
DNS Under Siege: The Covert Campaign Hijacking Thousands of Domains
The "Sitting Ducks" campaign exploits DNS vulnerabilities to hijack over 35,000 domains without accessing owner accounts. It targets domains with weak verification processes and misconfigured authoritative name servers or different DNS providers. Russian cybercriminals primarily use these hijacked domains for phishing, malware distribution, and data theft.
| Domains | Source | Last Update |
|---|
| Hashes | Source | Last Update |
|---|
| Ipv4s | Source | Last Update |
|---|---|---|
| 81.19.135.241 | SOCRadar | 2024-08-28 |
| 178.250.243.30 | SOCRadar | 2024-08-27 |
| 45.136.49.35 | SOCRadar | 2024-08-27 |
| Cves | Source | Last Update |
|---|
| Emails | Source | Last Update |
|---|
| Domains | Insert Date |
|---|
MITIGATION
T1078-Valid Accounts
T1547-Boot or Logon Autostart Execution
This type of attack technique cannot be easily mitigated with preventive controls since it is based on the abuse of system features.
T1071-Application Layer Protocol
REMEDIATION
T1078-Valid Accounts
T1547-Boot or Logon Autostart Execution
T1071-Application Layer Protocol
CONCLUSION
The "Sitting Ducks" campaign has underscored critical vulnerabilities within the Domain Name System (DNS), resulting in the hijacking of over 35,000 domains. This campaign exploits inadequacies in domain ownership verification processes and improper DNS configurations, allowing attackers to assume control without needing access to the owner's account. Consequently, hijacked domains are repurposed for phishing, malware dissemination, and data exfiltration, predominantly by Russian cybercriminal entities.
The persistence and sophistication of the "Sitting Ducks" campaign highlight the urgent need for strengthened DNS security measures. Exploiting DNS infrastructure vulnerabilities, attackers have managed to execute extensive operations with significant impact. Therefore, it is imperative to implement robust security protocols and continually monitor DNS configurations to mitigate such risks
Organizations and domain owners must undertake proactive measures, including routine DNS audits, the deployment of multi-factor authentication, and ensuring the accurate configuration of DNS records. Moreover, leveraging advanced threat intelligence and monitoring tools can facilitate early detection and response to these threats.
For enhanced protection and comprehensive oversight of potential attack surfaces, users and members are encouraged to adopt SOCRadar's Attack Surface Management (ASM) Tool. This tool offers real-time monitoring and alerts, thus bolstering defenses against domain hijacking and other cyber threats, ensuring a robust security posture against sophisticated campaigns like "Sitting Ducks".
| File Name | Description | Actions |
|---|
| APT Name | Aliases | Target Countries | Source Countries | Total IOCs |
|---|
In our previous Kenwood DMX958XR blog post, we detailed the internals of the Kenwood in-vehicle infotainment (IVI) head unit and provided annotated pictures of each PCB. In this post, we aim to outline the attack surface of the DMX958XR in the hopes of providing inspiration for vulnerability research.
We will cover the main supported technologies that present potential attack surfaces, such as USB, Bluetooth, Android Auto, Apple CarPlay, Kenwood apps, and more. We also provide a list of the open-source components the DMX958XR claims to use.
All information has been obtained through reverse engineering, experimenting, and combing through the following resources:
· Kenwood DMX958XR Product Page
· Kenwood DMX958XR Instruction Manual [PDF]
· Kenwood DMX958XR Quick Start Guide [PDF]
· Kenwood Portal App
· Kenwood Remote S App
USB
The DMX958XR is equipped with a single USB-C port that operates at USB 2.0 speeds and provides the necessary interface for wired Android Auto and Apple CarPlay. The USB port also supports playback of audio files from a USB flash drive. The supported audio filetypes and their associated extensions are:
· MP3 (.mp3)
· WMA (.wma)
· AAC-LC (.m4a)
· WAV (.wav)
· FLAC (.flac, .fla)
· Vorbis (.ogg)
Beyond just audio, a USB flash drive can also be used to play back video files. The supported video file types and their associated extensions are:
· MPEG-1 (.mpg, .mpeg)
· MPEG-2 (.mpg, .mpeg)
· H.264 / MPEG-4 (.mp4, .m4v, .avi, .flv, .f4v)
· WMV (.wmv)
· MKV (.mkv)
Robustly parsing and decoding these file formats is notoriously complicated and error-prone, which makes for a potentially rewarding attack surface. USB flash drives must be formatted as either FAT16, FAT32, exFAT, or NTFS for the head unit to be able to read them.
Bluetooth
Bluetooth version 5 is supported by the head unit and is used for making phone calls, receiving calls, and playing audio from a paired mobile phone. The following Bluetooth profiles are implemented:
· Hands-Free Profile v1.7
· Serial Port Profile
· Phonebook Access Profile
· Audio/Video Remote Control Profile (AVRCP) v1.6
· Advanced Audio Distribution Profile (A2DP)
· Supporting codecs: SBC, AAC or LDAC
Android Auto, Apple CarPlay, and the Kenwood apps all utilize Bluetooth in varying capacities.
Wi-Fi
The head unit provides a Wi-Fi access point, which is primarily used for wireless Android Auto and Apple CarPlay. There is no intention for the end user to directly connect to this access point, and there is no officially documented way of acquiring the password. However, internal research has discovered multiple methods to obtain the password. Once connected to the access point the following ports are listening:
· TCP: 7000, 8086
· UDP: 67, 5353, 35917, 50002, 60794
The two TCP ports and UDP port 50002 are of particular interest since they are running non-standard services.
Android Auto and Apple CarPlay
Both wired and wireless Android Auto and Apple CarPlay are supported without the need for a third-party application to be installed on the paired mobile phone. When using the wireless versions, the paired phone connects to the aforementioned Wi-Fi network to establish a high-bandwidth channel for data to be sent and received. When connecting using a USB cable, the Wi-Fi network isn't used by Android Auto or Apple CarPlay, but it is still active.
Pwn2Own Automotive 2024 didn’t see any entries that leveraged Android Auto or Apple CarPlay functionality to compromise a head unit. We will have to wait and see if Pwn2Own Automotive 2025 does!
Kenwood Apps
Kenwood offers two Android/iOS apps to interface with the DMX958XR. The first app is the Kenwood Portal App, which allows users to transfer photos from a mobile phone to the head unit over Bluetooth. The transferred photos can then be viewed as a slideshow on the head unit or be used as wallpaper.
This presents an interesting attack surface – especially if the DMX958XR itself performs any complex image handling tasks on the received images, such as resizing or converting between different image formats. The user-supplied images also need to be persisted in the head unit's filesystem, further expanding the attack surface.
The second app is the Kenwood Remote S app, which connects to the head unit over Bluetooth and allows for multimedia control, such as selecting a radio station, skipping a track, and more. The Bluetooth Audio/Video Remote Control Profile (AVRCP) is designed for this task. However, no research was performed to confirm if the Remote S app takes advantage of AVRCP. There are a few other Kenwood apps available, but they are not listed as supported on the DMX958XR product page and therefore have not been explored.
Open Source Software
A list of open-source licenses can be viewed from the head unit by navigating to Menu -> Settings -> Special -> Open Source Licenses. There is no guarantee these open-source projects are actually used, but a complete list of the projects is provided at the end of this blog post. Where available, the versions of the projects have also been included.
Summary
We hope that this blog post has provided enough information about the DMX958XR attack surface to guide vulnerability research. Not every attack surface has been mentioned and we encourage researchers to investigate further. The next post in this series will cover details of the DMX958XR firmware.
We are looking forward to Automotive Pwn2Own, again to be held in January 2025 at the Automotive World conference in Tokyo. We will see if IVI vendors have improved their product security. Don’t wait until the last minute to ask questions or register! We hope to see you there.
You can find me on Twitter at @ByteInsight, and follow the team on Twitter, Mastodon, LinkedIn, or Bluesky for the latest in exploit techniques and security patches.
Open Source Software List
Below is a complete list of all the open-source software the head unit claims to use:
· OpenSSL (2011)
· SSLeay (1998)
· ALSA
· BusyBox
· Cairo
· D-Bus
· dnsmasq (2014)
· e2fsprogs (2007)
· Freeware Advanced Audio Coder v1.36 (2009)
· flac (2014)
· fontconfig (2012)
· GLIB (1997)
· bashline (1993)
· iconv (2011)
· GNU MP (2007)
· GNU readline (2005)
· GNU tar (2006)
· gstreamer (2000)
· GdkPixbuf (1999)
· GnuTLS (2012)
· HarfBuzz (2012)
· ICU (2015)
· ImageMagick (2016)
· iperf (2007)
· libpng (2019)
· libusb (2015)
· xiph (2015)
· libxml2 (2012)
· libxslt (2002)
· Naver fonts (2007)
· GIO (2010)
· OpenSSH
· OpenSSL (2011)
· PCI Utilities v3.3.1 (2015)
· Qt (2013)
· Bluetooth SBC library (2013)
· Sysvinit (2004)
· Info-ZIP (2007)
· bzip2 v1.0.6 (2010)
· cURL (2015)
· dpkg (1995)
· libffi (2014)
· libjpeg v9a (2014)
· XFree86 (2000)
· libproxy (2006)
· libX11 (2006)
· soup-cache (2010)
· nettle (2002)
· libdpkg (1995)
· pango (1999)
· sysctl v1.0.1 (1999)
· alloc (2002)
· pslash (2006)
· tslib (2001)
· libudev (2011)
· usbmisc (2003)
· zlib v1.2.8
· s-bios (2011)
· devmem2 (2000)
· hostapd (2015)
· hidapi (2010)
· wpa-supplicant (2015)
· OpenMax (2008)
· oRTP (2015)
· unzip v1.1 (2010)
· hts_engine (2011)
· google-breakpad (2006)
· boost v1.0 (2003)
· SQLite (2001)
· PCRE (2019)
· OpenGL (2012)
· base64 (2001)
· mDNSResponder
· RapidJSON (2015)
· crc32 (2005)
· zconf (2005)
domain-protect scan Amazon Route53 across an AWS Organization for domain records vulnerable to takeover scan Cloudflare for vulnerable DNS records take over vulnerable subdomains yourself before attackers and bug bounty researchers automatically create known issues in Bugcrowd or HackerOne...
The post domain-protect: prevent subdomain takeover appeared first on Penetration Testing Tools.
Above Invisible protocol sniffer for finding vulnerabilities in the network. Designed for pentesters and security professionals. Mechanics Above is an invisible network sniffer for finding vulnerabilities in network equipment. It is based entirely on...
The post Above: Invisible protocol sniffer for finding vulnerabilities in the network appeared first on Penetration Testing Tools.
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent advisory regarding three critical vulnerabilities affecting Apple and Oracle products. These flaws, identified as CVE-2024-44308, CVE-2024-44309, and CVE-2024-21287, have the potential to be exploited in the wild, posing significant cybersecurity risks to organizations and individuals. CVE-2024-44308: Apple Code Execution Vulnerability The vulnerability, CVE-2024-44308, affects […]
The post CISA Warns of Apple & Oracle Agile Vulnerabilities Exploited in Wild appeared first on Cyber Security News.
As companies bolster defenses, cybercriminals turn attention to consumers.
A China-linked nation-state group called TAG-112 compromised Tibetan media and university websites in a new cyber espionage campaign designed to facilitate the delivery of the Cobalt Strike post-exploitation toolkit for follow-on information collection. “The attackers embedded malicious JavaScript in these sites, which spoofed a TLS certificate error to trick visitors into downloading a disguised security […]
The post China-Linked TAG-112 Targets Tibetan Media with Cobalt Strike Espionage Campaign appeared first on All Hacker News.
DoJ charges RaaS admin and extortionists, NodeStealer harvests data via Facebook, and DPRK front companies linked to active network in China.
A vulnerability, which was classified as problematic, was found in Avahi. This affects an unknown part of the component DNS Response Handler. The manipulation leads to injection. This vulnerability is uniquely identified as CVE-2024-52615. It is possible to initiate the attack remotely. There is no exploit available. It is recommended to apply a patch to fix this issue.
A vulnerability has been found in Avahi and classified as problematic. This vulnerability affects unknown code of the component DNS Transaction ID Handler. The manipulation leads to improper initialization. This vulnerability was named CVE-2024-52616. The attack can only be initiated within the local network. There is no exploit available. It is recommended to apply a patch to fix this issue.
Executive Summary
The Cybersecurity and Infrastructure Security Agency (CISA) conducted a red team assessment (RTA) at the request of a critical infrastructure organization. During RTAs, CISA’s red team simulates real-world malicious cyber operations to assess an organization’s cybersecurity detection and response capabilities. In coordination with the assessed organization, CISA is releasing this Cybersecurity Advisory to detail the red team’s activity—including their tactics, techniques, and procedures (TTPs) and associated network defense activity. Additionally, the advisory contains lessons learned and key findings from the assessment to provide recommendations to network defenders and software manufacturers for improving their organizations’ and customers’ cybersecurity posture.
Within this assessment, the red team (also referred to as ‘the team’) gained initial access through a web shell left from a third party’s previous security assessment. The red team proceeded to move through the demilitarized zone (DMZ) and into the network to fully compromise the organization’s domain and several sensitive business system (SBS) targets. The assessed organization discovered evidence of the red team’s initial activity but failed to act promptly regarding the malicious network traffic through its DMZ or challenge much of the red team’s presence in the organization’s Windows environment.
The red team was able to compromise the domain and SBSs of the organization as it lacked sufficient controls to detect and respond to their activities. The red team’s findings illuminate lessons learned for network defenders and software manufacturers about how to respond to and reduce risk.
- Lesson Learned: The assessed organization had insufficient technical controls to prevent and detect malicious activity. The organization relied too heavily on host-based endpoint detection and response (EDR) solutions and did not implement sufficient network layer protections.
- Lesson Learned: The organization’s staff require continuous training, support, and resources to implement secure software configurations and detect malicious activity. Staff need to continuously enhance their technical competency, gain additional institutional knowledge of their systems, and ensure they are provided sufficient resources by management to have the conditions to succeed in protecting their networks.
- Lesson Learned: The organization’s leadership minimized the business risk of known attack vectors for the organization. Leadership deprioritized the treatment of a vulnerability their own cybersecurity team identified, and in their risk-based decision-making, miscalculated the potential impact and likelihood of its exploitation.
To reduce risk of similar malicious cyber activity, CISA encourages critical infrastructure organizations to apply the recommendations in the Mitigations section of this advisory to ensure security processes and procedures are up to date, effective, and enable timely detection and mitigation of malicious activity.
This document illustrates the outsized burden and costs of compensating for insecure software and hardware borne by critical infrastructure owners and operators. The expectation that owners and operators should maintain the requisite sophisticated cyber defense skills creates undue risk. Technology manufacturers must assume responsibility for product security. Recognizing that insecure software contributes to these identified issues, CISA urges software manufacturers to embrace Secure by Design principles and implement the recommendations in the Mitigations section of this advisory, including those listed below:
- Embed security into product architecture throughout the entire software development lifecycle (SDLC).
- Eliminate default passwords.
- Mandate MFA, ideally phishing-resistant MFA, for privileged users and make MFA a default, rather than opt-in, feature.
Download the PDF version of this report:
INTRODUCTION
CISA has authority to—upon request—provide analyses, expertise, and other technical assistance to critical infrastructure owners and operators and provide operational and timely technical assistance to federal and non-federal entities with respect to cybersecurity risks. (See generally 6 U.S.C. §§ 652[c][5], 659[c][6]). The target organization for this assessment was a critical infrastructure organization in the United States. After receiving a request for an RTA from the organization and coordinating the high-level details of the engagement, CISA conducted the RTA over approximately a three-month period.
During RTAs, a CISA red team simulates real-world threat actors to assess an organization’s cybersecurity detection and response capabilities. During Phase I, the red team attempts to gain and maintain persistent access to an organization’s enterprise network, avoid detection, evade defenses, and access SBSs. During Phase II, the red team attempts to trigger a security response from the organization’s people, processes, and/or technology.
Drafted in coordination with the assessed organization, this advisory details the red team’s activity and TTPs, associated network defense activity, and lessons learned to provide network defenders with recommendations for improving an organization’s cybersecurity posture. The advisory also provides recommendations for software manufacturers to harden their customer networks against malicious activity and reduce the likelihood of domain compromise.
TECHNICAL DETAILS
Note: This advisory uses the MITRE ATT&CK® Matrix for Enterprise framework, version 16. See Appendix: MITRE ATT&CK Tactics and Techniques for a table of the red team’s activity mapped to MITRE ATT&CK tactics and techniques.
Phase I: Red Team Cyber Threat Activity
Overview
The CISA red team operated without prior knowledge of the organization’s technology assets and began the assessment by conducting open source research on the target organization to gain information about its network [T1590], defensive tools [T1590.006], and employees [T1589.003]. The red team designed spearphishing campaigns [T1566] tailored to employees most likely to communicate with external parties. The phishing attempts were ultimately unsuccessful—targets ran the payloads [T1204], but their execution did not result in the red team gaining access into the network.
After the failed spearphishing campaigns, the red team continued external reconnaissance of the network [T1595] and discovered a web shell [T1505.003] left from a previous Vulnerability Disclosure Program (VDP). The red team used this for initial access [TA0001] and immediately reported it to the organization’s trusted agents (TAs). The red team leveraged that access to escalate privileges [TA0004] on the host, discover credential material on a misconfigured Network File System (NFS) share [T1552.001], and move from a DMZ to the internal network [TA0008].
With access to the internal network, the red team gained further access to several SBSs. The red team leveraged a certificate for client authentication [T1649] they discovered on the NFS share to compromise a system configured for Unconstrained Delegation. This allowed the red team to acquire a ticket granting ticket (TGT) for a domain controller [T1558.001], used to further compromise the domain. The red team leveraged this level of access to exploit SBS targets provided by the organization’s TAs.
The assessed organization detected much of the red team’s activity in their Linux infrastructure after CISA alerted them via other channels to the vulnerability the red team used for initial access. Once given an official notification of a vulnerability, the organization’s network defenders began mitigating the vulnerability. Network defenders removed the site hosting the web shell from the public internet but did not take the server itself offline. A week later, network defenders officially declared an incident once they determined the web shell was used to breach the internal network. For several weeks, network defenders terminated much of the red team’s access until the team maintained implants on only four hosts. Network defenders successfully delayed the red team from accessing many SBSs that required additional positioning, forcing the red team to spend time refortifying their access in the network. Despite these actions, the red team was still able to access a subset of SBSs. Eventually, the red team and TAs decided that the network defenders would stand down to allow the red team to continue its operations in a monitoring mode. In monitoring mode, network defenders would report what they observed of the red team’s access, but not continue to block and terminate it.
