable files that a user needs to run as another user or root, and not a wildcard. Users should not have write access over any file in thesudoersentry.
- Default server configurations. The organization used default configurations for hosts with Windows Server 2012 R2, which allows unprivileged users to query membership of local administrator groups. This enabled the red team to identify several standard user accounts with administrative access.
- Finding #5: The red team’s activities generated security alerts that network defenders did not review. In many instances, the organization relied too heavily on known IOCs and their EDR solutions instead of conducting independent analysis of their network activity compared against baselines.
- Finding #6: The organization lacked proper identity management. Because network defenders did not implement a centralized identity management system in their Linux network, they had to manually query every Linux host for artifacts related to the red team’s lateral movement through SSH. Defenders also failed to detect anomalous activity in their organization’s Windows environment because of poor identity management.
Lesson Learned: Business Risk
The organization’s leadership minimized the business risk of known attack vectors for their organization. Leadership deprioritized the treatment of a vulnerability their own cybersecurity team identified, and in their risk-based decision-making, miscalculated the potential impact and likelihood of its exploitation.
- Finding #7: The organization used known insecure and outdated software. The red team discovered software on one of the organization’s web servers that was outdated.
- After their operations, the red team learned the insecure and outdated software was a known security concern. The organization’s security team alerted management to the risks associated this software, but management accepted the risk.
- Next, the security team implemented a VDP program, which resulted in a participant exploiting the vulnerability for initial access. The VDP program helped the security team gain management support, and they implemented a web application firewall (WAF) as a compensating control. However, they did not adequately mitigate the vulnerability as they configured the WAF to be only in monitoring mode. The security team either did not have processes (or implement them properly) to scan, assess, and test whether they treated the vulnerability effectively.
Additional Findings
The red team noted the following additional issues relevant to the security of the organization’s network that contributed to their activity.
- Unsecured Keys and Credentials. The organization stored many private keys that lacked password protection, allowing the red team to steal the keys and use them for authentication purposes.
- The private key of a PFX file was not password protected, allowing the red team to use that certificate to authenticate to active directory, access UDHOST, and eventually compromise the DC. In addition, the organization did not require password protection of SSH private keys.
Note: Without a password protected key, an actor can more easily steal the private key and use it to authenticate to a system through SSH. - The organization had files in a home share that contained cleartext passwords. The accounts included, among other accounts, a system administrator.
Note: The organization appeared to store cleartext passwords in the description and user password sections of Active Directory accounts. These passwords were accessible to all domain users.
- The private key of a PFX file was not password protected, allowing the red team to use that certificate to authenticate to active directory, access UDHOST, and eventually compromise the DC. In addition, the organization did not require password protection of SSH private keys.
- Email Address Verification. The active Microsoft Office 365 configuration allows an unauthenticated external user to validate email addresses through observing error messages in the form of
HTTP 302versusHTTP 200responses. This misconfiguration helps threat actors verify email addresses before sending phishing emails.
Noted Strengths
The red team noted the following technical controls or defensive measures that prevented or hampered offensive actions:
- Network defenders detected the initial compromise and some red team movement. After being alerted of the web shell, the organization initiated hunt activities, detected initial access, and tracked some of the red team’s Phase I movements. The organization terminated much of the red team’s access to the organization’s internal network. Of note, once the organization’s defenders discovered the red team’s access, the red team spent significant time and resources continuously refortifying their access to the network.
- Host-based EDR solutions prevented initial access by phishing. The EDR stopped the execution of multiple payloads the red team sent to a user of the organization over a week long period. The organization leveraged two products on workstations, one that was publicly discoverable and another the red team did not learn about until gaining initial access. The product the red team was unaware of, and did not test their payload against, was responsible for stopping the execution of their payloads.
- Strong domain password policy. The organization’s domain password policy neutralized the red team’s attempts to crack hashes and spray passwords. The team was unable to crack any hashes of all 115 service accounts it targeted.
- Effective separation of privileges. The organization’s administrative users had separate accounts for performing privileged actions versus routine activities. This makes privilege escalation more difficult for threat actors.
MITIGATIONS
Network Defenders
CISA recommends organizations implement the recommendations in Table 2 to mitigate the findings listed in the Lessons Learned and Key Findings section of this advisory. These mitigations align with the Cross-Sector Cybersecurity Performance Goals (CPGs) developed by CISA and the National Institute of Standards and Technology (NIST). The CPGs provide a minimum set of practices and protections that CISA and NIST recommend all organizations implement. CISA and NIST based the CPGs on existing cybersecurity frameworks and guidance to protect against the most common and impactful threats, tactics, techniques, and procedures. See CISA’s Cross-Sector Cybersecurity Performance Goals for more information on the CPGs, including additional recommended baseline protections.
| Finding | Recommendation |
|---|---|
| Insufficient Network Segmentation of DMZ |
|
| Insufficient Network Monitoring |
|
| Insufficient Host Monitoring in Legacy Environment |
|
| Insecure configurations of systems |
|
| Lack centralized identity management and monitoring systems |
|
| Use of known insecure and outdated software |
|
| Insecure Keys and Credentials |
|
Additionally, CISA recommends organizations implement the mitigations below to improve their cybersecurity posture:
- Provide users with regular training and exercises, specifically related to phishing emails. Phishing accounts for majority of initial access intrusion events.
- Enforce phishing-resistant MFA to the greatest extent possible.
- Reduce the risk of credential compromise via the following:
- Place domain admin accounts in the protected users group to prevent caching of password hashes locally; this also forces Kerberos AES authentication as opposed to weaker RC4 or NTLM authentication protocols.
- Upgrade to Windows Server 2019 or greater and Windows 10 or greater. These versions have security features not included in older operating systems.
As a long-term effort, CISA recommends organizations prioritize implementing a more modern, Zero Trust network architecture that:
- Leverages secure cloud services for key enterprise security capabilities (e.g., identity and access management, endpoint detection and response, and policy enforcement).
- Upgrades applications and infrastructure to leverage modern identity management and network access practices.
- Centralizes and streamlines access to cybersecurity data to drive analytics for identifying and managing cybersecurity risks.
- Invests in technology and personnel to achieve these goals.
Software Manufacturers
The above mitigations apply to critical infrastructure organizations with on-premises or hybrid environments. Recognizing that insecure software is the root cause of many of these flaws and responsibility should not fall on the end user, CISA urges software manufacturers to implement the following:
- Embed security into product architecture throughout the entire software development lifecycle (SDLC).
- Eliminate default passwords. Do not provide software with default passwords. To eliminate default passwords, require administrators to set a strong password [CPG 2.B] during installation and configuration.
- Design products so that the compromise of a single security control does not result in compromise of the entire system. For example, narrowly provision user privileges by default and employ ACLs to reduce the impact of a compromised account. This will make it more difficult for a malicious cyber actor to escalate privileges and move laterally.
- Mandate MFA, ideally phishing-resistant MFA, for privileged users and make MFA a default, rather than opt-in, feature.
- Reduce hardening guide size, with a focus on systems being secure by default. In this scenario, the red team noticed default Windows Server 2012 configurations that allowed them to enumerate privileged accounts.
- Important: Manufacturers need to implement routine nudges that are built into the product rather than relying on administrators to have the time, expertise, and awareness to interpret hardening guides.
These mitigations align with principles provided in the joint guide Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Secure by Design Software. CISA urges software manufacturers to take ownership of improving security outcomes of their customers by applying these and other secure by design practices. By adhering to secure by design principles, software manufacturers can make their product lines secure out of the box without requiring customers to spend additional resources making configuration changes, purchasing security software and logs, monitoring, and making routine updates.
For more information on secure by design, see CISA’s Secure by Design webpage. For more information on common misconfigurations and guidance on reducing their prevalence, see the joint advisory NSA and CISA Red and Blue Teams Share Top Ten Cybersecurity Misconfigurations.
VALIDATE SECURITY CONTROLS
In addition to applying mitigations, CISA recommends exercising, testing, and validating your organization's security program against the threat behaviors mapped to the MITRE ATT&CK for Enterprise framework in this advisory. CISA recommends testing your existing security controls inventory to assess how they perform against the ATT&CK techniques described in this advisory.
To get started:
- Select an ATT&CK technique described in this advisory (see Table 3 to Table 16).
- Align your security technologies against the technique.
- Test your technologies against the technique.
- Analyze your detection and prevention technologies’ performance.
- Repeat the process for all security technologies to obtain a set of comprehensive performance data.
- Tune your security program, including people, processes, and technologies, based on the data generated by this process.
CISA recommends continually testing your security program, at scale, in a production environment to ensure optimal performance against the MITRE ATT&CK techniques identified in this advisory.
RESOURCES
- See CISA’s RedEye tool on CISA’s GitHub page. RedEye is an interactive open source analytic tool used to visualize and report red team command and control activities. See CISA’s RedEye tool overview video for more information.
- See CISA’s Phishing Guidance.
- See CISA’s Secure by Design page to learn more about secure by design principles.
APPENDIX: MITRE ATT&CK TACTICS AND TECHNIQUES
See Table 3 to Table 16 for all referenced red team tactics and techniques in this advisory. Note: Unless noted, activity took place during Phase I. For assistance with mapping malicious cyber activity to the MITRE ATT&CK framework, see CISA and MITRE ATT&CK’s Best Practices for MITRE ATT&CK Mapping and CISA’s Decider Tool.
| Technique Title | ID | Use |
|---|---|---|
| Gather Victim Network Information | T1590 | The team conducted open source research on the target organization to gain information about its network. |
| Gather Victim Network Information: Network Security Appliances | T1590.006 | The team conducted open source research on the target organization to gain information about its defensive tools. |
| Gather Victim Identity Information: Employee Names | T1589.003 | The team conducted open source research on the target organization to gain information about its employees. |
| Active Scanning | T1595 | The team conducted external reconnaissance of the organization’s network. |
| Gather Victim Network Information: IP Addresses | T1590.005 | The team conducted reconnaissance of the organization’s external IP space. |
| Search Open Websites/Domains | T1593 | The team conducted open source research to identify information about the organization’s network. |
| Gather Victim Identity Information: Email Addresses | T1589.002 | The team looked for email addresses and names to infer email addresses from the organization’s email syntax. |
| Search Open Technical Databases: Scan Databases | T1596.005 | The team conducted reconnaissance with several publicly available tools, such as Shodan and Censys, to discover accessible devices and services on the internet. |
| Search Open Technical Databases: DNS/Passive DNS | T1596.001 | The team performed reverse DNS lookups on IP addresses within the ranges the TAs provided. |
| Technique Title | ID | Use |
|---|---|---|
| Acquire Infrastructure | T1583 | The team used third-party owned and operated infrastructure and services throughout its assessment. |
| Obtain Capabilities: Tool | T1588.002 | The team obtained tools (i.e., Sliver, Mythic, Cobalt Strike, and other commercial C2 frameworks). |
| Technique Title | ID | Use |
|---|---|---|
| Phishing | T1566 | The team designed spearphishing campaigns tailored to employees of the organization most likely to communicate with external parties. |
| Exploit Public-Facing Application | T1190 | The team gained initial access to the target by exploiting an internet-facing Linux web server. |
| Phishing: Spearphishing Link | T1566.002 | The team sent tailored spearphishing emails to 13 targets. |
| Technique Title | ID | Use |
|---|---|---|
| User Execution | T1204 | The team’s phishing attempts were ultimately unsuccessful; targets ran the payloads, but their execution did not result in the red team gaining access into the network. |
| User Execution: Malicious File | T1204.002 | One user responded and executed two malicious payloads. |
| Command and Scripting Interpreter | T1059 | The preexisting web shell allowed the team to run arbitrary commands on the server. |
| Command and Scripting Interpreter: Python | T1059.006 | The team used python scripts. |
| System Services: Service Execution | T1569.002 | The team compromised a Domain Admin account and used it to run PSExec on multiple workstations and a domain controller. |
| Remote Services: SMB/Windows Admin Shares | T1021.002 | The team established a session that originated from a target. |
| Technique Title | ID | Use |
|---|---|---|
| Server Software Component: Web Shell | T1505.003 | After the failed spearphishing campaigns, the red team continued external reconnaissance of the network and discovered a web shell left from a previous VDP program. |
| Boot or Logon Initialization Scripts | T1037 | The team backdoored several scripts run at boot time for persistence. |
| Scheduled Task/Job: Cron | T1053.003 | Some of the team’s techniques included modifying preexisting scripts run by the cron utility and ifup-post scripts. |
| Boot or Logon Initialization Scripts: Network Logon Script | T1037.003 | The team modified preexisting scripts run by the cron utility and ifup-post scripts. |
| Event Triggered Execution: Unix Shell Configuration Modification | T1546.004 | The team used a backdoor in .bashrc. |
| Create Account: Local Account | T1136.001 | During Phase II, the team created a local administrator account on a target server system. |
| Account Manipulation | T1098 | During Phase II, the team created a local administrator account on a target server system. |
| Create Account: Domain Account | T1136.002 | The team created AD accounts and added them to domain admins group. |
| Technique Title | ID | Use |
|---|---|---|
| Valid Accounts | T1078 | The team moved laterally from the web server to the organization’s internal network using valid accounts. |
| Abuse Elevation Control Mechanism: Sudo and Sudo Caching | T1548.003 | The team discovered that WEBUSER1 had excessive sudo rights, allowing them to run some commands as root without a password. |
| Technique Title | ID | Use |
|---|---|---|
| Process Injection | T1055 | The team modified its processes by changing their names in memory and at execution. |
| Reflective Code Loading | T1620 | The team used Python scripts run in memory to avoid on-disk detection. |
| Obfuscated Files or Information: Binary Padding | T1027.001 | The team inflated its file sizes above the upload threshold of the organization’s EDR. |
| Technique Title | ID | Use |
|---|---|---|
| Unsecured Credentials: Credentials In Files | T1552.001 | The team discovered credential material on a misconfigured Network File System. |
| Steal or Forge Authentication Certificates | T1649 | The team used a certificate for client authentication discovered on the NFS share to compromise a system configured for Unconstrained Delegation. |
| Steal or Forge Kerberos Tickets: Golden Ticket | T1558.001 | The team acquired a ticket granting ticket for a domain controller. |
| Unsecured Credentials: Bash History | T1552.003 | The team used its escalated privileges to search bash command histories. |
| Data from Network Shared Drive | T1039 | The team used its escalated privileges to search for private certificate files, Secure Shell (SSH) private keys, passwords, bash command histories, and other sensitive data across all user files on the NFS share. |
| Unsecured Credentials: Private Keys | T1552.004 | The team initially obtained 61 private SSH keys and a file containing valid cleartext domain credentials. |
| Valid Accounts: Domain Accounts | T1078.002 | The team initially obtained 61 private SSH keys and a file containing valid cleartext domain credentials. |
| Network Sniffing | T1187 | The red team leveraged this administrative access to upload a modified version of Rubeus in monitor mode to capture incoming tickets. |
| OS Credential Dumping: DCSync | T1003.006 | The team used DCSync through Linux tunnels to acquire the hash of several privileged accounts. |
| Technique Title | ID | Use |
|---|---|---|
| System Network Configuration Discovery | T1016 | The team leveraged the web shell to identify an open internal proxy server. |
| Account Discovery | T1087 | The team leveraged their AD data to identify administrators of the SCCM servers. |
| Account Discovery: Domain Account | T1087.002 | The team queried LDAPS to collect information about users, computers, groups, access control lists (ACL), organizational units (OU), and group policy objects (GPO). During Phase II, the team performed AD enumeration by querying all domain objects from the DC, as well as enumerating trust relationships within the AD Forest, user accounts, and current session information from every domain computer. |
| Remote System Discovery | T1018 | The team queried LDAPS to collect information about users, computers, groups, access control lists (ACL), organizational units (OU), and group policy objects (GPO). During Phase II, the team performed AD enumeration by querying all domain objects from the DC as well as enumerating trust relationships within the AD Forest, user accounts, and current session information from every domain computer. |
| Permission Groups Discovery: Domain Groups | T1069.002 | The team queried LDAPS to collect information about users, computers, groups, access control lists (ACL), organizational units (OU), and group policy objects (GPO). |
| Group Policy Discovery | T1615 | The team queried LDAPS to collect information about users, computers, groups, access control lists (ACL), organizational units (OU), and group policy objects (GPO). |
| Network Service Discovery | T1046 |
The team scanned SMB port 445/TCP. During Phase II, the team launched a scan from inside the network from a previously gained workstation. |
| Permission Groups Discovery | T1069 | The team discovered a user account through querying the Windows Server 2012 R2 target. |
| Permission Groups Discovery: Local Groups | T1069.001 | The team used Windows API calls to NetLocalGroupEnum and NetLocalGroupGetMembers to query local groups. |
| Domain Trust Discovery | T1482 | During Phase II, the team enumerated trust relationships within the AD Forest. |
| System Owner/User Discovery | T1033 | During Phase II, the team performed AD enumeration by querying all domain objects from the DC, as well as enumerating trust relationships within the AD Forest, user accounts, and current session information from every domain computer. |
| Technique Title | ID | Use |
|---|---|---|
| Taint Shared Content | T1080 | Since no_root_squash was used, the team could read and change any file on the shared file system and leave trojanized applications. |
| Remote Services: SSH | T1021.004 | The team’s acquisition of SSH private keys of user and service accounts, including two highly privileged accounts with root access to hundreds of servers, facilitated unrestricted lateral movement to other Linux hosts. |
| Software Deployment Tools | T1072 | Access to an Ansible Tower system provided the team easy access to multiple SBSs. |
| Technique Title | ID | Use |
|---|---|---|
| Data from Information Repositories | T1213 | The team accessed a database that received information from OT devices to feed monitoring dashboards, which the organization used to make decisions. |
| Technique Title | ID | Use |
|---|---|---|
| Ingress Tool Transfer | T1105 |
The team then downloaded and executed a Sliver payload that utilized this proxy to establish command and control. During Phase II, the team uploaded and executed a well-known malicious file to a target DC system to generate host-based alerts. |
| Application Layer Protocol: Web Protocols | T1071.001 | In the organization’s Linux environment, the red team leveraged HTTPS connections for C2. |
| Proxy: Internal Proxy | T1090.001 | The team leveraged an open internal HTTPS proxy for their traffic. |
| Application Layer Protocol: File Transfer Protocols | T1071.002 | The team connected to servers over SMB. |
| Proxy: External Proxy | T1090.002 | The team used cloud platforms to create flexible and dynamic redirect servers to send traffic to the team’s servers. |
| Encrypted Channel | T1573 | The team encrypted all data in transit and secured all data at rest through a VPN with multifactor authentication. |
| Proxy: Domain Fronting | T1090.004 | The team used domain fronting to disguise outbound traffic. |
| Application Layer Protocol | T1071 | During Phase II, the team established a session that originated from a target Workstation system directly to an external host over a clear text protocol, such as HTTP. |
| Technique Title | ID | Use |
|---|---|---|
| Exfiltration Over Alternative Protocol | T1048 | During Phase II, the team sent a large amount of mock sensitive information to an external host. |
| Technique Title | ID | Use |
|---|---|---|
| Account Access Removal | T1531 | The team locked out several administrative AD accounts in rapid succession. |
Russian Phobos ransomware operator Evgenii Ptitsyn, accused of managing attacks, was extradited from South Korea to the US to face cybercrime charges. Russian Phobos ransomware operator Evgenii Ptitsyn, suspected of playing a key role in the ransomware operations, was extradited from South Korea to the US to face cybercrime charges. According to the DoJ, the […]
What was browsing the web like in 2004? People said things like “surfing the internet,” for starters. Excessive pop-up ads were annoying but they felt like the norm. The search bar and multiple tabs did not exist, and there seemed to be only one browser in sight. That is, until Firefox 1.0 arrived and gave […]
The post 20 years of Firefox: How a community project changed the web appeared first on The Mozilla Blog.
LodaRAT, a remote access tool active since 2016, has resurfaced in a new campaign that’s taking the cybersecurity world by storm. Originally designed for basic information theft, this tool has transformed into a sophisticated malware capable of carrying out global cyber-espionage operations. What’s alarming is that while LodaRAT hasn’t been updated since 2021, its reach and effectiveness have grown, making it a pressing concern for individuals and organisations worldwide.
A Global Campaign with Far-Reaching Impact
What sets this latest campaign apart is its global nature. Unlike previous efforts that targeted specific regions, LodaRAT is now aiming at victims across the world. Around 30% of related malware samples uploaded to VirusTotal came from the United States, suggesting widespread infection. This shift indicates that LodaRAT is no longer confined to limited geographic boundaries, and its operators are adapting to target more diverse networks and systems.
How LodaRAT Works
LodaRAT’s tactics have become more complex, allowing it to infiltrate systems and operate undetected. Its distribution relies on a mix of phishing emails, system vulnerabilities, and other malware like DonutLoader and Cobalt Strike. It also disguises itself as trusted software such as Skype, Discord, or Windows Update to trick users into installing it.
Once installed, the malware carries out a variety of harmful activities, including:
- Spying on users by recording audio and video through webcams and microphones.
- Stealing credentials and cookies from popular browsers like Microsoft Edge and Brave.
- Disabling security measures such as the Windows Firewall to create backdoors.
- Spreading through networks, using SMB protocol exploits to infect other devices.
- Hiding its tracks by storing stolen data in concealed locations on the victim's system.
Increased Risks for Organizations
This new campaign has heightened risks for businesses and organisations. LodaRAT is capable of spreading within internal networks by exploiting specific vulnerabilities, particularly via port 445. This allows attackers to move laterally, targeting multiple devices in the same network. Such breaches can lead to stolen data, operational disruptions, and significant financial losses.
Protecting Against LodaRAT
To defend against LodaRAT, organisations and individuals need to take proactive measures:
1. Strengthen security systems by using advanced endpoint protection tools.
2. Monitor network activity to detect unusual behaviours that could indicate malware presence.
3. Educate users on phishing tactics to prevent accidental downloads.
4. Adopt strong authentication practices to make credential theft harder.
5. Use tools like Rapid7’s Insight Agent to identify potential threats and weak points.
The return of LodaRAT shows how minor tweaks to existing malware can make it highly effective. This campaign is a reminder that even older threats can evolve and remain dangerous. Staying vigilant and updating cybersecurity measures regularly are key to staying ahead of such attacks.
By understanding how LodaRAT operates and taking the necessary precautions, organisations and individuals can better protect themselves in an increasingly complex digital ecosystem.
For the latest discoveries in cyber research for the week of 11th November, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES The FBI and CISA issued a joint statement detailing a major Chinese cyber-espionage campaign targeting U.S. telecommunications infrastructure, led by the APT group Salt Typhoon. This operation compromised networks to steal call […]
The post 18th November – Threat Intelligence Report appeared first on Check Point Research.
Expert's Rating
Pros
- Clean, uncluttered interface
- Excellent antivirus protection
- Well-priced for its feature set
Cons
- Full scans affect PC performance when using Microsoft Office apps
- No included password manager
Our Verdict
Avast One expands upon the company’s free security suite, with upgraded defenses against online threats and additional features. You don’t get just excellent antivirus protection, but tools to safeguard your identity and privacy (including a VPN with unlimited bandwidth), as well as tune up your PC. While it lacks a password manager and parental controls, if you’re all set on those fronts, this app’s polish is hard to beat.
Price When Reviewed
This value will show the geolocated pricing text for product undefined
Best Pricing Today
You could let Windows protect your PC — it does already shield against online threats. But independent antivirus software like Avast One is better at catching viruses and malware, and wins on user friendliness, too.
Avast actually has two lines of paid products, both powered by the same antivirus engine. They have similarly clean interfaces, too. But the Avast One line focuses on identity and privacy concerns, making it arguably the better choice for most people. Life is largely conducted online these days, and staying safe is more than just thwarting malware and exploits. Phishing schemes and personal information leaked in data breaches can weaken your security, too.
Avast One lets you stay on top of these issues, which are currently unavoidable in modern life, and does so with polish.
Further reading: See our roundup of the best antivirus software for Windows to learn about competing products.
What does Avast One include?
Avast One enhances the already wide protection against online threats available in the free Essentials plan — it both upgrades existing defenses and adds new ones to the set, too.
The fundamentals include the company’s top-notch antivirus and firewall, which block malware, ransomware, malicious websites and downloads, and network intrusions. The suite also monitors for vulnerable networks, compromised applications, attempts at unauthorized access to the saved passwords in your browser, and appearances of your data on the dark web. And you get PC utilities, too: a system optimizer and software updater.

PCWorld
Upgrading to Avast One unlocks safeguards against dangers like webcam takeovers; webmail messages containing malware and phishing attempts; shady apps hunting for sensitive data (like social security numbers) on your PC; and malicious redirects for websites you visit (aka DNS hijacking).
You get strengthened identity and privacy protections as well. For starters, dark web monitoring becomes continuous in the background. The VPN puts no restrictions on bandwidth or server usage, too, and online trackers get blocked. Avast One even ties these latter two features together in a “Private Mode” setting for your default browser’s incognito tabs. When enabled, a secure VPN connection and tracking prevention will automatically kick in whenever you start an incognito session.
As for PC utilities, you get three extras: a disk cleaner, driver updater, and duplicate file finder.
Avast One does not include a password manager or parental controls. You’ll have to look elsewhere for these services, as Avast doesn’t offer them at all.
How much does Avast One cost?
If you buy a license directly from Avast, you get a discounted rate for the first year, then the standard price afterward. Plans purchased through Avast come with a 30-day money-back guarantee and are automatically enrolled in auto-renewal.
Individual plan (5 devices)
- $51 for the first year
- $110 per year thereafter
Family plan (30 devices)
- $70 for the first year
- $150 per year thereafter
For more savings on Avast One plans, you can take advantage of a special offer for PCWorld readers, which drops the cost of the first year to $33 for 5 devices and $53 for 30 devices. You can also check out our article on discounted antivirus software that explains how to get deals through online stores like Newegg.
If you use our link, PCWorld readers get a special rate for Avast One plans on the Avast website.
PCWorld
You can install Avast One on PC, Android, macOS, and iOS devices. The Avast One Family plan also includes a Family Sharing feature — it allows you to invite other users with separate accounts to share in that bigger device limit.
Relative to Avast’s Premium Security plan, which has a similar number of features, you’ll pay less for Avast One in the first year (relative to the number of devices you have). However, Avast One is more expensive in subsequent years, when the cost rises to the full list price.
Key features of Avast One
Installation and user interface
After downloading Avast One from your online account dashboard and installing, you’ll see a screen asking to start a scan of your PC. You can choose to do so (which is recommended), or skip to access the app.
Avast One’s interface is light-themed, with a mix of cream, tan, and orange accents for its color theme. A simple navigation bar lives on the left side of the screen, giving quick access to the dashboard, features, notifications, and settings. The tabs aren’t labeled as clearly as in competing software — Account is where you’ll find settings and other app-related info, for example. But you can get oriented quickly, thanks to good descriptions within each section of the software.

PCWorld
Opening the app will show the Home screen, which is a dashboard that lets you run a scan, turn on the VPN, or run one of several utilities. You have just two options for scanning here, a smart scan and a deep scan. For others, you must head to the Scan Center within the Explore tab, which houses all Avast One features. There you’ll find options for Targeted Scan and Boot-Time Scan in addition to the smart and deep scan defaults. You can also create a custom scan. But unlike Avast’s Premium Security suite, Avast One’s scan settings are more limited. In fact, this difference is how the two products diverge — Avast One focuses on a simpler experience geared toward life online, while Premium Security prioritizes greater control over security on your PC.
Some users may not like the list format of the Explore tab. Though it groups the different settings by type (Device Protection, Online Privacy, Smooth Performance), those who like to see everything on a screen at once may find it frustrating to have to scroll. But each entry is labeled clearly and described well.
Surprisingly, Avast One’s attempt to upsell its more premium plans is a fairly discreet button at the top of the window, next to the minimize and exit buttons. It’s far more subtle than the approach taken by Avast’s sister company, AVG.
Virus, malware, and threat protection
Real-time protection
Avast One keeps continuous watch for real-time threats, both online and on your PC. When you browse the web, the software scans pages for malware and watches for attempts to redirect you to fake sites. The traffic going to and from your PC also get screened for suspicious activity, as do attempts to access passwords saved to your browser. If you choose to give Avast access to your webmail account (like Gmail), it will also monitor your email for phishing scams and malware.
On your PC, Avast One scans files you add or open, checks downloaded email in Microsoft Outlook or Mozilla Thunderbird for malicious attachments, and limits access to folders often target by ransomware (and any others you add to the list). It also allows only approved apps to use your webcam.
PCWorld
Avast One also tracks data breaches to see if any of your email addresses (up to five) have appeared in them. You’ll get notified whenever a match is found. Changing your password on that service or site — and any others where you might have also used it or a close variant — will be up to you to perform yourself, though. (Which is when a password manager comes in handy.)
Scheduled and manual scans
Unlike other antivirus software makers, Avast does not set up a default scheduled scan in a freshly installed app — and so Avast One lacks this feature out of the box (so to speak), too. It’s an odd move, since scheduled scans keep up the security of a PC with minimal user effort needed.
To get your PC on a regular scan schedule, you can click the Automated Smart Scan scheduling button in the Scan Center’s Scan Now tab. A smart scan checks for malware, vulnerabilities in your browser and apps, and other issues, in order to keep your PC clean overall.
Alternatively, you can create your own custom scan, which lets you pick from Deep Scan, Targeted Scan, or Quick Scan as your template. Deep scans dig thoroughly through your PC, while targeted scans examine specific files or folders. Quick scans look at commonly targeted and critical areas of your system. You can then further tweak a handful of advanced settings.

PCWorld
For both smart scan and custom scan scheduling, your options are to run the scan just once, daily, weekly, or monthly. Of the options, I recommend scheduling a quick scan or custom scan — they require no user input to complete. Smart scans ask for your input on findings for each portion of the scan before moving to the next piece.
If you prefer to manually run a scan, your options are Smart Scan, Deep Scan, Targeted Scan, Boot-Time Scan (which searches for any threats before Windows starts), and any of your custom scans. Unlike Avast’s Premium Security suite, you can only adjust your custom scan’s settings.
Firewall
Avast One’s firewall handles all traffic coming and going from your PC, completely replacing Windows own default protection. For most people, it will feel like an upgrade — the interface makes monitoring and controlling app access feel easy, rather than scary. You can clearly see which Windows programs and services are currently online and which have asked for access, as well as immediately block any suspicious items on the list.
(Windows may have come a long way with its security suite, but dig into its firewall settings, and you’ll see a mix of interfaces from different eras—and most of them are not friendly to a non-technical audience.)
The default settings are adequate for most people, though Avast One doesn’t allow much customization. You can add new apps, block apps or devices, and change three settings (two of which are related to notifications). But that covers the basics sufficiently.
Ransomware Shield
A common protection against ransomware, which encrypts files so that the attacker can extort money from victims, is to limit software access to folders often targeted by such malware. Untrusted apps can’t change or delete files in those locations. So even if you accidentally install ransomware on your system, you get an extra layer of defense.
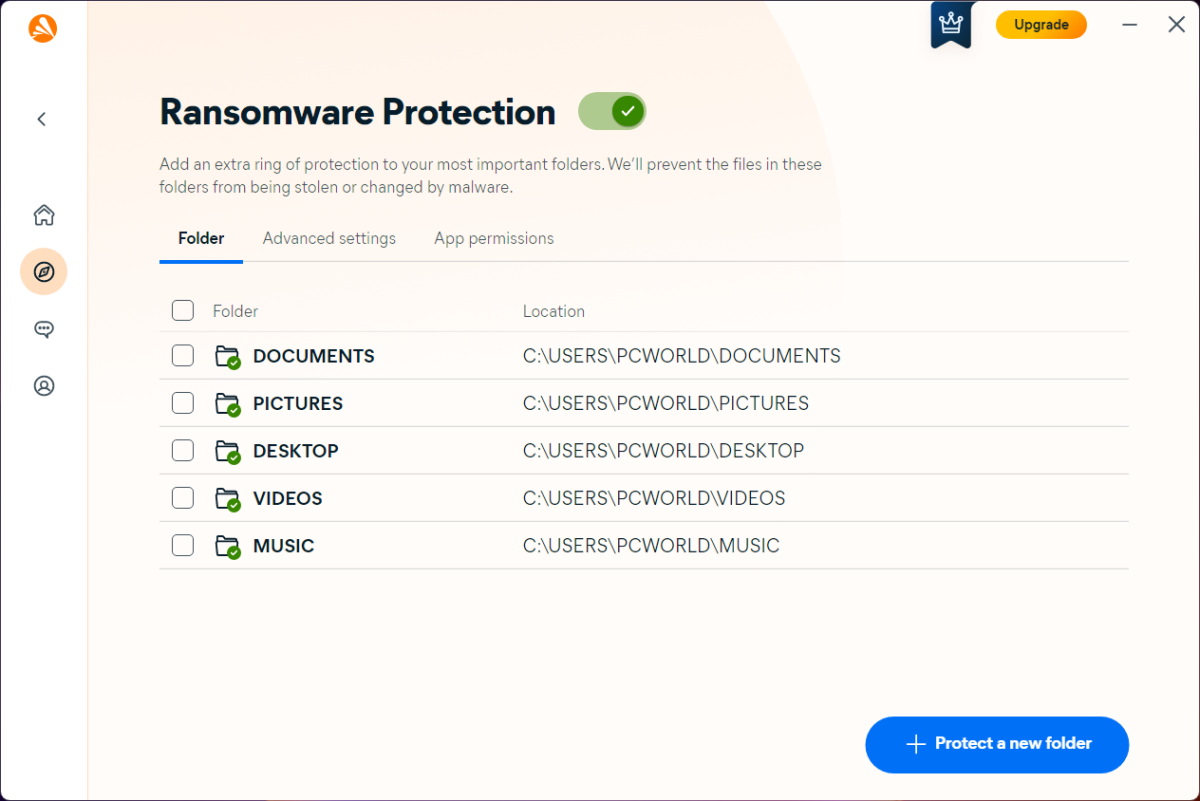
By default, Avast One protects select Windows folders from ransomware by limiting app access to them and certain file types within.