See Figure 1 for a timeline of the red team’s activity with key points access. See the following sections for additional details, including the red team’s TTPs.
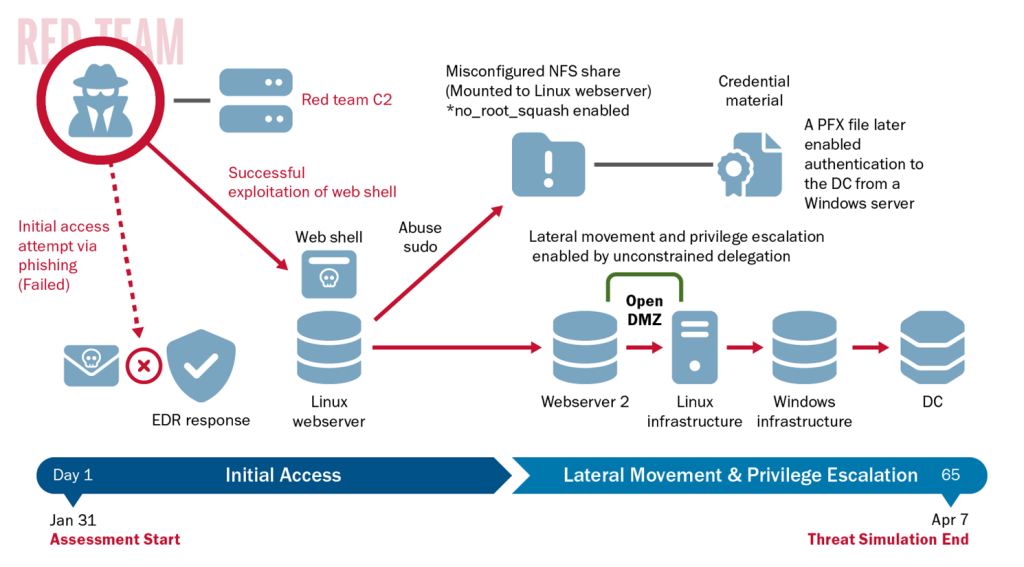
Initial Access
Following an unsuccessful spearphishing campaign, the red team gained initial access to the target by exploiting an internet-facing Linux web server [T1190] discovered through reconnaissance [TA0043] of the organization’s external internet protocol (IP) space [T1590.005].
The red team first conducted open source research [T1593] to identify information about the organization’s network, including the tools used to protect the network and potential targets for spearphishing. The red team looked for email addresses [T1589.002] and names to infer email addresses from the organization’s email syntax (discovered during reconnaissance). Following this action, the red team sent tailored spearphishing emails to 13 targets [T1566.002]. Of these 13 targets, one user responded and executed two malicious payloads [T1204.002]. However, the payloads failed to bypass a previously undiscovered technical control employed by the victim organization, preventing the red team’s first attempt to gain initial access.
To find an alternate pathway for initial access, the red team conducted reconnaissance with several publicly available tools, such as Shodan and Censys, to discover accessible devices and services on the internet [T1596.005]. The red team identified an old and unpatched service with a known XML External Entity (XXE) vulnerability and leveraged a public proof of concept to deploy a web shell. The associated product had an exposed endpoint—one that system administrators should typically block from the public internet—that allowed the red team to discover a preexisting web shell on the organization’s Linux web server. The preexisting web shell allowed the red team to run arbitrary commands on the server [T1059] as a user (WEBUSER1). Using the web shell, the red team identified an open internal proxy server [T1016] to send outbound communications to the internet via Hypertext Transfer Protocol Secure (HTTPS). The red team then downloaded [T1105] and executed a Sliver payload that utilized this proxy to establish command and control (C2) over this host, calling back to their infrastructure [TA0011].
Note: Because the web shell and unpatched vulnerability allowed actors to easily gain initial access to the organization, the CISA red team determined this was a critical vulnerability. CISA reported both the vulnerability and the web shell to the organization in an official vulnerability notification so the organization could remediate both issues. Following this notification, the victim organization initiated threat hunting activities, detecting some of the red team’s activity. The TAs determined that network defenders had previously identified and reported the vulnerability but did not remediate it. Further, the TAs found that network defenders were unaware of the web shell and believed it was likely leftover from prior VDP activity. See the Defense Evasion and Victim Network Defense Activities section for more information.
Linux Infrastructure Compromise
Local Privilege Escalation and Credential Access
The red team then moved laterally from the web server to the organization’s internal network using valid accounts [T1078] as the DMZ was not properly segmented from the organization’s internal domain.
The red team acquired credentials [TA0006] by first escalating privileges on the web server. The team discovered that WEBUSER1 had excessive sudo rights, allowing them to run some commands as root commands without a password. They used these elevated rights to deploy a new callback with root access [T1548.003].
With root access to the web server, the team had full access to the organization’s directories and files on a NFS share with no_root_squash enabled. If no_root_squash is used, remote root users can read and change any file on the shared file system and leave a trojan horse [T1080] for other users to inadvertently execute. On Linux operating systems this option is disabled by default, yet the organization enabled it to accommodate several legacy systems. The organization’s decision to enable the no_root_squash option allowed the red team to read all the files on the NFS share once it escalated its privileges on a single host with the NFS share mounted. This NFS share hosted the home directories of hundreds of Linux users—many of which had privileged access to one or more servers—and was auto-mounted when those users logged into Linux hosts in the environment.
The red team used its escalated privileges to search for private certificate files, Secure Shell (SSH) private keys, passwords, bash command histories [T1552.003], and other sensitive data across all user files on the NFS share [T1039]. The team initially obtained 61 private SSH keys [T1552.004] and a file containing valid cleartext domain credentials (DOMAINUSER1) that the team used to authenticate to the organization’s domain [T1078.002].
Linux Command and Control
In the organization’s Linux environment, the red team leveraged HTTPS connections for C2 [T1071.001]. Most of the Linux systems could not directly access the internet, but the red team circumvented this by leveraging an open internal HTTPS proxy [T1090.001] for their traffic.
Lateral Movement and Persistence
The red team’s acquisition of SSH private keys generated for user and service accounts facilitated unrestricted lateral movement to other Linux hosts [T1021.004]. This acquisition included two highly privileged accounts with root access to hundreds of servers. Within one week of initial access, the team moved to multiple Linux servers and established persistence [TA0003] on four. The team used a different persistence mechanism on each Linux host, so network defenders would be less likely to discover the red team’s presence on all four hosts. The team temporarily backdoored several scripts run at boot time to maintain persistence [T1037], ensuring the original versions of the scripts were re-enabled once the team successfully achieved persistence. Some of the team’s techniques included modifying preexisting scripts run by the cron utility [T1053.003] and ifup-post scripts [T1037.003].
Of note, the team gained root access to an SBS-adjacent infrastructure management server that ran Ansible Tower. Access to this Ansible Tower system [T1072] provided easy access to multiple SBSs. The team discovered a root SSH private key on the host, which allowed the team to move to six SBSs across six different sensitive IP ranges. A week after the team provided screenshots of root access to the SBSs to the TAs, the TAs deconflicted the red team’s access to the Ansible Tower system that network defenders discovered. The organization detected the compromise by observing abnormal usage of the root SSH private key. The root SSH private key was used to log into multiple hosts at times and for durations outside of preestablished baselines. In a real compromise, the organization would have had to shut down the server, significantly impacting business operations.
Windows Domain Controller Compromise
Approximately two weeks after gaining initial access, the red team compromised a Windows domain controller. This compromise allowed the team to move laterally to all domain-joined Windows hosts within the organization.
To first gain situational awareness about the organization’s environment, the red team exfiltrated Active Directory (AD) information [TA0010] from a compromised Linux host that had network access to a Domain Controller (DC). The team queried Lightweight Directory Access Protocol (Over SSL)—(LDAPS)—to collect information about users [T1087.002], computers [T1018], groups [T1069.002], access control lists (ACL), organizational units (OU), and group policy objects (GPO) [T1615]. Unfortunately, the organization did not have detections to monitor for anomalous LDAP traffic. A non-privileged user querying LDAP from the organization’s Linux domain should have alerted network defenders.
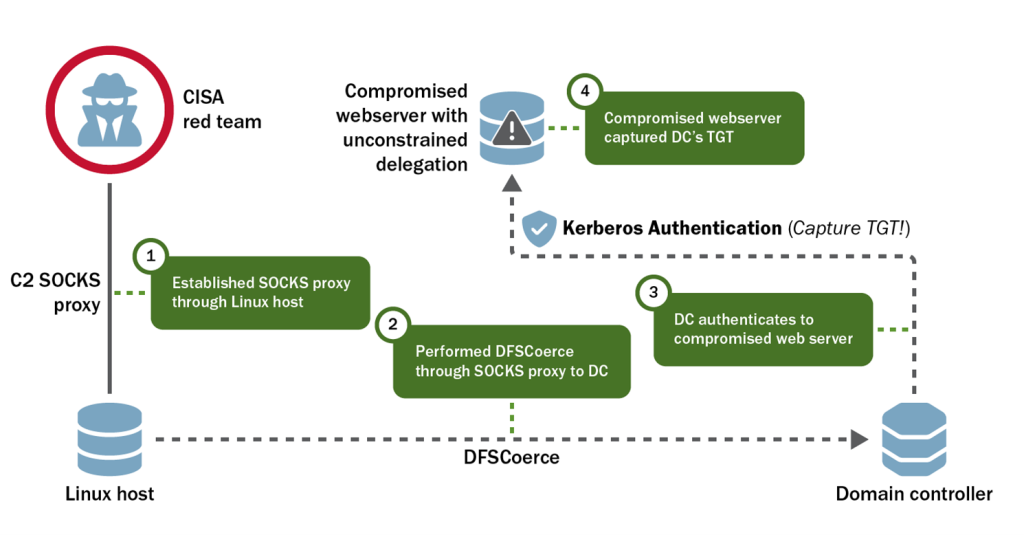
The red team observed a total of 42 hosts in AD that were not DCs, but had Unconstrained Delegation enabled. Hosts with Unconstrained Delegation enabled store the Kerberos TGTs of any user that authenticates to them. With sufficient privileges, an actor can obtain those tickets and impersonate associated users. A compromise of any of these hosts could lead to the escalation of privileges within the domain. Network defenders should work with system administrators to determine whether Unconstrained Delegation is necessary for their systems and limit the number of systems with Unconstrained Delegation unnecessarily enabled.
The red team observed insufficient network segmentation between the organization’s Linux and Windows domains. This allowed for Server Message Block (SMB) and Kerberos traffic to a DC and a domain server with Unconstrained Delegation enabled (UDHOST). The team discovered an unprotected Personal Information Exchange (.pfx) file on the NFS home share that they believed was for UDHOST based on its naming convention.
Equipped with the .pfx file, the red team used Rubeus—an open source toolset for Kerberos interaction and abuses—to acquire a TGT and New Technology Local Area Network Manager (NTLM) hash for UDHOST from the DC. The team then used the TGT to abuse the Server-for-User-to-Self (S4U2Self) Kerberos extension to gain administrative access to UDHOST.
The red team leveraged this administrative access to upload a modified version of Rubeus in monitor mode to capture incoming tickets [T1040] on UDHOST with Rubeus’ /monitor command. Next, the team ran DFSCoerce.py to force the domain controller to authenticate to UDHOST [T1187]. The team then downloaded the captured tickets from UDHOST.
With the DC’s TGT, the team used Domain Controller Sync (DCSync) through their Linux tunnels to acquire the hash of several privileged accounts—including domain, enterprise, and server administrators—and the critical krbtgt account [T1003.006].
Gaining access to AD is not unusual for most of CISA’s Red Team engagements, but it is rare to find network defenders who can secure and monitor it quickly and effectively.
Once the team harvested the credentials needed, they moved laterally to nearly any system in the Windows domain (see Figure 2) through the following steps (hereafter, this combination of techniques is referred to as the “Preferred Lateral Movement Technique”):
- The team either forged a golden ticket using the
krbtgthash or requested a valid TGT using the hashes they exfiltrated for a specific account before loading the ticket into their session for additional authentication. - The team dropped an inflated Dynamic Link Library (DLL) file associated with legitimate scheduled tasks on the organization’s domain.
- When the scheduled task executed on its own or through the red team’s prompting, the DLL hijack launched a C2 implant.
Windows Command and Control
The red team initially established C2 on a workstation over HTTPS before connecting to servers over SMB [T1071.002] in the organization’s Windows environment. To connect to certain SBSs later in its activity, the team again relied on HTTPS for C2.
Post-Exploitation Activity: Gaining Access to SBSs
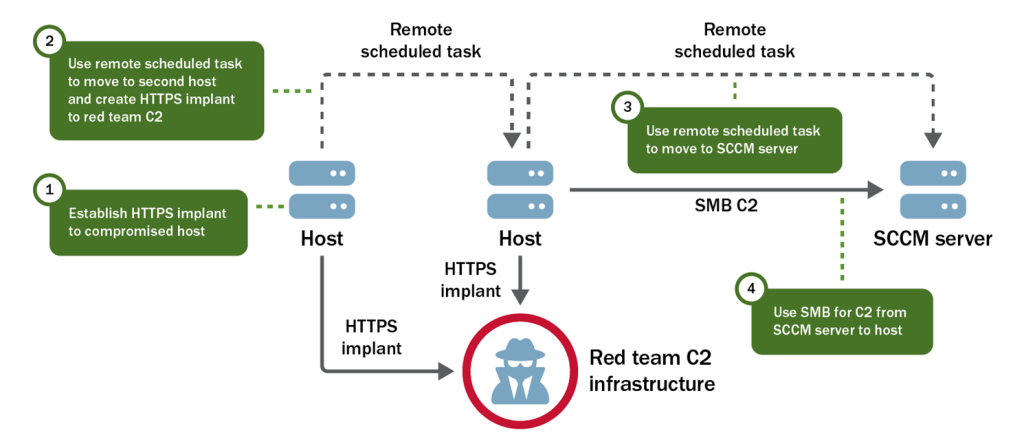
After the red team gained persistent access to Linux and Windows systems across the organization’s networks, the team began post-exploitation activities and attempted to access SBSs. The TAs provided a scope of the organization’s Classless Inter-Domain Routing (CIDR) ranges that contained SBSs. The team gained root access to multiple Linux servers in these ranges. The TAs then instructed the red team to exploit its list of primary targets: admin workstations and network ranges that included OT networks. The team only achieved access to the first two targets and did not find a path to the OT networks. While the team was able to affect the integrity of data derived from OT devices and applications, it was unable to find and access the organization’s internal network where the OT devices resided.
To gain access to the SBSs, the team first gained access to Microsoft System Center Configuration Manager (SCCM) servers, which managed most of the domain’s Windows systems. To access the SCCM servers, the team leveraged their AD data to identify administrators [T1087] of these targets. One of the users they previously acquired credentials for via DCSync was an administrator on the SCCM servers. The red team then used the Preferred Lateral Movement Technique to eventually authenticate to the SCCM servers. See Figure 3.
Admin Workstations
The first specific set of SBS targets provided by the TAs were admin workstations. These systems are used across various sensitive networks external to, or inaccessible from, the internal network where the team already had access. Normally, authorized personnel leverage these administrator workstations to perform administrator functions. CISA’s red team targeted these systems in the hopes that an authorized—but unwitting—user would move the tainted system to another network, resulting in a callback from the sensitive target network.
The red team reviewed AD data to identify these administrator systems. Through their review, the team discovered a subset of Windows workstations that could be identified with a prefix and determined a group likely to have administrative rights to the workstations.
With access to the SCCM server, the red team utilized their Preferred Lateral Movement Technique to gain access to each admin workstation target (see Figure 4).
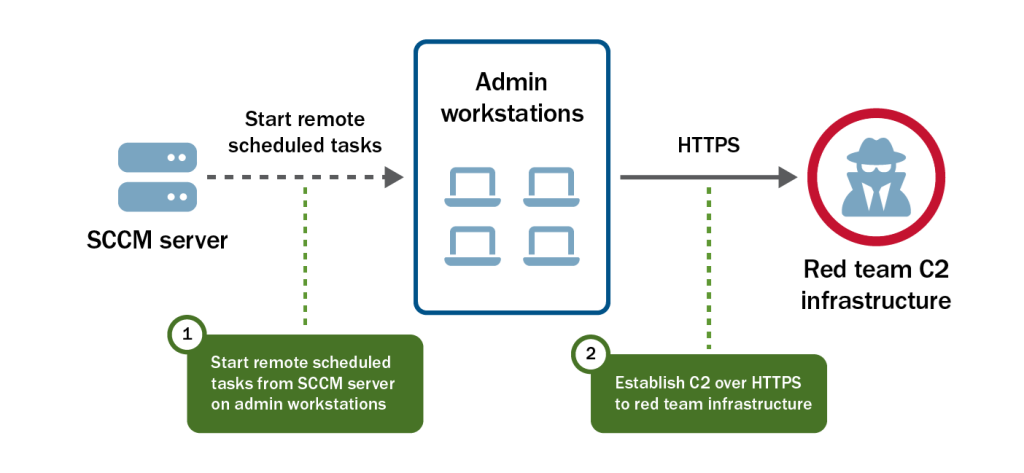
The red team maintained access to these systems for several weeks, periodically checking where they were communicating from to determine if they had moved to another network. Eventually, the team lost access to these systems without a deconfliction. To the best of the red team’s knowledge, these systems either did not move to new networks or, if they did, those systems no longer had the ability to communicate with red team’s C2 infrastructure.
Additional Host and Other Subnets
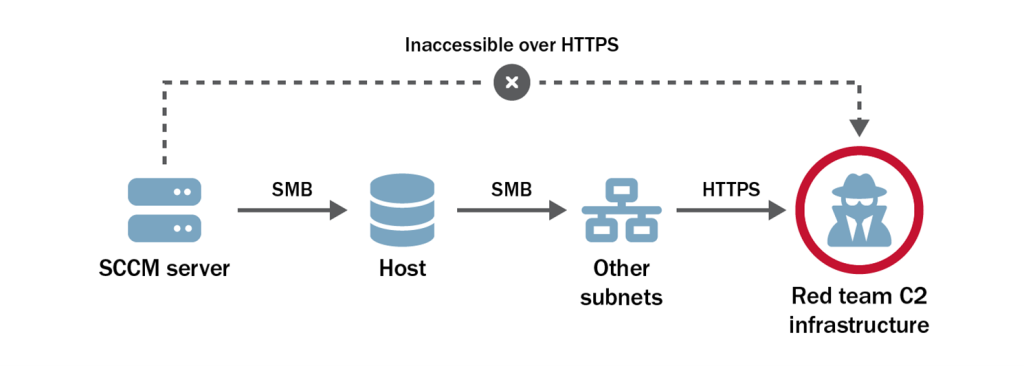
After compromising admin workstations, the red team requested that the TAs prioritize additional systems or IP ranges. The TAs provided four CIDR ranges to target:
- A corporate DMZ that contained a mixture of systems and other subnets.
- A second subnet.
- A third subnet.
- An internal network that contained OT devices.
Access to the corporate DMZ was necessary to reach the second and third ranges, and the red team hoped that gaining access to these would facilitate access to the fourth range.
The red team followed a familiar playbook to gain access to these SBSs from another SCCM server. First, the team performed reverse DNS lookups [T1596.001] on IP addresses within the ranges the TAs provided. They then scanned SMB port 445/TCP [T1046] from a previously compromised SCCM server to discover Windows hosts it could access on the corporate DMZ. The team discovered the server could connect to a host within the target IP range and that the system was running an outdated version of Windows Server 2012 R2. The default configuration of Windows Server 2012 R2 allows unprivileged users to query the group membership of local administrator groups. The red team discovered a user account [T1069] by querying the Windows Server 2012 R2 target that was in a database administrator group. The team leveraged its Preferred Lateral Movement Technique to authenticate to the target as that user, then repeated that technique to access a database. This database receives information from OT devices used to feed monitoring dashboards, information which factors into the organization’s decision-making process [T1213].
The new host had several active connections to systems in the internal ranges of the second and third subnets. Reverse domain name system (DNS) lookup requests for these hosts failed to return any results. However, the systems were also running Windows Server 2012 R2. The red team used Windows API calls to NetLocalGroupEnum and NetLocalGroupGetMembers to query local groups [T1069.001], revealing the system names for these targets as a result. The red team performed their Preferred Lateral Movement Technique to gain access to these hosts in the second and third provided network ranges.
With access to these subnets, the red team began exploring a path to systems on a private subnet where OT devices resided but failed to locate a path to that fourth subnet.
Corporate Workstations of Critical Infrastructure Administrators and Operators
Next, the red team targeted the corporate workstations of the administrators and operators of the organization’s critical infrastructure. Because the team lacked knowledge of the organization’s OT devices and failed to discover a path to the private subnet where they resided, they instead tried to locate users that interacted with human machine interfaces (HMI). Access to such users could enable the team to access the HMI, which serves as a dashboard for OT.
The red team leveraged its AD data once again, combining this data with user information from SCCM to identify targets by job role and their primary workstation. Then the team targeted the desktop of a critical infrastructure administrator, the workstation of another critical infrastructure administrator, and the workstations of three critical infrastructure operators spread across two geographically disparate sites.
The AD data revealed users in a group that were administrators of all the targets. The red team then repeated their Preferred Lateral Movement Technique and identified a logged-in user connected to a “System Status and Alarm Monitoring” interface. The team discovered credentials to the interface in the user’s home directory, proxied through the system, and accessed the HMI interface over HTTP. The team did not pursue further activity involving the interface because their remaining assessment time was limited. Additionally, they did not discover a way to compromise the underlying OT devices.
Command and Control
The team used third-party owned and operated infrastructure and services [T1583] throughout its assessment, including in certain cases for command and control (C2). The tools that the red team obtained included [T1588.002]:
- Sliver, Mythic, Cobalt Strike, and other commercial C2 frameworks.
- The team maintained multiple command and control servers hosted by several cloud vendors. They configured each server with a different domain and used the servers for communication with compromised hosts. These servers retained all assessment data.
- Two commercially available cloud-computing platforms.
- The team used these platforms to create flexible and dynamic redirect servers to send traffic to the team’s servers [T1090.002]. Redirecting servers make it difficult for defenders to attribute assessment activities to the backend team servers. The redirectors use HTTPS reverse proxies to redirect C2 traffic between the target organization’s network and the team servers. The team encrypted all data in transit [T1573] and secured all data at rest through a VPN with multifactor authentication.
- Content delivery network (CDN) services.
- This technique leverages CDNs associated with high-reputation domains, causing malicious traffic to appear directed towards a reputational domain. However, it is redirected to red team-controlled servers. This allows the team to obfuscate some of their C2 traffic.
The team used domain fronting [T1090.004] to disguise outbound traffic, diversifying communications between the domains and the persistent beacons. This technique (which also leverages CDNs) allows the beacon to appear to connect to third-party domains but instead connects to the team’s redirect server.
Defense Evasion and Victim Network Defense Activities
Most of the encounters between the red team and network defenders occurred in the organization’s Linux environment. The red team leveraged Linux tradecraft in an attempt to evade network defenses. In response, network defenders’ threat hunting activities identified some of the team’s presence in their Linux environment. To evade defenses, the red team reordered the process identifier (PID) of its executable processes to appear closer to the kernel and minimize the team’s likelihood of detection. The team also modified its processes [T1055] by changing their names in memory and at execution. In addition, they used Python scripts [T1059.006] run in memory [T1620] to avoid on-disk detection. Some of the red team’s Linux persistence techniques included modifying preexisting scripts run by the cron utility and creating backdoors through ifup-post scripts and .bashrc. Network defenders ultimately identified the team’s backdoor in .bashrc [T1546.004].
Defenders also successfully detected anomalous activity on their Ansible Tower host and other systems in their Linux environment. The defenders actively analyzed NetFlow data, which helped them identify the red team’s persistence and lateral movement. To mitigate the impact of the red team’s tactics, network defenders would have needed to shut down a critical server as part of their incident response activities. A shut down would have resulted in downtime for hundreds of systems, including SBSs.
The organization’s EDR solutions largely failed to protect the organization. EDR detected only a few of the red team’s payloads in the organization’s Windows and Linux environments. In the instance the EDR protected the organization from the initial phishing payload, it generated an alert that network defenders neither read nor responded to. The red team excelled in bypassing EDR solutions by avoiding the use of basic “known-bad” detections the tools would capture. The team also inflated its file sizes above the upload threshold of the organization’s EDR [T1027.001]. In addition, the organization completely lacked any EDR solution in a legacy environment. As such, the red team’s persistence there went undetected throughout the assessment.
Network defenders failed to detect red team activity in the organization’s Windows environment due to a lack of proper identity management. Specifically, network defenders failed to detect and respond to the red team’s S4U2Self, asktgs, dcsync, and golden ticket activity. Had the organization monitored for unusual activity involving AD and Kerberos, they would have detected more red team activity.
Lastly, there were significant deficiencies in the organization’s DMZ that should have detected traffic into the organization’s internal network over the ports used by SMB and LDAPS. Network defenders never properly implemented an intrusion detection system (IDS) or intrusion prevention system (IPS) to monitor the DMZ at the network level. This lack of implementation resulted in a failure to detect malicious network traffic through their DMZ. Further, the red team was able to move laterally through the DMZ because there was an open internal proxy with internet access that enabled the team’s C2.
Phase II: Red Team Measurable Events Activity
The red team executed 13 measurable events designed to provoke a response from the people, processes, and technology defending the organization’s network. The red team did not have full visibility into the organization’s responses to these events and lacked the support of a white team to help assess the organization’s responses. See Table 1 for a description of the events, the organization’s actual response, and key takeaways.
| Measurable Event | Description | MITRE ATT&CK Technique(s) | Organization’s Reported Reactions | Key Takeaways |
|---|---|---|---|---|
| Internal Port Scan | Launches a scan from inside the network from a previously gained workstation to enumerate ports on target workstation, server, and domain controller system(s). | Network Service Discovery [T1046] | Identified an AD enumeration tool and temporarily blocked access to one C2 domain, which resulted in the red team temporarily losing access to six SCCM servers. | The organization did not report identifying the port scan. In addition, with proper network segmentation, the scan’s target hosts should not have been able to communicate. |
| Comprehensive Active Directory and Host Enumeration | Performs AD enumeration by querying all domain objects from the DC and enumerates trust relationships within the AD Forest, user accounts, and current session information from every domain computer (workstation and server). |
Domain Trust Discovery [T1482] Account Discovery: Domain Account [T1087.002] System Owner/User Discovery [T1033] Remote System Discovery [T1018] |
Identified an AD enumeration tool and temporarily blocked access to one C2 domain, which resulted in the red team temporarily losing access to six SCCM servers. | The organization did not report identifying the port scan. In addition, with proper network segmentation, the scan’s target hosts should not have been able to communicate. |
| Data Exfiltration – 1 GB of Data | Sends a large amount (1GB) of mock sensitive information to an external host. | Exfiltration Over Alternative Protocol [T1048] | A proxy likely blocked 1GB of data exfiltration during the red team’s first attempt. However, the team’s second attempt was successful when they exfiltrated the data in 100MB blocks. Hours after the data exfiltration, the organization blocked the domain used for C2 and removed access to the compromised host. | Organizations should implement web proxies that contain data threshold restrictions. Furthermore, network defenders need to manually analyze proxy data to determine whether there is legitimate outbound traffic or potentially malicious data exfiltration. |
| Malicious Traffic Generation- Workstation to External Host | Establishes a session that originates from a target workstation system directly to an external host over a clear text protocol, such as HTTP. | Application Layer Protocol [T1071] | The organization blocked access to the host and the C2 domains the red team used. | The organization blocked the malicious traffic at the network level but did not appear to identify the source workstation. |
| Active Directory Account Lockout | Locks out several administrative AD accounts in rapid succession. | Account Access Removal [T1531] | The organization’s password policy locked out the AD accounts. However, within minutes the accounts reopened, likely due to a group policy and/or an automated response. | There was no identified active response from the organization. Organizations should monitor AD account activity in Windows event logs against baselines to detect anomalous and potentially malicious activity. |
| Local Admin User Account Creation (workstation) | Creates a local administrator account on a target workstation system. |
Create Account: Local Account [T1136.001] Account Manipulation [T1098] |
An automated response removed the account from local administrator’s group but did not delete it. | Despite group policy objects removing the account, there were no detections for the activity. |
| Local Admin User Account Creation (server) | Creates a local administrator account on a target server system. |
Create Account: Local Account [T1136.001] Account Manipulation [T1098] |
An automated response removed the account from local Administrator’s group but did not delete it. | Despite group policy objects removing the account, there were no detections for the activity. |
| Active Directory Account Creation | Creates AD accounts and add them to domain admins group |
Create Account: Domain Account [T1136.002] Account Manipulation [T1098] |
An alert existed for this action but was disabled at the time the original event was triggered, thus it was undetected. After coordination between the TAs and red team revealed this lapse, the alert was enabled, the red team performed the action once again, and this time, TAs provided a screenshot of the alert from their monitoring dashboards. | Detection tools are only useful when network defenders tune them appropriately and effectively monitor alerts. At first, the organization missed an opportunity to respond to a tool that should have produced a true positive alert because it was misconfigured. |
| Domain Admin Lateral Movement—Workstation to Domain Controller and Workstation to Workstation | Compromises a Domain Admin account and uses it to run PSExec on multiple workstations and domain controllers. |
System Services: Service Execution [T1569.002] Remote Services: SMB/Windows Admin Shares [T1021.002] |
None identified. | Detect malicious use of standard tools like PSExec that malicious cyber actors may use for lateral movement by monitoring Windows logs for anomalous activity. In addition, organizations should look for abnormal communications between workstations. |
| Malicious Traffic Generation- Domain Controller to External Host | Establishes a session that originates from a target domain controller system directly to an external host over a clear text protocol, such as HTTP. | Application Layer Protocol [T1071] | None identified. | DCs should never connect directly to an external host over HTTP. The organization failed to detect and respond to this. |
| Trigger Host-Based Protection- Domain Controller | Uploads and executes a well-known (e.g., with a signature) malicious file to a target DC system to generate host-based alerts. | Ingress Tool Transfer [T1105] | Malicious file was removed by host-based endpoint protection system. | Host based detection tools can be helpful in detecting known IOCs. However, organizations should focus on detecting anomalous behavior by monitoring their networks and hosts against good baselines. The blocking of this well-known tool on a DC should trigger an urgent investigation. |
| Ransomware Simulation |
Executes simulated ransomware on multiple workstation systems to simulate a ransomware attack. Note: This technique does not encrypt files on the target system. |
N/A | Two out of nine users reported the event to defensive staff who identified all hosts that executed the ransomware. Five users likely rebooted their systems when observing the ransomware, one logged off and on, one closed the ransomware application repeatedly and continued working, one locked their screen, and another user exited the ransomware process after two hours. | Security awareness training should provide employees effective tools on how to respond to ransomware activity. |
LESSONS LEARNED AND KEY FINDINGS
The red team noted the following lessons learned relevant to all organizations generated from the security assessment of the organization’s network. These findings contributed to the team’s ability to gain persistent access across the organization’s network. See the Mitigations section for recommendations on how to mitigate these findings.
Lesson Learned: Insufficient Technical Controls
The assessed organization had insufficient technical controls to prevent and detect malicious activity. The organization relied too heavily on host-based EDR solutions and did not implement sufficient network layer protections.
- Finding #1: The organization’s perimeter network was not adequately firewalled from its internal network, which allowed the red team a path through the DMZ to internal networks. A properly configured network should block access to a path from the DMZ to other internal networks.
- Finding #2: The organization was too reliant on its host-based tools and lacked network layer protections, such as well-configured web proxies or intrusion prevention systems (IPS). The organization’s EDR solutions also failed to catch all the red team’s payloads. Below is a list of some of the higher risk activities conducted by the team that were opportunities for detection:
- Phishing;
- Kerberoasting;
- Generation and use of golden tickets;
- S4U2self abuse;
- Anomalous LDAP traffic;
- Anomalous NFS enumeration;
- Unconstrained Delegation server compromise;
- DCSync;
- Anomalous account usage during lateral movement;
- Anomalous outbound network traffic;
- Anomalous outbound SSH connections to the team’s cloud servers from workstations; and
- Use of proxy servers from hosts intended to be restricted from internet access.
- Finding #3: The organization had insufficient host monitoring in a legacy environment. The organization had hosts with a legacy operating system without a local EDR solution, which allowed the red team to persist for several months on the hosts undetected.
Lesson Learned: Continuous Training, Support, and Resources
The organization’s staff requires continuous training, support, and resources to implement secure software configurations and detect malicious activity. Staff need to continuously enhance their technical competency, gain additional institutional knowledge of their systems, and ensure are provided sufficient resources by management to adequately protect their networks.
- Finding #4: The organization had multiple systems configured insecurely. This allowed the red team to compromise, maintain persistence, and further exploit those systems (i.e., access credentials, elevate privileges, and move laterally). Insecure system configurations included:
- Default server configurations. The organization used default configurations for hosts with Windows Server 2012 R2, which allows unprivileged users to query membership of local administrator groups. This enabled the red team to identify several standard user accounts with administrative access.
Note: By default, NFS shares change the root user to thenfsnobodyuser, an unprivileged user account. In this way, users with local root access are prevented from gaining root level access over the mounted NFS share. Here, the organization deviated from the secure by default configuration and implemented theno_root_squashoption to support a few legacy systems instead. This deviation from the default allowed the red team to escalate their privileges over the domain. - Hosts with
Unconstrained Delegationenabled unnecessarily. Hosts withUnconstrained Delegationenabled will store the Kerberos TGTs of all users that authenticate to that host. This affords threat actors the opportunity to steal TGTs, including the TGT for a domain controller, and use them to escalate their privileges over the domain. - Insecure Account Configuration. The organization had an account running a Linux webserver with excessive privileges. The entry for that user in the
sudoersfile—which controls user rights—contained paths with wildcards where that user had write access, allowing the team to escalate privileges.
Note: This file should only contain specific paths to executable files that a user needs to run as another user or root, and not a wildcard. Users should not have write access over any file in thesudoersentry.
- Default server configurations. The organization used default configurations for hosts with Windows Server 2012 R2, which allows unprivileged users to query membership of local administrator groups. This enabled the red team to identify several standard user accounts with administrative access.
- Finding #5: The red team’s activities generated security alerts that network defenders did not review. In many instances, the organization relied too heavily on known IOCs and their EDR solutions instead of conducting independent analysis of their network activity compared against baselines.
- Finding #6: The organization lacked proper identity management. Because network defenders did not implement a centralized identity management system in their Linux network, they had to manually query every Linux host for artifacts related to the red team’s lateral movement through SSH. Defenders also failed to detect anomalous activity in their organization’s Windows environment because of poor identity management.
Lesson Learned: Business Risk
The organization’s leadership minimized the business risk of known attack vectors for their organization. Leadership deprioritized the treatment of a vulnerability their own cybersecurity team identified, and in their risk-based decision-making, miscalculated the potential impact and likelihood of its exploitation.
- Finding #7: The organization used known insecure and outdated software. The red team discovered software on one of the organization’s web servers that was outdated.
- After their operations, the red team learned the insecure and outdated software was a known security concern. The organization’s security team alerted management to the risks associated this software, but management accepted the risk.
- Next, the security team implemented a VDP program, which resulted in a participant exploiting the vulnerability for initial access. The VDP program helped the security team gain management support, and they implemented a web application firewall (WAF) as a compensating control. However, they did not adequately mitigate the vulnerability as they configured the WAF to be only in monitoring mode. The security team either did not have processes (or implement them properly) to scan, assess, and test whether they treated the vulnerability effectively.
Additional Findings
The red team noted the following additional issues relevant to the security of the organization’s network that contributed to their activity.
- Unsecured Keys and Credentials. The organization stored many private keys that lacked password protection, allowing the red team to steal the keys and use them for authentication purposes.
- The private key of a PFX file was not password protected, allowing the red team to use that certificate to authenticate to active directory, access UDHOST, and eventually compromise the DC. In addition, the organization did not require password protection of SSH private keys.
Note: Without a password protected key, an actor can more easily steal the private key and use it to authenticate to a system through SSH. - The organization had files in a home share that contained cleartext passwords. The accounts included, among other accounts, a system administrator.
Note: The organization appeared to store cleartext passwords in the description and user password sections of Active Directory accounts. These passwords were accessible to all domain users.
- The private key of a PFX file was not password protected, allowing the red team to use that certificate to authenticate to active directory, access UDHOST, and eventually compromise the DC. In addition, the organization did not require password protection of SSH private keys.
- Email Address Verification. The active Microsoft Office 365 configuration allows an unauthenticated external user to validate email addresses through observing error messages in the form of
HTTP 302versusHTTP 200responses. This misconfiguration helps threat actors verify email addresses before sending phishing emails.
Noted Strengths
The red team noted the following technical controls or defensive measures that prevented or hampered offensive actions:
- Network defenders detected the initial compromise and some red team movement. After being alerted of the web shell, the organization initiated hunt activities, detected initial access, and tracked some of the red team’s Phase I movements. The organization terminated much of the red team’s access to the organization’s internal network. Of note, once the organization’s defenders discovered the red team’s access, the red team spent significant time and resources continuously refortifying their access to the network.