PCWorld
By default, Avast One monitors specific file types within your Documents, Pictures, Desktop, Videos, and Music folders, including documents, pictures, and videos. You can manually add more folders and file types (using file extensions like .tiff or .pdf) to the protected list. Well-known apps (e.g. Microsoft Word or Adobe Photoshop) automatically get access, but not any others.
For a stronger defense, you can change the settings to let only approved apps through, as well as wholesale protect all files within protected folders. But be aware these tighter restrictions can require intervention on your part to ensure apps like games still function normally.
Of course, for the best protection, you should still independently keep at least one current, offline copy of your files — like on an external drive you only connect to your PC when performing the backup. Your PC could fall to ransomware, but your data won’t be lost to you.
In addition to excellent malware protection, Avast One provides tools that simplify safeguarding your privacy and keeping your PC in tip-top shape
Additional features
Browser extensions
Avast One automatically screens and blocks malicious websites, but the optional Avast Online Security & Privacy extension can help you avoid clicking on bad links to begin with. Search results in Google and Bing get visual badges that indicate if a site is safe or not. They can be easy to miss at first, though, since the icons are smaller and more subtle.
The extension will also block trackers, several ad networks, and cookie permissions. In fact, it automatically requests only necessary cookies from sites. If you’re tired of pop-ups asking you for your cookie preferences, you’ll like the last feature. Having to manually install the extension becomes worth the effort.
Network Inspector
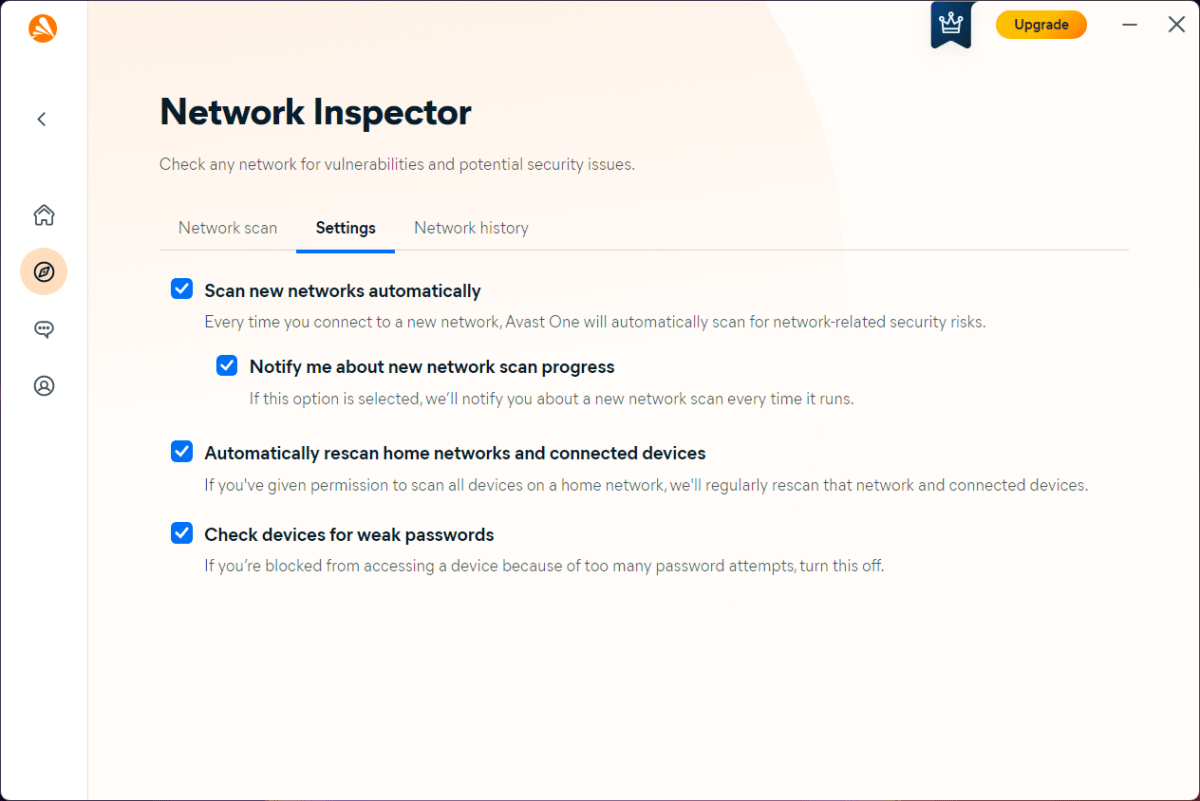
Avast One’s Network Inspector tool can be a good way to get verification that you’ve indeed done the basics to secure your home network.
PCWorld
Hopping onto a new network can expose you to vulnerabilities — an issue that Avast tries to solve with its Network Inspector feature. You run the scanner to look for potential threats lurking on the network you’re connected to, like DNS hijacking or a weak password on a router, or a vulnerable device.
This tool has limited utility, especially for public networks. To protect yourself on such connections, the answer is simple: Use the included VPN to maintain your security and privacy. For a private network that you trust (like the one you have at home), it can help you verify your router is configured with at least basic safeguards in place.
You can adjust the settings for automatic scanning and if devices are checked for weak passwords. You can also check to your connection history to see what networks you’ve recently used.
PC utilities (Disk Cleaner, Driver Updater, and Duplicate File Finder)
Avast One unlocks three additional utilities to help keep your PC running efficiently: Disk Cleaner, Driver Updater, and Duplicate File Finder.
Disk Cleaner and Driver Updater simplify tasks you can perform yourself in Windows. Disk Cleaner lets you dump temporary files, downloads, items in the Recycle Bin, broken shortcuts, and broken registry keys to free space on your PC. Driver Updater scans your PC for outdated drivers and handles updating any that are out of date.
Both have clean interfaces that are explained with clear, simple language, which is an improvement over poking around in Windows to do the same work. Disk Cleaner also lets you see exactly which temporary files are on the chopping block, and unselect specific categories to keep them around.
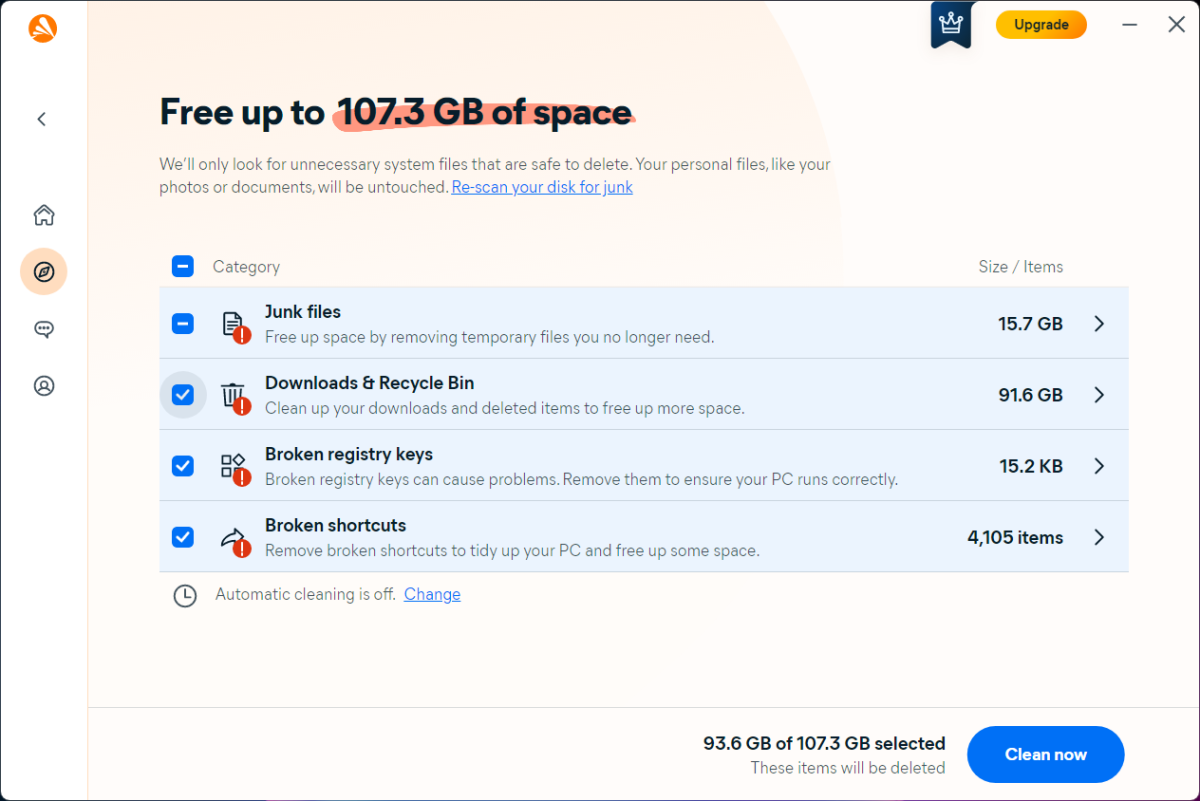
Avast One’s Disk Cleanup utility helps you purge temporary files from your PC — but its easy-to-use interface is a double-edged sword.
PCWorld
There’s just one downside to these two tools — how easy it is to use them. Disk Cleaner makes deleting elements from registry too quick and simple. Fiddling with your Windows registry can cause problems, so you should always understand what you’re changing; yet with Disk Cleaner, you can wipe parts of your registry without having to know where to dig and why. Similarly, updating a driver without knowing its source can also lead to later issues, though usually not as bad as a botched registry.
Happily, Duplicate File Finder gives no reason for concern. It performed surprisingly well in my light testing — the utility could tell the difference between files that were created separately but functionally the same, and actual copies with different names. Video files created as part of my Handbrake benchmarks are the same for real-world purposes, but the tool didn’t flag them. It did catch files I copied but renamed.
Sensitive Data Shield
Many people store files containing sensitive information on their computer, such as banking details, social security numbers, paycheck info, and even passwords — and that practice can become a liability if your computer is compromised.
(Side note: Storing passwords in a document on your PC is very insecure. Use a password manager with a database stored on your computer instead — it will encrypt the data and greatly strengthen your security.)
Avast tries to shield your PC from this threat with its Sensitive Data Shield feature. It scans your PC for documents for common types of private information, then restricts access to the list of the files found. Malicious apps won’t be able to discover and extract that data. You can manually flag additional files for protection, as well as allow or block specific apps.
The feature has limited effectiveness, though. The scanner doesn’t always catch every file with sensitive info — and it only looks for .pdf, .doc, .docx, .xls, and .xlsx files. You can’t manually add files of other types, either.
VPN
Accessing Avast One’s VPN is most easily done through the main dashboard, where you can instantly flip on a connection to the preselected server. You can also tap the tile to jump to the VPN Secure Connection screen, which lets you adjust a handful of settings.
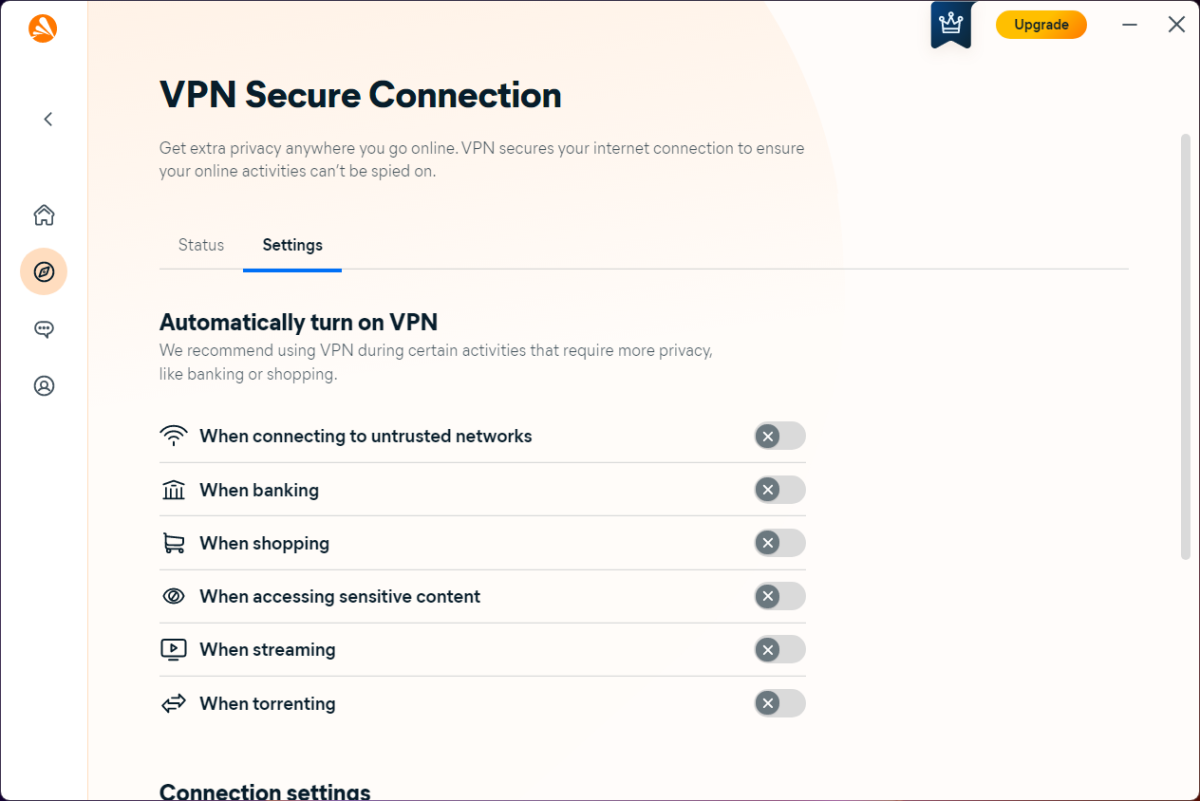
Avast One gives more granular control over automatic connection of the VPN when compared to some rivals.
PCWorld
If you choose the latter option, you can turn the VPN on and off, select a specific server, and change the connection settings. The VPN can be configured to automatically activate in certain scenarios, like when on an untrusted network (e.g., public Wi-Fi), a banking website, streaming, or shopping. It also supports peer-to-peer connections.
Additionally, you can toggle whether Avast sends autoconnection notifications, kills all internet traffic if the VPN accidentally disconnects while active, and allows your PC to see local devices (like printers) when the VPN is on. The first two features are enabled by default, while the latter is disabled.
Avast offers servers in 37 countries, which span Australia, Austria, Belgium, Brazil, Canada, Czech Republic, Denmark, Finland, France, Germany, Hungary, Iceland, Ireland, Israel, Italy, Japan, Latvia, Lithuania, Luxembourg, Malaysia, Mexico, Netherlands, New Zealand, Norway, Poland, Portugal, Republic of Singapore, South Africa, South Korea, Spain, Sweden, Switzerland, Taiwan, Turkey, UK, Ukraine, and the USA. You can choose a specific city for five countries (Australia, Canada, Germany, Spain, UK, and the USA).
Customer support
If you have questions about Avast One, you can use Avast’s support website or help forums to find answers. Customer service is also available by phone, email, or chat. The support website is the best place to start with for basic questions — there’s even a helpful user guide if you want to get properly acquainted with the software.
Updates and maintenance
Avast One automatically updates its virus definitions and the app itself in the background by default — you don’t have to check on it. However, you can change these settings so that you only get notified when updates are available, or go for complete manual control (not advisable). You can also manually check for updates in the app settings (Account > Settings > General).
Performance
Avast’s antivirus engine generally performs well in tests conducted by leading security research institutions. It detected 100 percent of the threats in AV-Test’s zero-day attack and malware evaluation for July and August 2024 (the most current results released). All 17,663 samples for recently discovered and widespread malware and 302 samples for zero-day attacks were blocked.
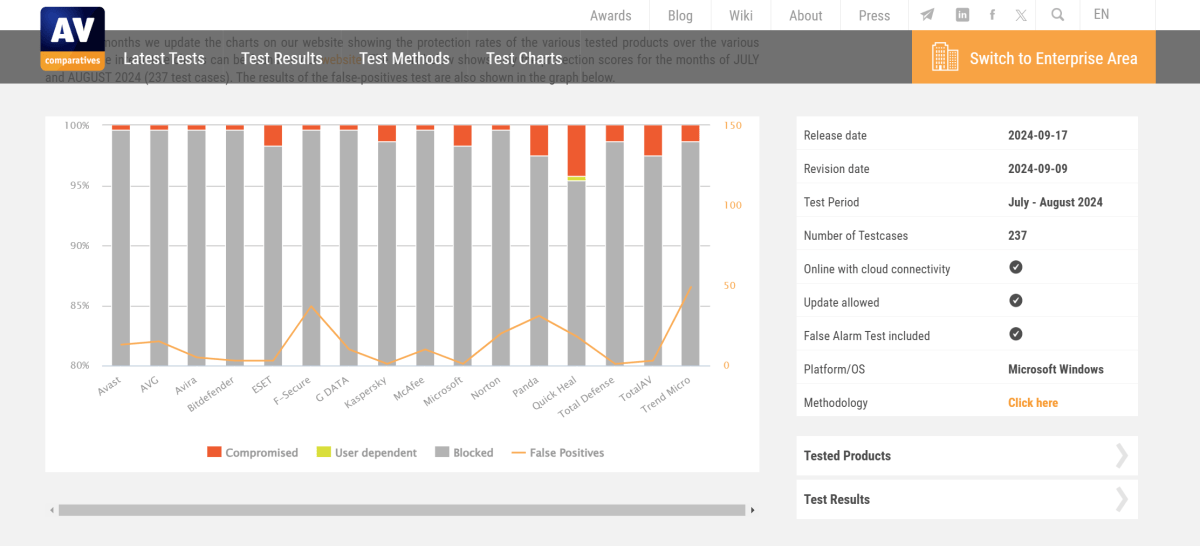
AV-Comparatives’ real-world test results for July and August 2024.
AV-Comparatives
In AV-Comparatives’ real-world protection test for July and August 2024, Avast also blocked 99.6 percent of the 237 test cases, with just 13 false positives. Its engine should notice and catch malicious web links, exploits (like drive-by downloads), and URLs that direct you to malware.
Avast also performed almost as well in AV-Comparatives’ September 2024 malware protection test, with a strong 99.93 percent online protection and 95.8 percent online detection rate. Its offline detection rate ranked near the top, coming in at 94.3 percent with four false positives.
For more sophisticated, targeted threats, Avast still has room to improve. It caught 12 of the 15 test cases in AV-Comparatives’ October 2024 Advanced Threat Protection Test, which involves threats like fileless attacks and malicious scripts. However, Avast caught test cases that higher performing rivals missed, suggesting that antivirus vendors are all still strengthening their protection in this area.
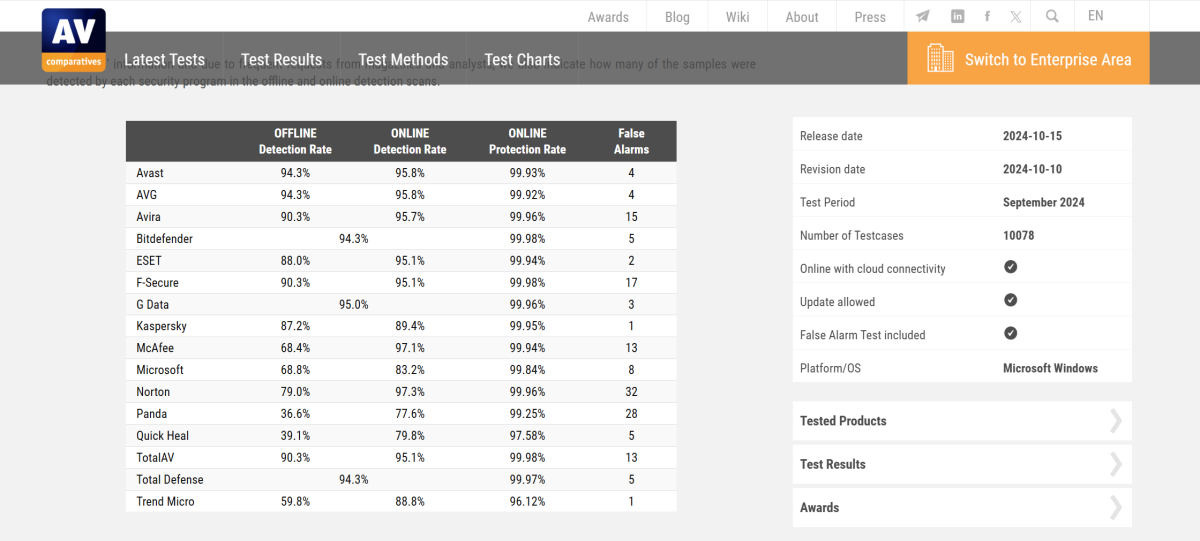
AV-Comparatives’ malware test results for September 2024.
AV-Comparatives
In daily use, expect Avast to have minimal impact on system resources during most typical tasks, especially when left idle in the background. When I ran PCMark 10’s Extended benchmark, which simulates web browsing, video chatting, gaming, and image and document editing in free, open-source apps, the scores remained the same as before installing Avast One. The software also had little effect on our Handbrake encoding test, which transforms a large, uncompressed video file into a smaller, compressed version. When running a deep scan continuously in the background, performance dipped by about 10 percent for both benchmarks — a modest amount compared to competitors.
The one exception to this behavior is when working on Microsoft Word, Excel, and PowerPoint documents. Avast was aggressive during in its scans when I ran UL Procyon’s Office Productivity benchmark, which focuses on Microsoft Office use. When Avast One was idle in the background, scores dropped by about 11 percent when idle. They fell by 25 percent when a deep scan was run continuously.
In the real world, these results suggest heavy Microsoft Office users on slower PCs should be strategic about the timing of scans. A full system scan scheduled for off-hours (like when you’re asleep) won’t interfere with getting work done. During active hours, you could see some performance effects when in Office apps, but not as notably.
Should you buy Avast One?
Avast One provides strong, broad defense against online threats, with features that make an upgrade from the free version (or Microsoft Defender) worthwhile. In addition to excellent malware protection, it provides tools that simplify safeguarding your privacy and keeping your PC in tip-top shape — and the interface for managing everything is clean and simple, to boot. This security suite does lack a password manager and parental controls, but if you’re set on those fronts, this app’s polish is hard to beat.
Editor’s note: Because online services are often iterative, gaining new features and performance improvements over time, this review is subject to change in order to accurately reflect the current state of the service. We’ve most recently updated it to include up-to-date protection result details.
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens' ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
1. EXECUTIVE SUMMARY
- CVSS v3 9.9
- ATTENTION: Exploitable remotely/low attack complexity/public exploits are available/known public exploitation
- Vendor: Siemens
- Equipment: SINEC INS
- Vulnerabilities: Improper Authentication, Out-of-bounds Write, Inefficient Regular Expression Complexity, Excessive Iteration, Reachable Assertion, Uncontrolled Resource Consumption, Improper Input Validation, Improper Check for Unusual or Exceptional Conditions, Memory Allocation with Excessive Size Value, Heap-based Buffer Overflow, Missing Encryption of Sensitive Data, Path Traversal, Incorrect Permission Assignment for Critical Resource, Exposure of Sensitive Information to an Unauthorized Actor, Covert Timing Channel, Truncation of Security-relevant Information, Integer Overflow or Wraparound, Use After Free, Code Injection, Path Traversal: 'dir/../../filename', Execution with Unnecessary Privileges, Server-Side Request Forgery (SSRF), OS Command Injection, HTTP Request/Response Smuggling, Use of Hard-coded Cryptographic Key, Insufficient Session Expiration
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow an unauthenticated attacker cause a denial-of-service condition, bypass permissions, access data they shouldn't have access to, or run arbitrary code.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
The following Siemens products are affected:
- SINEC INS: versions prior to V1.0 SP2 Update 3
3.2 Vulnerability Overview
3.2.1 IMPROPER AUTHENTICATION CWE-287
The AES-SIV cipher implementation contains a bug that causes it to ignore empty associated data entries which are unauthenticated as a consequence. Applications that use the AES-SIV algorithm and want to authenticate empty data entries as associated data can be mislead by removing adding or reordering such empty entries as these are ignored by the OpenSSL implementation. The AES-SIV algorithm allows for authentication of multiple associated data entries along with the encryption. To authenticate empty data the application has to call EVP_EncryptUpdate() (or EVP_CipherUpdate()) with NULL pointer as the output buffer and 0 as the input buffer length. The AES-SIV implementation in OpenSSL just returns success for such a call instead of performing the associated data authentication operation. The empty data thus will not be authenticated.
CVE-2023-2975 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N).
3.2.2 OUT-OF-BOUNDS WRITE CWE-787
The code that processes control channel messages sent to named calls certain functions recursively during packet parsing. Recursion depth is only limited by the maximum accepted packet size; depending on the environment, this may cause the packet-parsing code to run out of available stack memory, causing named to terminate unexpectedly. Since each incoming control channel message is fully parsed before its contents are authenticated, exploiting this flaw does not require the attacker to hold a valid RNDC key; only network access to the control channel's configured TCP port is necessary. This issue affects BIND 9 versions 9.2.0 through 9.16.43, 9.18.0 through 9.18.18, 9.19.0 through 9.19.16, 9.9.3-S1 through 9.16.43-S1, and 9.18.0-S1 through 9.18.18-S1.
CVE-2023-3341 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.3 INEFFICIENT REGULAR EXPRESSION COMPLEXITY CWE-1333
Applications that use the functions DH_check(), DH_check_ex() or EVP_PKEY_param_check() to check a DH key or DH parameters may experience long delays. Where the key or parameters that are being checked have been obtained from an untrusted source this may lead to a denial of service. The function DH_check() performs various checks on DH parameters. One of those checks confirms that the modulus ('p' parameter) is not too large. Trying to use a very large modulus is slow and OpenSSL will not normally use a modulus which is over 10,000 bits in length. However the DH_check() function checks numerous aspects of the key or parameters that have been supplied. Some of those checks use the supplied modulus value even if it has already been found to be too large. An application that calls DH_check() and supplies a key or parameters obtained from an untrusted source could be vulnerable to a denial-of-service attack. The function DH_check() is itself called by a number of other OpenSSL functions. An application calling any of those other functions may similarly be affected. The other functions affected by this are DH_check_ex() and EVP_PKEY_param_check(). Also vulnerable are the OpenSSL dhparam and pkeyparam command line applications when using the '-check' option. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are not affected by this issue.
CVE-2023-3446 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.4 EXCESSIVE ITERATION CWE-834
Applications that use the functions DH_check(), DH_check_ex() or EVP_PKEY_param_check() to check a DH key or DH parameters may experience long delays. Where the key or parameters that are being checked have been obtained from an untrusted source this may lead to a denial of service. The function DH_check() performs various checks on DH parameters. After fixing CVE-2023-3446 it was discovered that a large q parameter value can also trigger an overly long computation during some of these checks. A correct q value, if present, cannot be larger than the modulus p parameter, thus it is unnecessary to perform these checks if q is larger than p. An application that calls DH_check() and supplies a key or parameters obtained from an untrusted source could be vulnerable to a denial-of-service attack. The function DH_check() is itself called by a number of other OpenSSL functions. An application calling any of those other functions may similarly be affected. The other functions affected by this are DH_check_ex() and EVP_PKEY_param_check(). Also vulnerable are the OpenSSL dhparam and pkeyparam command line applications when using the "-check" option. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are not affected by this issue.
CVE-2023-3817 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.5 REACHABLE ASSERTION CWE-617
A flaw in the networking code handling DNS-over-TLS queries may cause named to terminate unexpectedly due to an assertion failure. This happens when internal data structures are incorrectly reused under significant DNS-over-TLS query load. This issue affects BIND 9 versions 9.18.0 through 9.18.18 and 9.18.11-S1 through 9.18.18-S1.
CVE-2023-4236 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.6 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
The DNS message parsing code in named includes a section whose computational complexity is overly high. It does not cause problems for typical DNS traffic, but crafted queries and responses may cause excessive CPU load on the affected named instance by exploiting this flaw. This issue affects both authoritative servers and recursive resolvers. This issue affects BIND 9 versions 9.0.0 through 9.16.45, 9.18.0 through 9.18.21, 9.19.0 through 9.19.19, 9.9.3-S1 through 9.11.37-S1, 9.16.8-S1 through 9.16.45-S1, and 9.18.11-S1 through 9.18.21-S1.
CVE-2023-4408 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.7 IMPROPER INPUT VALIDATION CWE-20
The POLY1305 MAC (message authentication code) implementation contains a bug that might corrupt the internal state of applications on the Windows 64 platform when running on newer X86_64 processors supporting the AVX512-IFMA instructions. If in an application that uses the OpenSSL library an attacker can influence whether the POLY1305 MAC algorithm is used, the application state might be corrupted with various application dependent consequences. The POLY1305 MAC (message authentication code) implementation in OpenSSL does not save the contents of non-volatile XMM registers on Windows 64 platform when calculating the MAC of data larger than 64 bytes. Before returning to the caller all the XMM registers are set to zero rather than restoring their previous content. The vulnerable code is used only on newer x86_64 processors supporting the AVX512-IFMA instructions. The consequences of this kind of internal application state corruption can be various - from no consequences, if the calling application does not depend on the contents of non-volatile XMM registers at all, to the worst consequences, where the attacker could get complete control of the application process. However given the contents of the registers are just zeroized so the attacker cannot put arbitrary values inside, the most likely consequence, if any, would be an incorrect result of some application dependent calculations or a crash leading to a denial of service. The POLY1305 MAC algorithm is most frequently used as part of the CHACHA20-POLY1305 AEAD (authenticated encryption with associated data) algorithm. The most common usage of this AEAD cipher is with TLS protocol versions 1.2 and 1.3 and a malicious client can influence whether this AEAD cipher is used by the server. This implies that server applications using OpenSSL can be potentially impacted. However we are currently not aware of any concrete application that would be affected by this issue therefore we consider this a Low severity security issue. As a workaround the AVX512-IFMA instructions support can be disabled at runtime by setting the environment variable OPENSSL_ia32cap: OPENSSL_ia32cap=:~0x200000 The FIPS provider is not affected by this issue.
CVE-2023-4807 has been assigned to this vulnerability. A CVSS v3 base score of 7.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.8 REACHABLE ASSERTION CWE-617
A flaw in query-handling code can cause named to exit prematurely with an assertion failure when: - nxdomain-redirect is configured, and - the resolver receives a PTR query for an RFC 1918 address that would normally result in an authoritative NXDOMAIN response. This issue affects BIND 9 versions 9.12.0 through 9.16.45, 9.18.0 through 9.18.21, 9.19.0 through 9.19.19, 9.16.8-S1 through 9.16.45-S1, and 9.18.11-S1 through 9.18.21-S1.
CVE-2023-5517 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.9 IMPROPER CHECK FOR UNUSUAL OR EXCEPTIONAL CONDITIONS CWE-754
Applications that use the functions DH_generate_key() to generate an X9.42 DH key may experience long delays. Likewise, applications that use DH_check_pub_key(), DH_check_pub_key_ex() or EVP_PKEY_public_check() to check an X9.42 DH key or X9.42 DH parameters may experience long delays. Where the key or parameters that are being checked have been obtained from an untrusted source this may lead to a denial of service. While DH_check() performs all the necessary checks (as of CVE-2023-3817), DH_check_pub_key() doesn't make any of these checks, and is therefore vulnerable for excessively large P and Q parameters. Likewise, while DH_generate_key() performs a check for an excessively large P, it doesn't check for an excessively large Q. An application that calls DH_generate_key() or DH_check_pub_key() and supplies a key or parameters obtained from an untrusted source could be vulnerable to a denial-of-service attack. DH_generate_key() and DH_check_pub_key() are also called by a number of other OpenSSL functions. An application calling any of those other functions may similarly be affected. The other functions affected by this are DH_check_pub_key_ex(), EVP_PKEY_public_check(), and EVP_PKEY_generate(). Also vulnerable are the OpenSSL pkey command line application when using the "-pubcheck" option, as well as the OpenSSL genpkey command line application. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are not affected by this issue.
CVE-2023-5678 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.10 REACHABLE ASSERTION CWE-617
A bad interaction between DNS64 and serve-stale may cause named to crash with an assertion failure during recursive resolution, when both of these features are enabled. This issue affects BIND 9 versions 9.16.12 through 9.16.45, 9.18.0 through 9.18.21, 9.19.0 through 9.19.19, 9.16.12-S1 through 9.16.45-S1, and 9.18.11-S1 through 9.18.21-S1.
CVE-2023-5679 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.11 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
A bad interaction between DNS64 and serve-stale may cause named to crash with an assertion failure during recursive resolution, when both of these features are enabled. This issue affects BIND 9 versions 9.16.12 through 9.16.45, 9.18.0 through 9.18.21, 9.19.0 through 9.19.19, 9.16.12-S1 through 9.16.45-S1, and 9.18.11-S1 through 9.18.21-S1.
CVE-2023-5680 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.12 OUT-OF-BOUNDS WRITE CWE-787
The POLY1305 MAC (message authentication code) implementation contains a bug that might corrupt the internal state of applications running on PowerPC CPU based platforms if the CPU provides vector instructions. If an attacker can influence whether the POLY1305 MAC algorithm is used, the application state might be corrupted with various application dependent consequences. The POLY1305 MAC (message authentication code) implementation in OpenSSL for PowerPC CPUs restores the contents of vector registers in a different order than they are saved. Thus the contents of some of these vector registers are corrupted when returning to the caller. The vulnerable code is used only on newer PowerPC processors supporting the PowerISA 2.07 instructions. The consequences of this kind of internal application state corruption can be various - from no consequences, if the calling application does not depend on the contents of non-volatile XMM registers at all, to the worst consequences, where the attacker could get complete control of the application process. However unless the compiler uses the vector registers for storing pointers, the most likely consequence, if any, would be an incorrect result of some application dependent calculations or a crash leading to a denial of service. The POLY1305 MAC algorithm is most frequently used as part of the CHACHA20-POLY1305 AEAD (authenticated encryption with associated data) algorithm. The most common usage of this AEAD cipher is with TLS protocol versions 1.2 and 1.3. If this cipher is enabled on the server a malicious client can influence whether this AEAD cipher is used. This implies that TLS server applications using OpenSSL can be potentially impacted.
CVE-2023-6129 has been assigned to this vulnerability. A CVSS v3 base score of 6.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:L/A:H).
3.2.13 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
Checking excessively long invalid RSA public keys may take a long time. Applications that use the function EVP_PKEY_public_check() to check RSA public keys may experience long delays. Where the key that is being checked has been obtained from an untrusted source this may lead to a denial of service. When function EVP_PKEY_public_check() is called on RSA public keys, a computation is done to confirm that the RSA modulus, n, is composite. For valid RSA keys, n is a product of two or more large primes and this computation completes quickly. However, if n is an overly large prime, then this computation would take a long time. An application that calls EVP_PKEY_public_check() and supplies an RSA key obtained from an untrusted source could be vulnerable to a denial-of-service attack. The function EVP_PKEY_public_check() is not called from other OpenSSL functions however it is called from the OpenSSL pkey command line application. For that reason that application is also vulnerable if used with the '-pubin' and '-check' options on untrusted data. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are affected by this issue.
CVE-2023-6237 has been assigned to this vulnerability. A CVSS v3 base score of 5.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.14 MEMORY ALLOCATION WITH EXCESSIVE SIZE VALUE CWE-789
To keep its cache database efficient, named running as a recursive resolver occasionally attempts to clean up the database. It uses several methods, including some that are asynchronous: a small chunk of memory pointing to the cache element that can be cleaned up is first allocated and then queued for later processing. It was discovered that if the resolver is continuously processing query patterns triggering this type of cache-database maintenance, named may not be able to handle the cleanup events in a timely manner. This in turn enables the list of queued cleanup events to grow infinitely large over time, allowing the configured max-cache-size limit to be significantly exceeded. This issue affects BIND 9 versions 9.16.0 through 9.16.45 and 9.16.8-S1 through 9.16.45-S1.
CVE-2023-6516 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.15 HEAP-BASED BUFFER OVERFLOW CWE-122
A vulnerability was found in SQLite SQLite3 up to 3.43.0 and classified as critical. This issue affects the function sessionReadRecord of the file ext/session/sqlite3session.c of the component make all test Handler. The manipulation leads to heap-based buffer overflow. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-248999.
CVE-2023-7104 has been assigned to this vulnerability. A CVSS v3 base score of 5.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L).
3.2.16 MISSING ENCRYPTION OF SENSITIVE DATA CWE-311
The use of Module._load() can bypass the policy mechanism and require modules outside of the policy.json definition for a given module. This vulnerability affects all users using the experimental policy mechanism in all active release lines: 16.x, 18.x and, 20.x. Note that at the time this CVE was issued, the policy was an experimental feature of Node.js.
CVE-2023-32002 has been assigned to this vulnerability. A CVSS v3 base score of 9.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
3.2.17 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
fs.mkdtemp() and fs.mkdtempSync() can be used to bypass the permission model check using a path traversal attack. This flaw arises from a missing check in the fs.mkdtemp() API and the impact is a malicious actor could create an arbitrary directory. This vulnerability affects all users using the experimental permission model in Node.js 20. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-32003 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N).
3.2.18 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
A vulnerability has been discovered in Node.js version 20, specifically within the experimental permission model. This flaw relates to improper handling of buffers in file system APIs causing a traversal path to bypass when verifying file permissions. This vulnerability affects all users using the experimental permission model in Node.js 20. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-32004 has been assigned to this vulnerability. A CVSS v3 base score of 8.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.19 INCORRECT PERMISSION ASSIGNMENT FOR CRITICAL RESOURCE CWE-732
A vulnerability has been identified in Node.js version 20, affecting users of the experimental permission model when the --allow-fs-read flag is used with a non-* argument. This flaw arises from an inadequate permission model that fails to restrict file stats through the fs.statfs API. As a result, malicious actors can retrieve stats from files that they do not have explicit read access to. This vulnerability affects all users using the experimental permission model in Node.js 20. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-32005 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N).
3.2.20 MISSING ENCRYPTION OF SENSITIVE DATA CWE-311
The use of module.constructor.createRequire() can bypass the policy mechanism and require modules outside of the policy.json definition for a given module. This vulnerability affects all users using the experimental policy mechanism in all active release lines: 16.x, 18.x, and, 20.x. Note that at the time this CVE was issued, the policy was an experimental feature of Node.js.
CVE-2023-32006 has been assigned to this vulnerability. A CVSS v3 base score of 8.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.21 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
The use of the deprecated API process.binding() can bypass the permission model through path traversal. This vulnerability affects all users using the experimental permission model in Node.js 20.x. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-32558 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N).
3.2.22 MISSING ENCRYPTION OF SENSITIVE DATA CWE-311
A privilege escalation vulnerability exists in the experimental policy mechanism in all active release lines: 16.x, 18.x and, 20.x. The use of the deprecated API process.binding() can bypass the policy mechanism by requiring internal modules and eventually take advantage of process.binding('spawn_sync') run arbitrary code, outside of the limits defined in a policy.json file. Note that at the time this CVE was issued, the policy was an experimental feature of Node.js.
CVE-2023-32559 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.23 IMPROPER INPUT VALIDATION CWE-20
When the Node.js policy feature checks the integrity of a resource against a trusted manifest, the application can intercept the operation and return a forged checksum to the node's policy implementation, thus effectively disabling the integrity check. This vulnerability affects all users using the experimental policy mechanism in all active release lines: 18.x and, 20.x. At the time this CVE was issued, the policy mechanism was an experimental feature of Node.js.
CVE-2023-38552 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N).
3.2.24 IMPROPER INPUT VALIDATION CWE-20
A previously disclosed vulnerability (CVE-2023-30584) was patched insufficiently in commit 205f1e6. The new path traversal vulnerability arises because the implementation does not protect itself against the application overwriting built-in utility functions with user-defined implementations. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-39331 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N).
3.2.25 IMPROPER INPUT VALIDATION CWE-20
Various node:fs functions allow specifying paths as either strings or Uint8Array objects. In Node.js environments, the Buffer class extends the Uint8Array class. Node.js prevents path traversal through strings (see CVE-2023-30584) and Buffer objects (see CVE-2023-32004), but not through non-Buffer Uint8Array objects. This is distinct from CVE-2023-32004 which only referred to Buffer objects. However, the vulnerability follows the same pattern using Uint8Array instead of Buffer. At the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-39332 has been assigned to this vulnerability. A CVSS v3 base score of 9.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
3.2.26 IMPROPER INPUT VALIDATION CWE-20
Maliciously crafted export names in an imported WebAssembly module can inject JavaScript code. The injected code may be able to access data and functions that the WebAssembly module itself does not have access to, similar to as if the WebAssembly module was a JavaScript module.
CVE-2023-39333 has been assigned to this vulnerability. A CVSS v3 base score of 6.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N).
3.2.27 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
CVE-2023-44487 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.28 EXPOSURE OF SENSITIVE INFORMATION TO AN UNAUTHORIZED ACTOR CWE-200
Undici is an HTTP/1.1 client written from scratch for Node.js. Prior to version 5.26.2, Undici already cleared authorization headers on cross-origin redirects, but did not clear cookie headers. By design, cookie headers are forbidden request headers, disallowing them to be set in RequestInit.headers in browser environments. Since undici handles headers more liberally than the spec, there was a disconnect from the assumptions the spec made, and undici's implementation of fetch. As such this may lead to accidental leakage of cookie to a third-party site or a malicious attacker who can control the redirection target (ie. an open redirector) to leak the cookie to the third party site. This was patched in version 5.26.2. There are no known workarounds.
CVE-2023-45143 has been assigned to this vulnerability. A CVSS v3 base score of 3.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:U/C:L/I:L/A:L).
3.2.29 COVERT TIMING CHANNEL CWE-385
Node.js versions which bundle an unpatched version of OpenSSL or run against a dynamically linked version of OpenSSL which are unpatched are vulnerable to the Marvin Attack - https://people.redhat.com/~hkario/marvin/, if PCKS #1 v1.5 padding is allowed when performing RSA descryption using a private key.
CVE-2023-46809 has been assigned to this vulnerability. A CVSS v3 base score of 7.4 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N).
3.2.30 OUT-OF-BOUNDS WRITE CWE-787
A vulnerability was found in perl 5.30.0 through 5.38.0. This issue occurs when a crafted regular expression is compiled by perl, which can allow an attacker controlled byte buffer overflow in a heap allocated buffer.
CVE-2023-47038 has been assigned to this vulnerability. A CVSS v3 base score of 7.0 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.31 HEAP-BASED BUFFER OVERFLOW CWE-122
This security issue occurs while Perl for Windows relies on the system path environment variable to find the shell (cmd.exe). When running an executable that uses the Windows Perl interpreter, Perl attempts to find and execute cmd.exe within the operating system. However, due to path search order issues, Perl initially looks for cmd.exe in the current working directory. This flaw allows an attacker with limited privileges to placecmd.exe in locations with weak permissions, such as C:\ProgramData. By doing so, arbitrary code can be executed when an administrator attempts to use this executable from these compromised locations.
CVE-2023-47039 has been assigned to this vulnerability. A CVSS v3 base score of 7.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.32 IMPROPER INPUT VALIDATION CWE-20
In Perl before 5.38.2, S_parse_uniprop_string in regcomp.c can write to unallocated space because a property name associated with a \p{...} regular expression construct is mishandled. The earliest affected version is 5.30.0.
CVE-2023-47100 has been assigned to this vulnerability. A CVSS v3 base score of 9.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
3.2.33 TRUNCATION OF SECURITY-RELEVANT INFORMATION CWE-222
The SSH transport protocol with certain OpenSSH extensions, found in OpenSSH before 9.6 and other products, allows remote attackers to bypass integrity checks such that some packets are omitted (from the extension negotiation message), and a client and server may consequently end up with a connection for which some security features have been downgraded or disabled, aka a Terrapin attack. This occurs because the SSH Binary Packet Protocol (BPP), implemented by these extensions, mishandles the handshake phase and mishandles use of sequence numbers. For example, there is an effective attack against SSH's use of ChaCha20-Poly1305 (and CBC with Encrypt-then-MAC). The bypass occurs in [email protected] and (if CBC is used) the [email protected] MAC algorithms. This also affects Maverick Synergy Java SSH API before 3.1.0-SNAPSHOT, Dropbear through 2022.83, Ssh before 5.1.1 in Erlang/OTP, PuTTY before 0.80, AsyncSSH before 2.14.2, golang.org/x/crypto before 0.17.0, libssh before 0.10.6, libssh2 through 1.11.0, Thorn Tech SFTP Gateway before 3.4.6, Tera Term before 5.1, Paramiko before 3.4.0, jsch before 0.2.15, SFTPGo before 2.5.6, Netgate pfSense Plus through 23.09.1, Netgate pfSense CE through 2.7.2, HPN-SSH through 18.2.0, ProFTPD before 1.3.8b (and before1.3.9rc2), ORYX CycloneSSH before 2.3.4, NetSarang XShell 7 before Build 0144, CrushFTP before 10.6.0, ConnectBot SSH library before 2.2.22, Apache MINA sshd through 2.11.0, sshj through 0.37.0, TinySSH through 20230101, trilead-ssh2 6401, the net-ssh gem 7.2.0 for Ruby, the mscdex ssh2 module before 1.15.0 for Node.js, the thrussh library before 0.35.1 for Rust, and the Russh crate before 0.40.2 for Rust; and there could be effects on Bitvise SSH through 9.31.
CVE-2023-48795 has been assigned to this vulnerability. A CVSS v3 base score of 5.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:H/A:N).
3.2.34 IMPROPER INPUT VALIDATION CWE-20
Certain DNSSEC aspects of the DNS protocol (in RFC 4033, 4034, 4035, 6840, and related RFCs) allow remote attackers to cause a denial of service (CPU consumption) via one or more DNSSEC responses, aka the "KeyTrap" issue. One of the concerns is that, when there is a zone with many DNSKEY and RRSIG records, the protocol specification implies that an algorithm must evaluate all combinations of DNSKEY and RRSIG records.
CVE-2023-50387 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.35 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
The Closest Enclosure Proof aspect of the DNS protocol (in RFC 5155 when RFC 9276 guidance is skipped) allows remote attackers to cause a denial of service (CPU consumption for SHA-1 computations) via DNSSEC responses in a random subdomain attack, aka the "NSEC3" issue. The RFC 5155 specification implies that an algorithm must perform thousands of iterations of a hash function in certain situations.
CVE-2023-50868 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.36 INTEGER OVERFLOW OR WRAPAROUND CWE-190
UTF32Encoding.cpp in POCO has a Poco::UTF32Encoding integer overflow and resultant stack buffer overflow because Poco::UTF32Encoding::convert() and Poco::UTF32::queryConvert() may return a negative integer if a UTF-32 byte sequence evaluates to a value of 0x80000000 or higher. This is fixed in 1.11.8p2, 1.12.5p2, and 1.13.0.
CVE-2023-52389 has been assigned to this vulnerability. A CVSS v3 base score of 9.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
3.2.37 USE AFTER FREE CWE-416
A heap use-after-free issue has been identified in SQLite in the jsonParseAddNodeArray() function in sqlite3.c. This flaw allows a local attacker to leverage a victim to pass specially crafted malicious input to the application, potentially causing a crash and leading to a denial of service.
CVE-2024-0232 has been assigned to this vulnerability. A CVSS v3 base score of 4.7 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:H/PR:N/UI:R/S:U/C:N/I:N/A:H).
3.2.38 IMPROPER INPUT VALIDATION CWE-20
Processing a maliciously formatted PKCS12 file may lead OpenSSL to crash leading to a potential denial-of-service attack. Applications loading files in the PKCS12 format from untrusted sources might terminate abruptly. A file in PKCS12 format can contain certificates and keys and may come from an untrusted source. The PKCS12 specification allows certain fields to be NULL, but OpenSSL does not correctly check for this case. This can lead to a NULL pointer dereference that results in OpenSSL crashing. If an application processes PKCS12 files from an untrusted source using the OpenSSL APIs then that application will be vulnerable to this issue. OpenSSL APIs that are vulnerable to this are: PKCS12_parse(), PKCS12_unpack_p7data(), PKCS12_unpack_p7encdata(), PKCS12_unpack_authsafes() and PKCS12_newpass(). We have also fixed a similar issue in SMIME_write_PKCS7(). However since this function is related to writing data we do not consider it security significant. The FIPS modules in 3.2, 3.1 and 3.0 are not affected by this issue.
CVE-2024-0727 has been assigned to this vulnerability. A CVSS v3 base score of 5.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H).
3.2.39 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
Some non-default TLS server configurations can cause unbounded memory growth when processing TLSv1.3 sessions. An attacker may exploit certain server configurations to trigger unbounded memory growth that would lead to a denial of service. This problem can occur in TLSv1.3 if the non-default SSL_OP_NO_TICKET option is being used (but not if early_data support is also configured and the default anti-replay protection is in use). In this case, under certain conditions, the session cache can get into an incorrect state and it will fail to flush properly as it fills. The session cache will continue to grow in an unbounded manner. A malicious client could deliberately create the scenario for this failure to force a denial of service. It may also happen by accident in normal operation. This issue only affects TLS servers supporting TLSv1.3. It does not affect TLS clients. The FIPS modules in 3.2, 3.1 and 3.0 are not affected by this issue. OpenSSL 1.0.2 is also not affected by this issue.
CVE-2024-2511 has been assigned to this vulnerability. A CVSS v3 base score of 3.7 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.40 USE AFTER FREE CWE-416
Calling the OpenSSL API function SSL_free_buffers may cause memory to be accessed that was previously freed in some situations
CVE-2024-4741 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.41 EXPOSURE OF SENSITIVE INFORMATION TO AN UNAUTHORIZED ACTOR CWE-200
Calling the OpenSSL API function SSL_select_next_proto with an empty supported client protocols buffer may cause a crash or memory contents to be sent to the peer. A buffer overread can have a range of potential consequences such as unexpected application behavior or a crash. In particular this issue could result in up to 255 bytes of arbitrary private data from memory being sent to the peer leading to a loss of confidentiality. However, only applications that directly call the SSL_select_next_proto function with a 0 length list of supported client protocols are affected by this issue. This would normally never be a valid scenario and is typically not under attacker control but may occur by accident in the case of a configuration or programming error in the calling application. The OpenSSL API function SSL_select_next_proto is typically used by TLS applications that support ALPN (Application Layer Protocol Negotiation) or NPN (Next Protocol Negotiation). NPN is older, was never standardized and is deprecated in favor of ALPN. We believe that ALPN is significantly more widely deployed than NPN. The SSL_select_next_proto function accepts a list of protocols from the server and a list of protocols from the client and returns the first protocol that appears in the server list that also appears in the client list. In the case of no overlap between the two lists it returns the first item in the client list. In either case it will signal whether an overlap between the two lists was found. In the case where SSL_select_next_proto is called with a zero length client list it fails to notice this condition and returns the memory immediately following the client list pointer (and reports that there was no overlap in the lists). This function is typically called from a server side application callback for ALPN or a client side application callback for NPN. In the case of ALPN the list of protocols supplied by the client is guaranteed by libssl to never be zero in length. The list of server protocols comes from the application and should never normally be expected to be of zero length. In this case if the SSL_select_next_proto function has been called as expected (with the list supplied by the client passed in the client/client_len parameters), then the application will not be vulnerable to this issue. If the application has accidentally been configured with a zero length server list, and has accidentally passed that zero length server list in the client/client_len parameters, and has additionally failed to correctly handle a "no overlap" response (which would normally result in a handshake failure in ALPN) then it will be vulnerable to this problem. In the case of NPN, the protocol permits the client to opportunistically select a protocol when there is no overlap. OpenSSL returns the first client protocol in the no overlap case in support of this. The list of client protocols comes from the application and should never normally be expected to be of zero length. However if the SSL_select_next_proto function is accidentally called with a client_len of 0 then an invalid memory pointer will be returned instead. If the application uses this output as the opportunistic protocol then the loss of confidentiality will occur. This issue has been assessed as Low severity because applications are most likely to be vulnerable if they are using NPN instead of ALPN - but NPN is not widely used. It also requires an application configuration or programming error. Finally, this issue would not typically be under attacker control making active exploitation unlikely. The FIPS modules in 3.3, 3.2, 3.1 and 3.0 are not affected by this issue. Due to the low severity of this issue we are not issuing new releases of OpenSSL at this time. The fix will be included in the next releases when they become available.
CVE-2024-5535 has been assigned to this vulnerability. A CVSS v3 base score of 5.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N).
3.2.42 IMPROPER AUTHENTICATION CWE-287
The Node.js Permission Model does not clarify in the documentation that wildcards should be only used as the last character of a file path. For example: --allow-fs-read=/home/node/.ssh/*.pub will ignore pub and give access to everything after .ssh/. This misleading documentation affects all users using the experimental permission model in Node.js 20 and Node.js 21. At the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2024-21890 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N).
3.2.43 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
Node.js could allow a remote attacker to bypass security restrictions, caused by improper path traversal sequence sanitization. By using a path traversal attack, an attacker could exploit this vulnerability leading to filesystem permission model bypass.
CVE-2024-21891 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N).
3.2.44 IMPROPER CONTROL OF GENERATION OF CODE ('CODE INJECTION') CWE-94
Node.js could allow a local authenticated attacker to gain elevated privileges on the system, caused by a bug in the implementation of the exception of CAP_NET_BIND_SERVICE. An attacker could exploit this vulnerability to inject code that inherits the process's elevated privileges.
CVE-2024-21892 has been assigned to this vulnerability. A CVSS v3 base score of 7.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.45 PATH TRAVERSAL: 'DIR/../../FILENAME' CWE-27
Node.js could allow a remote attacker to traverse directories on the system. By monkey-patching buffer internals, namely, Buffer.prototype.utf8Write, an attacker could send a specially crafted URL request containing "dot dot" sequences (/../) to read arbitrary files on the system.
CVE-2024-21896 has been assigned to this vulnerability. A CVSS v3 base score of 7.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:N).
3.2.46 EXECUTION WITH UNNECESSARY PRIVILEGES CWE-250
setuid() does not affect libuv's internal io_uring operations if initialized before the call to setuid(). This allows the process to perform privileged operations despite presumably having dropped such privileges through a call to setuid(). This vulnerability affects all users using version greater or equal than Node.js 18.18.0, Node.js 20.4.0 and Node.js 21.
CVE-2024-22017 has been assigned to this vulnerability. A CVSS v3 base score of 7.3 has been calculated; the CVSS vector string is (CVSS:3.0/AV:L/AC:L/PR:H/UI:N/S:C/C:L/I:H/A:L).
3.2.47 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
A vulnerability in Node.js HTTP servers allows an attacker to send a specially crafted HTTP request with chunked encoding, leading to resource exhaustion and denial of service. The server reads an unbounded number of bytes from a single connection, exploiting the lack of limitations on chunk extension bytes. The issue can cause CPU and network bandwidth exhaustion, bypassing standard safeguards like timeouts and body size limits.
CVE-2024-22019 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.48 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
Node.js is vulnerable to a denial of service, caused by a resource exhaustion vulnerability in fetch() brotli decoding . By sending a specially crafted request, a remote attacker could exploit this vulnerability to cause a denial-of-service condition.
CVE-2024-22025 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.49 EXPOSURE OF SENSITIVE INFORMATION TO AN UNAUTHORIZED ACTOR CWE-200
Undici is an HTTP/1.1 client, written from scratch for Node.js. Undici already cleared authorization headers on cross-origin redirects, but did not clear Proxy-Authentication headers. This issue has been patched in versions 5.28.3 and 6.6.1. Users are advised to upgrade. There are no known workarounds for this vulnerability.
CVE-2024-24758 has been assigned to this vulnerability. A CVSS v3 base score of 3.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:U/C:L/I:L/A:L).
3.2.50 SERVER-SIDE REQUEST FORGERY (SSRF) CWE-918
libuv is a multi-platform support library with a focus on asynchronous I/O. The uv_getaddrinfo function in src/unix/getaddrinfo.c (and its windows counterpart src/win/getaddrinfo.c), truncates hostnames to 256 characters before calling getaddrinfo. This behavior can be exploited to create addresses like 0x00007f000001, which are considered valid by getaddrinfo and could allow an attacker to craft payloads that resolve to unintended IP addresses, bypassing developer checks. The vulnerability arises due to how the hostname_ascii variable (with a length of 256 bytes) is handled in uv_getaddrinfo and subsequently in uv__idna_toascii. When the hostname exceeds 256 characters, it gets truncated without a terminating null byte. As a result attackers may be able to access internal APIs or for websites (similar to MySpace) that allows users to have username.example.com pages. Internal services that crawl or cache these user pages can be exposed to SSRF attacks if a malicious user chooses a long vulnerable username. This issue has been addressed in release version 1.48.0. Users are advised to upgrade. There are no known workarounds for this vulnerability.
CVE-2024-24806 has been assigned to this vulnerability. A CVSS v3 base score of 7.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L).
3.2.51 IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN AN OS COMMAND ('OS COMMAND INJECTION') CWE-78
Node.js could allow a remote attacker to execute arbitrary commands on the system, caused by the improper handling of batch files in child_process.spawn / child_process.spawnSync. By sending a specially crafted command line argument using args parameter, an attacker could exploit this vulnerability to inject and execute arbitrary commands on the system.
CVE-2024-27980 has been assigned to this vulnerability. A CVSS v3 base score of 7.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L).
3.2.52 INCONSISTENT INTERPRETATION OF HTTP REQUESTS ('HTTP REQUEST/RESPONSE SMUGGLING') CWE-444
A vulnerability in the http server, where malformed headers can lead to HTTP request smuggling. Specifically, if a space is placed before a content-length header, it is not interpreted correctly, enabling attackers to smuggle in a second request within the body of the first.
CVE-2024-27982 has been assigned to this vulnerability. A CVSS v3 base score of 6.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N).
3.2.53 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
Node.js is vulnerable to a denial of service, caused by an assertion failure in node::http2::Http2Session::~Http2Session(). By sending a small amount of HTTP/2 frames packets with a few HTTP/2 frames inside, an attacker could exploit this vulnerability to cause the HTTP/2 server to crash.
CVE-2024-27983 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.54 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
The affected application does not properly sanitize user provided paths for SFTP-based file up- and downloads. This could allow an authenticated remote attacker to manipulate arbitrary files on the filesystem and achieve arbitrary code execution on the device.
CVE-2024-46888 has been assigned to this vulnerability. A CVSS v3 base score of 9.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H).
3.2.55 USE OF HARD-CODED CRYPTOGRAPHIC KEY CWE-321
The affected application uses hard-coded cryptographic key material to obfuscate configuration files. This could allow an attacker to learn that cryptographic key material through reverse engineering of the application binary and decrypt arbitrary backup files.
CVE-2024-46889 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N).
3.2.56 IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN AN OS COMMAND ('OS COMMAND INJECTION') CWE-78
The affected application does not properly validate input sent to specific endpoints of its web API. This could allow an authenticated remote attacker with high privileges on the application to execute arbitrary code on the underlying OS.
CVE-2024-46890 has been assigned to this vulnerability. A CVSS v3 base score of 9.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H).
3.2.57 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
The affected application does not properly restrict the size of generated log files. This could allow an unauthenticated remote attacker to trigger a large amount of logged events to exhaust the system's resources and create a denial-of-service condition.
CVE-2024-46891 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.58 INSUFFICIENT SESSION EXPIRATION CWE-613
The affected application does not properly invalidate sessions when the associated user is deleted or disabled or their permissions are modified. This could allow an authenticated attacker to continue performing malicious actions even after their user account has been disabled.
CVE-2024-46892 has been assigned to this vulnerability. A CVSS v3 base score of 4.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:N).
3.2.59 EXPOSURE OF SENSITIVE INFORMATION TO AN UNAUTHORIZED ACTOR CWE-200
The affected application does not properly validate authorization of a user to query the "/api/sftp/users" endpoint. This could allow an authenticated remote attacker to gain knowledge about the list of configured users of the SFTP service and also modify that configuration.
CVE-2024-46894 has been assigned to this vulnerability. A CVSS v3 base score of 6.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Siemens reported these vulnerabilities to CISA.
4. MITIGATIONS
Siemens has released SINEC INS V1.0 SP2 Update 3 and recommends updating to the latest version.
Siemens has identified the following specific workarounds and mitigations users can apply to reduce risk:
As a general security measure, Siemens recommends protecting network access to devices with appropriate mechanisms. To operate the devices in a protected IT environment, Siemens recommends configuring the environment according to Siemens' operational guidelines for industrial security and following recommendations in the product manuals.
Additional information on industrial security by Siemens can be found on the Siemens industrial security webpage
For more information see the associated Siemens security advisory SSA-915275 in HTML and CSAF.
CISA recommends users take defensive measures to minimize the risk of exploitation of these vulnerabilities. CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov in the technical information paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
5. UPDATE HISTORY
- November 14, 2024: Initial Publication
Finding a reliable site to stream anime can be a daunting task, especially with the countless options available in 2024. Many free anime sites are not only riddled with ads but also operate illegally, posing risks to your online security and privacy. To help you navigate this overwhelming landscape, I've compiled a list of the...
Want to meet people in a new city on Hinge? Whether traveling, moving, or just exploring, changing your Hinge location can open up new connections. Find out how to do it in this guide.
L’article How to change location on Hinge est apparu en premier sur Comparitech.
Nation-state adversaries are changing their approach, pivoting from data destruction to prioritizing stealth and espionage. According to the Microsoft 2023 Digital Defense Report, “nation-state attackers are increasing their investments and launching more sophisticated cyberattacks to evade detection and achieve strategic priorities.” These actors pose a critical threat to United States infrastructure and protected data, and […]
The post Adversarial advantage: Using nation-state threat analysis to strengthen U.S. cybersecurity appeared first on Security Intelligence.
According to the HIPAA Journal, data breaches have increased by 51.5% in the past month alone making healthcare organizations to prioritize cybersecurity.
The post Why a Cyber-healthy Network is Essential for Patient Safety? appeared first on Fidelis Security.
The Federal Bureau of Investigation (FBI) is urging police departments and governments worldwide to beef up security around their email systems, citing a recent increase in cybercriminal services that use hacked police email accounts to send unauthorized subpoenas and customer data requests to U.S.-based technology companies.
Stealer malware is a type of malicious software designed to infiltrate computers and extract sensitive information. Once installed, it communicates with a command-and-control server operated by threat actors and enables data theft like saved passwords and browser cookies. Security experts at CheckPoint recently warned of fake copyright claims that deliver Rhadamanthys stealer malware. A widespread […]
The post Beware of Fake Copyright Claims That Deliver Rhadamanthys Stealer appeared first on Cyber Security News.
Learn how social engineering and insider threats are major reasons for data loss and explore strategies to prevent them with advanced monitoring solutions.
The post Leading Reasons for Data Loss: Social Engineering and Insider Threats appeared first on Fidelis Security.
Not every court is affected in the same way, but many are struggling.
1. EXECUTIVE SUMMARY
- CVSS v4 8.7
- ATTENTION: Exploitable remotely/low attack complexity
- Vendor: Bosch Rexroth
- Equipment: IndraDrive
- Vulnerability: Uncontrolled Resource Consumption
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow an attacker to cause a denial-of-service, rendering the device unresponsive by sending arbitrary UDP messages.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Bosch Rexroth reports that the following versions of IndraDrive, servo drive system, are affected:
- Bosch Rexroth AG IndraDrive FWA-INDRV*-MP*: 17VRS < 20V36
3.2 Vulnerability Overview
3.2.1 Uncontrolled Resource Consumption CWE-400
A vulnerability in the PROFINET stack implementation of the IndraDrive of Bosch Rexroth allows an attacker to cause a denial-of-service, rendering the device unresponsive by sending arbitrary UDP messages.
CVE-2024-48989 has been assigned to this vulnerability. A CVSS v3.1 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
A CVSS v4 score has also been calculated for CVE-2024-48989. A base score of 8.7 has been calculated; the CVSS vector string is (CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:N/VI:N/VA:H/SC:N/SI:N/SA:N).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Roni Gavrilov from OTORIO reported this vulnerability to CISA.
4. MITIGATIONS
Bosch Rexroth has fixed this vulnerability starting with FWA-INDRV-MP-20V36. Bosch Rexroth recommends updating as soon as possible.
In use cases in which a device update is not possible or not feasible, Bosch Rexroth recommends compensatory measures which prevent or at least complicate taking advantage of the vulnerability. Always define such compensatory measures individually, in the context of the operational environment.
Some possible measures are described in "Security Manual Electric Drives and Controls", like network segmentation. In general, it is highly recommended to implement the measures described in "Security Manual Drives and Controls".
For more information, refer to the Bosch PSIRT Security Advisory BOSCH-SA-2584444
Please contact the Bosch PSIRT if you have feedback, comments, or additional information about this vulnerability at: [email protected] .
CISA recommends users take defensive measures to minimize the risk of exploitation of this vulnerability, such as:
- Minimize network exposure for all control system devices and/or systems, ensuring they are not accessible from the internet.
- Locate control system networks and remote devices behind firewalls and isolating them from business networks.
- When remote access is required, use more secure methods, such as virtual private networks (VPNs), recognizing VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize VPN is only as secure as the connected devices.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov/ics. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov/ics in the technical information paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
No known public exploitation specifically targeting this vulnerability has been reported to CISA at this time.
5. UPDATE HISTORY
- November 7, 2024: Initial Publication
Hackers increasingly target remote workers by exploiting vulnerabilities arising from the shift to telecommuting. They use tactics like “voice phishing” (vishing) to gain access to corporate networks. They impersonate IT staff and trick employees into providing sensitive information via fake login pages. Zscaler researchers recently discovered that North Korean hackers are actively employing new tactics […]
The post North Korean Hackers Employing New Tactic To Acquire Remote Jobs appeared first on Cyber Security News.
As Americans make their travel plans, scammers lie in wait. We’ve uncovered the top ten “riskiest” destinations for travel scams...
The post The Top 10 Riskiest Online Destinations Revealed appeared first on McAfee Blog.
In what could potentially be the largest data breach in the history of pathology labs in the United States, the Medusa Ransomware group has reportedly affected over 1.8 million patients associated with Summit Pathology Laboratory in Colorado. This incident underscores a significant vulnerability within the healthcare sector and raises serious concerns about data security practices. […]
The post Medusa Ransomware attack impacts 1.8 million patients appeared first on Cybersecurity Insiders.
Microsoft has observed the threat actor tracked as Storm-0501 launching a multi-staged attack where they compromised hybrid cloud environments and performed lateral movement from on-premises to cloud environment, leading to data exfiltration, credential theft, tampering, persistent backdoor access, and ransomware deployment. The said attack targeted multiple sectors in the United States, including government, manufacturing, transportation, […]
The post Storm-0501: Ransomware attacks expanding to hybrid cloud environments appeared first on Microsoft Security Blog.
For the latest discoveries in cyber research for the week of 23rd September, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Medusa ransomware gang has claimed responsibility for an attack on the Providence Public School District (PPSD) in Rhode Island. The school district is still grappling with ongoing internet outages since September 11, […]
The post 23rd September – Threat Intelligence Report appeared first on Check Point Research.

- Cisco Talos discovered a malicious campaign in August 2022 delivering Cobalt Strike beacons that could be used in later, follow-on attacks.
- Lure themes in the phishing documents in this campaign are related to the job details of a government organization in the United States and a trade union in New Zealand.
- The attack involves a multistage and modular infection chain with fileless, malicious scripts.
Cisco Talos recently discovered a malicious campaign with a modularised attack technique to deliver Cobalt Strike beacons on infected endpoints.
The initial vector of this attack is a phishing email with a malicious Microsoft Word document attachment containing an exploit that attempts to exploit the vulnerability CVE-2017-0199, a remote code execution issue in Microsoft Office. If a victim opens the maldoc, it downloads a malicious Word document template hosted on an attacker-controlled Bitbucket repository.