- Host-based EDR solutions prevented initial access by phishing. The EDR stopped the execution of multiple payloads the red team sent to a user of the organization over a week long period. The organization leveraged two products on workstations, one that was publicly discoverable and another the red team did not learn about until gaining initial access. The product the red team was unaware of, and did not test their payload against, was responsible for stopping the execution of their payloads.
- Strong domain password policy. The organization’s domain password policy neutralized the red team’s attempts to crack hashes and spray passwords. The team was unable to crack any hashes of all 115 service accounts it targeted.
- Effective separation of privileges. The organization’s administrative users had separate accounts for performing privileged actions versus routine activities. This makes privilege escalation more difficult for threat actors.
MITIGATIONS
Network Defenders
CISA recommends organizations implement the recommendations in Table 2 to mitigate the findings listed in the Lessons Learned and Key Findings section of this advisory. These mitigations align with the Cross-Sector Cybersecurity Performance Goals (CPGs) developed by CISA and the National Institute of Standards and Technology (NIST). The CPGs provide a minimum set of practices and protections that CISA and NIST recommend all organizations implement. CISA and NIST based the CPGs on existing cybersecurity frameworks and guidance to protect against the most common and impactful threats, tactics, techniques, and procedures. See CISA’s Cross-Sector Cybersecurity Performance Goals for more information on the CPGs, including additional recommended baseline protections.
| Finding | Recommendation |
|---|---|
| Insufficient Network Segmentation of DMZ |
|
| Insufficient Network Monitoring |
|
| Insufficient Host Monitoring in Legacy Environment |
|
| Insecure configurations of systems |
|
| Lack centralized identity management and monitoring systems |
|
| Use of known insecure and outdated software |
|
| Insecure Keys and Credentials |
|
Additionally, CISA recommends organizations implement the mitigations below to improve their cybersecurity posture:
- Provide users with regular training and exercises, specifically related to phishing emails. Phishing accounts for majority of initial access intrusion events.
- Enforce phishing-resistant MFA to the greatest extent possible.
- Reduce the risk of credential compromise via the following:
- Place domain admin accounts in the protected users group to prevent caching of password hashes locally; this also forces Kerberos AES authentication as opposed to weaker RC4 or NTLM authentication protocols.
- Upgrade to Windows Server 2019 or greater and Windows 10 or greater. These versions have security features not included in older operating systems.
As a long-term effort, CISA recommends organizations prioritize implementing a more modern, Zero Trust network architecture that:
- Leverages secure cloud services for key enterprise security capabilities (e.g., identity and access management, endpoint detection and response, and policy enforcement).
- Upgrades applications and infrastructure to leverage modern identity management and network access practices.
- Centralizes and streamlines access to cybersecurity data to drive analytics for identifying and managing cybersecurity risks.
- Invests in technology and personnel to achieve these goals.
Software Manufacturers
The above mitigations apply to critical infrastructure organizations with on-premises or hybrid environments. Recognizing that insecure software is the root cause of many of these flaws and responsibility should not fall on the end user, CISA urges software manufacturers to implement the following:
- Embed security into product architecture throughout the entire software development lifecycle (SDLC).
- Eliminate default passwords. Do not provide software with default passwords. To eliminate default passwords, require administrators to set a strong password [CPG 2.B] during installation and configuration.
- Design products so that the compromise of a single security control does not result in compromise of the entire system. For example, narrowly provision user privileges by default and employ ACLs to reduce the impact of a compromised account. This will make it more difficult for a malicious cyber actor to escalate privileges and move laterally.
- Mandate MFA, ideally phishing-resistant MFA, for privileged users and make MFA a default, rather than opt-in, feature.
- Reduce hardening guide size, with a focus on systems being secure by default. In this scenario, the red team noticed default Windows Server 2012 configurations that allowed them to enumerate privileged accounts.
- Important: Manufacturers need to implement routine nudges that are built into the product rather than relying on administrators to have the time, expertise, and awareness to interpret hardening guides.
These mitigations align with principles provided in the joint guide Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Secure by Design Software. CISA urges software manufacturers to take ownership of improving security outcomes of their customers by applying these and other secure by design practices. By adhering to secure by design principles, software manufacturers can make their product lines secure out of the box without requiring customers to spend additional resources making configuration changes, purchasing security software and logs, monitoring, and making routine updates.
For more information on secure by design, see CISA’s Secure by Design webpage. For more information on common misconfigurations and guidance on reducing their prevalence, see the joint advisory NSA and CISA Red and Blue Teams Share Top Ten Cybersecurity Misconfigurations.
VALIDATE SECURITY CONTROLS
In addition to applying mitigations, CISA recommends exercising, testing, and validating your organization's security program against the threat behaviors mapped to the MITRE ATT&CK for Enterprise framework in this advisory. CISA recommends testing your existing security controls inventory to assess how they perform against the ATT&CK techniques described in this advisory.
To get started:
- Select an ATT&CK technique described in this advisory (see Table 3 to Table 16).
- Align your security technologies against the technique.
- Test your technologies against the technique.
- Analyze your detection and prevention technologies’ performance.
- Repeat the process for all security technologies to obtain a set of comprehensive performance data.
- Tune your security program, including people, processes, and technologies, based on the data generated by this process.
CISA recommends continually testing your security program, at scale, in a production environment to ensure optimal performance against the MITRE ATT&CK techniques identified in this advisory.
RESOURCES
- See CISA’s RedEye tool on CISA’s GitHub page. RedEye is an interactive open source analytic tool used to visualize and report red team command and control activities. See CISA’s RedEye tool overview video for more information.
- See CISA’s Phishing Guidance.
- See CISA’s Secure by Design page to learn more about secure by design principles.
APPENDIX: MITRE ATT&CK TACTICS AND TECHNIQUES
See Table 3 to Table 16 for all referenced red team tactics and techniques in this advisory. Note: Unless noted, activity took place during Phase I. For assistance with mapping malicious cyber activity to the MITRE ATT&CK framework, see CISA and MITRE ATT&CK’s Best Practices for MITRE ATT&CK Mapping and CISA’s Decider Tool.
| Technique Title | ID | Use |
|---|---|---|
| Gather Victim Network Information | T1590 | The team conducted open source research on the target organization to gain information about its network. |
| Gather Victim Network Information: Network Security Appliances | T1590.006 | The team conducted open source research on the target organization to gain information about its defensive tools. |
| Gather Victim Identity Information: Employee Names | T1589.003 | The team conducted open source research on the target organization to gain information about its employees. |
| Active Scanning | T1595 | The team conducted external reconnaissance of the organization’s network. |
| Gather Victim Network Information: IP Addresses | T1590.005 | The team conducted reconnaissance of the organization’s external IP space. |
| Search Open Websites/Domains | T1593 | The team conducted open source research to identify information about the organization’s network. |
| Gather Victim Identity Information: Email Addresses | T1589.002 | The team looked for email addresses and names to infer email addresses from the organization’s email syntax. |
| Search Open Technical Databases: Scan Databases | T1596.005 | The team conducted reconnaissance with several publicly available tools, such as Shodan and Censys, to discover accessible devices and services on the internet. |
| Search Open Technical Databases: DNS/Passive DNS | T1596.001 | The team performed reverse DNS lookups on IP addresses within the ranges the TAs provided. |
| Technique Title | ID | Use |
|---|---|---|
| Acquire Infrastructure | T1583 | The team used third-party owned and operated infrastructure and services throughout its assessment. |
| Obtain Capabilities: Tool | T1588.002 | The team obtained tools (i.e., Sliver, Mythic, Cobalt Strike, and other commercial C2 frameworks). |
| Technique Title | ID | Use |
|---|---|---|
| Phishing | T1566 | The team designed spearphishing campaigns tailored to employees of the organization most likely to communicate with external parties. |
| Exploit Public-Facing Application | T1190 | The team gained initial access to the target by exploiting an internet-facing Linux web server. |
| Phishing: Spearphishing Link | T1566.002 | The team sent tailored spearphishing emails to 13 targets. |
| Technique Title | ID | Use |
|---|---|---|
| User Execution | T1204 | The team’s phishing attempts were ultimately unsuccessful; targets ran the payloads, but their execution did not result in the red team gaining access into the network. |
| User Execution: Malicious File | T1204.002 | One user responded and executed two malicious payloads. |
| Command and Scripting Interpreter | T1059 | The preexisting web shell allowed the team to run arbitrary commands on the server. |
| Command and Scripting Interpreter: Python | T1059.006 | The team used python scripts. |
| System Services: Service Execution | T1569.002 | The team compromised a Domain Admin account and used it to run PSExec on multiple workstations and a domain controller. |
| Remote Services: SMB/Windows Admin Shares | T1021.002 | The team established a session that originated from a target. |
| Technique Title | ID | Use |
|---|---|---|
| Server Software Component: Web Shell | T1505.003 | After the failed spearphishing campaigns, the red team continued external reconnaissance of the network and discovered a web shell left from a previous VDP program. |
| Boot or Logon Initialization Scripts | T1037 | The team backdoored several scripts run at boot time for persistence. |
| Scheduled Task/Job: Cron | T1053.003 | Some of the team’s techniques included modifying preexisting scripts run by the cron utility and ifup-post scripts. |
| Boot or Logon Initialization Scripts: Network Logon Script | T1037.003 | The team modified preexisting scripts run by the cron utility and ifup-post scripts. |
| Event Triggered Execution: Unix Shell Configuration Modification | T1546.004 | The team used a backdoor in .bashrc. |
| Create Account: Local Account | T1136.001 | During Phase II, the team created a local administrator account on a target server system. |
| Account Manipulation | T1098 | During Phase II, the team created a local administrator account on a target server system. |
| Create Account: Domain Account | T1136.002 | The team created AD accounts and added them to domain admins group. |
| Technique Title | ID | Use |
|---|---|---|
| Valid Accounts | T1078 | The team moved laterally from the web server to the organization’s internal network using valid accounts. |
| Abuse Elevation Control Mechanism: Sudo and Sudo Caching | T1548.003 | The team discovered that WEBUSER1 had excessive sudo rights, allowing them to run some commands as root without a password. |
| Technique Title | ID | Use |
|---|---|---|
| Process Injection | T1055 | The team modified its processes by changing their names in memory and at execution. |
| Reflective Code Loading | T1620 | The team used Python scripts run in memory to avoid on-disk detection. |
| Obfuscated Files or Information: Binary Padding | T1027.001 | The team inflated its file sizes above the upload threshold of the organization’s EDR. |
| Technique Title | ID | Use |
|---|---|---|
| Unsecured Credentials: Credentials In Files | T1552.001 | The team discovered credential material on a misconfigured Network File System. |
| Steal or Forge Authentication Certificates | T1649 | The team used a certificate for client authentication discovered on the NFS share to compromise a system configured for Unconstrained Delegation. |
| Steal or Forge Kerberos Tickets: Golden Ticket | T1558.001 | The team acquired a ticket granting ticket for a domain controller. |
| Unsecured Credentials: Bash History | T1552.003 | The team used its escalated privileges to search bash command histories. |
| Data from Network Shared Drive | T1039 | The team used its escalated privileges to search for private certificate files, Secure Shell (SSH) private keys, passwords, bash command histories, and other sensitive data across all user files on the NFS share. |
| Unsecured Credentials: Private Keys | T1552.004 | The team initially obtained 61 private SSH keys and a file containing valid cleartext domain credentials. |
| Valid Accounts: Domain Accounts | T1078.002 | The team initially obtained 61 private SSH keys and a file containing valid cleartext domain credentials. |
| Network Sniffing | T1187 | The red team leveraged this administrative access to upload a modified version of Rubeus in monitor mode to capture incoming tickets. |
| OS Credential Dumping: DCSync | T1003.006 | The team used DCSync through Linux tunnels to acquire the hash of several privileged accounts. |
| Technique Title | ID | Use |
|---|---|---|
| System Network Configuration Discovery | T1016 | The team leveraged the web shell to identify an open internal proxy server. |
| Account Discovery | T1087 | The team leveraged their AD data to identify administrators of the SCCM servers. |
| Account Discovery: Domain Account | T1087.002 | The team queried LDAPS to collect information about users, computers, groups, access control lists (ACL), organizational units (OU), and group policy objects (GPO). During Phase II, the team performed AD enumeration by querying all domain objects from the DC, as well as enumerating trust relationships within the AD Forest, user accounts, and current session information from every domain computer. |
| Remote System Discovery | T1018 | The team queried LDAPS to collect information about users, computers, groups, access control lists (ACL), organizational units (OU), and group policy objects (GPO). During Phase II, the team performed AD enumeration by querying all domain objects from the DC as well as enumerating trust relationships within the AD Forest, user accounts, and current session information from every domain computer. |
| Permission Groups Discovery: Domain Groups | T1069.002 | The team queried LDAPS to collect information about users, computers, groups, access control lists (ACL), organizational units (OU), and group policy objects (GPO). |
| Group Policy Discovery | T1615 | The team queried LDAPS to collect information about users, computers, groups, access control lists (ACL), organizational units (OU), and group policy objects (GPO). |
| Network Service Discovery | T1046 |
The team scanned SMB port 445/TCP. During Phase II, the team launched a scan from inside the network from a previously gained workstation. |
| Permission Groups Discovery | T1069 | The team discovered a user account through querying the Windows Server 2012 R2 target. |
| Permission Groups Discovery: Local Groups | T1069.001 | The team used Windows API calls to NetLocalGroupEnum and NetLocalGroupGetMembers to query local groups. |
| Domain Trust Discovery | T1482 | During Phase II, the team enumerated trust relationships within the AD Forest. |
| System Owner/User Discovery | T1033 | During Phase II, the team performed AD enumeration by querying all domain objects from the DC, as well as enumerating trust relationships within the AD Forest, user accounts, and current session information from every domain computer. |
| Technique Title | ID | Use |
|---|---|---|
| Taint Shared Content | T1080 | Since no_root_squash was used, the team could read and change any file on the shared file system and leave trojanized applications. |
| Remote Services: SSH | T1021.004 | The team’s acquisition of SSH private keys of user and service accounts, including two highly privileged accounts with root access to hundreds of servers, facilitated unrestricted lateral movement to other Linux hosts. |
| Software Deployment Tools | T1072 | Access to an Ansible Tower system provided the team easy access to multiple SBSs. |
| Technique Title | ID | Use |
|---|---|---|
| Data from Information Repositories | T1213 | The team accessed a database that received information from OT devices to feed monitoring dashboards, which the organization used to make decisions. |
| Technique Title | ID | Use |
|---|---|---|
| Ingress Tool Transfer | T1105 |
The team then downloaded and executed a Sliver payload that utilized this proxy to establish command and control. During Phase II, the team uploaded and executed a well-known malicious file to a target DC system to generate host-based alerts. |
| Application Layer Protocol: Web Protocols | T1071.001 | In the organization’s Linux environment, the red team leveraged HTTPS connections for C2. |
| Proxy: Internal Proxy | T1090.001 | The team leveraged an open internal HTTPS proxy for their traffic. |
| Application Layer Protocol: File Transfer Protocols | T1071.002 | The team connected to servers over SMB. |
| Proxy: External Proxy | T1090.002 | The team used cloud platforms to create flexible and dynamic redirect servers to send traffic to the team’s servers. |
| Encrypted Channel | T1573 | The team encrypted all data in transit and secured all data at rest through a VPN with multifactor authentication. |
| Proxy: Domain Fronting | T1090.004 | The team used domain fronting to disguise outbound traffic. |
| Application Layer Protocol | T1071 | During Phase II, the team established a session that originated from a target Workstation system directly to an external host over a clear text protocol, such as HTTP. |
| Technique Title | ID | Use |
|---|---|---|
| Exfiltration Over Alternative Protocol | T1048 | During Phase II, the team sent a large amount of mock sensitive information to an external host. |
| Technique Title | ID | Use |
|---|---|---|
| Account Access Removal | T1531 | The team locked out several administrative AD accounts in rapid succession. |
As a relatively new security category, many security operators and executives I’ve met have asked us “What are these Automated Security Validation (ASV) tools?” We’ve covered that pretty extensively in the past, so today, instead of covering the “What is ASV?” I wanted to address the “Why ASV?” question. In this article, we’ll cover some […]
The post Cyber Story Time: The Boy Who Cried “Secure!” appeared first on All Hacker News.
Malware on public repositories is nothing new. For a couple of years now, ReversingLabs threat researchers have been monitoring npm, PyPI and recently VSCode Marketplace, RubyGems and NuGet for potential malware whose inclusion in the development cycle could cause a supply chain attack. More often than not, malicious packages are published by new accounts and are made from scratch.
Threat hunters are warning about an updated version of the Python-based NodeStealer that’s now equipped to extract more information from victims’ Facebook Ads Manager accounts and harvest credit card data stored in web browsers. “They collect budget details of Facebook Ads Manager accounts of their victims, which might be a gateway for Facebook malvertisement,” Netskope […]
The post NodeStealer Malware Targets Facebook Ad Accounts, Harvesting Credit Card Data appeared first on All Hacker News.
Cybersecurity researchers have confirmed that the exploitation of D-Link NAS devices has been ongoing. Recently it was found to contain a critical flaw, for which the manufacturer is no longer offering support on such devices.
Critical Flaw and Discontinued Support
A critical security flaw, rated 9.2 on the severity scale, was found in various editions of D-Link NAS devices. This flaw may allow attackers to remotely execute malevolent commands that would place sensitive data stored on these systems at risk. However, D-Link announced that it will not release a patch for this issue as these devices have reached EOL status. Users are instead advised to update to newer products in order to continue protection.
Tens of Thousands of Devices Vulnerable
Researchers have discovered more than 60,000 vulnerable devices worldwide. The affected models include DNS-320 Version 1.00, DNS-320LW Version 1.01.0914.2012, DNS-325 Versions 1.01 and 1.02, and DNS-340L Version 1.08. While the above number of possible exploited devices is very large, so far only around 1,100 instances of exploitation were seen, according to a threat monitoring service called Shadowserver.
Active Exploitation Starts
Exploitation attempts for this vulnerability, tracked as CVE-2024-10914, were first sighted on November 12. According to the researchers at Shadowserver, attackers are taking advantage of a command injection vulnerability on the "/cgi-bin/account_mgr.cgi" endpoint of the affected devices. Though the exploitation of this flaw is relatively complex, a public exploit available does increase the risk for its users.
Shadowserver makes a big point of pulling these types of devices off the internet as their EOL status signifies D-Link will not be putting out any further updates or releases on these devices.