Talos discovered two attack methodologies employed by the attacker in this campaign: One in which the downloaded DOTM template executes an embedded malicious Visual Basic script, which leads to the generation and execution of other obfuscated VB and PowerShell scripts and another that involves the malicious VB downloading and running a Windows executable that executes malicious PowerShell commands to download and implant the payload.
The payload discovered is a leaked version of a Cobalt Strike beacon. The beacon configuration contains commands to perform targeted process injection of arbitrary binaries and has a high reputation domain configured, exhibiting the redirection technique to masquerade the beacon's traffic.
Although the payload discovered in this campaign is a Cobalt Strike beacon, Talos also observed usage of the Redline information-stealer and Amadey botnet executables as payloads.
This campaign is a typical example of a threat actor using the technique of generating and executing malicious scripts in the victim's system memory. Defenders should implement behavioral protection capabilities in the organization's defense to effectively protect them against fileless threats.
Organizations should be constantly vigilant on the Cobalt Strike beacons and implement layered defense capabilities to thwart the attacker's attempts in the earlier stage of the attack's infection chain.
Initial vector
The initial infection email is themed to entice the recipient to review the attached Word document and provide some of their personal information.
The maldocs have lures containing text related to the collection of personally identifiable information (PII) which is used to determine the eligibility of the job applicant for employment with U.S. federal government contractors and their alleged enrollment status in the government's life insurance program.
The text in the maldoc resembles the contents of a declaration form of the U.S. Office of Personnel Management (OPM) which serves as the chief human resources agency and personnel policy manager for the U.S. federal government.
Another maldoc of the same campaign contains a job description advertising for roles related to delegating development, PSA plus — a prominent New Zealand trade union — and administrative support for National Secretaries at the Public Service Association office based out of Wellington, New Zealand. The contents of this maldoc lure resemble the legitimate job description documents for the New Zealand Public Service Association, another workers' union for New Zealand federal employees, headquartered in Wellington.
PSA New Zealand released this legitimate job description document in April 2022. The threat actor constructed the maldoc to contain the text lures to make it appear as a legitimate document on May 6, 2022. Talos' observation shows that the threat actors are also regular consumers of online news.
Attack methodologies
Attack methodologies employed by the actor in this campaign are highly modularised and have multiple stages in the infection chain.
Talos discovered two different attack methodologies of this campaign with a few variations in the TTPs', while the initial infection vector, use of remote template injection technique and the final payload remained the same.
Method 1
This is a modularised method with multiple stages in the infection chain to implant a Cobalt Strike beacon, as outlined below:
Stage 1 maldoc: DOTM template
The malicious Word document contains an embedded URL, https[://]bitbucket[.]org/atlasover/atlassiancore/downloads/EmmaJardi.dotm, within its relationship component "word/_rels/settings.xml.rels". When a victim opens the document, the malicious DOTM file is downloaded.
Stage 2: VBA dropper
The downloaded DOTM executes the malicious Visual Basic for Applications (VBA) macro. The VBA dropper code contains an encoded data blob which is decoded and written into an HTA file, "example.hta," in the user profile local application temporary folder. The decoded content written to an HTA file is the next VB script, which is executed using the ShellExecuted method.
Stage 3 VB script
The third-stage VBS structure is similar to that of the stage 2 VB dropper. An array of the encoded data will be decoded to a PowerShell script, which is generated in the victim's system memory and executed.
Stage 4 PowerShell script
The PowerShell dropper script executed in the victim's system memory contains an AES-encrypted data blob as a base64-encoded string and another base64-encoded string of a decryption key. The encoded strings are converted to generate the AES encrypted data block and the 256-bit AES decryption key. Using the decryption key, the encrypted data generates a PowerShell downloader script, which is executed using the PowerShell IEX function.
Stage 5 PowerShell downloader
The PowerShell downloader script is obfuscated and contains encoded blocks that are decoded to generate the download URL, file execution path and file extensions.
The following actions are performed by the script upon its execution in victim's system memory:
- The script downloads the payload from the actor controlled remote location through the URL "https[://]bitbucket[.]org/atlasover/atlassiancore/downloads/newmodeler.dll" to the user profile local application temporary folder.
- The script performs a check on the file extension of the downloaded payload file.
- If the payload has the extension .dll, the script will run the DLL using rundll32.exe exhibiting the use of sideloading technique.
-
If the payload has an MSI file extension, the payload is executed using the command
"msiexec /quiet /i". -
If the payload is an EXE file, then it will run it as a process using the PowerShell commandlet
Start-Process. - Upon running the payload, the script will hide the payload file to establish persistence by setting the "hidden" file system attribute of the payload file.
During our analysis, we discovered that the downloaded payload is a Cobalt Strike DLL beacon.
Method 2
The second attack method of this campaign is also modular, but is using less sophisticated Visual Basic and PowerShell scripts. We spotted that, in the attack chain, the actor employed a 64-bit Windows executable downloader which executes the PowerShell commands responsible for downloading and running the Cobalt Strike payload.
Stage 1 maldoc: DOTM template
When a victim opens the malicious document, Windows attempts to download a malicious remote DOTM template through the URL "https[://]bitbucket[.]org/clouchfair/oneproject/downloads/ww.dotm," which was embedded in its relationship component of the file settings.xml.rels."
Stage 2 VB script
The DOTM template contains a VBA macro that executes a function to decode an encoded data block of the macro to generate the PowerShell downloader script and execute it with the shell function.
Stage 3 PowerShell downloader
The PowerShell downloader command downloads a 64-bit Windows executable and runs it as a process in the victim's machine.
Stage 4 downloader executable
The downloader is a 64-bit executable that runs as a process in the victim's environment. It executes the PowerShell command, which downloads the Cobalt Strike payload DLL through the URL "https[://]bitbucket[.]org/clouchfair/oneproject/downloads/strymon.png" to the userprofile local application temporary directory with a spoofed extension .png and sideloads the DLL using rundll32.exe.
The downloader also executes the ping command to the IP address 1[.]1[.]1[.]1 and executes the delete command to delete itself. The usage of ping command is to instill a delay before deleting the downloader.
Payload
Talos discovered that the final payload of this campaign is a Cobalt Strike beacon. Cobalt Strike is a modularised attack framework and is customizable. Threat actors can add or remove features according to their malicious intentions. Employing Cobalt Strike beacons in the attacks' infection chain allows the attackers to blend their malicious traffic with legitimate traffic and evade network detections. Also, with its capabilities to configure commands in the beacon configuration, the attacker can perform various malicious operations such as injecting other malicious binary into the running processes of the infected machines and can avoid having a separate injection module implants in their infection chain.
The Cobalt Strike beacon configurations of this campaign showed us various characteristics of the beacon binary:- C2 server.
- Communication protocols.
- Process injection techniques.
- Malleable C2 Instructions.
- Target process to spawn for x86 and x64 processes.
- Watermark : "Xi54kA==".
The Cobalt Strike beacon used in this campaign has the following capabilities:
- Executes arbitrary codes in the target processes through process injection. Target processes described in the beacon configuration related to this campaign include:
"%windir%\syswow64\dns-sd.exe"
"%windir%\syswow64\rundll32.exe"
"%windir%\syswow64\dllhost.exe -o enable"
x64:
"%windir%\sysnative\getmac.exe /V"
"%windir%\sysnative\rundll32.exe"
"%windir%\sysnative\DeviceParingWizard.exe"
- A high-reputation domain defined in the HostHeader component of the beacon configuration. The actor is using this redirector technique to make the beacon traffic appear legitimate and avoid detection.
Malicious repository
The attacker in this campaign has hosted malicious DOTM templates and Cobalt Strike DLLs on Bitbucket using different accounts. We spotted two attacker-controlled accounts "atlasover" and "clouchfair" in this campaign: https[://]bitbucket[.]org/atlasover/atlassiancore/downloads and https[://]bitbucket[.]org/clouchfair/oneproject/downloads.
During our analysis, the account "atlasover" was live and showed us the hosting information of some of the malicious files in this campaign.
Talos also discovered in VirusTotal that the attacker operated the Bitbucket account "clouchfair," using the account to host two other information stealer executables, Redline and Amadey, along with a malicious DOTM template and Cobalt Strike DLL.
Command and control
Talos discovered the C2 server operated in this campaign with the IP address 185[.]225[.]73[.]238 running on Ubuntu Linux version 18.04, located in the Netherlands and is a part of the Alibaba cloud infrastructure.
Shodan search results showed us that the C2 server contained two self-signed SSL certificates with the serial numbers 6532815796879806872 and 1657766544761773100, which are valid from July 14, 2022 - July 14, 2023.
 |
SSL certificate associated with the C2 servers. |
Pivoting on the SSL certificates disclosed another Cobalt Strike C2 server with the IP address 43[.]154[.]175[.]230 running on Ubuntu Linux version 18.04 located in Hong Kong, which is also part of Alibaba cloud infrastructure and more likely is operated by the same actor of this campaign.
Coverage
Ways our customers can detect and block this threat are listed below.Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort Rule 60600 is available for this threat.
The following ClamAV signatures have been released to detect this threat:
Win.Packed.Generic-9956955-0
Win.Malware.CobaltStrike-9968593-1
Win.Dropper.AgentTesla-9969002-0
Win.Dropper.Swisyn-9969191-0
Win.Trojan.Swisyn-9969193-0
Win.Malware.RedlineStealer-9970633-0
IOC
The IOC list is available in Talos' Github repo here.
Cybersecurity researchers have disclosed a new phishing kit that has been put to use in campaigns targeting Australia, Japan, Spain, the U.K., and the U.S. since at least September 2024. Netcraft said more than 2,000 phishing websites have been identified the kit, known as Xiū gǒu, with the offering used in attacks aimed at a […]
The post New Phishing Kit Xiū gǒu Targets Users Across Five Countries With 2,000 Fake Sites appeared first on All Hacker News.
Data from Action Fraud, the national fraud and cybercrime reporting service, shows that 22,530 people reported that their online accounts had been hacked in 2023, with victims losing a total of £1.3 million. Pauline Smith, Head of Action Fraud, said: “Anyone with a social media or email account can be a target for fraudsters or […]
The process of protecting networks, computers, servers, mobile devices, electronic systems, and data from malicious
Since October 22, 2024, Microsoft Threat Intelligence has observed Russian threat actor Midnight Blizzard sending a series of highly targeted spear-phishing emails to individuals in government, academia, defense, non-governmental organizations, and other sectors. This activity is ongoing, and Microsoft will continue to investigate and provide updates as available. Based on our investigation of previous Midnight […]
The post Midnight Blizzard conducts large-scale spear-phishing campaign using RDP files appeared first on Microsoft Security Blog.
Learn how social engineering and insider threats are major reasons for data loss and explore strategies to prevent them with advanced monitoring solutions.
The post Leading Reason for Data Loss: Social Engineering & Insider Threats appeared first on Fidelis Security.
Google’s Ambitious Leap: AI to Replace Web Browsers? In a bold move that could redefine how users access information online, Google, a subsidiary of Alphabet Inc., is introducing an innovative initiative called Project Jarvis. This groundbreaking project aims to embed advanced artificial intelligence technology into smartphones, effectively eliminating the traditional need for web browsers. With […]
The post Trending Cybersecurity News Headlines on Google appeared first on Cybersecurity Insiders.
Cybersecurity researchers have warned of a spike in phishing pages created using a website builder tool called Webflow, as threat actors continue to abuse legitimate services like Cloudflare and Microsoft Sway to their advantage. “The campaigns target sensitive information from different crypto wallets, including Coinbase, MetaMask, Phantom, Trezor, and Bitbuy, as well as login credentials […]
The post Cybercriminals Use Webflow to Deceive Users into Sharing Sensitive Login Credentials appeared first on All Hacker News.
Healthcare organizations are an attractive target for ransomware attacks. Read our latest blog post to learn why and get strategies to protect yourself from cyberthreats.
The post Microsoft Threat Intelligence healthcare ransomware report highlights need for collective industry action appeared first on Microsoft Security Blog.
A new wave of phishing attacks is targeting Google Meet users with fake conference calls to trick them into downloading malware. Read the details here.
The post Deceptive Google Meet Invites Lure Users Into Malware Scams appeared first on eSecurity Planet.
TA866 (also known as Asylum Ambuscade) is a threat actor that has been conducting intrusion operations since at least 2020.
SUMMARY
The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Federal Bureau of Investigation (FBI) assess that People’s Republic of China (PRC) state-sponsored cyber actors are seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a major crisis or conflict with the United States.
CISA, NSA, FBI and the following partners are releasing this advisory to warn critical infrastructure organizations about this assessment, which is based on observations from the U.S. authoring agencies’ incident response activities at critical infrastructure organizations compromised by the PRC state-sponsored cyber group known as Volt Typhoon (also known as Vanguard Panda, BRONZE SILHOUETTE, Dev-0391, UNC3236, Voltzite, and Insidious Taurus):
- U.S. Department of Energy (DOE)
- U.S. Environmental Protection Agency (EPA)
- U.S. Transportation Security Administration (TSA)
- Australian Signals Directorate’s (ASD’s) Australian Cyber Security Centre (ACSC)
- Canadian Centre for Cyber Security (CCCS), a part of the Communications Security Establishment (CSE)
- United Kingdom National Cyber Security Centre (NCSC-UK)
- New Zealand National Cyber Security Centre (NCSC-NZ)
The U.S. authoring agencies have confirmed that Volt Typhoon has compromised the IT environments of multiple critical infrastructure organizations—primarily in Communications, Energy, Transportation Systems, and Water and Wastewater Systems Sectors—in the continental and non-continental United States and its territories, including Guam. Volt Typhoon’s choice of targets and pattern of behavior is not consistent with traditional cyber espionage or intelligence gathering operations, and the U.S. authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to OT assets to disrupt functions. The U.S. authoring agencies are concerned about the potential for these actors to use their network access for disruptive effects in the event of potential geopolitical tensions and/or military conflicts. CCCS assesses that the direct threat to Canada’s critical infrastructure from PRC state-sponsored actors is likely lower than that to U.S. infrastructure, but should U.S. infrastructure be disrupted, Canada would likely be affected as well, due to cross-border integration. ASD’s ACSC and NCSC-NZ assess Australian and New Zealand critical infrastructure, respectively, could be vulnerable to similar activity from PRC state-sponsored actors.
As the authoring agencies have previously highlighted, the use of living off the land (LOTL) techniques is a hallmark of Volt Typhoon actors’ malicious cyber activity when targeting critical infrastructure. The group also relies on valid accounts and leverage strong operational security, which combined, allows for long-term undiscovered persistence. In fact, the U.S. authoring agencies have recently observed indications of Volt Typhoon actors maintaining access and footholds within some victim IT environments for at least five years. Volt Typhoon actors conduct extensive pre-exploitation reconnaissance to learn about the target organization and its environment; tailor their tactics, techniques, and procedures (TTPs) to the victim’s environment; and dedicate ongoing resources to maintaining persistence and understanding the target environment over time, even after initial compromise.
The authoring agencies urge critical infrastructure organizations to apply the mitigations in this advisory and to hunt for similar malicious activity using the guidance herein provided, along with the recommendations found in joint guide Identifying and Mitigating Living Off the Land Techniques. These mitigations are primarily intended for IT and OT administrators in critical infrastructure organizations. Following the mitigations for prevention of or in response to an incident will help disrupt Volt Typhoon’s accesses and reduce the threat to critical infrastructure entities.
If activity is identified, the authoring agencies strongly recommend that critical infrastructure organizations apply the incident response recommendations in this advisory and report the incident to the relevant agency (see Contact Information section).
For additional information, see joint advisory People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection and U.S. Department of Justice (DOJ) press release U.S. Government Disrupts Botnet People’s Republic of China Used to Conceal Hacking of Critical Infrastructure. For more information on PRC state-sponsored malicious cyber activity, see CISA’s China Cyber Threat Overview and Advisories webpage.
Download the PDF version of this report:
Read the accompanying Malware Analysis Report: MAR-10448362-1.v1 Volt Typhoon.
For a downloadable copy of indicators of compromise (IOCs), see:
TECHNICAL DETAILS
Note: This advisory uses the MITRE ATT&CK for Enterprise framework, version 14. See Appendix C: MITRE ATT&CK Tactics and Techniques section for tables of the Volt Typhoon cyber threat actors’ activity mapped to MITRE ATT&CK® tactics and techniques. For assistance with mapping malicious cyber activity to the MITRE ATT&CK framework, see CISA and MITRE ATT&CK’s Best Practices for MITRE ATT&CK Mapping and CISA’s Decider Tool.
Overview of Activity
In May 2023, the authoring agencies—working with industry partners—disclosed information about activity attributed to Volt Typhoon (see joint advisory People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection). Since then, CISA, NSA, and FBI have determined that this activity is part of a broader campaign in which Volt Typhoon actors have successfully infiltrated the networks of critical infrastructure organizations in the continental and non-continental United States and its territories, including Guam.
The U.S. authoring agencies have primarily observed compromises linked to Volt Typhoon in Communications, Energy, Transportation Systems, and Water and Wastewater Systems sector organizations’ IT networks. Some victims are smaller organizations with limited cybersecurity capabilities that provide critical services to larger organizations or key geographic locations.
Volt Typhoon actors tailor their TTPs to the victim environment; however, the U.S. authoring agencies have observed the actors typically following the same pattern of behavior across identified intrusions. Their choice of targets and pattern of behavior is not consistent with traditional cyber espionage or intelligence gathering operations, and the U.S. authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable the disruption of OT functions across multiple critical infrastructure sectors (see Figure 1).
- Volt Typhoon conducts extensive pre-compromise reconnaissance to learn about the target organization’s network architecture and operational protocols. This reconnaissance includes identifying network topologies, security measures, typical user behaviors, and key network and IT staff. The intelligence gathered by Volt Typhoon actors is likely leveraged to enhance their operational security. For example, in some instances, Volt Typhoon actors may have abstained from using compromised credentials outside of normal working hours to avoid triggering security alerts on abnormal account activities.
- Volt Typhoon typically gains initial access to the IT network by exploiting known or zero-day vulnerabilities in public-facing network appliances (e.g., routers, virtual private networks [VPNs], and firewalls) and then connects to the victim’s network via VPN for follow-on activities.
- Volt Typhoon aims to obtain administrator credentials within the network, often by exploiting privilege escalation vulnerabilities in the operating system or network services. In some cases, Volt Typhoon has obtained credentials insecurely stored on a public-facing network appliance.
- Volt Typhoon uses valid administrator credentials to move laterally to the domain controller (DC) and other devices via remote access services such as Remote Desktop Protocol (RDP).
- Volt Typhoon conducts discovery in the victim’s network, leveraging LOTL binaries for stealth. A key tactic includes using PowerShell to perform targeted queries on Windows event logs, focusing on specific users and periods. These queries facilitate the discreet extraction of security event logs into
.datfiles, allowing Volt Typhoon actors to gather critical information while minimizing detection. This strategy, blending in-depth pre-compromise reconnaissance with meticulous post-exploitation intelligence collection, underscores their sophisticated and strategic approach to cyber operations. - Volt Typhoon achieves full domain compromise by extracting the Active Directory database (
NTDS.dit) from the DC. Volt Typhoon frequently employs the Volume Shadow Copy Service (VSS) using command-line utilities such asvssadminto accessNTDS.dit. TheNTDS.ditfile is a centralized repository that contains critical Active Directory data, including user accounts, passwords (in hashed form), and other sensitive data, which can be leveraged for further exploitation. This method entails the creation of a shadow copy—a point-in-time snapshot—of the volume hosting theNTDS.ditfile. By leveraging this snapshot, Volt Typhoon actors effectively bypass the file locking mechanisms inherent in a live Windows environment, which typically prevent direct access to theNTDS.ditfile while the domain controller is operational. - Volt Typhoon likely uses offline password cracking techniques to decipher these hashes. This process involves extracting the hashes from the
NTDS.ditfile and then applying various password cracking methods, such as brute force attacks, dictionary attacks, or more sophisticated techniques like rainbow tables to uncover the plaintext passwords. The successful decryption of these passwords allows Volt Typhoon actors to obtain elevated access and further infiltrate and manipulate the network. - Volt Typhoon uses elevated credentials for strategic network infiltration and additional discovery, often focusing on gaining capabilities to access OT assets. Volt Typhoon actors have been observed testing access to domain-joint OT assets using default OT vendor credentials, and in certain instances, they have possessed the capability to access OT systems whose credentials were compromised via
NTDS.dittheft. This access enables potential disruptions, such as manipulating heating, ventilation, and air conditioning (HVAC) systems in server rooms or disrupting critical energy and water controls, leading to significant infrastructure failures (in some cases, Volt Typhoon actors had the capability to access camera surveillance systems at critical infrastructure facilities). In one confirmed compromise, Volt Typhoon actors moved laterally to a control system and were positioned to move to a second control system.
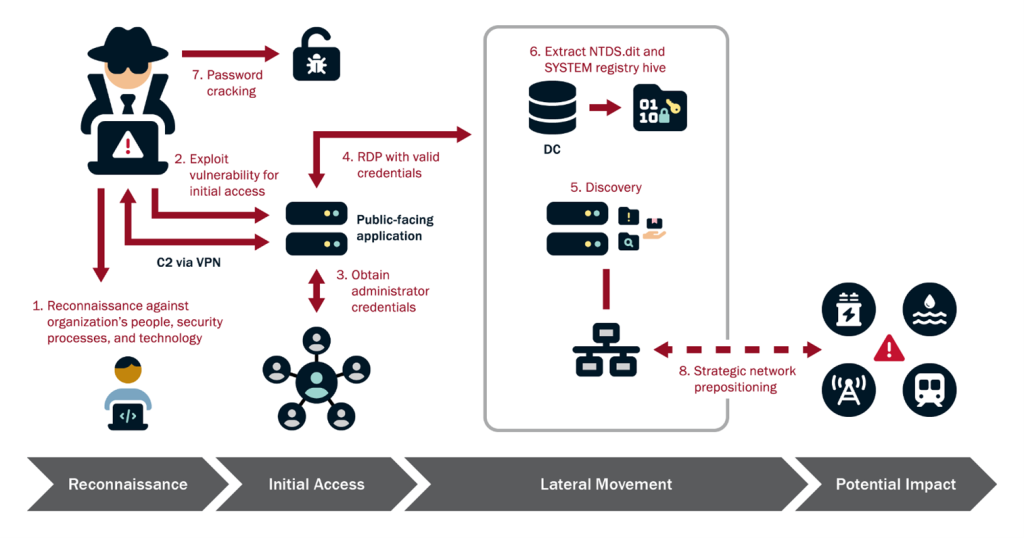
After successfully gaining access to legitimate accounts, Volt Typhoon actors exhibit minimal activity within the compromised environment (except discovery as noted above), suggesting their objective is to maintain persistence rather than immediate exploitation. This assessment is supported by observed patterns where Volt Typhoon methodically re-targets the same organizations over extended periods, often spanning several years, to continuously validate and potentially enhance their unauthorized accesses. Evidence of their meticulous approach is seen in instances where they repeatedly exfiltrate domain credentials, ensuring access to current and valid accounts. For example, in one compromise, Volt Typhoon likely extracted NTDS.dit from three domain controllers in a four-year period. In another compromise, Volt Typhoon actors extracted NTDS.dit two times from a victim in a nine-month period.
Industry reporting—identifying that Volt Typhoon actors are silent on the network following credential dumping and perform discovery to learn about the environment, but do not exfiltrate data—is consistent with the U.S. authoring agencies’ observations. This indicates their aim is to achieve and maintain persistence on the network. In one confirmed compromise, an industry partner observed Volt Typhoon actors dumping credentials at regular intervals.
In addition to leveraging stolen account credentials, the actors use LOTL techniques and avoid leaving malware artifacts on systems that would cause alerts. Their strong focus on stealth and operational security allows them to maintain long-term, undiscovered persistence. Further, Volt Typhoon’s operational security is enhanced by targeted log deletion to conceal their actions within the compromised environment.
See the below sections for Volt Typhoon TTPs observed by the U.S. authoring agencies from multiple confirmed Volt Typhoon compromises.
Observed TTPs
Reconnaissance
Volt Typhoon actors conduct extensive pre-compromise reconnaissance [TA0043] to learn about the target organization [T1591], its network [T1590], and its staff [T1589]. This includes web searches [T1593]—including victim-owned sites [T1594]—for victim host [T1592], identity, and network information, especially for information on key network and IT administrators. According to industry reporting, Volt Typhoon actors use FOFA[1], Shodan, and Censys for querying or searching for exposed infrastructure. In some instances, the U.S. authoring agencies have observed Volt Typhoon actors targeting the personal emails of key network and IT staff [T1589.002] post compromise.
Resource Development
Historically, Volt Typhoon actors use multi-hop proxies for command and control (C2) infrastructure [T1090.003]. The proxy is typically composed of virtual private servers (VPSs) [T1583.003] or small office/home office (SOHO) routers. Recently, Volt Typhoon actors used Cisco and NETGEAR end-of-life SOHO routers implanted with KV Botnet malware to support their operations [T1584.005]. (See DOJ press release U.S. Government Disrupts Botnet People’s Republic of China Used to Conceal Hacking of Critical Infrastructure for more information).
Initial Access
To obtain initial access [TA0001], Volt Typhoon actors commonly exploit vulnerabilities in networking appliances such as those from Fortinet, Ivanti Connect Secure (formerly Pulse Secure), NETGEAR, Citrix, and Cisco [T1190]. They often use publicly available exploit code for known vulnerabilities [T1588.005] but are also adept at discovering and exploiting zero-day vulnerabilities [T1587.004].
- In one confirmed compromise, Volt Typhoon actors likely obtained initial access by exploiting CVE-2022-42475 in a network perimeter FortiGate 300D firewall that was not patched. There is evidence of a buffer overflow attack identified within the Secure Sockets Layer (SSL)-VPN crash logs.
Once initial access is achieved, Volt Typhoon actors typically shift to establishing persistent access [TA0003]. They often use VPN sessions to securely connect to victim environments [T1133], enabling discreet follow-on intrusion activities. This tactic not only provides a stable foothold in the network but also allows them to blend in with regular traffic, significantly reducing their chances of detection.
Execution
Volt Typhoon actors rarely use malware for post-compromise execution. Instead, once Volt Typhoon actors gain access to target environments, they use hands-on-keyboard activity via the command-line [T1059] and other native tools and processes on systems [T1218] (often referred to as “LOLBins”), known as LOTL, to maintain and expand access to the victim networks. According to industry reporting, some “commands appear to be exploratory or experimental, as the operators [i.e., malicious actors] adjust and repeat them multiple times.”[2]
For more details on LOTL activity, see the Credential Access and Discovery sections and Appendix A: Volt Typhoon LOTL Activity.
Similar to LOTL, Volt Typhoon actors also use legitimate but outdated versions of network admin tools. For example, in one confirmed compromise, actors downloaded [T1105] an outdated version of comsvcs.dll on the DC in a non-standard folder. comsvcs.dll is a legitimate Microsoft Dynamic Link Library (DLL) file normally found in the System32 folder. The actors used this DLL with MiniDump and the process ID of the Local Security Authority Subsystem Service (LSASS) to dump the LSASS process memory [T1003.001] and obtain credentials (LSASS process memory space contains hashes for the current user’s operating system (OS) credentials).
The actors also use legitimate non-native network admin and forensic tools. For example, Volt Typhoon actors have been observed using Magnet RAM Capture (MRC) version 1.20 on domain controllers. MRC is a free imaging tool that captures the physical memory of a computer, and Volt Typhoon actors likely used it to analyze in-memory data for sensitive information (such as credentials) and in-transit data not typically accessible on disk. Volt Typhoon actors have also been observed implanting Fast Reverse Proxy (FRP) for command and control.[3] (See the Command and Control section).
Persistence
Volt Typhoon primarily relies on valid credentials for persistence [T1078].
Defense Evasion
Volt Typhoon has strong operational security. Their actors primarily use LOTL for defense evasion [TA0005], which allows them to camouflage their malicious activity with typical system and network behavior, potentially circumventing simplistic endpoint security capabilities. For more information, see joint guide Identifying and Mitigating Living off the Land Techniques.
Volt Typhoon actors also obfuscate their malware. In one confirmed compromise, Volt Typhoon obfuscated FRP client files (BrightmetricAgent.exe and SMSvcService.exe) and the command-line port scanning utility ScanLine by packing the files with Ultimate Packer for Executables (UPX) [T1027.002]. FRP client applications support encryption, compression, and easy token authentication and work across multiple protocols—including transmission control protocol (TCP), user datagram protocol (UDP), hypertext transfer protocol (HTTP), and hypertext transfer protocol secure (HTTPS). The FRP client applications use the Kuai connection protocol (KCP) for error-checked and anonymous data stream delivery over UDP, with packet-level encryption support. See Appendix C and CISA Malware Analysis Report (MAR)-10448362-1.v1 for more information.
In addition to LOTL and obfuscation techniques, Volt Typhoon actors have been observed selectively clearing Windows Event Logs [T1070.001], system logs, and other technical artifacts to remove evidence [T1070.009] of their intrusion activity and masquerading file names [T1036.005].
Credential Access
Volt Typhoon actors first obtain credentials from public-facing appliances after gaining initial access by exploiting privilege escalation vulnerabilities [T1068] in the operating system or network services. In some cases, they have obtained credentials insecurely stored on the appliance [T1552]. In one instance, where Volt Typhoon likely exploited CVE-2022-42475 in an unpatched Fortinet device, Volt Typhoon actors compromised a domain admin account stored inappropriately on the device.
Volt Typhoon also consistently obtains valid credentials by extracting the Active Directory database file (NTDS.dit)—in some cases multiple times from the same victim over long periods [T1003.003]. NTDS.dit contains usernames, hashed passwords, and group memberships for all domain accounts, essentially allowing for full domain compromise if the hashes can be cracked offline.
To obtain NTDS.dit, the U.S. authoring agencies have observed Volt Typhoon:
- Move laterally [TA0008] to the domain controller via an interactive RDP session using a compromised account with domain administrator privileges [T1021.001];
- Execute the Windows-native
vssadmin[T1006] command to create a volume shadow copy; - Use Windows Management Instrumentation Console (WMIC) commands [T1047] to execute
ntdsutil(a LOTL utility) to copyNTDS.ditandSYSTEMregistry hive from the volume shadow copy; and - Exfiltrate [TA0010]
NTDS.ditandSYSTEMregistry hive to crack passwords offline) [T1110.002]. (For more details, including specific commands used, see Appendix A: Volt Typhoon LOTL Activity.)
Note: A volume shadow copy contains a copy of all the files and folders that exist on the specified volume. Each volume shadow copy created on a DC includes itsNTDS.ditand theSYSTEMregistry hive, which provides keys to decrypt theNTDS.ditfile.
Volt Typhoon actors have also been observed interacting with a PuTTY application by enumerating existing stored sessions [T1012]. Given this interaction and the exposure of cleartext-stored proxy passwords used in remote administration, Volt Typhoon actors potentially had access to PuTTY profiles that allow access to critical systems (see the Lateral Movement section).
According to industry reporting, Volt Typhoon actors attempted to dump credentials through LSASS (see Appendix B for commands used).[2]
The U.S. authoring agencies have observed Volt Typhoon actors leveraging Mimikatz to harvest credentials, and industry partners have observed Volt Typhoon leveraging Impacket.[2]
- Mimikatz is a credential dumping tool and Volt Typhoon actors use it to obtain credentials. In one confirmed compromise, the Volt Typhoon used RDP to connect to a server and run Mimikatz after leveraging a compromised administrator account to deploy it.
- Impacket is an open source Python toolkit for programmatically constructing and manipulating network protocols. It contains tools for Kerberos manipulation, Windows credential dumping, packet sniffing, and relay attacks—as well as remote service execution.
Discovery
Volt Typhoon actors have been observed using commercial tools, LOTL utilities, and appliances already present on the system for system information [T1082], network service [T1046], group [T1069] and user [T1033] discovery.
Volt Typhoon uses at least the following LOTL tools and commands for system information, network service, group, and user discovery techniques:
|
|
|
Some observed specific examples of discovery include:
- Capturing successful logon events [T1654].
- Specifically, in one incident, analysis of the PowerShell console history of a domain controller indicated that security event logs were directed to a file named
user.dat, as evidenced by the executed commandGet-EventLog security -instanceid 4624 -after [year-month-date] | fl * | Out-File 'C:\users\public\documents\user.dat'. This indicates the group's specific interest in capturing successful logon events (event ID4624) to analyze user authentication patterns within the network. Additionally, file system analysis, specifically of the Master File Table (MFT), uncovered evidence of a separate file,systeminfo.dat, which was created inC:\Users\Public\Documentsbut subsequently deleted [T1070.004]. The presence of these activities suggests a methodical approach by Volt Typhoon actors in collecting and then possibly removing traces of sensitive log information from the compromised system.
- Specifically, in one incident, analysis of the PowerShell console history of a domain controller indicated that security event logs were directed to a file named
- Executing
tasklist /vto gather a detailed process listing [T1057], followed by executingtaskkill /f /im rdpservice.exe(the function of this executable is not known). - Executing
net userandquserfor user account information [T1087.001]. - Creating and accessing a file named
rult3uil.logon a domain controller inC:\Windows\System32\. Therult3uil.logfile contained user activities on a compromised system, showcasing a combination of window title information [T1010] and focus shifts, keypresses, and command executions across Google Chrome and Windows PowerShell, with corresponding timestamps. - Employing
pingwith various IP addresses to check network connectivity [T1016.001] andnet startto list running services [T1007].
See Appendix A for additional LOTL examples.
In one confirmed compromise, Volt Typhoon actors attempted to use Advanced IP Scanner, which was on the network for admin use, to scan the network.
Volt Typhoon actors have been observed strategically targeting network administrator web browser data—focusing on both browsing history and stored credentials [T1555.003]—to facilitate targeting of personal email addresses (see the Reconnaissance section) for further discovery and possible network modifications that may impact the threat actor’s persistence within victim networks.
In one confirmed compromise:
- Volt Typhoon actors obtained the history file from the
User Datadirectory of a network administrator user’s Chrome browser. To obtain the history file, Volt Typhoon actors first executed an RDP session to the user’s workstation where they initially attempted, and failed, to obtain theC$ File Name: users\{redacted}\appdata\local\Google\Chrome\UserData\default\Historyfile, as evidenced by the accompanying1016(reopen failed) SMB error listed in the application event log. The threat actors then disconnected the RDP session to the workstation and accessed the fileC:\Users\{redacted}\Downloads\History.zip. This file presumably contained data from the User Data directory of the user’s Chrome browser, which the actors likely saved in the Downloads directory for exfiltration [T1074]. Shortly after accessing thehistory.zipfile, the actors terminated RDP sessions. - About four months later, Volt Typhoon actors accessed the same user’s Chrome data
C$ File Name: Users\{redacted}\AppData\Local\Google\Chrome\User Data\Local Stateand$ File Name: Users\{redacted}\AppData\Local\Google\Chrome\User Data\Default\Login Datavia SMB. The Local State file contains the Advanced Encryption Standard (AES) encryption key [T1552.004] used to encrypt the passwords stored in the Chrome browser, which would enable the actors to obtain plaintext passwords stored in the Login Data file in the Chrome browser.
In another confirmed compromise, Volt Typhoon actors accessed directories containing Chrome and Edge user data on multiple systems. Directory interaction was observed over the network to paths such as C:\Users\{redacted}\AppData\Local\Google\Chrome\User Data\ and C:\Users\{redacted}\AppData\Local\Microsoft\Edge\User Data\. They also enumerated several directories, including directories containing vulnerability testing and cyber related content and facilities data, such as construction drawings [T1083].
Lateral Movement
For lateral movement, Volt Typhoon actors have been observed predominantly employing RDP with compromised valid administrator credentials. Note: With a full on-premises Microsoft Active Directory identity compromise (see the Credential Access section), the group may be capable of using other methods such as Pass the Hash or Pass the Ticket for lateral movement [T1550].
In one confirmed compromise of a Water and Wastewater Systems Sector entity, after obtaining initial access, Volt Typhoon actors connected to the network via a VPN with administrator credentials they obtained and opened an RDP session with the same credentials to move laterally. Over a nine-month period, they moved laterally to a file server, a domain controller, an Oracle Management Server (OMS), and a VMware vCenter server. The actors obtained domain credentials from the domain controller and performed discovery, collection, and exfiltration on the file server (see the Discovery and Collection and Exfiltration sections).
Volt Typhoon’s movement to the vCenter server was likely strategic for pre-positioning to OT assets. The vCenter server was adjacent to OT assets, and Volt Typhoon actors were observed interacting with the PuTTY application on the server by enumerating existing stored sessions. With this information, Volt Typhoon potentially had access to a range of critical PuTTY profiles, including those for water treatment plants, water wells, an electrical substation, OT systems, and network security devices. This would enable them to access these critical systems [T1563]. See Figure 2.
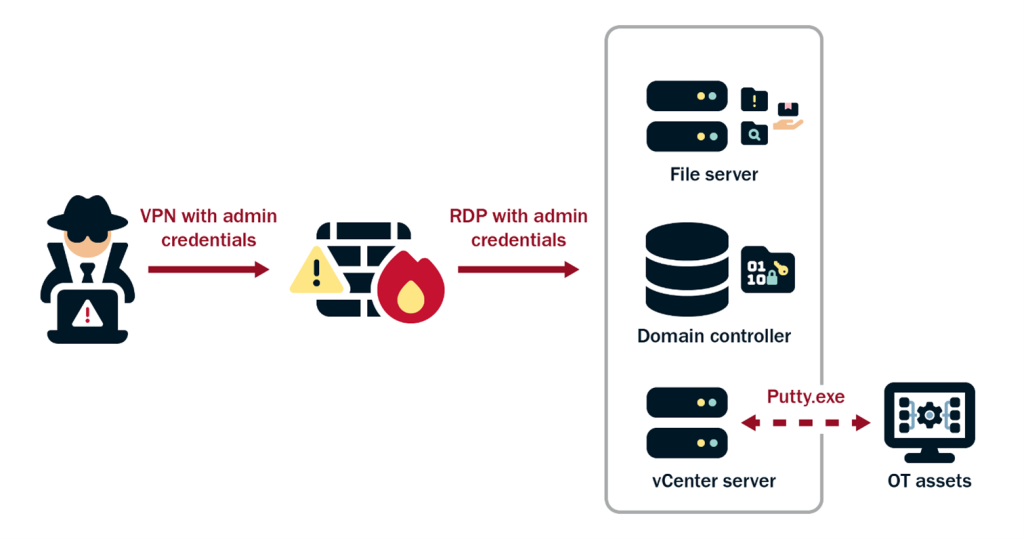
Additionally, Volt Typhoon actors have been observed using PSExec to execute remote processes, including the automated acceptance of the end-user license agreement (EULA) through an administrative account, signified by the accepteula command flag.
Volt Typhoon actors may have attempted to move laterally to a cloud environment in one victim’s network but direct attribution to the Volt Typhoon group was inconclusive. During the period of the their known network presence, there were anomalous login attempts to an Azure tenant [T1021.007] potentially using credentials [T1078.004] previously compromised from theft of NTDS.dit. These attempts, coupled with misconfigured virtual machines with open RDP ports, suggested a potential for cloud-based lateral movement. However, subsequent investigations, including password changes and multifactor authentication (MFA) implementations, revealed authentication failures from non-associated IP addresses, with no definitive link to Volt Typhoon.
Collection and Exfiltration
The U.S. authoring agencies assess Volt Typhoon primarily collects information that would facilitate follow-on actions with physical impacts. For example, in one confirmed compromise, they collected [TA0009] sensitive information obtained from a file server in multiple zipped files [T1560] and likely exfiltrated [TA0010] the files via Server Message Block (SMB) [T1048] (see Figure 3). Collected information included diagrams and documentation related to OT equipment, including supervisory control and data acquisition (SCADA) systems, relays, and switchgear. This data is crucial for understanding and potentially impacting critical infrastructure systems, indicating a focus on gathering intelligence that could be leveraged in actions targeting physical assets and systems.
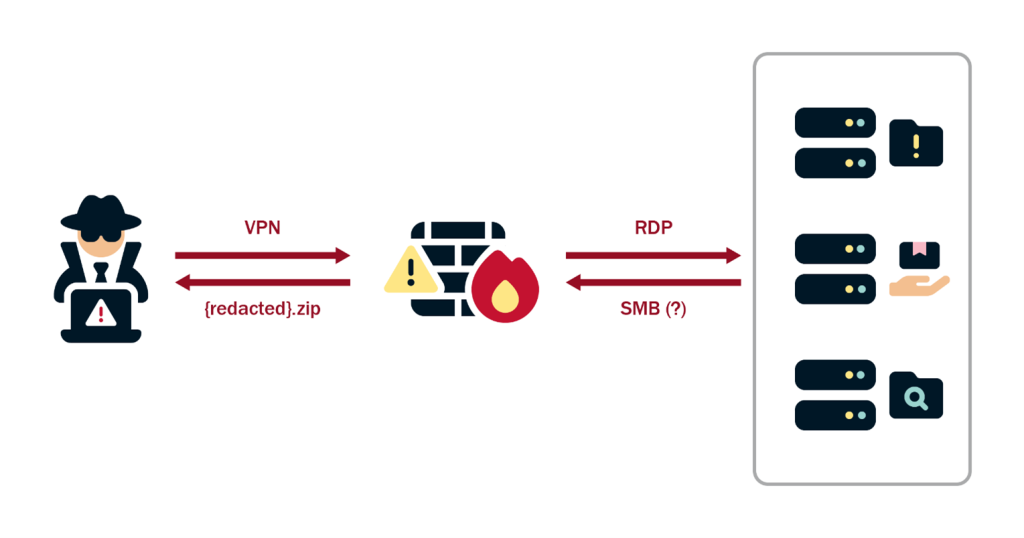
In another compromise, Volt Typhoon actors leveraged WMIC to create and use temporary directories (C:\Users\Public\pro, C:\Windows\Temp\tmp, C:\Windows\Temp\tmp\Active Directory and C:\Windows\Temp\tmp\registry) to stage the extracted ntds.dit and SYSTEM registry hives from ntdsutil execution volume shadow copies (see the Credential Access section) obtained from two DCs. They then compressed and archived the extracted ntds.dit and accompanying registry files by executing ronf.exe, which was likely a renamed version of the archive utility rar.exe) [T1560.001].
Command and Control
Volt Typhoon actors have been observed leveraging compromised SOHO routers and virtual private servers (VPS) to proxy C2 traffic. For more information, see DOJ press release U.S. Government Disrupts Botnet People’s Republic of China Used to Conceal Hacking of Critical Infrastructure).
They have also been observed setting up FRP clients [T1090] on a victim’s corporate infrastructure to establish covert communications channels [T1573] for command and control. In one instance, Volt Typhoon actors implanted the FRP client with filename SMSvcService.exe on a Shortel Enterprise Contact Center (ECC) server and a second FRP client with filename Brightmetricagent.exe on another server. These clients, when executed via PowerShell [T1059.001], open reverse proxies between the compromised system and Volt Typhoon C2 servers. Brightmetricagent.exe has additional capabilities. The FRP client can locate servers behind a network firewall or obscured through Network Address Translation (NAT) [T1016]. It also contains multiplexer libraries that can bi-directionally stream data over NAT networks and contains a command-line interface (CLI) library that can leverage command shells such as PowerShell, Windows Management Instrumentation (WMI), and Z Shell (zsh) [T1059.004]. See Appendix C and MAR-10448362-1.v1 for more information.
In the same compromise, Volt Typhoon actors exploited a Paessler Router Traffic Grapher (PRTG) server as an intermediary for their FRP operations. To facilitate this, they used the netsh command, a legitimate Windows command, to create a PortProxy registry modification [T1112] on the PRTG server [T1090.001]. This key alteration redirected specific port traffic to Volt Typhoon’s proxy infrastructure, effectively converting the PRTG’s server into a proxy for their C2 traffic [T1584.004] (see Appendix B for details).
DETECTION/HUNT RECOMMENDATIONS
Apply Living off the Land Detection Best Practices
Apply the prioritized detection and hardening best practice recommendations provided in joint guide Identifying and Mitigating Living off the Land Techniques. Many organizations lack security and network management best practices (such as established baselines) that support detection of malicious LOTL activity—this makes it difficult for network defenders to discern legitimate behavior from malicious behavior and conduct behavior analytics, anomaly detection, and proactive hunting. Conventional IOCs associated with the malicious activity are generally lacking, complicating network defenders’ efforts to identify, track, and categorize this sort of malicious behavior. This advisory provides guidance for a multifaceted cybersecurity strategy that enables behavior analytics, anomaly detection, and proactive hunting, which are part of a comprehensive approach to mitigating cyber threats that employ LOTL techniques.
Review Application, Security, and System Event Logs
Routinely review application, security, and system event logs, focusing on Windows Extensible Storage Engine Technology (ESENT) Application Logs. Due to Volt Typhoon’s ability for long-term undetected persistence, network defenders should assume significant dwell time and review specific application event log IDs, which remain on endpoints for longer periods compared to security event logs and other ephemeral artifacts. Focus on Windows ESENT logs because certain ESENT Application Log event IDs (216, 325, 326, and 327) may indicate actors copying NTDS.dit.
See Table 1 for examples of ESENT and other key log indicators that should be investigated. Please note that incidents may not always have exact matches listed in the Event Detail column due to variations in event logging and TTPs.
| Event ID (Log) | Event Detail | Description |
|---|---|---|
| 216 (Windows ESENT Application Log) | A database location change was detected from 'C:\Windows\NTDS\ntds.dit' to '\\?\GLOBALROOT\Device\{redacted}VolumeShadowCopy1\Windows\NTDS\ntds.dit' | A change in the NTDS.dit database location is detected. This could suggest an initial step in NTDS credential dumping where the database is being prepared for extraction. |
| 325 (Windows ESENT Application Log) | The database engine created a new database (2, C:\Windows\Temp\tmp\Active Directory\ntds.dit). | Indicates creation of a new NTDS.dit file in a non-standard directory. Often a sign of data staging for exfiltration. Monitor for unusual database operations in temp directories. |
| 637 (Windows ESENT Application Log) | C:\Windows\Temp\tmp\Active Directory\ntds.jfm-++- (0) New flush map file “C:\Windows\Temp\tmp\Active Directory\ntds.jfm” will be created to enable persisted lost flush detection. | A new flush map file is being created for NTDS.dit. This may suggest ongoing operations related to NTDS credential dumping, potentially capturing uncommitted changes to the NTDS.dit file. |
| 326 (Windows ESENT Application Log) |
NTDS-++-12460,D,100-++--++-1-++- C:\$SNAP_{redacted}_VOLUMEC$\Windows\NTDS\ntds.dit-++-0-++- [1] The database engine attached a database. Began mounting of C:\Windows\NTDS\ntds.dit file created from volume shadow copy process |
Represents the mounting of an NTDS.dit file from a volume shadow copy. This is a critical step in NTDS credential dumping, indicating active manipulation of a domain controller’s data. |
| 327 (Windows ESENT Application Log) | C:\Windows\Temp\tmp\Active Directory\ntds.dit-++-1-++- [1] The database engine detached a database (2, C:\Windows\Temp\tmp\Active Directory\ntds.dit). Completion of mounting of ntds.dit file to C:\Windows\Temp\tmp\Active Director | The detachment of a database, particularly in a temp directory, could indicate the completion of a credential dumping process, potentially as part of exfiltration preparations. |
| 21 (Windows Terminal Services Local Session Manager Operational Log) | Remote Desktop Services: Session logon succeeded: User: {redacted}\{redacted} Session ID: {redacted} Source Network Address: {redacted} | Successful authentication to a Remote Desktop Services session. |
| 22 (Windows Terminal Services Local Session Manager Operational Log) | Remote Desktop Services: Shell start notification received: User: {redacted}\{redacted} Session ID: {redacted} Source Network Address: {redacted} | Successful start of a new Remote Desktop session. This may imply lateral movement or unauthorized remote access, especially if the user or session is unexpected. |
| 23 (Windows Terminal Services Local Session Manager Operational Log) | Remote Desktop Services: Session logoff succeeded: User: {redacted}\{redacted} Session ID: {redacted} | Successful logoff of Remote Desktop session. |
| 24 (Windows Terminal Services Local Session Manager Operational Log) | Remote Desktop Services: Session has been disconnected: User: {redacted}\{redacted} Session ID: {redacted} Source Network Address: {redacted} | Remote Desktop session disconnected by user or due to network connectivity issues. |
| 25 (Windows Terminal Services Local Session Manager Operational Log) | Remote Desktop Services: Session reconnection succeeded: User: {redacted}\{redacted} Session ID: {redacted} Source Network Address: {redacted} | Successful reconnection to a Remote Desktop Services session. This may imply lateral movement or unauthorized remote access, especially if the user or session is unexpected. |
| 1017 (Windows System Log) |
Handle scavenged. Share Name: C$ File Name: users\{redacted}\downloads\History.zip Durable: 1 Resilient or Persistent: 0 Guidance: The server closed a handle that was previously reserved for a client after 60 seconds. |
Indicates the server closed a handle for a client. While common in network operations, unusual patterns or locations (like History.zip in a user’s downloads) may suggest data collection from a local system. |
| 1102 (Windows Security Log) | All | All Event ID 1102 entries should be investigated as logs are generally not cleared and this is a known Volt Typhoon tactic to cover their tracks. |
Monitor and Review OT System Logs
- Review access logs for communication paths between IT and OT networks, looking for anomalous accesses or protocols.
- Measure the baseline of normal operations and network traffic for the industrial control system (ICS) and assess traffic anomalies for malicious activity.
- Configure intrusion detection systems (IDS) to create alarms for any ICS network traffic outside normal operations.
- Track and monitor audit trails on critical areas of ICS.
- Set up security incident and event monitoring (SIEM) to monitor, analyze, and correlate event logs from across the ICS network to identify intrusion attempts.
Review CISA’s Recommended Cybersecurity Practices for Industrial Control Systems and the joint advisory, NSA and CISA Recommend Immediate Actions to Reduce Exposure Across all Operational Technologies and Control Systems, for further OT system detection and mitigation guidance.
Use gait to Detect Possible Network Proxy Activities
Use gait[4] to detect network proxy activities. Developed by Sandia National Labs, gait is a publicly available Zeek[5] extension. The gait extension can help enrich Zeek’s network connection monitoring and SSL logs by including additional metadata in the logs. Specifically, gait captures unique TCP options and timing data such as a TCP, transport layer security (TLS), and Secure Shell (SSH) layer inferred round trip times (RTT), aiding in the identification of the software used by both endpoints and intermediaries.
While the gait extension for Zeek is an effective tool for enriching network monitoring logs with detailed metadata, it is not specifically designed to detect Volt Typhoon actor activities. The extension’s capabilities extend to general anomaly detection in network traffic, including—but not limited to—proxying activities. Therefore, while gait can be helpful in identifying tactics similar to those used by Volt Typhoon, such as proxy networks and FRP clients for C2 communication, not all proxying activities detected by using this additional metadata are necessarily indicative of Volt Typhoon presence. It serves as a valuable augmentation to current security stacks for a broader spectrum of threat detection.
For more information, see Sandia National Lab’s gait GitHub page sandialabs/gait: Zeek Extension to Collect Metadata for Profiling of Endpoints and Proxies.
Review Logins for Impossible Travel
Examine VPN or other account logon times, frequency, duration, and locations. Logons from two geographically distant locations within a short timeframe from a single user may indicate an account is being used maliciously. Logons of unusual frequency or duration may indicate a threat actor attempting to access a system repeatedly or maintain prolonged sessions for the purpose of data extraction.
Review Standard Directories for Unusual Files
Review directories, such as C:\windows\temp\ and C:\users\public\, for unexpected or unusual files. Monitor these temporary file storage directories for files typically located in standard system paths, such as the System32 directory. For example, Volt Typhoon has been observed downloading comsvcs.dll to a non-standard folder (this file is normally found in the System32 folder).
INCIDENT RESPONSE
If compromise, or potential compromise, is detected, organizations should assume full domain compromise because of Volt Typhoon’s known behavioral pattern of extracting the NTDS.dit from the DCs. Organizations should immediately implement the following immediate, defensive countermeasures:
- Sever the enterprise network from the internet. Note: this step requires the agency to understand its internal and external connections. When making the decision to sever internet access, knowledge of connections must be combined with care to avoid disrupting critical functions.
- If you cannot sever from the internet, shutdown all non-essential traffic between the affected enterprise network and the internet.
- Reset credentials of privileged and non-privileged accounts within the trust boundary of each compromised account.
- Reset passwords for all domain users and all local accounts, such as
Guest,HelpAssistant,DefaultAccount,System,Administrator, andkrbtgt. Thekrbtgtaccount is responsible for handling Kerberos ticket requests as well as encrypting and signing them. Thekrbtgtaccount should be reset twice because the account has a two-password history. The first account reset for thekrbtgtneeds to be allowed to replicate prior to the second reset to avoid any issues. See CISA’s Eviction Guidance for Networks Affected by the SolarWinds and Active Directory/M365 Compromise for more information. Although tailored to FCEB agencies compromised in the 2020 SolarWinds Orion supply chain compromise, the steps are applicable to organizations with Windows AD compromise.- Review access policies to temporarily revoke privileges/access for affected accounts/devices. If it is necessary to not alert the attacker (e.g., for intelligence purposes), then privileges can be reduced for affected accounts/devices to “contain” them.
- Reset the relevant account credentials or access keys if the investigation finds the threat actor’s access is limited to non-elevated permissions.
- Monitor related accounts, especially administrative accounts, for any further signs of unauthorized access.
- Reset passwords for all domain users and all local accounts, such as
- Audit all network appliance and edge device configurations with indicators of malicious activity for signs of unauthorized or malicious configuration changes. Organizations should ensure they audit the current network device running configuration and any local configurations that could be loaded at boot time. If configuration changes are identified:
- Change all credentials being used to manage network devices, to include keys and strings used to secure network device functions (SNMP strings/user credentials, IPsec/IKE preshared keys, routing secrets, TACACS/RADIUS secrets, RSA keys/certificates, etc.).
- Update all firmware and software to the latest version.
- Report the compromise to an authoring agency (see the Contact Information section).
- For organizations with cloud or hybrid environments, apply best practices for identity and credential access management.
- Verify that all accounts with privileged role assignments are cloud native, not synced from Active Directory.
- Audit conditional access policies to ensure Global Administrators and other highly privileged service principals and accounts are not exempted.
- Audit privileged role assignments to ensure adherence to the principle of least privilege when assigning privileged roles.
- Leverage just-in-time and just-enough access mechanisms when administrators need to elevate to a privileged role.
- In hybrid environments, ensure federated systems (such as AD FS) are configured and monitored properly.
- Audit Enterprise Applications for recently added applications and examine the API permissions assigned to each.
- Reconnect to the internet. Note: The decision to reconnect to the internet depends on senior leadership’s confidence in the actions taken. It is possible—depending on the environment—that new information discovered during pre-eviction and eviction steps could add additional eviction tasks.
- Minimize and control use of remote access tools and protocols by applying best practices from joint Guide to Securing Remote Access Software and joint Cybersecurity Information Sheet: Keeping PowerShell: Security Measures to Use and Embrace.
- Consider sharing technical information with an authoring agency and/or a sector-specific information sharing and analysis center.
For more information on incident response and remediation, see:
- Joint advisory Technical Approaches to Uncovering and Remediating Malicious Activity. This advisory provides incident response best practices.
- CISA’s Federal Government Cybersecurity Incident and Vulnerability Response Playbooks. Although tailored to U.S. Federal Civilian Executive Branch (FCEB) agencies, the playbooks are applicable to all organizations. The incident response playbook provides procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents.
- Joint Water and Wastewater Sector - Incident Response Guide. This joint guide provides incident response best practices and information on federal resources for Water and Wastewater Systems Sector organizations.
MITIGATIONS
These mitigations are intended for IT administrators in critical infrastructure organizations. The authoring agencies recommend that software manufactures incorporate secure by design and default principles and tactics into their software development practices to strengthen the security posture for their customers.
For information on secure by design practices that may protect customers against common Volt Typhoon techniques, see joint guide Identifying and Mitigating Living off the Land Techniques and joint Secure by Design Alert Security Design Improvements for SOHO Device Manufacturers.
For more information on secure by design, see CISA’s Secure by Design webpage and joint guide.
The authoring agencies recommend organizations implement the mitigations below to improve your organization’s cybersecurity posture on the basis of Volt Typhoon activity. These mitigations align with the Cross-Sector Cybersecurity Performance Goals (CPGs) developed by CISA and the National Institute of Standards and Technology (NIST). The CPGs provide a minimum set of practices and protections that CISA and NIST recommend all organizations implement. CISA and NIST based the CPGs on existing cybersecurity frameworks and guidance to protect against the most common and impactful threats, tactics, techniques, and procedures. Visit CISA’s Cross-Sector Cybersecurity Performance Goals for more information on the CPGs, including additional recommended baseline protections.
IT Network Administrators and Defenders
Harden the Attack Surface
- Apply patches for internet-facing systems within a risk-informed span of time [CPG 1E]. Prioritize patching critical assets, known exploited vulnerabilities, and vulnerabilities in appliances known to be frequently exploited by Volt Typhoon (e.g., Fortinet, Ivanti, NETGEAR, Citrix, and Cisco devices).
- Apply vendor-provided or industry standard hardening guidance to strengthen software and system configurations. Note: As part of CISA’s Secure by Design campaign, CISA urges software manufacturers to prioritize secure by default configurations to eliminate the need for customer implementation of hardening guidelines.
- Maintain and regularly update an inventory of all organizational IT assets [CPG 1A].
- Use third party assessments to validate current system and network security compliance via security architecture reviews, penetration tests, bug bounties, attack surface management services, incident simulations, or table-top exercises (both announced and unannounced) [CPG 1F].
- Limit internet exposure of systems when not necessary. An organization’s primary attack surface is the combination of the exposure of all its internet-facing systems. Decrease the attack surface by not exposing systems or management interfaces to the internet when not necessary.
- Plan “end of life” for technology beyond manufacturer supported lifecycle. Inventories of organizational assets should be leveraged in patch and configuration management as noted above. Inventories will also enable identification of technology beyond the manufacturer’s supported lifecycle. Where technology is beyond “end of life” or “end of support,” additional cybersecurity vigilance is necessary, and may warrant one or more of the following:
- Supplemental support agreements;
- Additional scanning and testing;
- Configuration changes;
- Isolation;
- Segmentation; and
- Development of forward-looking plans to facilitate replacement.
Secure Credentials
- Do not store credentials on edge appliances/devices. Ensure edge devices do not contain accounts that could provide domain admin access.
- Do not store plaintext credentials on any system [CPG 2L]. Credentials should be stored securely—such as with a credential/password manager or vault, or other privileged account management solutions—so they can only be accessed by authenticated and authorized users.
- Change default passwords [CPG 2A] and ensure they meet the policy requirements for complexity.
- Implement and enforce an organizational system-enforced policy that:
- Requires passwords for all IT password-protected assets to be at least 15 characters;
- Does not allow users to reuse passwords for accounts, applications, services, etc., [CPG 2C]; and
- Does not allow service accounts/machine accounts to reuse passwords from member user accounts.
- Configure Group Policy settings to prevent web browsers from saving passwords and disable autofill functions.
- Disable the storage of clear text passwords in LSASS memory.
Secure Accounts
- Implement phishing-resistant MFA for access to assets [CPG 2H].
- Separate user and privileged accounts.
- User accounts should never have administrator or super-user privileges [CPG 2E].
- Administrators should never use administrator accounts for actions and activities not associated with the administrator role (e.g., checking email, web browsing).
- Enforce the principle of least privilege.
- Ensure administrator accounts only have the minimum permissions necessary to complete their tasks.
- Review account permissions for default/accounts for edge appliances/devices and remove domain administrator privileges, if identified.
- Significantly limit the number of users with elevated privileges. Implement continuous monitoring for changes in group membership, especially in privileged groups, to detect and respond to unauthorized modifications.
- Remove accounts from high-privilege groups like Enterprise Admins and Schema Admins. Temporarily reinstate these privileges only when necessary and under strict auditing to reduce the risk of privilege abuse.
- Transition to Group Managed Service Accounts (gMSAs) where suitable for enhanced management and security of service account credentials. gMSAs provide automated password management and simplified Service Principal Name (SPN) management, enhancing security over traditional service accounts. See Microsoft’s Group Managed Service Accounts Overview.
- Enforce strict policies via Group Policy and User Rights Assignments to limit high-privilege service accounts.
- Consider using a privileged access management (PAM) solution to manage access to privileged accounts and resources [CPG 2L]. PAM solutions can also log and alert usage to detect any unusual activity.
- Complement the PAM solution with role-based access control (RBAC) for tailored access based on job requirements. This ensures that elevated access is granted only when required and for a limited duration, minimizing the window of opportunity for abuse or exploitation of privileged credentials.
- Implement an Active Directory tiering model to segregate administrative accounts based on their access level and associated risk. This approach reduces the potential impact of a compromised account. See Microsoft’s PAM environment tier model.
- Harden administrative workstations to only permit administrative activities from workstations appropriately hardened based on the administrative tier. See Microsoft’s Why are privileged access devices important - Privileged access.
- Disable all user accounts and access to organizational resources of employees on the day of their departure [CPG 2G]
- Regularly audit all user, admin, and service accounts and remove or disable unused or unneeded accounts as applicable.
- Regularly roll NTLM hashes of accounts that support token-based authentication.
- Improve management of hybrid (cloud and on-premises) identity federation by:
- Using cloud only administrators that are asynchronous with on-premises environments and ensuring on-premises administrators are asynchronous to the cloud.
- Using CISA’s SCuBAGear tool to discover cloud misconfigurations in Microsoft cloud tenants. SCuBA gear is automation script for comparing Federal Civilian Executive Branch (FCEB) agency tenant configurations against CISA M365 baseline recommendations. SCuBAGear is part of CISA’s Secure Cloud Business Applications (SCuBA) project, which provides guidance for FCEB agencies, securing their cloud business application environments and protecting federal information created, accessed, shared, and stored in those environments. Although tailored to FCEB agencies, the project provides security guidance applicable to all organizations with cloud environments. For more information on SCuBAGear see CISA’s Secure Cloud Business Applications (SCuBA) Project.
- Using endpoint detection and response capabilities to actively defend on-premises federation servers.
Secure Remote Access Services
- Limit the use of RDP and other remote desktop services. If RDP is necessary, apply best practices, including auditing the network for systems using RDP, closing unused RDP ports, and logging RDP login attempts.
- Disable Server Message Block (SMB) protocol version 1 and upgrade to version 3 (SMBv3) after mitigating existing dependencies (on existing systems or applications), as they may break when disabled.
- Harden SMBv3 by implementing guidance included in joint #StopRansomware Guide (see page 8 of the guide).
- Apply mitigations from the joint Guide to Securing Remote Access Software.
Secure Sensitive Data
- Securely store sensitive data (including operational technology documentation, network diagrams, etc.), ensuring that only authenticated and authorized users can access the data.
Implement Network Segmentation
- Ensure that sensitive accounts use their administrator credentials only on hardened, secure computers. This practice can reduce lateral movement exposure within networks.
- Conduct comprehensive trust assessments to identify business-critical trusts and apply necessary controls to prevent unauthorized cross-forest/domain traversal.
- Harden federated authentication by enabling Secure Identifier (SID) Filtering and Selective Authentication on AD trust relationships to further restrict unauthorized access across domain boundaries.
- Implement network segmentation to isolate federation servers from other systems and limit allowed traffic to systems and protocols that require access in accordance with Zero Trust principles.
Secure Cloud Assets
- Harden cloud assets in accordance with vendor-provided or industry standard hardening guidance.
- Organizations with Microsoft cloud infrastructure, see CISA’s Microsoft 365 Security Configuration Baseline Guides, which provide minimum viable secure configuration baselines for Microsoft Defender for Office 365, Azure Active Directory (now known as Microsoft Entra ID), Exchange Online, OneDrive for Business, Power BI, Power Platform, SharePoint Online, and Teams. For additional guidance, see the Australian Signals Directorate’s Blueprint for Secure Cloud.
- Organizations with Google cloud infrastructure, see CISA’s Google Workspace Security Configuration Baseline Guides, which provide minimum viable secure configuration baselines for Groups for Business, GMAIL, Google Calendar, Google Chat, Google Common Controls, Google Classroom, Google Drive and Docs, Google Meet, and Google Sites.
- Revoke unnecessary public access to cloud environment. This involves reviewing and restricting public endpoints and ensuring that services like storage accounts, databases, and virtual machines are not publicly accessible unless absolutely necessary. Disable legacy authentication protocols across all cloud services and platforms. Legacy protocols frequently lack support for advanced security mechanisms such as multifactor authentication, rendering them susceptible to compromises. Instead, enforce the use of modern authentication protocols that support stronger security features like MFA, token-based authentication, and adaptive authentication measures.
- Enforce this practice through the use of Conditional Access Policies. These policies can initially be run in report-only mode to identify potential impacts and plan mitigations before fully enforcing them. This approach allows organizations to systematically control access to their cloud resources, significantly reducing the risk of unauthorized access and potential compromise.
- Regularly monitor and audit privileged cloud-based accounts, including service accounts, which are frequently abused to enable broad cloud resource access and persistence.
Be Prepared
- Ensure logging is turned on for application, access, and security logs (e.g., intrusion detection systems/intrusion prevention systems, firewall, data loss prevention, and VPNs) [CPG 2T]. Given Volt Typhoon’s use of LOTL techniques and their significant dwell time, application event logs may be a valuable resource to hunt for Volt Typhoon activity because these logs typically remain on endpoints for relatively long periods of time.
- For OT assets where logs are non-standard or not available, collect network traffic and communications between those assets and other assets.
- Implement file integrity monitoring (FIM) tools to detect unauthorized changes.
- Store logs in a central system, such as a security information and event management (SIEM) tool or central database.
- Ensure the logs can only be accessed or modified by authorized and authenticated users [CPG 2U].
- Store logs for a period informed by risk or pertinent regulatory guidelines.
- Tune log alerting to reduce noise while ensuring there are alerts for high-risk activities. (For information on alert tuning, see joint guide Identifying and Mitigating Living Off the Land Techniques.)
- Establish and continuously maintain a baseline of installed tools and software, account behavior, and network traffic. This way, network defenders can identify potential outliers, which may indicate malicious activity. Note: For information on establishing a baseline, see joint guide Identifying and Mitigating Living off the Land Techniques.
- Document a list of threats and cyber actor TTPs relevant to your organization (e.g., based on industry or sectors), and maintain the ability (such as via rules, alerting, or commercial prevention and detection systems) to detect instances of those key threats [CPG 3A].
- Implement periodic training for all employees and contractors that covers basic security concepts (such as phishing, business email compromise, basic operational security, password security, etc.), as well as fostering an internal culture of security and cyber awareness [CPG 2I].
- Tailor the training to network IT personnel/administrators and other key staff based on relevant organizational cyber threats and TTPs, such as Volt Typhoon. For example, communicate that Volt Typhoon actors are known to target personal email accounts of IT staff, and encourage staff to protect their personal email accounts by using strong passwords and implementing MFA.
- In addition to basic cybersecurity training, ensure personnel who maintain or secure OT as part of their regular duties receive OT-specific cybersecurity training on at least an annual basis [CPG 2J].
- Educate users about the risks associated with storing unprotected passwords.
OT Administrators and Defenders
- Change default passwords [CPG 2A] and ensure they meet the policy requirements for complexity. If the asset’s password cannot be changed, implement compensating controls for the device; for example, segment the device into separate enclaves and implement increased monitoring and logging.
- Require that passwords for all OT password-protected assets be at least 15 characters, when technically feasible. In instances where minimum passwords lengths are not technically feasible (for example, assets in remote locations), apply compensating controls, record the controls, and log all login attempts. [CPG 2B].
- Enforce strict access policies for accessing OT networks. Develop strict operating procedures for OT operators that details secure configuration and usage.
- Segment OT assets from IT environments by [CPG 2F]:
- Denying all connections to the OT network by default unless explicitly allowed (e.g., by IP address and port) for specific system functionality.