Why NAS Devices Are Attractive
For centralizing data storage, NAS devices make it possible for quite a few users and devices to access and share files, let alone back them up. They are highly used in homes and businesses for reliability, ease of use, and scalability. However, due to their nature as data hubs, they are great targets for cybercriminals-these criminals typically try to steal, encrypt, or delete valuable information, and one of the most commonly used tools is through ransomware attacks.
What Users Should Do
Thereby, the owners of affected D-Link NAS devices are advised to replace them with the supported versions. Disconnecting the affected devices from the internet would be one of the immediate steps to reduce the exposure.
Furthermore, users should keep their systems up to date and implement robust security measures in place for protecting data. For this reason, cyber threats evolve very fast, and only a vigilant user can save the sensitive information.
A new China-linked cyber espionage group has been attributed as behind a series of targeted cyber attacks targeting telecommunications entities in South Asia and Africa since at least 2020 with the goal of enabling intelligence collection. Cybersecurity company CrowdStrike is tracking the adversary under the name Liminal Panda, describing it as possessing deep knowledge about […]
The post China-Backed Hackers Leverage SIGTRAN, GSM Protocols to Infiltrate Telecom Networks appeared first on All Hacker News.
Over 1 million registered domains could be vulnerable to a cyberattack method known as “Sitting Ducks,” as recently unveiled in a new report from Infoblox Threat Intel. This relatively unknown attack vector allows malicious actors to hijack legitimate domains by exploiting misconfigurations in DNS settings. The Sitting Ducks attack, which has been active since 2018, […]
The post Hackers Using Sitting Ducks Attack To Hijack Domains, 1 Million Domains Vulnerable appeared first on Cyber Security News.
IT Asset Management Tools are vital in monitoring and maintaining a company’s assets, and they are known as asset management. Any property a business owns with a cash value is an asset. Examples include goods, business accounts, and even office buildings. It includes buying and selling investments within a portfolio and other investment services institutions provide […]
The post 10 Best IT Asset Management Tools In 2024 appeared first on Cyber Security News.
End-of-Day report
Timeframe: Montag 18-11-2024 18:00 - Dienstag 19-11-2024 18:00 Handler: Alexander Riepl Co-Handler: n/aNews
Spotify abused to promote pirated software and game cheats
Spotify playlists and podcasts are being abused to push pirated software, game cheat codes, spam links, and "warez" sites. By injecting targeted keywords and links in playlist names and podcast descriptions, threat actors may .. https://www.bleepingcomputer.com/news/security/spotify-abused-to-promote-pirated-software-and-game-cheats/New Helldown Ransomware Variant Expands Attacks to VMware and Linux Systems
Cybersecurity researchers have shed light on a Linux variant of a relatively new ransomware strain called Helldown, suggesting that the threat actors are broadening their attack focus."Helldown deploys Windows ransomware derived from the LockBit 3.0 code," Sekoia .. https://thehackernews.com/2024/11/new-helldown-ransomware-expands-attacks.htmlCritical 9.8-rated VMware vCenter RCE bug exploited after patch fumble
If you didnt fix this a month ago, your to-do list probably needs a reshuffle Two VMware vCenter server bugs, including a critical heap-overflow vulnerability that leads to remote code execution (RCE), have been exploited in attacks after Broadcom-s first attempt to fix the flaws fell short. https://www.theregister.com/2024/11/18/vmware_vcenter_rce_exploited/Veritas Enterprise Vault: Kritische Codeschmuggel-Lücken in Archivsoftware
In Vertias Enterprise Vault können Angreifer kritische Lücke zum Einschleusen von Schadcode missbrauchen. https://www.heise.de/news/Veritas-Enterprise-Vault-Kritische-Codeschmuggel-Luecken-in-Archivsoftware-10053675.htmlKritische Palo-Alto-Lücke: Details und Patches sind da, CISA warnt vor Exploit
Fast drei Wochen nach ersten Exploit-Gerüchten hat der Hersteller nun endlich reagiert, trickst aber. Derweil warnt die US-Cyberbehörde vor Angriffen. https://www.heise.de/news/Kritische-Palo-Alto-Luecke-Patches-sind-da-CISA-warnt-vor-Exploit-10051696.htmlFreeBSD Foundation releases Bhyve and Capsicum security audit
The FreeBSD Foundation has announced the release of a security audit report conducted by security firm Synacktiv. The audit uncovered a number of vulnerabilities: Most of these vulnerabilities have been addressed through official FreeBSD Project security advisories, which offer detailed information about each vulnerability, its impact, and the measures .. https://lwn.net/Articles/998615/FrostyGoop-s Zoom-In: A Closer Look into the Malware Artifacts, Behaviors and Network Communications
We analyze FrostyGoop malware, which targets OT systems. This article walks through newly discovered samples, indicators, and also examines configurations and network communications. https://unit42.paloaltonetworks.com/frostygoop-malware-analysis/The Importance of Establishing a Solid Third Party Risk Management Framework for Risk Mitigation
In the previous post, we introduced the concept of Third-Party Risk Management (TPRM) and its importance in today-s interconnected world. Now, let us have a look at the practical aspects of building a solid TPRM program and why it is important for your company. 1. Start with a Third-Party Inventory The first step in building .. https://blog.nviso.eu/2024/11/19/the-importance-of-establishing-a-solid-third-party-risk-management-framework-for-risk-mitigation/Facebook Malvertising Campaign Spreads Malware via Fake Bitwarden
A Facebook malvertising campaign disguised as Bitwarden updates spreads malware, targeting business accounts. Users are tricked .. https://hackread.com/facebook-malvertising-malware-via-fake-bitwarden/Threat Actors Hijack Misconfigured Servers for Live Sports Streaming
To keep up with the ever-evolving world of cybersecurity, Aqua Nautilus researchers deploy honeypots that mimic real-world development environments. During a recent threat-hunting operation, they uncovered a surprising new .. https://blog.aquasec.com/threat-actors-hijack-misconfigured-servers-for-live-sports-streamingPots and Pans, AKA an SSLVPN - Palo Alto PAN-OS CVE-2024-0012 and CVE-2024-9474
Note: Since this is breaking news and more details are being released, were updating this .. https://labs.watchtowr.com/pots-and-pans-aka-an-sslvpn-palo-alto-pan-os-cve-2024-0012-and-cve-2024-9474/NVD Backlog Tops 20,000 CVEs Awaiting Analysis as NIST Prepares System Updates
CVEs awaiting analysis by the NVD have broken the 20,000 mark, after the security community noticed its enrichment activity slowed to nearly a halt again last week. NIST failed to meet its self-imposed deadline of .. https://socket.dev/blog/nvd-backlog-tops-20-000-cvesThreat Actor Exposes Playbook for Exploiting npm to Build Blockchain-Powered Botnets
In October 2024, Socket discovered a widespread npm malware campaign using Ethereum smart contracts to evade detection and maintain control over infected systems. Building on our initial research and equipped with analyses of the .. https://socket.dev/blog/exploiting-npm-to-build-a-blockchain-powered-botnetExtending Burp Suite for fun and profit - The Montoya way - Part 7
Last time we saw how to develop an extension that will add custom active and passive checks to the Burp Scanner. Today we will modify that extension to detect serialization issues using .. https://security.humanativaspa.it/extending-burp-suite-for-fun-and-profit-the-montoya-way-part-7/U.S. Extradites and Charges Alleged Phobos Ransomware Admin
The United States secured the extradition of a Russian national from South Korea who is allegedly the mastermind behind the notorious Phobos ransomware. Evgenii Ptitsyn, 42, is accused of administering the Phobos .. https://thecyberexpress.com/us-charges-alleged-phobos-ransomware-admin/Vulnerabilities
ZDI-24-1516: Trend Micro Deep Security Agent Manual Scan Command Injection Remote Code Execution Vulnerability
This vulnerability allows remote attackers to execute arbitrary code on affected installations of Trend Micro Deep Security Agent. Authentication is required to exploit this vulnerability. The ZDI has assigned a CVSS rating of 7.5. The following CVEs are assigned: CVE-2024-51503. http://www.zerodayinitiative.com/advisories/ZDI-24-1516/ZDI-24-1517: McAfee Total Protection Uncontrolled Search Path Element Local Privilege Escalation Vulnerability
This vulnerability allows local attackers to escalate privileges on affected installations of McAfee Total Protection. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. The ZDI has assigned a CVSS rating of 6.7. The following CVEs are assigned: CVE-2024-49592. http://www.zerodayinitiative.com/advisories/ZDI-24-1517/Security updates for Tuesday
Security updates have been issued by AlmaLinux (.NET 9.0, bcc, bluez, bpftrace, bubblewrap, flatpak, buildah, cockpit, containernetworking-plugins, cups, cyrus-imapd, edk2, expat, firefox, fontforge, gnome-shell, gnome-shell-extensions, grafana, grafana-pcp, gtk3, httpd, iperf3, jose, krb5, libgcrypt, libsoup, libvirt, libvpx, lldpd, microcode_ctl, .. https://lwn.net/Articles/998755/Oracle Security Alert for CVE-2024-21287 - 18 November 2024
https://www.oracle.com/security-alerts/alert-cve-2024-21287.html
Malicious actors are exploiting misconfigured JupyterLab and Jupyter Notebooks to conduct stream ripping and enable sports piracy using live streaming capture tools. The attacks involve the hijack of unauthenticated Jupyter Notebooks to establish initial access, and perform a series of actions designed to facilitate illegal live streaming of sports events, Aqua said in a report […]
The post Hackers Hijack Unsecured Jupyter Notebooks to Stream Illegal Sports Broadcasts appeared first on All Hacker News.
At Microsoft, security is our top priority, and with every release, Windows becomes even more secure. At Ignite 2024, we will highlight new Windows security innovations that will provide the clarity and confidence our customers and organizations requ
The post Windows security and resiliency: Protecting your business appeared first on Windows Blog.
DNS Reaper DNS Reaper is yet another subdomain takeover tool, but with an emphasis on accuracy, speed, and the number of signatures in our arsenal! We can scan around 50 subdomains per second, testing...
The post dnsReaper: subdomain takeover tool for attackers, bug bounty hunters and the blue team appeared first on Penetration Testing Tools.
Cybersecurity researchers have shed light on a new stealthy malware loader called BabbleLoader that has been observed in the wild delivering information stealer families such as WhiteSnake and Meduza. BabbleLoader is an “extremely evasive loader, packed with defensive mechanisms, that is designed to bypass antivirus and sandbox environments to deliver stealers into memory,” Intezer security […]
The post New Stealthy BabbleLoader Malware Spotted Delivering WhiteSnake and Meduza Stealers appeared first on All Hacker News.
 Welcome to this week's Data Breaches Digest, a catalogue of links concerning Data Breaches and Cyber Security that were published on the Internet during the period between 18th November and 24th November 2024.
Welcome to this week's Data Breaches Digest, a catalogue of links concerning Data Breaches and Cyber Security that were published on the Internet during the period between 18th November and 24th November 2024.18th November
1.5 Million Exposed: Set Forth & Centrex Hit by Massive Data Breach
ADT Freight Services listed as alleged victim by Sarcoma ransomware gang
AI Can Be Leveraged For Phishing Scams: What You Need To Know To Stay Safe
APT Group DONOT Launches Cyberattack on Pakistan’s Maritime and Defense Industry
Argentina: Student Database Breach in Entre Ríos Province
Australia: Cyber security bill recommended for 'urgent' parliamentary approval
Bitfinex hacker who stole 120,000 bitcoins gets five years in prison
Black Friday or Black Fraud-day? A Prime Time for Fraud and Cyberattacks
Chatbots & Voice Phishing: How To Safeguard Against Potential Risks From AI
Chinese Salt Typhoon Hacked T-Mobile in US Telecom Breach Spree
Critical RCE bug in VMware vCenter Server now exploited in attacks
Don’t Hold Down The Ctrl Key - New Warning As Cyber Attacks Confirmed
Fake Bitwarden ads on Facebook push info-stealing Chrome extension
Fake Discount Sites Exploit Black Friday to Hijack Shopper Information
Ford Customer Data Breach, German Statistical Data Leak, and Bank of France Targeted
Germany: Stauberstahl.com Database Breach Exposes Sensitive Data
Gmail's New Shielded Email Feature Lets Users Create Aliases for Email Privacy
Hacked crypto project Thala agrees to $300K bounty, recovers $25M
Helix darknet Bitcoin 'mixer' will fork over $750M, serve time, for processing 1M+ transactions
How and where to report cybercrime: What you need to know
How to ensure a fast recovery from the inevitable cyber-attack
Increased GDPR Enforcement Highlights the Need for Data Security
India: NCISM NEET Students Data Breach Exposes Personal Details
India: Sreedharscce.com Data Breach Exposes Millions of Records
India: Tjori.com 2021 Data Breach Exposes 1 Million User Records
India sees 135,173 financial phishing attacks in H1 2024, says study
Major US telecom T-Mobile among victims of China-linked breach
Microsoft 365 Admin portal abused to send sextortion emails
Mistakes that leave you open to attack
Mozilla 0Din Warns of ChatGPT Sandbox Flaws Enabling Python Execution
Navigating the compliance labyrinth: A CSO’s guide to scaling security
North Korean IT Worker Network Tied to BeaverTail Phishing Campaign
NSO Group Exploited WhatsApp to Install Pegasus Spyware Even After Meta's Lawsuit
Palo Alto firewalls exploited after critical zero-day vulnerability
Palo Alto Networks patches two firewall zero-days used in attacks
RansomHub ransomware gang claims data breach targeting Mexican government
RansomHub says 313GB exfiltrated in Mexican government cyber attack
Ransomware: Significant rise of attacks on Indian businesses
Ransomware attacks surge in Southeast Asia with 57,000 cases
Strengthening cybersecurity this Black Friday: combatting social engineering and phishing threats
Surge in DocuSign Phishing Attacks Target US State Contractors
T-Mobile confirms breach amid wave of Chinese state-sponsored telecom attacks
TEAM Software Breach, Hackers Gain Unauthorized Access To Network Infrastructure
Thala recovers $25.5M in crypto lost through v1 farming vulnerability
The Problem of Permissions and Non-Human Identities - Why Remediating Credentials Takes Longer Than You Think
Transforce.in – Database Breach Exposes Sensitive User Data
Turkey fines Amazon’s Twitch 2 million lira for data breach
Turkey sanctions Twitch for user data breach
Türkiye fines Twitch $58K over massive data breach impacting thousands
Twitch Fined $58K in Turkey Over Major Data Breach Fail
UK Shoppers Lost £11.5m Last Christmas, National Cyber Security Centre (NCSC) Warns
Unraveling the Mysteries of Ransomware- How AI-Driven Detection is Turning the Tide
Urgent: Critical WordPress Plugin Vulnerability Exposes Over 4 Million Sites
URL Login & Password Leak – 2.5 Million Records Exposed
US charges Phobos ransomware admin after South Korea extradition
US space tech giant Maxar discloses employee data breach
When trying to download QuickBooks via a Google search, users may visit the wrong site and get an installer containing malware.
A new phishing campaign is targeting e-commerce shoppers in Europe and the United States with bogus pages that mimic legitimate brands with the goal of stealing their personal information ahead of the Black Friday shopping season. “The campaign leveraged the heightened online shopping activity in November, the peak season for Black Friday discounts. The threat […]
The post Fake Discount Sites Exploit Black Friday to Hijack Shopper Information appeared first on All Hacker News.
ADcheck Assess the security of your Active Directory with few or all privileges. This tool offers functionalities similar to PingCastle, ORADAD, or even PurpleKnight (with some bonuses). ADcheck is developed in pure Python to bypass operating system...
The post ADcheck: Assess the security of your Active Directory appeared first on Penetration Testing Tools.
A vulnerability was found in ISC BIND up to 9.18.27/9.18.27-S1/9.19.24. It has been classified as critical. Affected is an unknown function of the component DNS Messages over TCP Handler. The manipulation leads to resource consumption. This vulnerability is traded as CVE-2024-0760. It is possible to launch the attack remotely. There is no exploit available. It is recommended to upgrade the affected component.
A vulnerability was found in Samba up to 4.16.x. It has been rated as critical. This issue affects some unknown processing. The manipulation of the argument dNSHostName leads to incorrect default permissions. The identification of this vulnerability is CVE-2022-32743. Access to the local network is required for this attack. There is no exploit available. It is recommended to upgrade the affected component.
You notice your battery draining faster than usual, your phone feels hotter than it should, and those creepy, overly specific ads are popping up more frequently. You can’t help but wonder — is someone tracking my every move? It’s a chilling thought, especially since our phones feel like part of us these days. The truth...
Expert's Rating
Pros
- Clean, simple interface
- Essential protection against malware
- Lower impact on PC system resources
Cons
- Less participation in testing performed by independent security organizations
- Extremely light on features
Our Verdict
Malwarebytes Premium Security offers a simple, easy-to-use alternative to Windows Security—but don’t expect big bang for your buck. Seasoned security vets may also find the lower amount of available independent performance test results offputting.
Price When Reviewed
This value will show the geolocated pricing text for product undefined
Best Pricing Today
Price When Reviewed
60
Best Prices Today: Malwarebytes Premium Security
Malwarebytes was once a crucial piece of software—a necessary supplement for your main antivirus scanner. You couldn’t always count on just one program to catch everything, and Malwarebytes rose to prominence as a reliable secondary tool.
But the world has changed since 2010. Now if you run multiple antivirus apps, you could open yourself up to software conflicts or increased risk for system vulnerabilities. One single program is the way to go—and if you’re a newbie to security and prefer a dead simple app, then Malwarebytes’ streamlined, elegant approach can fit the bill.
How much does Malwarebytes Premium Security cost?
As a simple suite, Malwarebytes Premium Security costs $60 per year. New subscribers can sign up for a two-year package to save $9 ($111 total). Unlike most other antivirus vendors, Malwarebytes bills in monthly installments over a 12-month term, rather than charging the total cost upfront.
For its consumer products, the company offers a 14-day trial, and a 60-day money back guarantee.
Single-device plan (3 devices)
- $60 per year (billed monthly over a 12-month term)
Malwarebytes’ plan allows you to spread your device allotment over those running Windows, macOS, Android, iOS, and even ChromeOS.
PCWorld
If you want to cover more gear, or save a little more cash, you can get licenses for Malwarebytes through third-parties like Amazon and the PCWorld Software store with more flexible terms and at lower rates. However, such plans currently don’t include VPN service, which Malwarebytes added to the subscriptions it sells directly.
What does Malwarebytes Premium Security include?
When you step up from Malwarebytes’ free version to a paid subscription, real-time monitoring for malware, email, web, and select network threats becomes active. (The free plan only scans if you initiate a manual check.) Overall, you’re protected against viruses, ransomware, and other malware, as well as other common attacks like phishing attempts, zero-day exploits on the web and over email, and suspicious apps.