- Requiring necessary communications paths between IT and OT networks to pass through an intermediary, such as a properly configured firewall, bastion host, “jump box,” or a demilitarized zone (DMZ), which is closely monitored, captures network logs, and only allows connections from approved assets.
- Closely monitor all connections into OT networks for misuse, anomalous activity, or OT protocols.
- Monitor for unauthorized controller change attempts. Implement integrity checks of controller process logic against a known good baseline. Ensure process controllers are prevented from remaining in remote program mode while in operation if possible.
- Lock or limit set points in control processes to reduce the consequences of unauthorized controller access.
- Be prepared by:
- Determining your critical operational processes’ reliance on key IT infrastructure:
- Maintain and regularly update an inventory of all organizational OT assets.
- Understand and evaluate cyber risk on “as-operated” OT assets.
- Create an accurate “as-operated” OT network map and identify OT and IT network inter-dependencies.
- Identifying a resilience plan that addresses how to operate if you lose access to or control of the IT and/or OT environment.
- Plan for how to continue operations if a control system is malfunctioning, inoperative, or actively acting contrary to the safe and reliable operation of the process.
- Develop workarounds or manual controls to ensure ICS networks can be isolated if the connection to a compromised IT environment creates risk to the safe and reliable operation of OT processes.
- Create and regularly exercise an incident response plan.
- Regularly test manual controls so that critical functions can be kept running if OT networks need to be taken offline.
- Implement regular data backup procedures on OT networks.
- Regularly test backup procedures.
- Determining your critical operational processes’ reliance on key IT infrastructure:
- Follow risk-informed guidance in the joint advisory NSA and CISA Recommend Immediate Actions to Reduce Exposure Across all Operational Technologies and Control Systems, the NSA advisory Stop Malicious Cyber Activity Against Connected Operational Technology.
CONTACT INFORMATION
US organizations: To report suspicious or criminal activity related to information found in this joint Cybersecurity Advisory, contact:
- CISA’s 24/7 Operations Center at [email protected] or 1-844-Say-CISA (1-844-729-2472) or your local FBI field office. When available, please include the following information regarding the incident: date, time, and location of the incident; type of activity; number of people affected; type of equipment used for the activity; the name of the submitting company or organization; and a designated point of contact.
- For NSA client requirements or general cybersecurity inquiries, contact [email protected].
- Water and Wastewater Systems Sector organizations, contact the EPA Water Infrastructure and Cyber Resilience Division at [email protected] to voluntarily provide situational awareness.
- Entities required to report incidents to DOE should follow established reporting requirements, as appropriate. For other energy sector inquiries, contact [email protected].
- For transportation entities regulated by TSA, report to CISA Central in accordance with the requirements found in applicable Security Directives, Security Programs, or TSA Order.
Australian organizations: Visit cyber.gov.au or call 1300 292 371 (1300 CYBER 1) to report cybersecurity incidents and access alerts and advisories.
Canadian organizations: Report incidents by emailing CCCS at [email protected].
New Zealand organizations: Report cyber security incidents to [email protected] or call 04 498 7654.
United Kingdom organizations: Report a significant cyber security incident: ncsc.gov.uk/report-an-incident (monitored 24 hours) or, for urgent assistance, call 03000 200 973.
VALIDATE SECURITY CONTROLS
In addition to applying mitigations, the authoring agencies recommend exercising, testing, and validating your organization's security program against the threat behaviors mapped to the MITRE ATT&CK for Enterprise framework in this advisory. The authoring agencies recommend testing your existing security controls inventory to assess how they perform against the ATT&CK techniques described in this advisory.
To get started:
- Select an ATT&CK technique described in this advisory (see Table 5 through Table 17).
- Align your security technologies against the technique.
- Test your technologies against the technique.
- Analyze your detection and prevention technologies’ performance.
- Repeat the process for all security technologies to obtain a set of comprehensive performance data.
- Tune your security program, including people, processes, and technologies, based on the data generated by this process.
The authoring agencies recommend continually testing your security program, at scale, in a production environment to ensure optimal performance against the MITRE ATT&CK techniques identified in this advisory.
REFERENCES
[1] fofa
[2] Microsoft: Volt Typhoon targets US critical infrastructure with living-off-the-land techniques
[3] GitHub - fatedier/frp: A fast reverse proxy to help you expose a local server behind a NAT or firewall to the internet
[4] GitHub - sandialabs/gait: Zeek Extension to Collect Metadata for Profiling of Endpoints and Proxies
[5] The Zeek Network Security Monitor
RESOURCES
Microsoft: Volt Typhoon targets US critical infrastructure with living-off-the-land techniques
Secureworks: Chinese Cyberespionage Group BRONZE SILHOUETTE Targets U.S. Government and Defense Organizations
DISCLAIMER
The information in this report is being provided “as is” for informational purposes only. The authoring agencies do not endorse any commercial entity, product, company, or service, including any entities, products, or services linked within this document. Any reference to specific commercial entities, products, processes, or services by service mark, trademark, manufacturer, or otherwise, does not constitute or imply endorsement, recommendation, or favoring by the authoring agencies.
ACKNOWLEDGEMENTS
Fortinet and Microsoft contributed to this advisory.
VERSION HISTORY
February 7, 2024: Initial Version.
March 7, 2024: Updated Mitigations section to add recommendation on “end of life” technology.
APPENDIX A: VOLT TYPHOON OBSERVED COMMANDS / LOTL ACTIVITY
See Table 2 and Table 3 for Volt Typhoon commands and PowerShell scripts observed by the U.S. authoring agencies during incident response activities. For additional commands used by Volt Typhoon, see joint advisory People's Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection.
| Command/Script | Description/Use |
|---|---|
| Get-EventLog security -instanceid 4624 -after {redacted date} | fl * | Out-File 'C:\users\public\documents\user.dat' | PowerShell command extracts security log entries with the Event ID 4624 after a specified date. The output is formatted (fl *) and saved to user.dat. Potentially used to analyze logon patterns and identify potential targets for lateral movement. |
| Get-EventLog security -instanceid 4624 | Where-Object {$_.message.contains('{redacted user account}')} | select -First 1 | fl * | PowerShell command extracts security log entries with the Event ID 4624 and filters them to include only those containing a specific user account, selecting the first instance of such an event. |
| wminc process get name,processid | Appears to be an attempt to use the wmic command but with a misspelling (wminc instead of wmic). This command, as it stands, would not execute successfully and would return an error in a typical Windows environment. This could indicate a mistake made during manual input. |
| wmic process get name,processid | WMI command lists all running processes with process names and process IDs. Potentially used to find process IDs needed for other operations, like memory dumping. |
| tasklist /v | Command displays detailed information about currently running processes, including the name, PID, session number, and memory usage. |
| taskkill /f /im rdpservice.exe | Command forcibly terminates the process rdpservice.exe. Potentially used as a cleanup activity post-exploitation. |
| ping -n 1 {redacted IP address} | Command sends one ICMP echo request to a specified IP address. |
| ping -n 1 -w 1 {redacted IP address} | Command sends one ICMP echo request to a specified IP address with a timeout (-w) of 1 millisecond. |
| net user | Lists all user accounts on the local machine or domain, useful for quickly viewing existing user accounts. |
|
quser
query user |
Displays information about user sessions on a system, aiding in identifying active users or sessions. |
| net start | Lists all active services. |
| cmd | Opens a new instance of the command prompt. |
| cd [Redacted Path] | Changes the current directory to a specified path, typically for navigating file systems. |
| Remove-Item .\Thumbs.db | PowerShell command to delete the Thumbs.db file, possibly for cleanup or removing traces. |
| move .\Thumbs.db ttt.dat | Relocates and renames the file Thumbs.db in the current directory to ttt.dat within the same directory. |
| del .\Thumbs.db /f /s /q | Force deletes Thumbs.db files from the current directory and all subdirectories, part of cleanup operations to erase traces. |
| del ?? | Deletes files with two-character names, potentially a targeted cleanup command. |
| del /? | Displays help information for the del command. |
| exit | Terminates the command prompt session. |
| ipconfig | Retrieves network configuration details, helpful for discovery and mapping the victim's network. |
| net time /dom | Queries or sets the network time for a domain, potentially used for reconnaissance or to manipulate system time. |
| netstta -ano | Intended as netstat -ano; a mistyped command indicating a potential operational error. |
| netstat -ano | Lists active network connections and processes, helpful for identifying communication channels and potential targets. |
| type .\Notes.txt | Displays the contents of Notes.txt, possibly used for extracting specific information or intelligence gathering. |
| logoff | Logs off the current user session. |
| Script name and location | Contents | Description/Use |
|---|---|---|
| C:\{redacted}\ logins.ps1 |
# Find DC list from Active Directory $DCs = Get-ADDomainController -Filter *
# Define time for report (default is 1 day) $startDate = (get-date).AddDays(-1)
# Store successful logon events from security logs with the specified dates and workstation/IP in an array foreach ($DC in $DCs){ $slogonevents = Get-Eventlog -LogName Security -ComputerName $DC.Hostname -after $startDate | where {$_.eventID -eq 4624 }}
# Crawl through events; print all logon history with type, date/time, status, account name, computer and IP address if user logged on remotely
foreach ($e in $slogonevents){ # Logon Successful Events # Local (Logon Type 2) if (($e.EventID -eq 4624 ) -and ($e.ReplacementStrings[8] -eq 2)){ write-host "Type: Local Logon`tDate: "$e.TimeGenerated "`tStatus: Success`tUser: "$e.ReplacementStrings[5] "`tWorkstation: "$e.ReplacementStrings[11] } # Remote (Logon Type 10) if (($e.EventID -eq 4624 ) -and ($e.ReplacementStrings[8] -eq 10)){ write-host "Type: Remote Logon`tDate: "$e.TimeGenerated "`tStatus: Success`tUser: "$e.ReplacementStrings[5] "`tWorkstation: "$e.ReplacementStrings[11] "`tIP Address: "$e.ReplacementStrings[18] }} |
The script is designed for user logon discovery in a Windows Active Directory environment. It retrieves a list of DCs and then queries security logs on these DCs for successful logon events (Event ID 4624) within the last day. The script differentiates between local (Logon Type 2) and remote (Logon Type 10) logon events. For each event, it extracts and displays details including the logon type, date/time of logon, status, account name, and the workstation or IP address used for the logon. Volt Typhoon may be leveraging this script to monitor user logon activities across the network, potentially to identify patterns, gather credentials, or track the movement of users and administrators within the network. |
APPENDIX B: INDICATORS OF COMPROMISE
See Table 4 for Volt Typhoon IOCs obtained by the U.S. authoring agencies during incident response activities.
Note: See MAR-10448362-1.v1 for more information on this malware.
| File Name | Description | MD5 | Hashes (SHA256) |
|---|---|---|---|
| BrightmetricAgent.exe |
The file is an FRP that could be used to reveal servers situated behind a network firewall or obscured through Network Address Translation (NAT).
|
fd41134e8ead1c18ccad27c62a260aa6 | edc0c63065e88ec96197c8d7a40662a15a812a9583dc6c82b18ecd7e43b13b70 |
| SMSvcService.exe | The file is a Windows executable "FRPC” designed to open a reverse proxy between the compromised system and the threat actor(s) C2 server. | b1de37bf229890ac181bdef1ad8ee0c2 | 99b80c5ac352081a64129772ed5e1543d94cad708ba2adc46dc4ab7a0bd563f1 |
APPENDIX C: MITRE ATT&CK TACTICS AND TECHNIQUES
See Table 5 through Table 17 for all referenced threat actor tactics and techniques in this advisory.
| Reconnaissance | ||
|---|---|---|
| Technique Title | ID | Use |
| Gather Victim Host Information | T1592 | Volt Typhoon conducts extensive pre-compromise reconnaissance. This includes web searches, including victim-owned sites, for victim host, identity, and network information, especially for information on key network and IT administrators. |
| Gather Victim Identity Information | T1589 | Volt Typhoon conducts extensive pre-compromise reconnaissance to learn about the target organization’s staff. |
| Gather Victim Identity Information: Email Addresses | T1589.002 | Volt Typhoon targets the personal emails of key network and IT staff. |
| Gather Victim Network Information | T1590 | Volt Typhoon conducts extensive pre-compromise reconnaissance to learn about the target organization’s network. |
| Gather Victim Org Information | T1591 | Volt Typhoon conducts extensive pre-compromise reconnaissance to learn about the target organization. |
| Search Open Websites/Domains | T1593 | Volt Typhoon conducts extensive pre-compromise reconnaissance. This includes web searches, including victim-owned sites, for victim host, identity, and network information, especially for information on key network and IT administrators. |
| Search Victim-Owned Websites | T1594 | Volt Typhoon conducts extensive pre-compromise reconnaissance. This includes web searches, including victim-owned sites, for victim host, identity, and network information, especially for information on key network and IT administrators. |
| Resource Development | ||
|---|---|---|
| Technique Title | ID | Use |
| Acquire Infrastructure: Botnet | T1583.003 | Volt Typhoon uses multi-hop proxies for command-and-control infrastructure. The proxy is typically composed of Virtual Private Servers (VPSs) or small office/home office (SOHO) routers. |
| Compromise Infrastructure: Botnet | T1584.005 | Volt Typhoon used Cisco and NETGEAR end-of-life SOHO routers implanted with KV Botnet malware to support their operations. |
| Compromise Infrastructure: Server | T1584.004 | Volt Typhoon has redirected specific port traffic to their proxy infrastructure, effectively converting the PRTG’s Detection Guidance server into a proxy for their C2 traffic. |
| Develop Capabilities: Exploits | T1587.004 | Volt Typhoon uses publicly available exploit code, but is also adept at discovering and exploiting vulnerabilities as zero days. |
| Obtain Capabilities: Exploits | T1588.005 | Volt Typhoon uses publicly available exploit code, but is also adept at discovering and exploiting vulnerabilities as zero days. |
| Initial Access | ||
|---|---|---|
| Technique Title | ID | Use |
| Exploit Public-Facing Application | T1190 | Volt Typhoon commonly exploits vulnerabilities in networking appliances such as Fortinet, Ivanti (formerly Pulse Secure), NETGEAR, Citrix, and Cisco. |
| External Remote Services | T1133 | Volt Typhoon often uses VPN sessions to securely connect to victim environments, enabling discreet follow-on intrusion activities. |
| Execution | ||
|---|---|---|
| Technique Title | ID | Use |
| Command and Scripting Interpreter | T1059 | Volt Typhoon uses hands-on-keyboard execution for their malicious activity via the command-line. |
| Command and Scripting Interpreter: PowerShell | T1059.001 | Volt Typhoon has executed clients via PowerShell. |
| Command and Scripting Interpreter: Unix Shell | T1059.004 | Volt Typhoon has used Brightmetricagent.exe, which contains multiplexer libraries that can bi-directionally stream data over through NAT networks and contains a command-line interface (CLI) library that can leverage command shells such as PowerShell, Windows Management, Instrumentation (WMI), and Z Shell (zsh). |
| Windows Management Instrumentation | T1047 | Volt Typhoon has used Windows Management Instrumentation Console (WMIC) commands. |
| Persistence | ||
|---|---|---|
| Technique Title | ID | Use |
| Valid Accounts | T1078 | Volt Typhoon primarily relies on valid credentials for persistence. |
| Privilege Escalation | ||
|---|---|---|
| Technique Title | ID | Use |
| Exploitation for Privilege Escalation | T1068 | Volt Typhoon first obtains credentials from public-facing appliances after gaining initial access by exploiting privilege escalation vulnerabilities in the operating system or network services. |
| Defense Evasion | ||
|---|---|---|
| Technique Title | ID | Use |
| Direct Volume Access | T1006 | Volt Typhoon has executed the Windows-native vssadmin command to create a volume shadow copy. |
| Indicator Removal: Clear Persistence | T1070.009 | Volt Typhoon has selectively cleared Windows Event Logs, system logs, and other technical artifacts to remove evidence of their intrusion activity and masquerading file names. |
| Indicator Removal: Clear Windows Event Logs | T1070.001 | Volt Typhoon has selectively cleared Windows Event Logs, system logs, and other technical artifacts to remove evidence of their intrusion activity and masquerading file names. |
| Indicator Removal: File Deletion | T1070.004 | Volt Typhoon created systeminfo.dat in C:\Users\Public\Documents, but subsequently deleted it. |
| Masquerading: Match Legitimate Name or Location | T1036.005 | Volt Typhoon has selectively cleared Windows Event Logs, system logs, and other technical artifacts to remove evidence of their intrusion activity and masquerading file names. |
| Modify Registry | T1112 | Volt Typhoon has used the netsh command, a legitimate Windows command, to create a PortProxy registry modification on the PRTG server. |
| Obfuscated Files or Information: Software Packing | T1027.002 | Volt Typhoon has obfuscated FRP client files (BrightmetricAgent.exe and SMSvcService.exe) and the command-line port scanning utility ScanLine by packing the files with Ultimate Packer for Executables (UPX). |
| System Binary Proxy Execution | T1218 | Volt Typhoon uses hands-on-keyboard activity via the command-line and use other native tools and processes on systems (often referred to as “LOLBins”), known as LOTL, to maintain and expand access to the victim networks. |
| Credential Access | ||
|---|---|---|
| Technique Title | ID | Use |
| Brute Force: Password Cracking | T1110.002 | Volt Typhoon has exfiltrated NTDS.dit and SYSTEM registry hive to crack passwords offline. |
| Credentials from Password Stores | T1555 | Volt Typhoon has installed browsers saved passwords history, credit card details, and cookies. |
| Credentials from Password Stores: Credentials from Web Browsers | T1555.003 | Volt Typhoon has strategically targeted network administrator web browser data, focusing on both browsing history and stored credentials. |
| OS Credential Dumping: LSASS Memory | T1003.001 | Volt Typhoon used a DLL with MiniDump and the process ID of Local Security Authority Subsystem Service (LSASS) to dump the LSASS process memory and obtain credentials. |
| OS Credential Dumping: NTDS | T1003.003 | Volt Typhoon appears to prioritize obtaining valid credentials by extracting the Active Directory database file (NTDS.dit). |
| Unsecured Credentials | T1552 | Volt Typhoon has obtained credentials insecurely stored on an appliance. |
| Unsecured Credentials: Private Keys | T1552.004 | Volt Typhoon has accessed a Local State file that contains the Advanced Encryption Standard (AES) encryption key used to encrypt the passwords stored in the Chrome browser, which enables the actors to obtain plaintext passwords stored in the Login Data file in the Chrome browser. |
| Discovery | ||
|---|---|---|
| Technique Title | ID | Use |
| Account Discovery: Local Account | T1087.001 | Volt Typhoon executed net user and quser for user account information. |
| Application Window Discovery | T1010 | Volt Typhoon created and accessed a file named rult3uil.log on a Domain Controller in C:\Windows\System32\. The rult3uil.log file contained user activities on a compromised system, showcasing a combination of window title information and focus shifts, keypresses, and command executions across Google Chrome and Windows PowerShell, with corresponding timestamps. |
| Browser Information Discovery | T1217 | Volt Typhoon has installed browsers saved passwords history, credit card details, and cookies. |
| File and Directory Discovery | T1083 | Volt Typhoon enumerated several directories, including directories containing vulnerability testing and cyber related content and facilities data, such as construction drawings. |
| Log Enumeration | T1654 | Volt Typhoon has captured successful logon events. |
| Network Service Discovery | T1046 | Volt Typhoon has used commercial tools, LOTL utilities, and appliances already present on the system for system information, network service, group, and user discovery. |
| Peripheral Device Discovery | T1120 | Volt Typhoon has obtained the victim's system screen dimension and display devices information. |
| Permission Groups Discovery | T1069 | Volt Typhoon has used commercial tools, LOTL utilities, and appliances already present on the system for system information, network service, group, and user discovery. |
| Process Discovery | T1057 | Volt Typhoon executed tasklist /v to gather a detailed process listing. |
| Query Registry | T1012 | Volt Typhoon has interacted with a PuTTY application by enumerating existing stored sessions. |
| Software Discovery | T1518 | Volt Typhoon has obtained the victim's list of applications installed on the victim's system. |
| System Information Discovery | T1082 | Volt Typhoon has used commercial tools, LOTL utilities, and appliances already present on the system for system information, network service, group, and user discovery. |
| System Location Discovery | T1614 | Volt Typhoon has obtained the victim's system current locale. |
| System Network Configuration Discovery: Internet Connection Discovery | T1016.001 | Volt Typhoon employs ping with various IP addresses to check network connectivity and net start to list running services. |
| System Owner/User Discovery | T1033 | Volt Typhoon has used commercial tools, LOTL utilities, and appliances already present on the system for system information, network service, group, and user discovery. |
| System Service Discovery | T1007 | Volt Typhoon employs ping with various IP addresses to check network connectivity and net start to list running services. |
| System Time Discovery | T1124 | Volt Typhoon has obtained the victim's system timezone. |
| Lateral Movement | ||
|---|---|---|
| Technique Title | ID | Use |
| Remote Service Session Hijacking | T1563 | Volt Typhoon potentially had access to a range of critical PuTTY profiles, including those for water treatment plants, water wells, an electrical substation, operational technology systems, and network security devices. This would enable them to access these critical systems. |
| Remote Services: Cloud Services | T1021.007 | During the period of Volt Typhoon’s known network presence, there were anomalous login attempts to an Azure tenant potentially using credentials previously compromised from theft of NTDS.dit. |
| Remote Services: Remote Desktop Protocol | T1021.001 | Volt Typhoon has moved laterally to the Domain Controller via an interactive RDP session using a compromised account with domain administrator privileges. |
| Use Alternate Authentication Material | T1550 | Volt Typhoon may be capable of using other methods such as Pass the Hash or Pass the Ticket for lateral movement. |
| Valid Accounts: Cloud Accounts | T1078.004 | During the period of Volt Typhoon’s known network presence, there were anomalous login attempts to an Azure tenant potentially using credentials previously compromised from theft of NTDS.dit. |
| Collection | ||
|---|---|---|
| Technique Title | ID | Use |
| Archive Collected Data | T1560 | Volt Typhoon collected sensitive information obtained from a file server in multiple zipped files. |
| Archive Collected Data: Archive via Utility | T1560.001 | Volt Typhoon has compressed and archived the extracted ntds.dit and accompanying registry files (by executing ronf.exe, which was likely a renamed version of rar.exe). |
| Data Staged | T1074 | Volt Typhoon accessed the file C:\Users\{redacted}\Downloads\History.zip, which presumably contained data from the User Data directory of the user’s Chrome browser, which the actors likely saved in the Downloads directory for exfiltration. |
| Screen Capture | T1113 | Volt Typhoon has obtained a screenshot of the victim's system using two libraries (gdi32.dll and gdiplus.dll) |
| Command and Control | ||
|---|---|---|
| Technique Title | ID | Use |
| Encrypted Channel | T1573 | Volt Typhoon has setup FRP clients on a victim’s corporate infrastructure to establish covert communications channels for command and control. |
| Ingress Tool Transfer | T1105 | Volt Typhoon uses legitimate, but outdated versions of network admin tools. For example, in one confirmed compromise, actors downloaded an outdated version of comsvcs.dll, on the DC in a non-standard folder. |
| Proxy | T1090 | Volt Typhoon has setup FRP clients on a victim’s corporate infrastructure to establish covert communications channels for command and control. |
| Proxy: Internal Proxy | T1090.001 | Volt Typhoon has used the netsh command, a legitimate Windows command, to create a PortProxy registry modification on the PRTG server. |
| Proxy: Multi-hop Proxy | T1090.003 | Volt Typhoon uses multi-hop proxies for command-and-control infrastructure. |
| Exfiltration | ||
|---|---|---|
| Technique Title | ID | Use |
| Exfiltration Over Alternative Protocol | T1048 | Volt Typhoon exfiltrated files via Server Message Block (SMB). |
- Elephant framework (GrimPlant (Backdoor) and GraphSteel (Stealer).)
- Graphiron Backdoor
- OutSteel (LorecDocStealer)
- BabaDeda
- Cobalt Strike (Beacon)
- SaintBot Downloader
- WhisperGate Wiper
- Graphiron
- Graphiron is a two-stage threat consisting of a downloader (Downloader.Graphiron) and a payload (Infostealer.Graphiron)
- The downloader contains hardcoded command-and-control (C&C) server addresses
- The downloader is configured to check against a blacklist of malware analysis tools and connect to a C&C server to download the payload, which is then added to autorun
- The payload is capable of stealing information from Firefox and Thunderbird, private keys from MobaXTerm, SSH known hosts, stored passwords, taking screenshots, and exfiltrating data
- The password theft is carried out using a PowerShell command
- The payload communicates with the C&C server using port 443 and communications are encrypted using AES cipher
- Graphiron has similarities with older Nodaria (UNC2589_EmberBear_BleedingBear_Nodaria) tools such as GraphSteel and GrimPlant but can exfiltrate more data such as screenshots and SSH keys
- Nodaria is a threat group active since at least March 2021, mainly targeting organizations in Ukraine and has also been linked to attacks in Kyrgyzstan and Georgia
- The group uses spear-phishing emails to deliver a range of payloads to targets and their previous tools include Elephant Dropper, Elephant Downloader, SaintBot, OutSteel, GrimPlant, and GraphSteel
- Nodaria's earlier tools were written in Go and Graphiron appears to be the latest piece of malware authored by the same developers, using Go version 1.18.
- Elephant (GrimPlant (Backdoor) and GraphSteel (Stealer))
- The Elephant Framework consists of two core components: GrimPlant (Backdoor) and GraphSteel (Stealer).
- GrimPlant allows remote execution of PowerShell commands and communicates with the C&C server using gRPC and encrypted with TLS.
- GraphSteel exfiltrates data from infected machines by communicating with the C&C server using WebSockets and the GraphQL query language.
- GraphSteel exfiltrates information about the infected system, files from various folders and drives, and credentials from various sources including wifi passwords, browser credentials, password vault, and SSH sessions.
- GraphSteel Backdoor
- GrimPlant is a simple backdoor allowing for remote execution of PowerShell commands. Communication with the C2 server uses port 80 and is based on gRPC. The communications are encrypted with TLS, and its certificate is hardcoded in the binary. GraphSteel backdoor is designed to exfiltrate data from infected machines. Communication with the C&C server uses port 443 and is encrypted using the AES cipher. GraphQL query language is used for communication.
- Attacks reported: GraphSteel & GrimPlant used in email phishing attacks on Ukrainian government organizations on April 26, 2022, March 28, 2022 and March 11, 2022 (Source: CERT-UA). GraphSteel and GrimPlant are both written in the Go language.
- GrimPlant is a simple backdoor allowing for remote execution of PowerShell commands. Communication with the C2 server uses port 80 and is encrypted with TLS.
- GraphSteel is designed to exfiltrate data from infected machines. Communication with the C&C server uses port 443 and is encrypted using AES cipher. GraphQL is used for communication.
- APT responsible: UNC2589 (Ember Bear, Lorec53, UAC-0056)
- Attacks reported: GraphSteel & GrimPlant were used in email phishing attacks on Ukrainian government organizations on April 26, March 28, and March 11, 2022 (Source: CERT-UA)
- GrimPlant Backdoor
- GrimPlant is a simple backdoor allowing for remote execution of PowerShell commands. Communication with the C2 server uses port 80 and is based on gRPC. The communications are encrypted with TLS, and its certificate is hardcoded in the binary. GraphSteel backdoor is designed to exfiltrate data from infected machines. Communication with the C&C server uses port 443 and is encrypted using the AES cipher. GraphQL query language is used for communication.
- Attacks reported: GraphSteel & GrimPlant used in email phishing attacks on Ukrainian government organizations on April 26, 2022, March 28, 2022 and March 11, 2022 (Source: CERT-UA) GraphSteel and GrimPlant are both written in the Go language.
- GrimPlant is a simple backdoor allowing for remote execution of PowerShell commands. Communication with the C2 server uses port 80 and is encrypted with TLS.
- OutSteel (LorecDocStealer)
- OutSteel malware is used in spear-phishing campaigns with malicious attachments.
- The main payload is an infostealer that steals files from the victim's machine and uploads them to a Command and Control (C2) server.
- The downloader used to load the infostealer is BabaDeda crypter.
- The malware is believed to be state-sponsored, carried out by a hacker group called Lorec53.
- The group is suspected of conducting espionage attacks against government employees in Georgia and Ukraine.
- The BabaDeda crypter acts as an installer and executes shellcode stored encrypted in a file, such as xml or pdf.
- The BabaDeda crypter is an evasive malware that has the purpose to load a malicious payload stored in another file.
- The BabaDeda crypter is used to load a second BabaDeda crypter in the second phase of the attack.
- The final payload is Outsteel, which sends the stolen files to a specified URL. SaintBot Downloader
- BabaDeda
- BabaDeda Crypter is dropped by a downloader, which can be delivered via a file with the extension ".cpl"
- The ".cpl" file is designed to automatically execute when double-clicked, making it easier for uneducated users to trigger the malware
- BabaDeda Crypter is installed by an MSI file that is downloaded by LorecCPL downloader
- The final payload is delivered as a main malicious binary named "mathparser.exe"
- Capabilities of BabaDeda Crypter:
- BabaDeda Crypter has the ability to install itself onto the victim's system
- The malware can execute a main malicious binary, which could perform various malicious activities such as data theft, information exfiltration, or other malicious actions.
- SaintBot Downloader
- SaintBot malware was observed in a targeted email sent to an individual at an energy organization in Ukraine on Feb 1, 2022.
- The email was a spear phishing attempt that used social engineering tactics to convince the targeted individual to open the attached malicious Word document.
- The document instructed the user to double-click icons with exclamation points which, in turn, ran malicious JavaScript.
- The JavaScript file ran a PowerShell one-liner that downloaded an executable from a URL and saved it to a specific location.
- The URL was hosting a malicious executable that was a loader, acting as the first stage of several in the overall infection chain.
- The infection chain resulted in the installation and execution of OutSteel (a document stealer), SaintBot (a loader Trojan), a batch script turned into an executable that disables Windows Defender, and a legitimate Google Chrome installation executable.
- The initial loader was signed using a certificate related to the Electrum Bitcoin wallet.
- The first-stage loader was a simple wrapper for later stages that decrypt DLLs and load them into memory.
- The DLL is obfuscated but contains anti-analysis functionality that refuses to execute inside a virtual machine.
- The DLL is another stager that will decrypt and execute four embedded binaries.
- The four embedded binaries are OutSteel, SaintBot, an executable that runs a batch script to disable Windows Defender, and the Google Chrome installer
- Cobalt Strike (Beacon)
- Cobalt Strike is a commercial penetration testing tool that is used by threat actors as a backdoor agent named 'Beacon' on target machines. It is a versatile tool that is used by a wide range of threat actors, including APT groups and ransomware operators, for downloading and executing malicious payloads.
- The Beacon implant is a file-less, stage-less or multi-stage shellcode that is loaded either by exploiting a vulnerability or executing a shellcode loader. The Beacon can communicate with the C&C server using several protocols including HTTP, HTTPS, DNS, SMB, named pipes as well as forward and reverse TCP. The Beacon can also chain connections to establish a foothold inside the compromised network and pivot internally into other systems.
- Cobalt Strike has been used in multiple email phishing attacks on Ukrainian government organizations and is attributed to the UNC2589 APT group. The Beacon has also been used in combination with exploits like CVE-2021-40444 and CVE-2022-30190 (Follina)
- BEACON: backdoor written in C/C++, part of the Cobalt Strike framework
- Supports shell command execution, file transfer, file execution, file management
- Can capture keystrokes and screenshots, act as a proxy server
- Can harvest system credentials, port scan, and enumerate systems on a network
- Communicates with C&C server via HTTP or DNS
- WhisperGate Wiper
- Uses the following Windows Command Shell command to execute the destructive malware:
- cmd.exe /Q /c start c:\stage1.exe 1> \127.0.0.1\ADMIN$__[TIMESTAMP] 2>&1
- Uses PowerShell commands to connect its Command and Control (C2) server and download additional payloads
- Delivers PowerShell commands in Base64 encoded form
- PowerShell command: Start-Sleep -s 10
- Tactic: Defense Evasion & Persistence
- Modifies the Master Boot Record (MBR) to evade defense
- Delivers PowerShell commands in Base64 encoded form
- Searches for specific file extensions in certain directories to alter their content
- Downloads file corruptor payload from a Discord channel hosted by the APT group
- Download link for the malicious executable is hardcoded in the stage2.exe
- Overwrites the Master Boot Record (MBR) causing the infected system to not boot up after power down
- Overwrites files and corrupts their integrity
- Renames the files to further its impact
- Misrepresents itself as ransomware
- Two-stage wiper malware
- Initial access stage is unknown, but suspected to be a supply chain attack
- Overwrites Master Boot Records (MBR) with a fake ransom note
- Corrupts files with certain extensions and in certain directories by overwriting them with 0xCC bytes
- Renames the files with a random four-byte extension
Summary:
Nodaria (UAC-0056) is targeting Ukraine with new information-stealing malware. Infostealer.Graphiron malware steals system information, credentials, screenshots, and files from compromised computers.Graphiron is a two-stage threat consisting of a downloader (Downloader.Graphiron) and a payload (Infostealer.Graphiron).The downloader hardcodes C&C server addresses. It checks a malware analysis tool blacklist when performed.If no blacklisted processes are found, it will download, decrypt, and autorun the payload from a C&C server. Graphiron uses AES with hardcoded keys. It generates.lock and.trash files. MicrosoftOfficeDashboard.exe and OfficeTemplate.exe are hardcoded file names.GraphSteel and GrimPlant are comparable to Graphiron. Using PowerShell, GraphSteel exfiltrates files, system information, and password vault credentials. Graphiron can also exfiltrate screenshots and SSH keys.