Choosing Malwarebytes Premium Security adds on access to the company’s VPN, which Malwarebytes advertises as a no-log service. As premium upgrades go, this one is simplistic—you don’t get parental controls, a password manager, additional defenses like protected folders, or PC utilities, as you do with a rival like AVG. The company seems to weigh its VPN service as equally valuable to a collection of such antivirus features.
Key features of Malwarebytes Premium Security
Installation and user interface
After you install the app, you’ll see the main dashboard. The interface is incredibly streamlined, with just two tabs on the left navbar—Dashboard and Settings. You can choose between Light, Dark, or matching Windows’ mode.
PCWorld
Accordingly, you’ll send almost all your time on the Dashboard view, which is divided into three segments. In the larger one, you’ll see a couple of sections blocked out. At the upper left is Security, with Scanner, Detection History, and Real-Time Protection as the three options and their settings:
- Scanner lets you run a quick, full, or custom scan, as well as jump directly to related settings. You can also access the scheduled scans to review what’s already set up and create new ones.
- Detection History shows quarantined items, the history of events (like detected viruses), and your allow list—items that you’ve approved as safe after initially being flagged by Malwarebytes.
- Real-Time Protection is not so much a feature, but an explanation for how Malwarebytes and how it safeguards your PC continuously.
Directly underneath the security section is one for the VPN. It puts the major controls at your fingertips, letting you quickly activate the service and change the location. You can also jump into related settings.
Along the right side is a rating for your PC’s protection level—Malwarebyte’s assessment of how close you are to utilizing the app fully. You can also check on other devices associated with your account.
PCWorld
Generally, the interface is clean and simple, as are the settings for the app and its features. The only area where you can dig in deeper are the antivirus protection settings—but as Malwarebytes rightly warns, nearly all users are better off leaving the defaults as they are.
One tip: Once the software is installed, head to Settings > Notifications, scroll down to the bottom, and turn off marketing notifications.
Virus, malware, and threat protection
Real-time protection
Malwarebytes Premium Security constantly keeps an eye out for a variety of threats. When you’re opening or adding files, using apps, or browsing the web, it’ll block viruses, ransomware, and other malware like rootkits, along with phishing attempts.
Unlike other rivals, Malwarebytes doesn’t offer a firewall. That job is left to Windows. It also doesn’t offer additional protections against dangers like DNS hijacking and webcam takeovers. As for identity protection, like dark web monitoring and insurance coverage, you must upgrade to the company’s Complete Protection plan, which costs twice as much per year.
PCWorld
If you want to adjust your real-time scanning settings, you can change what the app screens for and how stringent it is with its filters, as well as how it handles suspicious files. Malwarebytes allows you dig surprisingly deep, though only experts should get into the weeds. The overwhelming majority of users should keep the defaults as they are.
Scheduled and manual scans
At installation, Malwarebytes Premium Security automatically creates a scheduled scan for once per week. It runs whenever your system is idle, which the app calls a “smart scan.” You can edit this default or create additional scheduled scans.
For manual scans, Malwarebytes offers three types. The default is a threat scan, which checks commonly targeted areas of your PC, including things running in memory and at startup, as well as registry changes. Files stored on your PC are also looked over.

PCWorld
To fire up a quick or custom scan, you must choose Advanced Scan from the three-dot menu for the Scanner on the dashboard. Custom scans let you tweak a handful of settings related to file types and areas of your PC, as well as how to handle potentially unwanted programs and modifications to your system.
Additional features
Browser extension
Malwarebytes offers a Browser Guard extension for Chrome, Firefox, and Edge, but despite being available as a separate free download, it’s still considered a component of the Premium Security suite. After installation, it runs quietly in the background, protecting your browser from malware and scams (including credit card skimming), as well as serving as an adblocker.
VPN
Malwarebytes keeps its controls for its VPN simple rather than restrictive. Firing up the service is quick and fast, as is choosing a location for a server—and Malwarebytes lets you choose a handful of cities within countries outside of the US, more similar to a dedicated VPN.
PCWorld
You can choose servers in Albania, Australia, Austria, Belgium, Brazil, Bulgaria, Canada, Chile, Colombia, Croatia, Czech Republic, Denmark, Estonia, Finland, Germany, Greece, Hong Kong, Hungary, Indonesia, Ireland, Israel, Italy, Japan, Latvia, Mexico, Netherlands, New Zealand, Norway, Poland, Portugal, Romania, Serbia, Singapore, Slovakia, Slovenia, South Africa, Spain, Sweden, Switzerland, Thailand, UK, Ukraine, USA.
This country list isn’t as large as with some VPN services, but as mentioned above, you can generally choose between two to four cities per country. The exception is the United States, which has 18 cities available, coast to coast.
Speeds held stable when using the VPN during light testing. For US server speeds, Los Angeles (within the same state as PCWorld’s San Francisco location) showed a decrease of about 5 to 7 percent, while New York saw a roughly 26 percent drop.
Customer support
From within the app, you can jump to Malwarebytes’ user guide, support pages, and support tool. You can also use an AI chatbot for answers to your questions, or if you’re signed into your Malwarebytes account, to contact customer support—you’ll get funneled to your choice of email or live chat.
Updates and maintenance
Updates for the app and virus definitions happen automatically in the background, but you can also trigger a check manually. You’ll need to click on the person icon in the upper right of the app window, then choose About Malwarebytes and click on the Check for updates button.
PCWorld
Performance
While Malwarebytes participates in some independent benchmarking of its software, it has no current results from AV-Test and AV-Comparatives, two major organizations that test how well antivirus suites can catch threats.
Instead, the company points the curious toward AVLabs’s testing data. During the company’s September 2024 advanced in-the-wild test, Malwarebytes caught all 510 samples, with its detection rate was split between 90.98 percent pre-launch and 9.02 percent post-launch of the samples (that is, before the malware samples could activate versus after).
When asked about its participation in independent benchmarks, a representative from Malwarebytes said the company “focuses on third-party testing that is most closely aligned with the needs of customers” and that it works “with the third-party testers that are most relevant to what our customers encounter in today’s threat landscape.”
PCWorld / AVLab
During hardware performance tests on our budget Acer Aspire 3 test laptop, Malwarebytes lived up to its claims of light impact on PC resources. When left idle in the background, it had virtually no effect on typical tasks, as shown by PCMark 10’s extended benchmark. That test simulates video chatting, web browsing, gaming, image and document editing in free apps like GIMP and LibreOffice, and the like.
If you work instead on Microsoft Office documents, our UL Procyon tests showed a minimal impact on results, with a less than 3 percent difference. Similarly, our Handbrake encoding test only dipped by about 4 percent.
Even running a threat scan continuously during our benchmarks didn’t disturb these numbers much—PCMark 10 slipped by about 7 percent, Procyon by about 14 percent, and Handbrake by about 19 percent. Given how rival antivirus engines from rivals like McAfee and Norton are far greedier about system resources, Malwarebytes does distinguish itself in this regard.
Conclusion
If you dislike complicated interfaces, Malwarebytes Premium Security can be a good fit as an alternative to Windows Security—so long as you don’t mind not getting as much bang for your buck. The app is attractive and clean in its layout, and the settings are clear and straightforward. However, more seasoned security vets may have reason to hesitate on pulling the trigger, due to the relatively low amount of independent testing data available about software performance.
A relatively unknown attack method is leaving thousands of websites compromised.
Expert's Rating
Pros
- Clean, uncluttered interface
- Excellent antivirus protection
- Well-priced for its feature set
Cons
- Full scans affect PC performance when using Microsoft Office apps
- No included password manager
Our Verdict
Avast One expands upon the company’s free security suite, with upgraded defenses against online threats and additional features. You don’t get just excellent antivirus protection, but tools to safeguard your identity and privacy (including a VPN with unlimited bandwidth), as well as tune up your PC. While it lacks a password manager and parental controls, if you’re all set on those fronts, this app’s polish is hard to beat.
Price When Reviewed
This value will show the geolocated pricing text for product undefined
Best Pricing Today
You could let Windows protect your PC — it does already shield against online threats. But independent antivirus software like Avast One is better at catching viruses and malware, and wins on user friendliness, too.
Avast actually has two lines of paid products, both powered by the same antivirus engine. They have similarly clean interfaces, too. But the Avast One line focuses on identity and privacy concerns, making it arguably the better choice for most people. Life is largely conducted online these days, and staying safe is more than just thwarting malware and exploits. Phishing schemes and personal information leaked in data breaches can weaken your security, too.
Avast One lets you stay on top of these issues, which are currently unavoidable in modern life, and does so with polish.
Further reading: See our roundup of the best antivirus software for Windows to learn about competing products.
What does Avast One include?
Avast One enhances the already wide protection against online threats available in the free Essentials plan — it both upgrades existing defenses and adds new ones to the set, too.
The fundamentals include the company’s top-notch antivirus and firewall, which block malware, ransomware, malicious websites and downloads, and network intrusions. The suite also monitors for vulnerable networks, compromised applications, attempts at unauthorized access to the saved passwords in your browser, and appearances of your data on the dark web. And you get PC utilities, too: a system optimizer and software updater.

PCWorld
Upgrading to Avast One unlocks safeguards against dangers like webcam takeovers; webmail messages containing malware and phishing attempts; shady apps hunting for sensitive data (like social security numbers) on your PC; and malicious redirects for websites you visit (aka DNS hijacking).
You get strengthened identity and privacy protections as well. For starters, dark web monitoring becomes continuous in the background. The VPN puts no restrictions on bandwidth or server usage, too, and online trackers get blocked. Avast One even ties these latter two features together in a “Private Mode” setting for your default browser’s incognito tabs. When enabled, a secure VPN connection and tracking prevention will automatically kick in whenever you start an incognito session.
As for PC utilities, you get three extras: a disk cleaner, driver updater, and duplicate file finder.
Avast One does not include a password manager or parental controls. You’ll have to look elsewhere for these services, as Avast doesn’t offer them at all.
How much does Avast One cost?
If you buy a license directly from Avast, you get a discounted rate for the first year, then the standard price afterward. Plans purchased through Avast come with a 30-day money-back guarantee and are automatically enrolled in auto-renewal.
Individual plan (5 devices)
- $51 for the first year
- $110 per year thereafter
Family plan (30 devices)
- $70 for the first year
- $150 per year thereafter
For more savings on Avast One plans, you can take advantage of a special offer for PCWorld readers, which drops the cost of the first year to $33 for 5 devices and $53 for 30 devices. You can also check out our article on discounted antivirus software that explains how to get deals through online stores like Newegg.
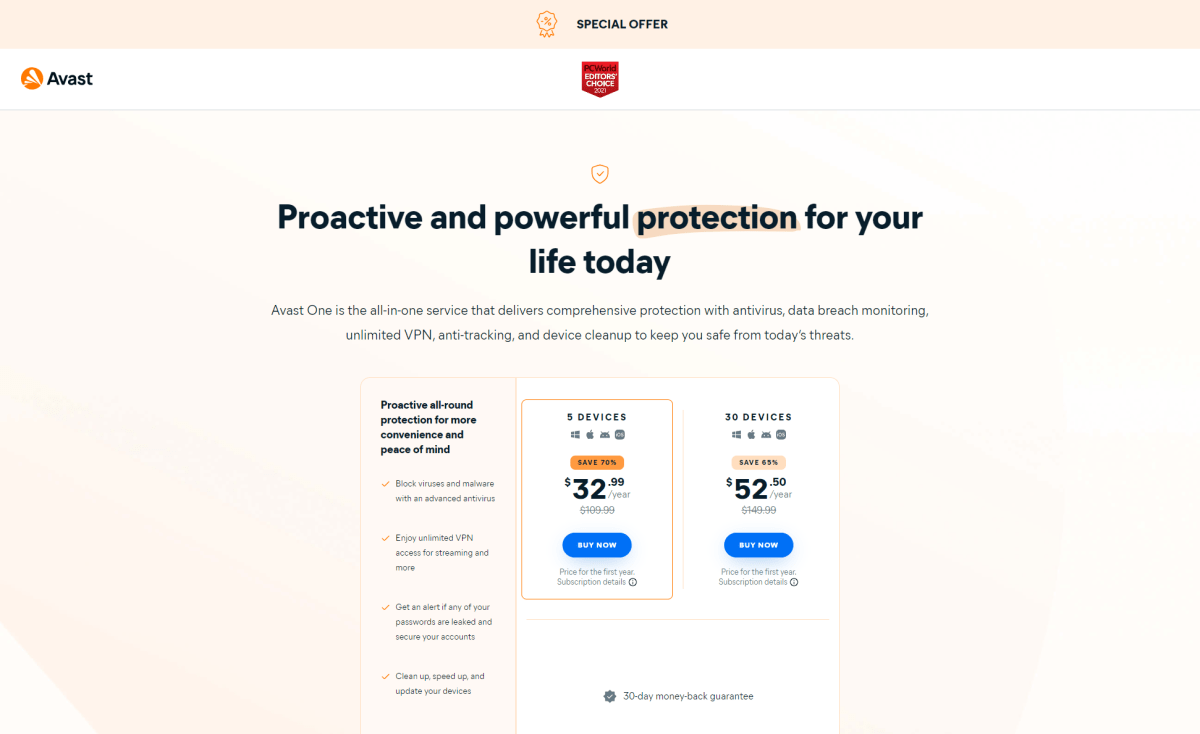
If you use our link, PCWorld readers get a special rate for Avast One plans on the Avast website.
PCWorld
You can install Avast One on PC, Android, macOS, and iOS devices. The Avast One Family plan also includes a Family Sharing feature — it allows you to invite other users with separate accounts to share in that bigger device limit.
Relative to Avast’s Premium Security plan, which has a similar number of features, you’ll pay less for Avast One in the first year (relative to the number of devices you have). However, Avast One is more expensive in subsequent years, when the cost rises to the full list price.
Key features of Avast One
Installation and user interface
After downloading Avast One from your online account dashboard and installing, you’ll see a screen asking to start a scan of your PC. You can choose to do so (which is recommended), or skip to access the app.
Avast One’s interface is light-themed, with a mix of cream, tan, and orange accents for its color theme. A simple navigation bar lives on the left side of the screen, giving quick access to the dashboard, features, notifications, and settings. The tabs aren’t labeled as clearly as in competing software — Account is where you’ll find settings and other app-related info, for example. But you can get oriented quickly, thanks to good descriptions within each section of the software.

PCWorld
Opening the app will show the Home screen, which is a dashboard that lets you run a scan, turn on the VPN, or run one of several utilities. You have just two options for scanning here, a smart scan and a deep scan. For others, you must head to the Scan Center within the Explore tab, which houses all Avast One features. There you’ll find options for Targeted Scan and Boot-Time Scan in addition to the smart and deep scan defaults. You can also create a custom scan. But unlike Avast’s Premium Security suite, Avast One’s scan settings are more limited. In fact, this difference is how the two products diverge — Avast One focuses on a simpler experience geared toward life online, while Premium Security prioritizes greater control over security on your PC.
Some users may not like the list format of the Explore tab. Though it groups the different settings by type (Device Protection, Online Privacy, Smooth Performance), those who like to see everything on a screen at once may find it frustrating to have to scroll. But each entry is labeled clearly and described well.
Surprisingly, Avast One’s attempt to upsell its more premium plans is a fairly discreet button at the top of the window, next to the minimize and exit buttons. It’s far more subtle than the approach taken by Avast’s sister company, AVG.
Virus, malware, and threat protection
Real-time protection
Avast One keeps continuous watch for real-time threats, both online and on your PC. When you browse the web, the software scans pages for malware and watches for attempts to redirect you to fake sites. The traffic going to and from your PC also get screened for suspicious activity, as do attempts to access passwords saved to your browser. If you choose to give Avast access to your webmail account (like Gmail), it will also monitor your email for phishing scams and malware.
On your PC, Avast One scans files you add or open, checks downloaded email in Microsoft Outlook or Mozilla Thunderbird for malicious attachments, and limits access to folders often target by ransomware (and any others you add to the list). It also allows only approved apps to use your webcam.
PCWorld
Avast One also tracks data breaches to see if any of your email addresses (up to five) have appeared in them. You’ll get notified whenever a match is found. Changing your password on that service or site — and any others where you might have also used it or a close variant — will be up to you to perform yourself, though. (Which is when a password manager comes in handy.)
Scheduled and manual scans
Unlike other antivirus software makers, Avast does not set up a default scheduled scan in a freshly installed app — and so Avast One lacks this feature out of the box (so to speak), too. It’s an odd move, since scheduled scans keep up the security of a PC with minimal user effort needed.
To get your PC on a regular scan schedule, you can click the Automated Smart Scan scheduling button in the Scan Center’s Scan Now tab. A smart scan checks for malware, vulnerabilities in your browser and apps, and other issues, in order to keep your PC clean overall.
Alternatively, you can create your own custom scan, which lets you pick from Deep Scan, Targeted Scan, or Quick Scan as your template. Deep scans dig thoroughly through your PC, while targeted scans examine specific files or folders. Quick scans look at commonly targeted and critical areas of your system. You can then further tweak a handful of advanced settings.

PCWorld
For both smart scan and custom scan scheduling, your options are to run the scan just once, daily, weekly, or monthly. Of the options, I recommend scheduling a quick scan or custom scan — they require no user input to complete. Smart scans ask for your input on findings for each portion of the scan before moving to the next piece.
If you prefer to manually run a scan, your options are Smart Scan, Deep Scan, Targeted Scan, Boot-Time Scan (which searches for any threats before Windows starts), and any of your custom scans. Unlike Avast’s Premium Security suite, you can only adjust your custom scan’s settings.
Firewall
Avast One’s firewall handles all traffic coming and going from your PC, completely replacing Windows own default protection. For most people, it will feel like an upgrade — the interface makes monitoring and controlling app access feel easy, rather than scary. You can clearly see which Windows programs and services are currently online and which have asked for access, as well as immediately block any suspicious items on the list.
(Windows may have come a long way with its security suite, but dig into its firewall settings, and you’ll see a mix of interfaces from different eras—and most of them are not friendly to a non-technical audience.)
The default settings are adequate for most people, though Avast One doesn’t allow much customization. You can add new apps, block apps or devices, and change three settings (two of which are related to notifications). But that covers the basics sufficiently.
Ransomware Shield
A common protection against ransomware, which encrypts files so that the attacker can extort money from victims, is to limit software access to folders often targeted by such malware. Untrusted apps can’t change or delete files in those locations. So even if you accidentally install ransomware on your system, you get an extra layer of defense.