Summary:
HermeticWiper:APT responsible: Sandworm (Black Energy, UAC-0082)Attacks reported: Massive cyberattacks against Ukrainian organizations on February 23, 2022Disables the Volume Shadow Copy Service (VSS)Abuses legitimate drivers to corrupt data and render recovery impossibleTargets Windows registry files ntuser.dat and Windows event logsTriggers system restart rendering the targeted host inoperableSHA256: 0385eeab00e946a302b24a91dea4187c1210597b8e17cd9e2230450f5ece21daHermeticRansom:APT responsible: Sandworm (Black Energy, UAC-0082)Attacks reported: Cyberattacks against Ukrainian organizations on February 23, 2022Written in Go languageEnumerates available drives and renames selected filesEncrypts file contents using AES algorithmCreates a read_me.html file with a ransom noteSHA256: 4dc13bb83a16d4ff9865a51b3e4d24112327c526c1392e14d56f20d6f4eaf382IsaacWiper:APT responsible: Gamaredon (Primitive Bear, Armageddon)Attacks reported: Cyberattacks against Ukrainian government organizations on February 24, 2022Overwrites existing content with random bytesRenames files it can't access and attempts to wipe newly renamed filesCreates a log file with corrupting activity progressSHA256: 13037b749aa4b1eda538fda26d6ac41c8f7b1d02d83f47b0d187dd645154e033AcidRain:APT responsible: UnknownAttacks reported: Cyberattacks against Viasat’s KA-SAT network and Enercon wind turbines on February 24, 2022Overwrites files and symbolic links with random data from the memory bufferAvoids certain directories if executed with root permissionsTriggers a device reboot after wipingSHA256: 9b4dfaca873961174ba935fddaf696145afe7bbf5734509f95feb54f3584fd9aLoadEdge (InvisiMole):APT responsible: InvisiMole (UAC-0035)Attacks reported: Email phishing attacks on Ukrainian government organizations on March 18, 2022Supports functionalities such as file execution, upload, download, deletion, and obtaining system informationCommunication with C&C uses HTTP and JSON formatted dataPersistence provided by HTA file creating an entry under the Run registry keyResembles an upgraded version of InvisiMole's TCP downloader componentSHA256: fd72080eca622fa3d9573b43c86a770f7467f3354225118ab2634383bd7b42ebGraphSteel & GrimPlant:APT responsible: UNC2589 Ember Bear, Lorec53, UAC-0056Attacks reported: Email phishing attacks on Ukrainian government organizations on March 11, March 28, and April 26, 2022Both written in Go languageGrimPlant is a simple backdoor allowing for remote execution of PowerShell commandsGraphSteel exfiltrates data and steals credentials using
Summary:
UNC1151 is a group that is believed to be sponsored by Belarus and has frequently used the access and information gained by their intrusions to support information operations tracked as “Ghostwriter.”
UNC2589 is believed to act in support of Russian government interest and has been conducting extensive espionage collection in Ukraine.
UNC2589 uses spear phishing campaigns with various themes, including COVID-19 and the war in Ukraine, and has used a variety of different infrastructure.
Mandiant has attributed the January 14 destructive attack on Ukraine using PAYWIPE (WHISPERGATE) to UNC2589.
GRIMPLANT is a backdoor used by UNC2589 and GRAPHSTEEL is an infostealer.
Mandiant analyzed a malicious document with an evacuation plan-themed lure, which was likely used by UNC2589 to target Ukrainian entities in a phishing campaign in late February 2022.
The malware was delivered via phishing email and the Remote Utilities utility was installed upon execution.
Remote Utilities allows attackers to set persistence through creating a startup service.
Mandiant Intelligence discovered another likely UNC2589-related phishing campaign targeting Ukrainian entities with GRIMPLANT and GRAPHSTEEL malware on March 27, 2022.The malware was delivered via phishing email and was dropped onto the victim machine through a macro in an XLS document.
Summary:
The malware appears to be designed to render targeted devices inoperable rather than to obtain a ransom, unlike typical ransomware attacks.The malware has been identified on dozens of systems in Ukraine, including multiple government, non-profit, and information technology organizations.MSTIC assesses that this activity represents an elevated risk to any organization located or with systems in Ukraine.The malware operates in two stages: Stage 1 overwrites the Master Boot Record (MBR) with a ransom note, and Stage 2 is a file corrupter that overwrites files with a fixed number of 0xCC bytes.Microsoft has implemented detections for this malware family as WhisperGate and is continuing its investigation.MSTIC recommends organizations to investigate the provided indicators of compromise (IOCs), enable multifactor authentication, and enable Controlled Folder Access in Microsoft Defender for Endpoint to prevent MBR/VBR modification.The detections in place across Microsoft security products include DoS:Win32/WhisperGate.A!dha, DoS:Win32/WhisperGate.C!.dha, DoS:Win32/WhisperGate.H!dha, and DoS:Win32/WhisperGate.X!dha.
Summary:
HermeticWiper: Malware that makes a system inoperable by corrupting its data. It disables the Volume Shadow Copy Service, wipes the MBR, MFT, and NTUSER files, and overwrites various folders with random bytes generated by CryptGenRandom.HermeticWizard: Worm that spreads HermeticWiper across a local network via WMI and SMB. It is a DLL file that exports functions DllInstall, DllRegisterServer, and DllUnregisterServer. It gathers IP addresses on a network, and when it finds a reachable machine, drops HermeticWiper and executes it.HermeticRansom: Ransomware written in Go that encrypts files and displays a ransom message to the victim.Threat actors TTPs:Initial access: Unknown for both HermeticWiper and IsaacWiper, although it is suspected that the attackers may have used tools such as Impacket to move laterally. HermeticWiper was deployed in at least one instance through the default domain policy (GPO), suggesting the attackers had prior access to the victim's Active Directory server.Lateral movement: HermeticWizard worm was used to spread HermeticWiper across the compromised networks via SMB and WMI.Persistence: HermeticWiper and HermeticWizard are signed by a code-signing certificate assigned to Hermetica Digital Ltd issued on April 13th, 2021, which was not stolen, but instead likely obtained by attackers impersonating the Cypriot company to get this certificate from DigiCert.Malware delivery: HermeticWiper and HermeticWizard were deployed through various methods, including GPO and the use of Impacket tools. HermeticRansom was deployed through GPO in at least one instance.Attribution: ESET researchers have not yet found any tangible connection with a known threat actor. The malware families do not share any significant code similarity with other samples in the ESET malware collection.
Summary:
The threat group UAC-0056 is targeting government organizations and companies involved with critical infrastructure in Ukraine and other countries. Their primary goal is to steal sensitive information for situational awareness and leverage in dealing with Ukraine.The initial loader Trojan is used as a simple wrapper for the next few stages.The packer used to pack and obfuscate the initial loader allows cloning .NET assemblies from other binaries and certificates.The decrypted DLL, named SHCore2.dll, is obfuscated.The stager contains anti-analysis functionality, including checks to refuse to execute inside a virtual machine or on bare metal systems.The stager will decrypt and execute a total of four embedded binaries.OutSteel is a file uploader and document stealer developed with the scripting language AutoIT. It searches for files with specific extensions and uploads them to a hardcoded command and control server.The Windows_defender_disable.bat is used to disable Windows Defender functionality.The SaintBot .NET Loader is composed of several stages with varying levels of obfuscation.The SaintBot Payload is capable of downloading further payloads and updating itself on disk.The threat actors use different social engineering themes in their attacks, such as cryptocurrency, COVID, law enforcement, and fake resumes.Email is used as the attack vector, and different infection chains are used to compromise systems.The threat group has overlaps with previous attack campaigns focused on other organizations in Ukraine and Georgia, as well as other nations’ assets local to Ukraine.The attackers used Discord’s content delivery network (CDN) to host the payload.The threat group makes use of several hardcoded command and control (C2) servers, all reaching out to the same endpoint.
Summary:
A new APT group named Lorec53 was identified by NSFOCUS Security Labs and confirmed by the Ukrainian Computer Emergency Response Center (UAC-0056).
Lorec53 is active in Eastern Europe and has been involved in large-scale cyber espionage attacks against Ukraine and Georgia.
The group has strong infiltration ability and flexible attack methods, using phishing attacks and social engineering techniques.
Lorec53 targets key state sectors such as the Ministry of Defense, Ministry of Finance, embassies, state-owned enterprises, and public medical facilities to collect personnel information.
The group has Russian-linked characteristics in attack tools, domain names, and asset location.
Victims of the Lorec53 group include the National Bank of Iran, Georgia’s Ministry of Epidemic Prevention and Health, Ukraine’s Ministry of Defense, Presidential Office, Ministry of the Interior, and Border Service.
A recent long wave of attacks from Lorec53 targeted a wide range of victims using baits such as Ukrainian government documents, shortcut files, and cpl files.
The group used 3 domain names (3237.site, stun.site, and eumr.site) as download servers for phishing files.
Lorec53 employed known Trojan programs including LorecDocStealer (OutSteel), LorecCPL, and SaintBot.
The first phishing attack in this wave used phishing documents referring to a presidential decree and the second attack used PDF and DOCX files with malicious macros.
The third attack used a phishing document in .zip format targeted at the Ukrainian medical system.
The main purpose of these attacks is still information gathering and the TTPs of the Lorec53 group are evident at each stage.
Summary:
Threat Campaign: Spear-phishing emails with malicious attachments used to steal files from victims' machine.Malware: Infostealer "OutSteel" that uploads stolen files to a Command and Control server. Downloader used to load OutSteel is the BabaDeda crypter.Threat Actor: State-sponsored group "Lorec53" (as named by NSFocus), suspected of being employed by high-level espionage organizations to target government employees in Georgia and Ukraine.TTPs:BabaDeda Crypter is an evasive malware that acts as an installer and executes a shellcode stored encrypted in a file (xml or pdf).The first stage of the attack is downloading the BabaDeda crypter from a malicious LNK file or WORD template document.The BabaDeda crypter first loads and runs a malicious DLL, which then loads and executes another malicious DLL in another thread.The first DLL reads and parses the shellcode and writes it in the main binary's text section.The decrypted shellcode extracts the loader shellcode and the payload, then decrypts them and transfers execution to the decrypted loader shellcode.The final payload is OutSteel, which exfiltrates stolen documents to a specified URL.The second malicious library is a mere downloader that downloads the next stage of the attack.BabaDeda CrypterLorecCPL downloadersOutsteel InfostealerTTPs (Tactics, Techniques, and Procedures):Persistence achieved by creating a link file in the start-up directory using the IShellLinkW interfacePayload execution after decryptionSelf-deletion routineFile size checking before executionDownloading and running the next stage in a new processCode overlap with WhisperGate malwareHosting the archive on DiscordUsing CPL files to trick uneducated users into executing the malwareUsing xor decryption to hide the real codePutting arguments on the stack and using them in functionsDownloading the final payload from a URLPacking the final payload with ASProtectExfiltrating documents to a C2 server
2022-02-08 NSFocus - Apt Retrospection: Lorec53, An Active Russian Hack Group Launched Phishing Attacks Against Georgian Government
PDF: https://contagio.deependresearch.org/read/Ember_Bear_2022_APT_Retrospection__Lorec53%2C_An_Active_Russian_Hack_Group_Launched_Phishing_Attacks_Against_Georgian_Government.pdf
Summary:
In July 2021, a phishing campaign was discovered targeting Georgian government officials and using current political issues to create bait for specific victims.
The campaign utilized phishing documents named "828-ში ცვლილება.doc" and "დევნილთა 2021-2022 წლების სტრატეგიის სამოქმედო გეგმა.doc" to lure victims into enabling the editing feature of Office and executing malicious macros.
The malicious macros created a C# Dropper Trojan that downloaded and executed an AutoIt executable doc, a customized Trojan designed to steal various document-typed files from the victim's computer.
The attacker, tentatively named Lorec53, has been linked to a similar phishing campaign against the Ukrainian government in April 2021.
The attacker is believed to be a Russian hacking group that uses known generation tools to build the attack process and has a bias toward espionage operations.
The attacker controls a large amount of attack resources in the Russian network domain and has been found to conduct long-term vulnerability scanning activities.
Summary:
WhisperGate MBR payload: Tampering with the Master Boot Record (MBR) to render the system inoperable. The ransomware note is stored in a buffer that is written over the MBR.Discord downloader and injector: After gaining a foothold, the stage 2 binary downloads and launches a payload via Discord, which then launches a number of events such as adding Windows Defender exclusion, stopping Windows Defender, and deleting the Windows Defender directory.File corruptor: The file corruptor payload is loaded in memory via process hollowing and targets any local hard drives, attached USB drives, or mounted network shares. The file corruptor scans directories for files matching specific extensions, overwrites the start of each file with 1MB of static data, renames each file with a randomized extension, and deletes itself.
Summary:
The DEV-0586 APT group targeted Ukrainian organizations with WhisperGate wiper malware.WhisperGate is a two-stage wiper malware that masquerades as ransomware. The initial access stage is unknown, but it is suspected to be a supply chain attack.In its first stage, WhisperGate overwrites the Master Boot Record (MBR) with a fake ransom note, making the infected system unable to boot up.In its second stage, WhisperGate corrupts files with certain extensions by overwriting them and renaming them with a random four-byte extension.DEV-0586 uses the following TTPs in their WhisperGate campaign:Execution: The first stage uses Windows Command Shell and the second stage uses PowerShell to connect to its Command and Control server.Defense Evasion & Persistence: WhisperGate modifies the MBR to evade defense and deliver its payload in Base64 encoding.Discovery: The second stage searches for specific file extensions in certain directories.Command and Control: The second stage downloads file corruptor payload from a Discord channel hosted by the APT group.Impact: WhisperGate overwrites the MBR and files, affecting their integrity.
Summary:
The Elephant malware is a threat group associated with pro-Russian cyber attacks, primarily focused on cyber espionage with a focus on key state sectors in Ukraine. The group, also known as UAC-0056, Lorec53, UNC2589, EmberBear, LorecBear, BleedingBear, SaintBear, and TA471, has been active since at least March 2021. The malware is part of the Elephant Framework, a collection of tools written in the Go language and deployed in recent phishing attacks on .gov.ua targets.The Elephant Framework uses the spear-phishing tactic for initial compromise, with emails originating from spoofed Ukrainian email addresses and using social engineering techniques. The launcher component, written in Go language or Python, downloads the malware payload and establishes persistence. The downloader component, Java-sdk.exe, also written in Go, is responsible for downloading the Elephant Framework, which includes two components: GrimPlant, a backdoor that allows remote execution of PowerShell commands, and GraphSteel, a stealer used for data exfiltration of credentials, certificates, passwords, and other sensitive information.GraphSteel exfiltrates information using WebSockets and the GraphQL query language, with all communication encrypted using the AES cipher. The malware runs a heartbeat routine every 20 seconds and an exfiltration routine every 20 minutes, exfiltrating files from designated folders and harvests credentials from various sources.In one reported phishing campaign, the malware deployed a parallel deployment of Cobalt Strike Beacon, which downloads another executable from Discord. The C&C server used by the Elephant Framework is different from the one used by the Cobalt Strike Beacon.
2021-04-06 Malwarebytes - A deep dive into Saint Bot, a new downloader
PDF: http://contagio.deependresearch.org/read/Nodaria_2022_A_deep_dive_into_Saint_Bot%2C_a_new_downloader.pdf
Summary:
The malware was a PowerShell script disguised as a link to a Bitcoin wallet, which led to the download of a lesser-known malware called Saint Bot. Saint Bot is a downloader that can be used to distribute various types of malware and is being actively developed.In March 2021, Malwarebytes analysts discovered a phishing email that contained a zip file with unfamiliar malware.
The malware is distributed through phishing emails with a zip attachment that lures victims with the promise of accessing a Bitcoin wallet.
The malware employs a variety of techniques, including obfuscation and anti-analysis techniques, process injection, and command and control infrastructure and communication.
The initial malware is a .NET downloader that carries another .NET binary in its resources.The second .NET binary is responsible for downloading and deploying two executables, one that disables Windows Defender and another that is the main payload. The main payload is heavily obfuscated and sets up persistence by installing itself in the startup directory and creating a new
The content sent to/from the C2 is obfuscated using an algorithm that is different from the one used to obfuscate internal strings.
2021-11 NSFocus - 2021 Analysis Report on Lorec53 Group
PDF: https://s3.amazonaws.com/contagio.deependresearch.org/read/EmberBear+_2021_-Lorec53-Group+(1).pdf
Summary:
A new APT group called Lorec53 has been identified by NSFOCUS Security Labs, targeting Eastern European countries like Ukraine and Georgia with espionage attacks against government workers.
Lorec53 uses a variety of social engineering techniques, such as phishing attacks, watering hole sites, and lnk script execution, along with temporary domain names like .site, .space, .xyz, and others.
The group has acted like a mercenary hacker group by using the attack methods and network facilities of other hacker groups to launch unique downloaders and spy Trojan programs.
Lorec53's attack payloads include Trojan horse programs like LorecCPL and LorecDocStealer, which have not been seen in other spying activities.
The group prefers to use attack resources from Russia, such as servers owned by Russian service providers and registrants and Trojan horse programs from Russian hacker forums or black markets.
The group's phishing attacks involve fake documents with malicious macros that download and run the LorecDocStealer Trojan, and fake download pages disguised as Adobe Acrobat DC readers, among others.
Lorec53 has also used fake websites, including a fake website for the President of Ukraine, to lure people in and send them malware.
The group is suspected to have been behind a phishing campaign that targeted Iran's Android app, using watering hole sites and an Android Trojan called Pardakht to steal SMS messages from Iranian cell phone users.
| MD5 | SHA1 | SHA256 |
|---|---|---|
| 28f18fc7d9a0ab530742c2314cbd5c32 | 81670ac52bd2356148406e1a6dae97581cb24f99 | 14736be09a7652d206cd6ab35375116ec4fad499bb1b47567e4fd56dcfcd22ea |
| 8409920ef2d78549fc214718c4719d3a | 37cb1ee7842cf73cb9c1eb98a12aad7b6a78b705 | e68c83ce6359691ce63c957ebfdbf959c5b199c83fd2480aebe4220fec9f3304 |
| c73d42d7546fe049f63115635c092288 | da568ee6037959967ea4d5a879c66222d9dff06a | 73e1f2762ffe8e674f08d83c1308362bd96ccd4f64c307ee0a568bc66faf45bb |
| 23cf0517359c014a8d25085eceb2cb25 | 23cf0517359c014a8d25085eceb2cb25 | f3f43f3f4d55c0382f9045fd8093eef66074ca7d97dad066746ace47cc47319a |
| 36ff9ec87c458d6d76b2afbd5120dfae | 9a3161c8570f1ca410038bed6e2aa297aebaf548 | 8ffe7f2eeb0cbfbe158b77bbff3e0055d2ef7138f481b4fac8ade6bfb9b2b0a1 |
| 06124da5b4d6ef31dbfd7a6094fc52a6 | 265a613ac405e6c3557e36a19f0ead2d18638cb0 | 9e9fa8b3b0a59762b429853a36674608df1fa7d7f7140c8fccd7c1946070995a |
| b8b7a10dcc0dad157191620b5d4e5312 | ff37d700d76cb6ed7d123f33362f5017136d1c08 | b5b989f8eab271b63d8ab96d00d5fb5c41ab622e6cfde46ea62189765326af5a |
| 6b413beb61e46241481f556bb5cdb69c | 189f1879fcac60030dd3a751daae46a7444245ff | c83d8b36402639ea3f1ad5d48edc1a22005923aee1c1826afabe27cb3989baa3 |
| 4a5de4784a6005aa8a19fb0889f1947a | a20b0724746a742bf1ea14e6c9571fa6aa29e022 | 99a2b79a4231806d4979aa017ff7e8b804d32bfe9dcc0958d403dfe06bdd0532 |
| aafe14a65c2198e6f70174c620760645 | d0f1518db54f280dde5008404a2750641e76ceb2 | c8e3869f431937f4db3bbb34b0bb4afa3d7e6982d43e81ee840382eeb5525ab2 |
| 563ccff9d1021076a12176ae49404d32 | f9d5b4cd52b42858917a4e1a1a60763c039f8930 | a318fbaddaa11df5edde620b4c45ff31316dcfadf085d0f862004c857be568d7 |
| da305627acf63792acb02afaf83d94d1 | b4100aad572f619632ec28042a76c52ba2350acc | c1afb561cd5363ac5826ce7a72f0055b400b86bd7524da43474c94bc480d7eff |
| 3bfb04e40b548d58ea3a9c8c82aae205 | ba9cea9ae60f473d7990c4fb6247c11c080788d3 | c73a1f1ff53e50e07cd654b2296139747c2c0394ce507de88b2d7a1248b8ac25 |
| 7052d63610b063c859af7f128a0c05cd | 7d44391b76368b8331c4f468f8ddbaf6ee5a6793 | 6e3917257f9239ff1c0ec0c17a7d9b6b01dead526c56218a11b0676174440112 |
| 1c09d7e1f5d2a7ee08a630bb22ade850 | 3a0a4e711c95e35c91a196266aeaf1dc0674739d | 449a8f555ab4ec871612374f638076ad4a7d8d6d628beaaf6799fa7723f9e40a |
| 28267ea322e3975f1e98c64a1c77f509 | e1d92e085df142d703ed9fd9c65ed92562a759fa | 18f24841651461bd84a5eac08be9bce9eab54b133b0e837d5298dac44e199d5f |
| c3c04682c9b03439f022af6052c7c1a8 | 0d94bac4c4df1fe3ad9fd5d6171c7460b30d8203 | ef6f02c41b4bad58fc1930d0ed00a5db1e122b89bc2782ba4dbdc785bc07dba0 |
| cb5e37a1c74b3cd1e4008fd3ee4ef613 | 66117493eed35fbd3824e35971b0919190cd1de7 | 92767e39f24f845c9a12fb44035eda7f801560f8285d7435e82d6c57c059cd83 |
| 26e326ba69f5258c4979902b5bd4f24e | d6e4d803b1062b4f55c1cef61e5a517dd98cd4b7 | 9dec13e1b0ed9337fcbe233d5f83eff09c64a14c7f2400b9b915a685b29612ea |
| aa5e8268e741346c76ebfd1f27941a14 | a6772c80f51d3805d5704f02a80e08501b133fac | 2f92d416f73472db1ebe880b3bec677bcb1d96d6ad62974da00b4be5f6d61f5b |
| d0a11d7904cf6c67b0b947c58aeeeb3c | 3bbe45cdcc2731c0bb4751d1098eccc50f98ef66 | 44a002ea931156d09ebfcb395ac60b7a804a8a7f94d4fb5b2fa8aa7268e1bc28 |
| d8beed484e8e7e171aeaa6753ac8d8b8 | ac672a07c62d48c0a7f98554038913770efaef11 | 424ca2f8aec060f5a7268f543b71e7038d90bec60914f5380cebdbfcfd1f041d |
| 5f6aacd3106f727d45c295fd0f25054d | 0d584d72fe321332df0b0a17720191ad96737f47 | 14bde11c50a2df2401831fea50760dd6cf9a492a3a98753ab3b1c6ce4d079196 |
| 49ac3e120ee12d904145dfaefd041c0c | 75afd05e721553211ce2b6d6760b3e6426378469 | 01b620642cc6ed6b75d0d1ee307f117fbd45ce5f1bd67d95bd80daa104e80e2f |
| 2e0f1315c52e8b017fb6110398b28e60 | d9b4676229dbe5192d9ec22b017b6ffa2f76f9bd | ba1066f7a47b3662b1589579c9b7100a6f275a1cd82de75b166f31e9ee913562 |
| 15c525b74b7251cfa1f7c471975f3f95 | 51267f49e508965de494441aacd8a0c8b43e7b54 | 39b3c82b1e7e5626e380a53df4ccb52f3002749447cfab362b8ec217189a0fd5 |
| beaed555048e1074fc13cdf8431abd49 | ec148ab5332da96df92e87e9b5a8e66bb517a1de | 0d0a675516f1ff9247f74df31e90f06b0fea160953e5e3bada5d1c8304cfbe63 |
| ec18353f05c0ec9c014d4eb57f35dd40 | 00e59476d9e250b342131d96bb67fea917c6152c | eee1d29a425231d981efbc25b6d87fdb9ca9c0e4e3eb393472d5967f7649a1e6 |
| ef81f74875718d370876289088c93150 | 1e749ae20fe5d6ce46dbee6d4a27e8f6dec38d9d | 878450da2e44f5c89ce1af91479b9a9491fe45211fee312354dfe69e967622db |
| aa6f5570b814e336cc91e57f1dbbf22c | 3d022052c70ecc34dfbfac318b05ca7e6ba4a244 | 80e6a9079deffd6837363709f230f6ab3b2fe80af5ad30e46f6470a0c73e75a7 |
| 89eb4a35ea3122f01f47abe5e8b4982a | 5a85b4e69a7169897fadca712eab31c805689509 | f0fd55b743a2e8f995820884e6e684f1150e7a6369712afe9edb57ffd09ad4c1 |
| 8b245119a08313ede84ecda10d2b83c7 | 32ce463f1125a5de26aa07377e0a7d5a86bda8b3 | 4787c415dd0114e4b709e684b3ed686aed3d0c11549427ee23083c7ba53ef0e0 |
| 628f41776ae3b2e8343eeb9cdcd019f2 | d77421caae67f4955529f91f229b31317dff0a95 | 8e77118d819681fdc49ce3362d8bfd8f51f8469353396be7113c5a8978a171f6 |
| eee2f9fab737eef8884e0b9432055edc | ed4f5914178324405ec4b12b693313fae6ac47ee | 47a734e624dac47b9043606c8833001dde8f341d71f77129da2eade4e02b3878 |
| b3370eb3c5ef6c536195b3bea0120929 | b2d863fc444b99c479859ad7f012b840f896172e | 923eb77b3c9e11d6c56052318c119c1a22d11ab71675e6b95d05eeb73d1accd6 |
| 4c2e3c21a4b4eeec05dc364b854c57d6 | 1c10158495a90ad1dfa1092cb80e387bd82f38df | 5cda471f91413a31d3bc0e05176c4eb9180dfcac3695b83edd6a5d4b544fe3f1 |
| be2d21ce56597f0ba2610852f6b9a122 | 1175dc063ab6f17f28300f0c624e59c35283a04f | 8bb427b4f80fe1ede3e3ed452d9f0a4ce202b77cda4ad2d54968ab43578e9fa9 |
| cdcbd3dd6a5be09f409c47995a4de934 | 769dc031f90c296e14c7e2c38823743933e75956 | b89a71c9dbc9492ecb9debb38987ab25a9f1d9c41c6fbc33e67cac055c2664bc |
| 09a833a75039f9b3e923683b32344415 | ac44f6b7caa9bb14483623a9bf5f738d13808120 | 35180c81ebcefbc32c2442c683cab6fd299af797a0493d38589d5c5d1d6b5313 |
| c6e7af8d31a951b8c05565ab18c4f258 | 8da49c2dbaf1abd4b2ba81669b201e2ab5b95926 | 024054ff04e0fd75a4765dd705067a6b336caa751f0a804fefce787382ac45c1 |
| dd9439b5cb3b1fc91181092f9da5aa69 | f2b8ab6f531621ab355912de64385410c39c1909 | db03917ca3cb91cdebcb681fa2733c1a2a9679e5201beeba21aee911de05973e |
| 5d735d8c7243f61a30f5e91539f76df9 | 26474ba449682e82ca38fef32836dcb23ee24012 | f00b523635707cf97be5877c9dea1abec7abf8d0e6bcce529cc96826344511a0 |
| 410ff2fc20418aceee5fcbc7ab56076b | 931a86f402fee99ae1358bb0b76d055b2d04518f | 0f13f5f9a53a78fc4f528e352cd94929ae802873374ffb9ac6a16652bd9ea4c5 |
| 48e26159d9aa517ba2a1f1010c8e7c00 | dbc9c8a492ae270bb7ed845680b81b94483ab585 | 7e1355e51eb9c38e006368de1ae80b268ffab6918237696474f50802e3d8a9c8 |
| c717265dc91b1980921320c8d6257b53 | dd2444ddba96fa070559828934c025b4c2fae86a | 07ed980373c344fd37d7bdf294636dff796523721c883d48bb518b2e98774f2c |
| 6af7a85274f02d1bc61f2d90674cb131 | 15791db60928df6d7a86d80b80b88609c15aaa20 | 2b15ade9de6fb993149f27c802bb5bc95ad3fc1ca5f2e86622a044cf3541a70d |
| 5077eff8ea0ad83e30860ec93c18fc2a | 693607b23dec9d41a373a41aed2e8c32e17098d1 | 891f526fea4d9490a8899ce895ce86af102a09a50b40507645fee0cf2ab5bef5 |
| 900e892c8151f0f59a93af1206583ce6 | aea15a7ce95761a556199f5a774be293a82c17c2 | 96f815abb422bb75117e867384306a3f1b3625e48b81c44ebf032953deb2b3ff |
| f7f23e5f3ff42eef595bb4b804c68eea | 968126ecd4e526e9b6e1a16e9d001efcfde8fad1 | 157b05db61aaf171823c7897a2f931d96a62083a3ad6014cb41c6b42694a0c2f |
| 0e16df6845cde1260087902f25842f79 | 5698c8836bf2d5b542a7534b9a49c29beba3af43 | a356be890d2f48789b46cd1d393a838be10bdea79f12a10b1adf1d78178343c5 |
| b2a5d1107613834cd380b492afcdd930 | 9394c4528bfb504d6a4aee256dbbbd1cf177b821 | 882597c251905f9be31352ba034835764124c9a9e25ef1ba0150e5998c621f07 |
| ae9b71972359f44c60ff636a761efd69 | 82e3bf5efbad08d27428aacd27018bec8b040f34 | 2c879f5d97f126820f1fbf575df7e681c90f027062b6bcb3451bb09607c922da |
| 6296f167c93a0ca4dd75af9c23c94232 | 9a97b0957ddc18e4c445099f533d2400f5dd2788 | 52173598ca2f4a023ec193261b0f65f57d9be3cb448cd6e2fcc0c8f3f15eaaf7 |
| 122975532c1e1af554d4d39511e7eb3e | 8290ba1e792c291ea039fdb459c652e2c7fea5ad | 63d7b35ca907673634ea66e73d6a38486b0b043f3d511ec2d2209597c7898ae8 |
| 5ab92ca35e41b9a7aa07cc7efc60bbd1 | 468a2d057a805ca971047b6fbd5ec359a67bc20a | 461eeadbe118b5ad64a62f2991a8bd66bdcd3dd1808cd7070871e7cc02effad7 |
| a8bb31dcf791e09e656618ab726cdc2d | 9533ffa146e213e64e70c236344cf84484caa993 | c9761f30956f5ba1ac9abc8b000eae8686158d05238d9e156f42dd5c17520296 |
| 081a6edd07e2de8c8161380bcd60547c | 3d0011d42e69b962f97b2d35f25012c4e5da55fe | b7c6b82a8074737fb35adccddf63abeca71573fe759bd6937cd36af5658af864 |
| 1f7fc4fd6c7d2735dfc446f62ada2e09 | d2694a3201e45a5d4239b36483e0c6b05b4fff1d | d99f998207c38fe3ab98b0840707227af4d96c1980a5c2f8f9ac7062fab0596d |
| 096eef1eb2bb266e37f1eeca0db21bd5 | 5727ee8b41c309e0935748a2fd9633d0f972013a | 354868cd615a0377e0028bcaee422c29f6b6088b83a0b37a32e00cce5dba43f9 |
| 333796e18eb3f3d1529d07ec90c63e61 | 051f30587f7ab8101602b40748f7f21fac21658a | 0be1801a6c5ca473e2563b6b77e76167d88828e1347db4215b7a83e161dae67f |
| 847b071fa537e21507e78c80b5aa7d59 | 9455119a6522727905dd14ee3b29e87f55e88a26 | a60f4a353ea89adc8def453c8a1e65ea2ecc46c64d0d9ea375ca4e85e1c428fd |
| efcff826fa14c23c9abcd53e0a148383 | f79f22761707f666178f8855fcfb95a46065dd21 | f6ae1d54de68b48ba8bd5262233edaec6669c18f05f986764cf9873ce3247166 |
| 51e5c14cd5a2be650ab6e932b86d29f2 | a65f8e57c960bf32fef0ab2d611dbb1871b024a2 | 4fcfe7718ea860ab5c6d19b27811f81683576e7bb60da3db85b4658230414b70 |
| 44697aad796c0d82c1adbee15fd1266b | 0349463deb6e3803c425fa7725f7dedaccc6e6aa | 9803e65afa5b8eef0b6f7ced42ebd15f979889b791b8eadfc98e7f102853451a |
| 99b983e5885f7418a950b822b5d5acc5 | ab94ce54005fc530851bf5443117441e91555b24 | 92af444e0e9e4e49deda3b7e5724aaecbb7baf888b6399ec15032df31978f4cf |
| f7b0f59bff65176713c678693f1bf1f2 | 417858f4722442a311f4ef2d5126c8a8cae760cb | a16e466bed46fcf9c0a771ca0e41bc42a1ac13e66717354e4824f61d1695dbb1 |
| 5107d2108da21e3572db8087060a53c0 | c0e9735b42f00ea0c45a5eb3c1b858a407fb3fcb | 64057982a5874a9ccdb1b53fc15dd40f298eda2eb38324ac676329f5c81b64e0 |
| fa23f43fa759f0f38cde2b703d98ba05 | 0412055469c67c4cfc63b3c412833d064ec06270 | fbe13003a4e39a5dea3648ee906ea7b86ed121fd3136f15678cf1597d216c58a |
| b56975725c4e260370af540f9c0b6709 | 77741870383a8d347c407ffda23e26d1b440500e | f69125eafdd54e1aae10707e0d95b0526e80b3b224f2b64f5f6d65485ca9e886 |
| 6bbe141ee44548490fbc55127e59fd37 | 63d1b7fcb7d00a1b8326c896e30dc2b44c54ca1e | 2ec710d38a0919f9f472b220cfe8d554a30d24bfa4bdd90b96105cee842cf40d |
| c26566e3ac35986456f68bbd9e29db73 | 1dde1d09bd13d54baf2022974e83ddbc623880b2 | 1092d367692045995fab78ba1b9b236d5b99d817dd09cba69fd3834e45bd3ddf |
| 7de66b5c7d3ddae321fa6cfeeaa94819 | 2c399c6b34a3ff2e09b29ed98d941d9550ad423b | 276ac9b9fe682d76382ec6e5bc3d1d045ce937438f92949c23453468eb62a143 |
| 2ce1c17b5a46a7fc42f98c67edf2e409 | f0f8095dce21916470f0aea2b9d0b8486038fe54 | 275388ffad3a1046087068a296a6060ed372d5d4ef6cf174f55c3b4ec7e8a0e8 |
| dbdb7908b3c16fac52a8e279b43ac83c | 02e623c353ca99c8572c9bf44a4d288f5d41ad98 | 677500881c64f4789025f46f3d0e853c00f2f41216eb2f2aaa1a6c59884b04cc |
| 549334edbfacd98b6c5c3154949d5b12 | a17eef04cf987d16ab2f7c23f97885e6e428f500 | 33a4655fd61e471d8956bc7681ee56a9926da91df3583b79e80cb26a14e45548 |
| 12840e2c8a5f378153d9eaea226c592b | a6cfa25e5a9eb7fca97b19b2f5b8003ed7c7aaae | dfe11b83da7c4dc02ff7675d086ff7ddd97fec71c62cc96f1a391f574bec6b4f |
| df45ee66dd410b491e3e01c8880f6966 | e4fec41a80337c87acc8f67864047aba34690bb4 | 434d39bfbcee378ed62a02aa40acc6507aa00b2a3cb0bf356c0b23cc9eebcd77 |
| 664104684583dcca00c6aa94b2d5e8ca | 9b41eac0a97ab72885cd15e4d6beb93cfc55ae6d | f0d99b7056dac946af19b50e27855b89f00550d3d8dc420a28731814a039d052 |
| 5897322f62070e894488b4115463939d | 217490d9df6b3eb30caec933c6f3a04ae3a3a82f | 101d9f3a9e4a8d0c8d80bcd40082e10ab71a7d45a04ab443ef8761dfad246ca5 |
| 0a3d8fae9ffbe6b9e8cfdeb4c485cf88 | e89ae58166546908d3e4ecf1b0eba601c17c1882 | 5d8c5bb9858fb51271d344eac586cff3f440c074254f165c23dd87b985b2110b |
| 19b6965b648160b89e7057ab02898162 | 1d3b1bfecbbc17d521e4da93104a426bd690b392 | 5d9c7192cae28f4b6cc0463efe8f4361e449f87c2ad5e74a6192a0ad96525417 |
| 7516e343441c2f0e782dd42f5fa85d8b | 54a8dd58216e1afa4b718e51fa86b435bd08f621 | 90ce65b0b91df898de16aa652d7603566748ac32857972f7d568925821764e17 |
| 803f772489ff905eccdc4684def6adde | fbb3e24f9d517714c312fc88d7e60ab05860dff6 | 10d21d4bf93e78a059a32b0210bd7891e349aabe88d0184d162c104b1e8bee2e |
| 5e8c9f85256e83d6042bbbac2905d1f3 | e4d3b29b69ce6d80bb8d1c6309d1c7ebb12f9942 | 0db336cab2ca69d630d6b7676e5eab86252673b1197b34cf4e3351807229f12a |
| 5f6aacd3106f727d45c295fd0f25054d | 0d584d72fe321332df0b0a17720191ad96737f47 | 14bde11c50a2df2401831fea50760dd6cf9a492a3a98753ab3b1c6ce4d079196 |
| db6ea5fcda79fc4253f423fce607dddc | 9cd4c35204e7753ec5ae5836a0398e960e964241 | e39a12f34bb8a7a5a03fd23f351846088692e1248a3952e488102d3aea577644 |
| 66de28a0d0769f9b7f1397ebd10d2ab4 | be7ca341419631d12032ac64269d9c36e445f9b5 | 68313c90ca8eb0d5fc5e63e2b0f7a5f4d1fe15f825fe8ca0b4b3e922a253caa7 |
| dc202f657b67b99186b20cd15ae85184 | 6c38f8ad13512c535a1350e50378d0e5c36f9867 | 5227adda2d80fb9b66110eeb26d57e69bbbb7bd681aecc3b1e882dc15e06be17 |
| afc8158cd8f52a526dc77bd2236e0987 | d90ccb4cc0c19a71d90eb768d1c9957478971d74 | 84e651b2d55a75ec59b861b11a8f8f7cb155ed81604081c95dd11b8aec5b31b1 |
| be339b83946635d6aa3b1dc3e42c1b02 | 9786ed20fce197edbab2f1bc4c61d153b353bb78 | 8c8ef518239308216d06b4bf9b2771dbb70759cb1c9e6327a1cd045444f2b69a |
| 09a4937fa4256020c5b1a5efee53452a | 8dca575d32a4c362e81eabe4d778e9ac6acedf01 | 5dabf2e0fcc2366d512eda2a37d73f4d6c381aa5cb8e35e9ce7f53dae1065e4a |
| aa3e4c243b101ed6c92b38fe8670a724 | b85ef90888d2169252af104e809726e92aa518ef | 172f12c692611e928e4ea42b883b90147888b54a8fb858fc97140b82eef409f3 |
| d7510192dd826e6c63266ba412c4a8c6 | e51431ab4448d503db3d154d1da7bec25eb5aaac | ffad5217eb782aced4ab2c746b49891b496e1b90331ca24186f8349a5fa71a28 |
| 65792e4d02f910d20dcf74487cb9fab1 | 942337f3ea28f553b47dc05726bb062befe09fef | 9fbeb629ea0dc72ac8db680855984d51b28c1195e48abff2e68b0228f49d5b0f |
| a92bd5072f0e3e683be1b27117df76d7 | a80db2f724e6d10c4b704f8e221c0946f5a12ad8 | 2bef4a398a88749828afac59b773ae8b31c8e4e5b499aad516dd39ada1a11eca |
| 059c5bbec45da7e50d92a54160622d36 | a97230965dea34f32ac9db418aece125ceb63426 | b83c41763b5e861e15614d3d6ab8573c7948bf176143ee4142516e9b8bcb4423 |
| cb408fab657233d0ed6aff130def8984 | 598f9c6d330d6a3ab2428d66655694b0f1bb9856 | f4a56c86e2903d509ede20609182fbe001b3a3ca05f8c23c597189935d4f71b8 |
| 75d6f57cfba0ebc3633a49a8412a43e5 | dd7a31b07f1dfdcdbb72f59c3535636b41d0eaad | 2d9d61ce6c01329808db1ca466c1c5fbf405e4e869ed04c59f0e45d7ad12f25b |
| 29e47258c517f5f33349caacef044645 | 42cfb37c1f47de8f1ef6f4dbd047c1a06922adc0 | c6c47d3d7e56213f0d0ced379c64e166ed5a86308ea96856163a4e0155b1fc6e |
| ede3bf69a09cec27ded2d20c95ca78e3 | 8d3a1b800d73d5315998b3b5f966b084fdb4b806 | 320d091b3f8de8688ce3b45cdda64a451ea6c22da1fcea60fe31101eb6f0f6c2 |
| a718ba0edee0b2108aad0ce0fd7fdd0f | 711b27ab368a13ccda3c279a8645a77c8e9fbf4e | 9917c962b7e0a36592c4740d193adbd31bc1eae748d2b441e77817d648487cff |
| e9da5c53a8d86b9616c4163423699dbd | f5af420de5ae4835a292d262a398342f73a53ef5 | 0c644fedcb4298b705d24f2dee45dda0ae5dd6322d1607e342bcf1d42b59436c |
| 2a211218afa6a34db27c1ac6f6ba3390 | 92fa9d3de5d976391e2dc3ca6fcf053ae072b654 | b02c420e6f8a977cd254cd69281a7e8ce8026bda3fc594e1fc550c3b5e41565d |
| b69de5d4550ed214bcc8ad2f839735d8 | f7806011d03923ffe4f4eb92891289efdeb003e8 | ec8868287e3f0f851ff7a2b0e7352055b591a2b2cb1c2a76c53885dee66562dc |
| abc87856247dea1e4d01e2c3b352ab77 | fa48ec02991837bd7ce2248a130da934ec6555ad | db8975fd6c04a7d3790eb73ab8e95b6dbf6c9d65ad5c6a6d3c862d0284f87c34 |
| 3b6f68801cade1cd388138500fd8e986 | 9bc818e0e6ef9aaafb02065800a97d8bd98ee76d | a61725f3b57fd45487688ad06f152d0db139a6cb29f3515ea90ffe15cb7e9a7a |
| ed1deddf6287d2435e1c4c02daf0278d | 7b67ed1f42e5cf388a0a981566598e716d9b4f99 | d4d4aa7d621379645d28f3a16b3ba41b971216869f5448ea5c1fc2e78cfecb26 |
| 103118660a0abadc99831e23777979b5 | f69be5dcf16ef31a9aa66dce34f35fd84972f3e7 | afdc010fc134b0b4a8b8788d084c6b0cff9ea255d84032571e038f1a29b56d0a |
| eb0309e8c3246307635d24d035322895 | 9bdea3ab3b6ea567997de2d9ad37d5dbe5cd863e | 975f9ce0769a079e99f06870122e9c4d394dfd51a6020818feeef9ccdb8b0614 |
| 593ac1acb0452748340d6a5ccdb18f12 | 2d2af604a8e4f0df9b36c047c8f9e9b0759327e9 | 82d2779e90cbc9078aa70d7dc6957ff0d6d06c127701c820971c9c572ba3058e |
| 79c66ae4a99e15d855785cbf98762e21 | ccf3715644dc622e8f3815e2feda5fa62e7d5ad1 | f2bdde99f9f6db249f4f0cb1fb8208198ac5bf55976a94f6a1cebfb0d6c30551 |
| 92ce4437539947884d25ac80756a624f | 1a4ef45b728cd415a92eac24b91140bd1cf466db | 61f5e96ec124fef0c11d8152ee7c6441da0ea954534ace3f5f5ec631dd4f1196 |
| fe6663b00d94a8106c07b4a951522266 | 24492ca47b178e1990c4e5bd684547bb62bfad7a | 4c8a433ed99cc4b6994b2e1df59eb171f326373ba100a3653eb37e8a8ee2e6f2 |
| 304d1ac0296fedec694a097480b341d9 | fb60d4ab152acf71847dbbd36c75b8032c5da303 | b2f5edef0e599005e205443b20f6ffd9804681b260eec52fa2f7533622f46a6c |
| e852e90f778f616f09900b4f1b05c03c | 91b6442fa2c070f07437a887fbb42805bf59b8cb | dfc24fa837b6cd3210e7ea0802db3dcf7bb1f85bff2c1b4bda4c3c599821bf8c |
| 6181cb68aa34a470503452087a63bc1b | 2b12581fbfcf812b39d00854e71c9ff641d2f79a | 005d2d373e7ba5ee42010870b9f9bf829213a42b2dd3c4f3f4405c8b904641f2 |
| ab2a92e0fc5a6f63336e442f34089f16 | 24f71409bde9d01e3519236e66f3452236302e46 | e8207e8c31a8613112223d126d4f12e7a5f8caf4acaaf40834302ce49f37cc9c |
| 259f06fcdb971f606d239b3178110981 | e2180bf4b9783d42d396826fc25ff8f9394cd430 | f58c41d83c0f1c1e8c1c3bd99ab6deabb14a763b54a3c5f1e821210c0536c3ff |
| b8cd8b40bda5bec1e8d5b765b5a90db4 | 41057c8497d0845fd54771d0e23ca234af9b3b2c | df3b1ad5445d628c24c1308aa6cb476bd9a06f0095a2b285927964339866b2c3 |
| 2371d432700a7e1f9c070a6e97fdb634 | 00d6c66ab2fd1810628d13980cc73275884933b1 | fa1bc7d6f03a49af50f7153814a078a32f24f353c9cb2b8e3f329888f2b37a6e |
| 247951ff7b519fa8d39ef07d33e0ba5b | cf4587b6015d2a00c26a369339504595a266401f | ec3c0afccfef11f753a408c859d98bbba4841e87f7f1a48573270c0d82252b03 |
| fa4d702a335aab44355c84863395617a | a2a308cec43c9bea9260243970aa914fb8751707 | bd83e801b836906bab4854351b4d6000e0a435736524a504b9839b5f7bdf97cc |
| ec0883bd8594cc34092a5e9a70a1b249 | 4ba9c7d411006de1bf589eac2fa179d1d7120468 | c222122fe3e1206ba2363c17fb37ae2f8e271840e17b3bb9ba5359f2793f9574 |
| 2e0cee9eb10dd9dbe060f5a25cebfa80 | b7d4ade87108f36ff04b07c7adba6a2be6005412 | 27868ae50b849506121c36b00d92afe3115ce2f041cc28476db8dfc0cc1d6908 |
| f6ce89bf34e3ff6509a32347c400ca8d | c4da78729b0e12c30c55036b1df7093ccd0ef719 | 8ab3879ed4b1601feb0de11637c9c4d1baeb5266f399d822f565299e5c1cd0c4 |
| 6bd9390577ee23f236d81f7d20d47fea | 34a08fbfe099b70fa547b240d0b1ddd41c4959a5 | 3075a467e89643d1f37e9413a2b38328fbec4dd1717ae57128fdf1da2fe39819 |
| d34f6a8493b14371e552f9f317aac50f | 884917375758a77f708c96648477012a70579c02 | 0222f6bdfd21c41650bcb056f618ee9e4724e722b3abcd8731b92a99167c6f8d |
| 01033729316e2886515a15dc93ea85c4 | 8d7e3b9e1f5cedeb6050f4808ec057fe6603c3eb | cd93f6df63187e3ac31ea56339f9b859b0f4fbe3e73e1c07192cef4c9a6f8b08 |
| 572fdac6723a4031febc449795f51df5 | fdf8662e68a5dfc900cec85fa509ac392471e856 | 9cf4b83688dd5035623182d6a895c61e1e71ea02dc3e474111810f6641df1d69 |
| a7913461e211158d5ac34ac3bd06bc7b | 71c3f7a9eac34b0b5ccd5ec2df01f9c95f14235b | 5fc108db5114be4174cb9365f86a17e25164a05cc1e90ef9ee29ab30abed3a13 |
| e0ca9d7fdf345af474332533ee50dfb6 | 303f5df8841a33886413435a61809d338a66639b | cb4a93864a19fc14c1e5221912f8e7f409b5b8d835f1b3acc3712b80e4a909f1 |
| 23f5b5fcd6f181088af23614bf6e015f | edba6f00b0b697b59ce958c01f8c62bfac51b021 | 9ec80626504ca869f5e731aef720e446936333aaf6ab32bae03c0de3c2299f34 |
| 7327a3dd34b3a6c218d00ef9cfa2ef1b | 2b12fae645fce9c944e6035f6e69bdc67103f28d | a9a89bb76c6f06277b729bc2de5e1aaef05fc0d9675edbc0895c7591c35f17eb |
| d9300ff1b9e6c7ef3f1c6cac4c30bb72 | 833a8f095aa555f3fa3e873adadc0879a4bcfc5a | 71e9cc55f159f2cec96de4f15b3c94c2b076f97d5d8cecb60b8857e7a8113a35 |
| e3ffe9b1db336ca7f34e0f26215d4ee4 | 3ec434df80529311342401ac7a7acd066e19c90f | 700b05fede8afe3573b6fec81452d4b09c29adb003cdacb762c8b53d84709901 |
| e65e7ca60642f80fe2a95823247f8726 | fc0700076fd443edb24777e4ee7eed802411fd70 | e0c46e23bd1b5b96123e0c64914484bbfae7a7ad13cbd45184035d4c0f8a10a2 |
| 893b17ed65ecffa8376063349f22d2bc | 50c556277899d6b9da5ec125c0a58650a14a08a7 | ebbf30e06de3a25f76cf43c72c521d14a27053e4d9be566b41f50c41bea3a7a9 |
| 2124d2e449117ecbc66c3e67e3ed289c | 5455fb1f943ec04431c69857806de4a7a0625eb3 | 707971879e65cbd70fd371ae76767d3a7bff028b56204ca64f27e93609c8c473 |
| 45abce50a00d40dff21edb7264824758 | 0861d2abbcf16bf6394dc7aadd341b348a3c8c4d | 3f7b0d15f4cbe63e57fb06b57575bf6dd9eb777c737b0886250166768169fc6c |
| d4fa9c88bd43d2b9bcb66c3e7292b52a | 5cf627b7cc836506958a5e04e902f8530cdb58b6 | b8ce958f56087c6cd55fa2131a1cd3256063e7c73adf36af313054b0f17b7b43 |
| 13ea6a80588a9eeea6b919a4f104a7de | 7e79e0459e7aa0fa54bd5a2e5e79b6c0587f2334 | 1e6596320a3fa48d8c13609a66e639b35fb1e9caae378552956aa9659809162b |
| e4855693722de3856421b1b6920ba54d | 9c50313f3b6d84a2b063d0acca64417bfe283d6d | 0e1e2f87699a24d1d7b0d984c3622971028a0cafaf665c791c70215f76c7c8fe |
| d377c71f7df1c515705eb6b0cc745f7d | a2ac278ec99ec0bcab10b55427753327da1cc3a4 | 89da9a4a5c26b7818e5660b33941b45c8838fa7cfa15685adfe83ff84463799a |
| 091cd6e1b1addd88794b7ea0dd09750d | 97f4863b80f584d5505e799661976f588624b383 | 9ef2d114c329c169e7b62f89a02d3f7395cb487fcd6cff4e7cac1eb198407ba6 |
| e640bdb76d7b30cb9ca9250d5b6631e3 | 0540792efa9eb7ecdcfce3340dc0be1204c1e8c8 | b1af67bcfaa99c369960580f86e7c1a42fc473dd85a0a4d3b1c989a6bc138a42 |
| 44f05f473b7d568be2abd9d498fc10ef | e9768aac3c51d92a377d7b91e6863c38ea762680 | b72188ba545ad865eb34954afbbdf2c9e8ebc465a87c5122cebb711f41005939 |
| 7910a78498cb7953b1c0db2ef4f8db27 | 8f61608330261c1d5214f5d19f98b4d64f51ac12 | 9528a97d8d73b0dbed2ac496991f0a2eecc5a857d22e994d227ae7c3bef7296f |
| 1bf3028a0b65a4174a66f3677e872026 | 1e33b01f84a96b93cdded1d23fdb1b7f6f58a077 | 619393d5caf08cf12e3e447e71b139a064978216122e40f769ac8838a7edfca4 |
| 78e941e780adc1a159fdc7090194c96d | 9cd8a786572a7ee8713492302555fe4ce3432911 | 7ee8cfde9e4c718af6783ddd8341d63c4919851ba6418b599b2f3c2ac8d70a32 |
| 3640ff45519f1acc1505348010626b6d | d5b85fddbf7c893e50560da787d7bc0dcef658e9 | 4ee84419fb9267081480954f1be176095a45fe299078dfa95f980e513b46a020 |
| d3d15e62d61981e85ae81ad54bd23b40 | 053d987ff528964bf18ffc1898acd678b8917dd7 | 6ee2fd3994acdbb9a1b1680ccd3ac4b7dcb077b30b44c8677252202a03dccf79 |
| b9d5a18d4cb2ad3afddacc3a3a25b146 | a6c5f29fe14fb234fc0801c348876f215c30e0ff | 494122ff204f3dedaa8f0027f9f98971b32c50acbcce4efa8de0498efa148365 |
| bafdcdfdac4e0d5a835c1048af2a3815 | 8ed85a4739ab5945ee21e05947eb204ef04bcc02 | fad2e8293cf38eec695b1b5c012e187999bd94fbcad91d8f110605a9709c31b3 |
| 67b8f4bb9c81aca61abf8d49640a85b9 | fbf00a827bf1a44340a1e4bb1698285b27dab56c | 7b3d377ca2f6f9ea48265a80355fe6dc622a9b4b43855a9ddec7eb5e4666a1d4 |
| dfff334622bccba782126e953bcf1fae | cac977827bc96e7ee2a9291f315f0da4e4eedb70 | 9ee1a587acaddb45481aebd5778a6c293fe94f70fe89b4961098eb7ba32624a8 |
| 48e26159d9aa517ba2a1f1010c8e7c00 | dbc9c8a492ae270bb7ed845680b81b94483ab585 | 7e1355e51eb9c38e006368de1ae80b268ffab6918237696474f50802e3d8a9c8 |
| c5baf146ada97b638b337d94eaeabe22 | aa3e65e4881e937b51286c3ae0649df5dd7eda6d | d6e2a79bc87d48819fabe332dd3539f572605bb6091d34ae7d25ae0934b606b5 |
| ae37c9bfa13df2a6353039fe6e7a54e7 | c99c15bd925d9364b5101f490bdcb05e3227b2cf | b6e34665dd0d045c2c79bf3148f34da0b877514a6b083b7c8c7e2577362463b3 |
| 66c3ae9bddbbbcc2cc979d23792f15ac | 822c3ee867e390135c260590da2c7bca5dd3112e | b0b0cb50456a989114468733428ca9ef8096b18bce256634811ddf81f2119274 |
| 167ac4792548676f7e9b648a5c4b5546 | 90ef8db9cea3d981535659c4fa6b1476744b3834 | 4d59a7739f15c17f144587762447d5abb81c01f16224a3f7ce5897d1b6f7ee77 |
| eb332fd9cc8be8e6a60d4ff9c5f5fcf7 | e18df098c2fcb6a3961c310fdde58106e07ef9c0 | 4715a5009de403edd2dd480cf5c78531ee937381f2e69e0fb265b2e9f81f15c4 |
| c073d9f6c0af5eff0a7150debe1d63db | d838a5b99044f8be1030a179ad3f8322ea4fb010 | ec62c984941954f0eb4f3e8baee455410a9dc0deb222360d376e28981c53b1a0 |
| 2699077a996951eac7b369b6356ff296 | 8c6acecf8009665e0670ce634ce8f0d2907481c1 | 7419f0798c70888e7197f69ed1091620b2c6fbefead086b5faf23badf0474044 |
| e3ed0d3b6f801d8ffe8dc18b262c14c5 | a3c499d65a090b2df7fb519a9a366f4cb3d39f79 | 506c90747976c4cc3296a4a8b85f388ab97b6c1cfae11096f95977641b8f8b6f |
| ee6021e6682455f1bb8bead3d761530d | 9bfe2745dd3123d6c0e3057717e394b6ca601588 | 0fc7154ebd80ea5d81d82e3a4920cb2699a8dd7c31100ca8ec0693a7bd4af8b7 |
| f1639890944c37c25e1a4bdea35a6012 | 228684d884a11f1434620ce8e9af9226ab636658 | 6a698edb366f25f156e4b481639903d816c5f5525668f65e2c097ef682afc269 |
| a7eb8d7b83e5fd622c1e205c911a110a | c685312922a40d841e583f9399f66d35d6ccfb46 | 187e0a02620b7775c2a8f88d5b27e80b5d419ad156afc50ef217a95547d0feaa |
| a31cb445d3131bf567720c43f2a74484 | 29e763a59424f9bb147df11a7b2ebfe9373a451f | 56731c777896837782beff4432330486a941e4f3af44b4d24be7c62c16e96256 |
| 9ae3d8ba1311af690523aeb2e69bb469 | 1357dbf294817122b1e193762fb3d66a5d73e651 | c33a905e513005cee9071ed10933b8e6a11be2335755660e3f7b2adf554f704a |
| 89aafef2f334d6349d3d850e7f68f10f | 97b4b5f19be70177dc5f867ed580478c9dc7e2b6 | b0b4550ba09080e02c8a15cec8b5aeaa9fbb193cec1d92c793bdede78a70cec6 |
| 363e2b62f93c58c177e58dbe0a247fa0 | e8abab85ccbaf646305aa5a786c0894d59bdcfd1 | 75f728fa692347e096386acd19a5da9b02dca372b66918be7171c522d9c6b42d |
| 959553930a01d5518588340aa55a2de2 | 32e80ffc4948828009b192076fa85922528a5740 | 1a1fe7b6455153152037668d47c7c42a068b334b91949739ed93256d5e3fbd89 |
| 124f0b9dadbef030a4cba26393ce25df | 15479f31109fd0a367ad681fb3ee63c6fb0ade0a | 3d7a05e7ba9b3dd84017acab9aab59b459db6c50e9224ec1827cbf0a2aee47db |
| 946a1974ec330a30aadb514efe8c394d | 7af3c242e9dd444a7498de118911b0f5ad49a969 | 2762cbc81056348f2816de01e93d43398ba65354252c97928a56031e32ec776f |
| efec7686f695867bd45a4d2ccaf964d5 | 04af410cffd8f4b7ef0270ccae11ce6e01cc4633 | cce564eb25a80549d746c180832d0b3d45dcd4419d9454470bfd7517868d0e10 |
| ee3895f50bbc6316a746c239afc47e71 | 4aaf0acb7891fe06868ea442f55e5913961117d7 | 39e8455d21447e32141dc064eb7504c6925f823bf6d9c8ce004d44cb8facc80b |
| fd0ed9f5ffa9c912ba8d677687776448 | b7abe535dccf587c80cbcd2d4cc0c30e330b3a54 | 750c447d6e3c7d74ccab736a0082ef437b1cd2000d761d3aff2b73227457b29c |
| cf584e69d6832fb7f92af0633e6e5222 | fb652a73f6d6de07d22e13de5a19e9fc6f9814b5 | f24ee966ef2dd31204b900b5c7eb7e367bc18ff92a13422d800c25dbb1de1e99 |
| c96cfe462657240c155d4b1842292a4c | e94483c338213c667720a44d89c12a3f50547c71 | ff07325f5454c46e883fefc7106829f75c27e3aaf312eb3ab50525faba51c23c |
| 83cd7984cee0a4fde468216521d9d3fc | e8fa43110dd36085d79199788d2ea5c57236136e | 37be3d8810959e63d5b6535164e51f16ccea9ca11d7dab7c1dfaa335affe6e3d |
| 28267ea322e3975f1e98c64a1c77f509 | e1d92e085df142d703ed9fd9c65ed92562a759fa | 18f24841651461bd84a5eac08be9bce9eab54b133b0e837d5298dac44e199d5f |
| eb8385915f68d5fbbf7c0c05e480a999 | a72734fcddbad58308d91274ad444a5b1d970c21 | 7d7d9a9df8b8ffd0a0c652a3d41b9a5352efb19424e42942aaf26196c9698019 |
| 22840909e11530390e8f74c6a162ded1 | 78d82f0ff396393e958553f25a47145916ea4e39 | 9a72e56ac0f1badd3ca761b53e9998a7e0525f2055dbec01d867f62bdb30418e |
| 577df0d0d1ebfde0c67cf6489d9a1974 | a57a31db630fd55666cfd3ccdacf78cec8fabc43 | 4fdc37f59801976606849882095992efecee0931ece77d74015113123643796e |
| 22cb7775c867ac98f7c4b1266e3534b4 | 55b6a0512a9da7f7e854cb5155708e3f7fc34d7a | 7eb1dc1719f0918828cc8349ee56ca5e6bbde7cada3bc67a11d7ff7f420c7871 |
| 1e2e2b8f1c81c01bac895e113f7a4846 | 3bcf40b51363e2e69aacea81f700bd246fa99882 | c532d19652ea6d4e0ebb509766de1ec594dd80152f92f7ef6b80ad29d2aa8cf4 |
| 9e2b456c62b027c89b36dc9109e50f01 | 617fddb80de29bc455c0ecfd4b64d194fe911541 | e9a858127f5f6e5e0e94ed655a2bf9ed228f87bc99d9b12113e27dcc84be3909 |
| 61a3d983a1fde813204b8f6f13842163 | 336a3a59b782b49c2253bd0afeefdb43b24f70b6 | 7963f8606e4c0e7502a813969a04e1266e7cd20708bef19c338e8933c1b85eda |
| f5de326683df44d71ed1b986fd836e0b | 33bc899da6afd2b82b27d59acd0844b521e57079 | 17c3cf5742d2a0995afb4dd2a2d711abe5de346abde49cf4cf5b82c14e0a155f |
| 268c62a4b45d08a0639ead11b2feebd8 | c1d9237230acc994067fdc1d6502b6a84afd1b9a | cb6c05b2e9d8e3c384b7eabacde32fc3ac2f9663c63b9908e876712582bf2293 |
| 2d9702caab94b9c7788443c13b1b1ce1 | 08cef1c0cc4942221a5304ad0a680324a2f0f39a | 0f7a8611deea696b2b36e44ea652c8979e296b623e841796a4ea4b6916b39e7c |
| 12ed130045b2e731bc66c9261c88efaa | df697bee43eb208144496ad3ab56a02c92d3b69a | B258a747202b1ea80421f8c841c57438ffb0670299f067dfeb2c53ab50ff6ded |
| 65792e4d02f910d20dcf74487cb9fab1 | 942337f3ea28f553b47dc05726bb062befe09fef | 9fbeb629ea0dc72ac8db680855984d51b28c1195e48abff2e68b0228f49d5b0f |
| 08982381ef296038ae7ad8d083ef8ca8 | 8cf1d9dbd5d41dd9481249a1d5b1d930afa083d3 | d0aad99f10bdd6f6af2f7a0f6c319ed7d126de4d1ff44ca86858e7ffc17cc39b |
| df32b34cc480934ca2ac0895863dd030 | e0256ff9efa8fca3813924d7ac556ddc44dc08b1 | 5fd4e486bd7e12454f67ba8fcdaa9afc88b4d1c29705b0cffc9d32000700d314 |
| a89521c26b2c660d41101ca0a6100cd3 | 75c8cf7b14ea7bb8557efd80170a1df1c89d9797 | 6f3994ad6b418b55ba2a3cd4f4d8cff35284a5790ea3dd38f1abf8699410430a |
| 65501683cfe1e0af1ff7463de684a2fe | fa7887bc9d48fcfc6fd0e774092ca711ae28993a | 61da1819361c095f802ce2151092df02531eeeb713e7db07100a9a80874d902a |
| 079766094541035de5f115a9bbb4f583 | 8423b25054aa78535c49042295558f33d34deae1 | 6434913278186cb5b12ca38580a4e94b2ce2af83a836f7e50ab9c5ea8e265a59 |
| d8434e637305cfc941744807698c846a | 0de3fce5c10b9122335866f5c1a817ed8a6d4269 | a98e108588e31f40cdaeab1c04d0a394eb35a2e151f95fbf8a913cba6a7faa63 |
| d2efb0b8b82576016416aacbde6c3873 | 19cac454edb76d7e879598d8c7e8e032f9d006d2 | a4b705baac8bb2c0d2bc111eae9735fb8586d6d1dab050f3c89fb12589470969 |
| f690fa242d8200f27e71e11d469b584d | f14f8a0ee542b6db79c52266450c5fe0412a0d62 | 2d88db4098a72cd9cb58a760e6a019f6e1587b7b03d4f074c979e776ce110403 |
| 4d01975268c215fc26ed79ebd17ec22d | 64c6752af3632f6f49fd6db091182e753e5d9f80 | 992df82cf31a91acd034411bb43a1ec127fa15d613b108287384882807f81764 |
| cd8915c63f3134425aa7c851f5f1e645 | 3ba578e4396145b18747c914fed9d6c8f027fe2c | 0f9f31bbc69c8174b492cf177c2fbaf627fcdb5ac4473ca5589aa2be75cee735 |
| ccc3750d9270d1e8c95649d91f94033b | 058f0190a58646ab1a6295eed496732e1e3f7cbf | 29decd1e88b297aa67fef6e14e39889cfd2454c581b9371a1003b63a28324d0f |
| af9a60ea728985f492119ebf713e0716 | 4fecd1895b6f7ff41b8b0dee700b5f194743b36a | 9d7c3463d4a4f4390313c214c7a79042b4525ae639e151b5ec8a560b0dd5bd0a |
| 5d5c99a08a7d927346ca2dafa7973fc1 | 189166d382c73c242ba45889d57980548d4ba37e | a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92 |
| 14c8482f302b5e81e3fa1b18a509289d | 16525cb2fd86dce842107eb1ba6174b23f188537 | dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78 |
| e61518ae9454a563b8f842286bbdb87b | 82d29b52e35e7938e7ee610c04ea9daaf5e08e90 | 9ef7dbd3da51332a78eff19146d21c82957821e464e8133e9594a07d716d892d |
| 3907c7fbd4148395284d8e6e3c1dba5d | a67205dc84ec29eb71bb259b19c1a1783865c0fc | 34CA75A8C190F20B8A7596AFEB255F2228CB2467BD210B2637965B61AC7EA907 |
| e61518ae9454a563b8f842286bbdb87b | 82d29b52e35e7938e7ee610c04ea9daaf5e08e90 | 9ef7dbd3da51332a78eff19146d21c82957821e464e8133e9594a07d716d892d |
| ee47d6ae8414f6c6ca28a3b76bf75e44 | a983bd69a71322d64199e67f2abcfe5ef0e1bca7 | 9cdaacaba35c3a473ec5b652d035a9593ee822609e79662223869e2b7298dc0a |
| ba45247858c0739865a52996768b7485 | aff0b6eab23bbf4e5cb94fd4292c6d961dee060e | 00bc665d96ecadc6beb2a9384773a70391f08f8e7a2876253f32ceec793eb728 |
| 6f93fd91f17130aabd5251e7bae3eeaa | 2af6e61d203191b4b8df982f37048937a1f9696c | ff3b45ecfbbdb780b48b4c829d2b6078d8f7673d823bedbd6321699770fa3f84 |
| 14c8482f302b5e81e3fa1b18a509289d | 16525cb2fd86dce842107eb1ba6174b23f188537 | dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78 |
| 56af47c87029b9fba5fe7c81e99cedca | ea65565404ffde218ebccaeaca00ac1a2937dc57 | 35ab54a9502e975c996cbaee3d6a690da753b4af28808d3be2054f8a58e5c7c5 |
| 5d5c99a08a7d927346ca2dafa7973fc1 | 189166d382c73c242ba45889d57980548d4ba37e | a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92 |
| db600240aecf9c6d75c733de57f252bf | 8756712e2c73ee3f92ded3852e41a486be3de6e2 | bbe1949ffd9188f5ad316c6f07ef4ec18ba00e375c0e6c2a6d348a2a0ab1e423 |