By default, Avast One protects select Windows folders from ransomware by limiting app access to them and certain file types within.
PCWorld
By default, Avast One monitors specific file types within your Documents, Pictures, Desktop, Videos, and Music folders, including documents, pictures, and videos. You can manually add more folders and file types (using file extensions like .tiff or .pdf) to the protected list. Well-known apps (e.g. Microsoft Word or Adobe Photoshop) automatically get access, but not any others.
For a stronger defense, you can change the settings to let only approved apps through, as well as wholesale protect all files within protected folders. But be aware these tighter restrictions can require intervention on your part to ensure apps like games still function normally.
Of course, for the best protection, you should still independently keep at least one current, offline copy of your files — like on an external drive you only connect to your PC when performing the backup. Your PC could fall to ransomware, but your data won’t be lost to you.
In addition to excellent malware protection, Avast One provides tools that simplify safeguarding your privacy and keeping your PC in tip-top shape
Additional features
Browser extensions
Avast One automatically screens and blocks malicious websites, but the optional Avast Online Security & Privacy extension can help you avoid clicking on bad links to begin with. Search results in Google and Bing get visual badges that indicate if a site is safe or not. They can be easy to miss at first, though, since the icons are smaller and more subtle.
The extension will also block trackers, several ad networks, and cookie permissions. In fact, it automatically requests only necessary cookies from sites. If you’re tired of pop-ups asking you for your cookie preferences, you’ll like the last feature. Having to manually install the extension becomes worth the effort.
Network Inspector
Avast One’s Network Inspector tool can be a good way to get verification that you’ve indeed done the basics to secure your home network.
PCWorld
Hopping onto a new network can expose you to vulnerabilities — an issue that Avast tries to solve with its Network Inspector feature. You run the scanner to look for potential threats lurking on the network you’re connected to, like DNS hijacking or a weak password on a router, or a vulnerable device.
This tool has limited utility, especially for public networks. To protect yourself on such connections, the answer is simple: Use the included VPN to maintain your security and privacy. For a private network that you trust (like the one you have at home), it can help you verify your router is configured with at least basic safeguards in place.
You can adjust the settings for automatic scanning and if devices are checked for weak passwords. You can also check to your connection history to see what networks you’ve recently used.
PC utilities (Disk Cleaner, Driver Updater, and Duplicate File Finder)
Avast One unlocks three additional utilities to help keep your PC running efficiently: Disk Cleaner, Driver Updater, and Duplicate File Finder.
Disk Cleaner and Driver Updater simplify tasks you can perform yourself in Windows. Disk Cleaner lets you dump temporary files, downloads, items in the Recycle Bin, broken shortcuts, and broken registry keys to free space on your PC. Driver Updater scans your PC for outdated drivers and handles updating any that are out of date.
Both have clean interfaces that are explained with clear, simple language, which is an improvement over poking around in Windows to do the same work. Disk Cleaner also lets you see exactly which temporary files are on the chopping block, and unselect specific categories to keep them around.
Avast One’s Disk Cleanup utility helps you purge temporary files from your PC — but its easy-to-use interface is a double-edged sword.
PCWorld
There’s just one downside to these two tools — how easy it is to use them. Disk Cleaner makes deleting elements from registry too quick and simple. Fiddling with your Windows registry can cause problems, so you should always understand what you’re changing; yet with Disk Cleaner, you can wipe parts of your registry without having to know where to dig and why. Similarly, updating a driver without knowing its source can also lead to later issues, though usually not as bad as a botched registry.
Happily, Duplicate File Finder gives no reason for concern. It performed surprisingly well in my light testing — the utility could tell the difference between files that were created separately but functionally the same, and actual copies with different names. Video files created as part of my Handbrake benchmarks are the same for real-world purposes, but the tool didn’t flag them. It did catch files I copied but renamed.
Sensitive Data Shield
Many people store files containing sensitive information on their computer, such as banking details, social security numbers, paycheck info, and even passwords — and that practice can become a liability if your computer is compromised.
(Side note: Storing passwords in a document on your PC is very insecure. Use a password manager with a database stored on your computer instead — it will encrypt the data and greatly strengthen your security.)
Avast tries to shield your PC from this threat with its Sensitive Data Shield feature. It scans your PC for documents for common types of private information, then restricts access to the list of the files found. Malicious apps won’t be able to discover and extract that data. You can manually flag additional files for protection, as well as allow or block specific apps.
The feature has limited effectiveness, though. The scanner doesn’t always catch every file with sensitive info — and it only looks for .pdf, .doc, .docx, .xls, and .xlsx files. You can’t manually add files of other types, either.
VPN
Accessing Avast One’s VPN is most easily done through the main dashboard, where you can instantly flip on a connection to the preselected server. You can also tap the tile to jump to the VPN Secure Connection screen, which lets you adjust a handful of settings.
Avast One gives more granular control over automatic connection of the VPN when compared to some rivals.
PCWorld
If you choose the latter option, you can turn the VPN on and off, select a specific server, and change the connection settings. The VPN can be configured to automatically activate in certain scenarios, like when on an untrusted network (e.g., public Wi-Fi), a banking website, streaming, or shopping. It also supports peer-to-peer connections.
Additionally, you can toggle whether Avast sends autoconnection notifications, kills all internet traffic if the VPN accidentally disconnects while active, and allows your PC to see local devices (like printers) when the VPN is on. The first two features are enabled by default, while the latter is disabled.
Avast offers servers in 37 countries, which span Australia, Austria, Belgium, Brazil, Canada, Czech Republic, Denmark, Finland, France, Germany, Hungary, Iceland, Ireland, Israel, Italy, Japan, Latvia, Lithuania, Luxembourg, Malaysia, Mexico, Netherlands, New Zealand, Norway, Poland, Portugal, Republic of Singapore, South Africa, South Korea, Spain, Sweden, Switzerland, Taiwan, Turkey, UK, Ukraine, and the USA. You can choose a specific city for five countries (Australia, Canada, Germany, Spain, UK, and the USA).
Customer support
If you have questions about Avast One, you can use Avast’s support website or help forums to find answers. Customer service is also available by phone, email, or chat. The support website is the best place to start with for basic questions — there’s even a helpful user guide if you want to get properly acquainted with the software.
Updates and maintenance
Avast One automatically updates its virus definitions and the app itself in the background by default — you don’t have to check on it. However, you can change these settings so that you only get notified when updates are available, or go for complete manual control (not advisable). You can also manually check for updates in the app settings (Account > Settings > General).
Performance
Avast’s antivirus engine generally performs well in tests conducted by leading security research institutions. It detected 100 percent of the threats in AV-Test’s zero-day attack and malware evaluation for July and August 2024 (the most current results released). All 17,663 samples for recently discovered and widespread malware and 302 samples for zero-day attacks were blocked.
AV-Comparatives’ real-world test results for July and August 2024.
AV-Comparatives
In AV-Comparatives’ real-world protection test for July and August 2024, Avast also blocked 99.6 percent of the 237 test cases, with just 13 false positives. Its engine should notice and catch malicious web links, exploits (like drive-by downloads), and URLs that direct you to malware.
Avast also performed almost as well in AV-Comparatives’ September 2024 malware protection test, with a strong 99.93 percent online protection and 95.8 percent online detection rate. Its offline detection rate ranked near the top, coming in at 94.3 percent with four false positives.
For more sophisticated, targeted threats, Avast still has room to improve. It caught 12 of the 15 test cases in AV-Comparatives’ October 2024 Advanced Threat Protection Test, which involves threats like fileless attacks and malicious scripts. However, Avast caught test cases that higher performing rivals missed, suggesting that antivirus vendors are all still strengthening their protection in this area.
AV-Comparatives’ malware test results for September 2024.
AV-Comparatives
In daily use, expect Avast to have minimal impact on system resources during most typical tasks, especially when left idle in the background. When I ran PCMark 10’s Extended benchmark, which simulates web browsing, video chatting, gaming, and image and document editing in free, open-source apps, the scores remained the same as before installing Avast One. The software also had little effect on our Handbrake encoding test, which transforms a large, uncompressed video file into a smaller, compressed version. When running a deep scan continuously in the background, performance dipped by about 10 percent for both benchmarks — a modest amount compared to competitors.
The one exception to this behavior is when working on Microsoft Word, Excel, and PowerPoint documents. Avast was aggressive during in its scans when I ran UL Procyon’s Office Productivity benchmark, which focuses on Microsoft Office use. When Avast One was idle in the background, scores dropped by about 11 percent when idle. They fell by 25 percent when a deep scan was run continuously.
In the real world, these results suggest heavy Microsoft Office users on slower PCs should be strategic about the timing of scans. A full system scan scheduled for off-hours (like when you’re asleep) won’t interfere with getting work done. During active hours, you could see some performance effects when in Office apps, but not as notably.
Should you buy Avast One?
Avast One provides strong, broad defense against online threats, with features that make an upgrade from the free version (or Microsoft Defender) worthwhile. In addition to excellent malware protection, it provides tools that simplify safeguarding your privacy and keeping your PC in tip-top shape — and the interface for managing everything is clean and simple, to boot. This security suite does lack a password manager and parental controls, but if you’re set on those fronts, this app’s polish is hard to beat.
Editor’s note: Because online services are often iterative, gaining new features and performance improvements over time, this review is subject to change in order to accurately reflect the current state of the service. We’ve most recently updated it to include up-to-date protection result details.
KEY TAKEAWAYS Volexity discovered and reported a vulnerability in Fortinet's Windows VPN client, FortiClient, where user credentials remain in process memory after a user authenticates to the VPN. This vulnerability was abused by BrazenBamboo in their DEEPDATA malware. BrazenBamboo is the threat actor behind development of the LIGHTSPY malware family. LIGHTSPY variants have been discovered for all major operating systems, including iOS, and Volexity has recently discovered a new Windows variant. In July 2024, Volexity identified exploitation of a zero-day credential disclosure vulnerability in Fortinet’s Windows VPN client that allowed credentials to be stolen from the memory of the client’s process. This vulnerability was discovered while analyzing a recent sample of the DEEPDATA malware family. DEEPDATA is a modular post-exploitation tool for the Windows operating system that is used to gather a wide range of information from target devices. Analysis of the sample revealed a plugin that was designed to […]
The post BrazenBamboo Weaponizes FortiClient Vulnerability to Steal VPN Credentials via DEEPDATA appeared first on Volexity.
A vulnerability was found in ISC BIND up to 9.19.19. It has been declared as critical. This vulnerability affects unknown code of the component DNS Message Parser. The manipulation leads to resource consumption. This vulnerability was named CVE-2023-4408. The attack can be initiated remotely. There is no exploit available. It is recommended to upgrade the affected component.
A vulnerability classified as critical has been found in ISC BIND up to 9.16.45/9.16.45-S1/9.18.21/9.18.21-S1/9.19.19. Affected is an unknown function of the component DNS64. The manipulation leads to reachable assertion. This vulnerability is traded as CVE-2023-5679. It is possible to launch the attack remotely. There is no exploit available. It is recommended to upgrade the affected component.
A vulnerability was found in DNS Protocol and classified as critical. This issue affects some unknown processing of the component Closest Encloser Proof. The manipulation leads to resource consumption. The identification of this vulnerability is CVE-2023-50868. The attack may be initiated remotely. There is no exploit available.
Hijacking domains using a ‘Sitting Ducks attack’ remains an underrecognized topic in the cybersecurity community. Few threat researchers are familiar with this attack vector, and knowledge is scarce. However, the prevalence of these attacks and the risk to organizations are significant. Infoblox researchers estimate that over 1 million registered domains could be vulnerable daily. More evidence found on Sitting Ducks Attacks During a Sitting Ducks attack, the malicious actor gains control of a domain by … More
The post Cybercriminals hijack DNS to build stealth attack networks appeared first on Help Net Security.
A vulnerability, which was classified as problematic, was found in Unbound up to 1.19.0. This affects an unknown part of the component DNSSEC Validator. The manipulation leads to denial of service. This vulnerability is uniquely identified as CVE-2023-50387. Access to the local network is required for this attack. There is no exploit available. It is recommended to upgrade the affected component.
A vulnerability was found in Microsoft Windows Server 2008 R2 SP1 up to Server 2022. It has been classified as problematic. Affected is an unknown function of the component DNSSEC Verification Handler. The manipulation leads to denial of service. This vulnerability is traded as CVE-2023-50387. It is possible to launch the attack remotely. There is no exploit available. It is recommended to apply a patch to fix this issue.
A vulnerability, which was classified as critical, has been found in DNSSEC. This issue affects some unknown processing. The manipulation leads to resource consumption. The identification of this vulnerability is CVE-2023-50387. The attack may be initiated remotely. There is no exploit available.
The exploitation of the recently disclosed ‘won’t fix’ issue CVE-2024-10914 in legacy D-Link NAS devices began days after its disclosure. Days after D-Link announced it wouldn’t patch a critical vulnerability, tracked as CVE-2024-10914 (CVSS score of 9.8), in legacy D-Link NAS devices, that threat actors started attempting to exploit. The vulnerability CVE-2024-10914 is a command […]
End-of-life devices with critical flaws are already being attacked, days after the vuln was found
Multiple threat actors have been found taking advantage of an attack technique called Sitting Ducks to hijack legitimate domains for using them in phishing attacks and investment fraud schemes for years. The findings come from Infoblox, which said it identified nearly 800,000 vulnerable registered domains over the past three months, of which approximately 9% (70,000) […]
The post Experts Uncover 70,000 Hijacked Domains in Widespread ‘Sitting Ducks’ Attack Scheme appeared first on All Hacker News.
Over 1 million domains are vulnerable to “Sitting Ducks” attack, which exploits DNS misconfigurations
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens' ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
1. EXECUTIVE SUMMARY
- CVSS v4 8.6
- ATTENTION: Exploitable remotely/low attack complexity
- Vendor: Siemens
- Equipment: SCALANCE M-800 Family
- Vulnerabilities: Out-of-bounds Read, Missing Encryption of Sensitive Data, Integer Overflow or Wraparound, Uncontrolled Resource Consumption, Excessive Iteration, Use After Free, Improper Output Neutralization for Logs, Observable Discrepancy, Improper Locking, Missing Release of Resource after Effective Lifetime, Improper Input Validation, Improper Access Control, Path Traversal, Cross-site Scripting, Injection
2. RISK EVALUATION
Successful exploitation of these vulnerabilities could impact the confidentiality, integrity or availability.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
The following Siemens products are affected:
- RUGGEDCOM RM1224 LTE(4G) EU (6GK6108-4AM00-2BA2): versions prior to V8.2
- RUGGEDCOM RM1224 LTE(4G) NAM (6GK6108-4AM00-2DA2): versions prior to V8.2
- SCALANCE M804PB (6GK5804-0AP00-2AA2): versions prior to V8.2
- SCALANCE M812-1 ADSL-Router (6GK5812-1AA00-2AA2): versions prior to V8.2
- SCALANCE M812-1 ADSL-Router (6GK5812-1BA00-2AA2): versions prior to V8.2
- SCALANCE M816-1 ADSL-Router (6GK5816-1AA00-2AA2): versions prior to V8.2
- SCALANCE M816-1 ADSL-Router (6GK5816-1BA00-2AA2): versions prior to V8.2
- SCALANCE M826-2 SHDSL-Router (6GK5826-2AB00-2AB2): versions prior to V8.2
- SCALANCE M874-2 (6GK5874-2AA00-2AA2): versions prior to V8.2
- SCALANCE M874-3 3G-Router (CN) (6GK5874-3AA00-2FA2): versions prior to V8.2
- SCALANCE M874-3 (6GK5874-3AA00-2AA2): versions prior to V8.2
- SCALANCE M876-3 (6GK5876-3AA02-2BA2): versions prior to V8.2
- SCALANCE M876-3 (ROK) (6GK5876-3AA02-2EA2): versions prior to V8.2
- SCALANCE M876-4 (6GK5876-4AA10-2BA2): versions prior to V8.2
- SCALANCE M876-4 (EU) (6GK5876-4AA00-2BA2): versions prior to V8.2
- SCALANCE M876-4 (NAM) (6GK5876-4AA00-2DA2): versions prior to V8.2
- SCALANCE MUM853-1 (A1) (6GK5853-2EA10-2AA1): versions prior to V8.2
- SCALANCE MUM853-1 (B1) (6GK5853-2EA10-2BA1): versions prior to V8.2
- SCALANCE MUM853-1 (EU) (6GK5853-2EA00-2DA1): versions prior to V8.2
- SCALANCE MUM856-1 (A1) (6GK5856-2EA10-3AA1): versions prior to V8.2
- SCALANCE MUM856-1 (B1) (6GK5856-2EA10-3BA1): versions prior to V8.2
- SCALANCE MUM856-1 (CN) (6GK5856-2EA00-3FA1): versions prior to V8.2
- SCALANCE MUM856-1 (EU) (6GK5856-2EA00-3DA1): versions prior to V8.2
- SCALANCE MUM856-1 (RoW) (6GK5856-2EA00-3AA1): versions prior to V8.2
- SCALANCE S615 EEC LAN-Router (6GK5615-0AA01-2AA2): versions prior to V8.2
- SCALANCE S615 LAN-Router (6GK5615-0AA00-2AA2): versions prior to V8.2
3.2 Vulnerability Overview
3.2.1 OUT-OF-BOUNDS READ CWE-125
An out-of-bounds (OOB) memory access flaw was found in fs/f2fs/node.c in the f2fs module in the Linux kernel in versions before 5.12.0-rc4. A bounds check failure allows a local attacker to gain access to out-of-bounds memory leading to a system crash or a leak of internal kernel information. The highest threat from this vulnerability is to system availability.
CVE-2021-3506 has been assigned to this vulnerability. A CVSS v3 base score of 7.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:H).
3.2.2 MISSING ENCRYPTION OF SENSITIVE DATA CWE-311
An issue was discovered in Dnsmasq before 2.90. The default maximum EDNS.0 UDP packet size was set to 4096 but should be 1232 because of DNS Flag Day 2020.
CVE-2023-28450 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.3 INTEGER OVERFLOW OR WRAPAROUND CWE-190
dnsmasq 2.9 is vulnerable to Integer Overflow via forward_query.
CVE-2023-49441 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.4 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
Issue summary: Some non-default TLS server configurations can cause unbounded memory growth when processing TLSv1.3 sessions Impact summary: An attacker may exploit certain server configurations to trigger unbounded memory growth that would lead to a Denial of Service This problem can occur in TLSv1.3 if the non-default SSL_OP_NO_TICKET option is being used (but not if early_data support is also configured and the default anti-replay protection is in use). In this case, under certain conditions, the session cache can get into an incorrect state, and it will fail to flush properly as it fills. The session cache will continue to grow in an unbounded manner. A malicious client could deliberately create the scenario for this failure to force a Denial of Service. It may also happen by accident in normal operation. This issue only affects TLS servers supporting TLSv1.3. It does not affect TLS clients. The FIPS modules in 3.2, 3.1 and 3.0 are not affected by this issue. OpenSSL 1.0.2 is also not affected by this issue.
CVE-2024-2511 has been assigned to this vulnerability. A CVSS v3 base score of 3.7 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.5 EXCESSIVE ITERATION CWE-834
Issue summary: Checking excessively long DSA keys or parameters may be very slow. Impact summary: Applications that use the functions EVP_PKEY_param_check() or EVP_PKEY_public_check() to check a DSA public key or DSA parameters may experience long delays. Where the key or parameters that are being checked have been obtained from an untrusted source this may lead to a Denial of Service. The functions EVP_PKEY_param_check() or EVP_PKEY_public_check() perform various checks on DSA parameters. Some of those computations take a long time if the modulus (p parameter) is too large. Trying to use a very large modulus is slow and OpenSSL will not allow using public keys with a modulus which is over 10,000 bits in length for signature verification. However, the key and parameter check functions do not limit the modulus size when performing the checks. An application that calls EVP_PKEY_param_check() or EVP_PKEY_public_check() and supplies a key or parameters obtained from an untrusted source could be vulnerable to a Denial of Service attack. These functions are not called by OpenSSL itself on untrusted DSA keys so only applications that directly call these functions may be vulnerable. Also vulnerable are the OpenSSL pkey and pkeyparam command line applications when using the -check option. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are affected by this issue.
CVE-2024-4603 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.6 USE AFTER FREE CWE-416
Issue summary: Calling the OpenSSL API function SSL_free_buffers may cause memory to be accessed that was previously freed in some situations
CVE-2024-4741 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.7 IMPROPER OUTPUT NEUTRALIZATION FOR LOGS CWE-117
control channel: refuse control channel messages with nonprintable characters in them. Security scope: a malicious openvpn peer can send garbage to openvpn log, or cause high CPU load
CVE-2024-5594 has been assigned to this vulnerability. A CVSS v3 base score of 5.4 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:L).
3.2.8 OBSERVABLE DISCREPANCY CWE-203
iPerf3 before 3.17, when used with OpenSSL before 3.2.0 as a server with RSA authentication, allows a timing side channel in RSA decryption operations. This side channel could be sufficient for an attacker to recover credential plaintext. It requires the attacker to send a large number of messages for decryption, as described in "Everlasting ROBOT: the Marvin Attack" by Hubert Kario.
CVE-2024-26306 has been assigned to this vulnerability. A CVSS v3 base score of 5.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N).
3.2.9 IMPROPER LOCKING CWE-667
In the Linux kernel, the following vulnerability has been resolved: netfilter: nf_tables: release mutex after nft_gc_seq_end from abort path The commit mutex should not be released during the critical section between nft_gc_seq_begin() and nft_gc_seq_end(), otherwise, async GC worker could collect expired objects and get the released commit lock within the same GC sequence. nf_tables_module_autoload() temporarily releases the mutex to load module dependencies, then it goes back to replay the transaction again. Move it at the end of the abort phase after nft_gc_seq_end() is called.
CVE-2024-26925 has been assigned to this vulnerability. A CVSS v3 base score of 5.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H).
3.2.10 MISSING RELEASE OF RESOURCE AFTER EFFECTIVE LIFETIME CWE-772
OpenVPN from 2.6.0 through 2.6.10 in a server role accepts multiple exit notifications from authenticated clients which will extend the validity of a closing session
CVE-2024-28882 has been assigned to this vulnerability. A CVSS v3 base score of 6.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:N).
3.2.11 IMPROPER INPUT VALIDATION CWE-20
Affected devices do not properly validate input in configuration fields of the iperf functionality. This could allow an unauthenticated remote attacker to execute arbitrary code on the device.
CVE-2024-50557 has been assigned to this vulnerability. A CVSS v3 base score of 7.2 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H).
A CVSS v4 score has also been calculated for CVE-2024-50557. A base score of 8.6 has been calculated; the CVSS vector string is (CVSS4.0/AV:N/AC:L/AT:N/PR:H/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N).
3.2.12 IMPROPER ACCESS CONTROL CWE-284
Affected devices improperly manage access control for read-only users. This could allow an attacker to cause a temporary denial of service condition.
CVE-2024-50558 has been assigned to this vulnerability. A CVSS v3 base score of 4.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L).
A CVSS v4 score has also been calculated for CVE-2024-50558. A base score of 5.3 has been calculated; the CVSS vector string is (CVSS4.0/AV:N/AC:L/AT:N/PR:L/UI:N/VC:N/VI:N/VA:L/SC:N/SI:N/SA:N).
3.2.13 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
Affected devices do not properly validate the filenames of the certificate. This could allow an authenticated remote attacker to append arbitrary values which will lead to compromise of integrity of the system.
CVE-2024-50559 has been assigned to this vulnerability. A CVSS v3 base score of 4.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N).
A CVSS v4 score has also been calculated for CVE-2024-50559. A base score of 5.1 has been calculated; the CVSS vector string is (CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:A/VC:N/VI:L/VA:N/SC:N/SI:N/SA:N).
3.2.14 IMPROPER INPUT VALIDATION CWE-20
Affected devices truncates usernames longer than 15 characters when accessed via SSH or Telnet. This could allow an attacker to compromise system integrity.
CVE-2024-50560 has been assigned to this vulnerability. A CVSS v3 base score of 3.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:N/I:L/A:N).
A CVSS v4 score has also been calculated for CVE-2024-50560. A base score of 2.3 has been calculated; the CVSS vector string is (CVSS:4.0/AV:N/AC:H/AT:P/PR:L/UI:N/VC:N/VI:L/VA:N/SC:N/SI:N/SA:N).
3.2.15 IMPROPER NEUTRALIZATION OF INPUT DURING WEB PAGE GENERATION ('CROSS-SITE SCRIPTING') CWE-79
Affected devices do not properly sanitize the filenames before uploading. This could allow an authenticated remote attacker to compromise of integrity of the system.
CVE-2024-50561 has been assigned to this vulnerability. A CVSS v3 base score of 4.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N).
A CVSS v4 score has also been calculated for CVE-2024-50561. A base score of 5.1 has been calculated; the CVSS vector string is (CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:A/VC:N/VI:L/VA:N/SC:N/SI:N/SA:N).
3.2.16 IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS IN OUTPUT USED BY A DOWNSTREAM COMPONENT ('INJECTION') CWE-74
Affected devices do not properly sanitize an input field. This could allow an authenticated remote attacker with administrative privileges to inject code or spawn a system root shell.
CVE-2024-50572 has been assigned to this vulnerability. A CVSS v3 base score of 7.2 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H).
A CVSS v4 score has also been calculated for CVE-2024-50572. A base score of 8.6 has been calculated; the CVSS vector string is (CVSS:4.0/AV:N/AC:L/AT:N/PR:H/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing, Communications
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Siemens reported these vulnerabilities to CISA.
4. MITIGATIONS
Siemens has identified the following specific workarounds and mitigations users can apply to reduce risk:
- All affected products: Update to V8.2 or later version
As a general security measure, Siemens recommends protecting network access to devices with appropriate mechanisms. To operate the devices in a protected IT environment, Siemens recommends configuring the environment according to Siemens' operational guidelines for industrial security and following recommendations in the product manuals.
Additional information on industrial security by Siemens can be found on the Siemens industrial security webpage
For more information see the associated Siemens security advisory SSA-354112 in HTML and CSAF.
CISA recommends users take defensive measures to minimize the risk of exploitation of these vulnerabilities, such as:
- Minimize network exposure for all control system devices and/or systems, ensuring they are not accessible from the internet.
- Locate control system networks and remote devices behind firewalls and isolating them from business networks.
- When remote access is required, use more secure methods, such as Virtual Private Networks (VPNs). Recognize VPNs may have vulnerabilities, should be updated to the most recent version available, and are only as secure as the connected devices.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov in the technical information paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
No known public exploitation specifically targeting these vulnerabilities has been reported to CISA at this time.
5. UPDATE HISTORY
- November 14, 2024: Initial Publication
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens' ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
1. EXECUTIVE SUMMARY
- CVSS v3 9.9
- ATTENTION: Exploitable remotely/low attack complexity/public exploits are available/known public exploitation
- Vendor: Siemens
- Equipment: SINEC INS
- Vulnerabilities: Improper Authentication, Out-of-bounds Write, Inefficient Regular Expression Complexity, Excessive Iteration, Reachable Assertion, Uncontrolled Resource Consumption, Improper Input Validation, Improper Check for Unusual or Exceptional Conditions, Memory Allocation with Excessive Size Value, Heap-based Buffer Overflow, Missing Encryption of Sensitive Data, Path Traversal, Incorrect Permission Assignment for Critical Resource, Exposure of Sensitive Information to an Unauthorized Actor, Covert Timing Channel, Truncation of Security-relevant Information, Integer Overflow or Wraparound, Use After Free, Code Injection, Path Traversal: 'dir/../../filename', Execution with Unnecessary Privileges, Server-Side Request Forgery (SSRF), OS Command Injection, HTTP Request/Response Smuggling, Use of Hard-coded Cryptographic Key, Insufficient Session Expiration
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow an unauthenticated attacker cause a denial-of-service condition, bypass permissions, access data they shouldn't have access to, or run arbitrary code.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
The following Siemens products are affected:
- SINEC INS: versions prior to V1.0 SP2 Update 3
3.2 Vulnerability Overview
3.2.1 IMPROPER AUTHENTICATION CWE-287
The AES-SIV cipher implementation contains a bug that causes it to ignore empty associated data entries which are unauthenticated as a consequence. Applications that use the AES-SIV algorithm and want to authenticate empty data entries as associated data can be mislead by removing adding or reordering such empty entries as these are ignored by the OpenSSL implementation. The AES-SIV algorithm allows for authentication of multiple associated data entries along with the encryption. To authenticate empty data the application has to call EVP_EncryptUpdate() (or EVP_CipherUpdate()) with NULL pointer as the output buffer and 0 as the input buffer length. The AES-SIV implementation in OpenSSL just returns success for such a call instead of performing the associated data authentication operation. The empty data thus will not be authenticated.
CVE-2023-2975 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N).
3.2.2 OUT-OF-BOUNDS WRITE CWE-787
The code that processes control channel messages sent to named calls certain functions recursively during packet parsing. Recursion depth is only limited by the maximum accepted packet size; depending on the environment, this may cause the packet-parsing code to run out of available stack memory, causing named to terminate unexpectedly. Since each incoming control channel message is fully parsed before its contents are authenticated, exploiting this flaw does not require the attacker to hold a valid RNDC key; only network access to the control channel's configured TCP port is necessary. This issue affects BIND 9 versions 9.2.0 through 9.16.43, 9.18.0 through 9.18.18, 9.19.0 through 9.19.16, 9.9.3-S1 through 9.16.43-S1, and 9.18.0-S1 through 9.18.18-S1.
CVE-2023-3341 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.3 INEFFICIENT REGULAR EXPRESSION COMPLEXITY CWE-1333
Applications that use the functions DH_check(), DH_check_ex() or EVP_PKEY_param_check() to check a DH key or DH parameters may experience long delays. Where the key or parameters that are being checked have been obtained from an untrusted source this may lead to a denial of service. The function DH_check() performs various checks on DH parameters. One of those checks confirms that the modulus ('p' parameter) is not too large. Trying to use a very large modulus is slow and OpenSSL will not normally use a modulus which is over 10,000 bits in length. However the DH_check() function checks numerous aspects of the key or parameters that have been supplied. Some of those checks use the supplied modulus value even if it has already been found to be too large. An application that calls DH_check() and supplies a key or parameters obtained from an untrusted source could be vulnerable to a denial-of-service attack. The function DH_check() is itself called by a number of other OpenSSL functions. An application calling any of those other functions may similarly be affected. The other functions affected by this are DH_check_ex() and EVP_PKEY_param_check(). Also vulnerable are the OpenSSL dhparam and pkeyparam command line applications when using the '-check' option. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are not affected by this issue.
CVE-2023-3446 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.4 EXCESSIVE ITERATION CWE-834
Applications that use the functions DH_check(), DH_check_ex() or EVP_PKEY_param_check() to check a DH key or DH parameters may experience long delays. Where the key or parameters that are being checked have been obtained from an untrusted source this may lead to a denial of service. The function DH_check() performs various checks on DH parameters. After fixing CVE-2023-3446 it was discovered that a large q parameter value can also trigger an overly long computation during some of these checks. A correct q value, if present, cannot be larger than the modulus p parameter, thus it is unnecessary to perform these checks if q is larger than p. An application that calls DH_check() and supplies a key or parameters obtained from an untrusted source could be vulnerable to a denial-of-service attack. The function DH_check() is itself called by a number of other OpenSSL functions. An application calling any of those other functions may similarly be affected. The other functions affected by this are DH_check_ex() and EVP_PKEY_param_check(). Also vulnerable are the OpenSSL dhparam and pkeyparam command line applications when using the "-check" option. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are not affected by this issue.
CVE-2023-3817 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.5 REACHABLE ASSERTION CWE-617
A flaw in the networking code handling DNS-over-TLS queries may cause named to terminate unexpectedly due to an assertion failure. This happens when internal data structures are incorrectly reused under significant DNS-over-TLS query load. This issue affects BIND 9 versions 9.18.0 through 9.18.18 and 9.18.11-S1 through 9.18.18-S1.
CVE-2023-4236 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.6 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
The DNS message parsing code in named includes a section whose computational complexity is overly high. It does not cause problems for typical DNS traffic, but crafted queries and responses may cause excessive CPU load on the affected named instance by exploiting this flaw. This issue affects both authoritative servers and recursive resolvers. This issue affects BIND 9 versions 9.0.0 through 9.16.45, 9.18.0 through 9.18.21, 9.19.0 through 9.19.19, 9.9.3-S1 through 9.11.37-S1, 9.16.8-S1 through 9.16.45-S1, and 9.18.11-S1 through 9.18.21-S1.
CVE-2023-4408 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.7 IMPROPER INPUT VALIDATION CWE-20
The POLY1305 MAC (message authentication code) implementation contains a bug that might corrupt the internal state of applications on the Windows 64 platform when running on newer X86_64 processors supporting the AVX512-IFMA instructions. If in an application that uses the OpenSSL library an attacker can influence whether the POLY1305 MAC algorithm is used, the application state might be corrupted with various application dependent consequences. The POLY1305 MAC (message authentication code) implementation in OpenSSL does not save the contents of non-volatile XMM registers on Windows 64 platform when calculating the MAC of data larger than 64 bytes. Before returning to the caller all the XMM registers are set to zero rather than restoring their previous content. The vulnerable code is used only on newer x86_64 processors supporting the AVX512-IFMA instructions. The consequences of this kind of internal application state corruption can be various - from no consequences, if the calling application does not depend on the contents of non-volatile XMM registers at all, to the worst consequences, where the attacker could get complete control of the application process. However given the contents of the registers are just zeroized so the attacker cannot put arbitrary values inside, the most likely consequence, if any, would be an incorrect result of some application dependent calculations or a crash leading to a denial of service. The POLY1305 MAC algorithm is most frequently used as part of the CHACHA20-POLY1305 AEAD (authenticated encryption with associated data) algorithm. The most common usage of this AEAD cipher is with TLS protocol versions 1.2 and 1.3 and a malicious client can influence whether this AEAD cipher is used by the server. This implies that server applications using OpenSSL can be potentially impacted. However we are currently not aware of any concrete application that would be affected by this issue therefore we consider this a Low severity security issue. As a workaround the AVX512-IFMA instructions support can be disabled at runtime by setting the environment variable OPENSSL_ia32cap: OPENSSL_ia32cap=:~0x200000 The FIPS provider is not affected by this issue.
CVE-2023-4807 has been assigned to this vulnerability. A CVSS v3 base score of 7.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.8 REACHABLE ASSERTION CWE-617
A flaw in query-handling code can cause named to exit prematurely with an assertion failure when: - nxdomain-redirect is configured, and - the resolver receives a PTR query for an RFC 1918 address that would normally result in an authoritative NXDOMAIN response. This issue affects BIND 9 versions 9.12.0 through 9.16.45, 9.18.0 through 9.18.21, 9.19.0 through 9.19.19, 9.16.8-S1 through 9.16.45-S1, and 9.18.11-S1 through 9.18.21-S1.
CVE-2023-5517 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.9 IMPROPER CHECK FOR UNUSUAL OR EXCEPTIONAL CONDITIONS CWE-754
Applications that use the functions DH_generate_key() to generate an X9.42 DH key may experience long delays. Likewise, applications that use DH_check_pub_key(), DH_check_pub_key_ex() or EVP_PKEY_public_check() to check an X9.42 DH key or X9.42 DH parameters may experience long delays. Where the key or parameters that are being checked have been obtained from an untrusted source this may lead to a denial of service. While DH_check() performs all the necessary checks (as of CVE-2023-3817), DH_check_pub_key() doesn't make any of these checks, and is therefore vulnerable for excessively large P and Q parameters. Likewise, while DH_generate_key() performs a check for an excessively large P, it doesn't check for an excessively large Q. An application that calls DH_generate_key() or DH_check_pub_key() and supplies a key or parameters obtained from an untrusted source could be vulnerable to a denial-of-service attack. DH_generate_key() and DH_check_pub_key() are also called by a number of other OpenSSL functions. An application calling any of those other functions may similarly be affected. The other functions affected by this are DH_check_pub_key_ex(), EVP_PKEY_public_check(), and EVP_PKEY_generate(). Also vulnerable are the OpenSSL pkey command line application when using the "-pubcheck" option, as well as the OpenSSL genpkey command line application. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are not affected by this issue.
CVE-2023-5678 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.10 REACHABLE ASSERTION CWE-617
A bad interaction between DNS64 and serve-stale may cause named to crash with an assertion failure during recursive resolution, when both of these features are enabled. This issue affects BIND 9 versions 9.16.12 through 9.16.45, 9.18.0 through 9.18.21, 9.19.0 through 9.19.19, 9.16.12-S1 through 9.16.45-S1, and 9.18.11-S1 through 9.18.21-S1.
CVE-2023-5679 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.11 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
A bad interaction between DNS64 and serve-stale may cause named to crash with an assertion failure during recursive resolution, when both of these features are enabled. This issue affects BIND 9 versions 9.16.12 through 9.16.45, 9.18.0 through 9.18.21, 9.19.0 through 9.19.19, 9.16.12-S1 through 9.16.45-S1, and 9.18.11-S1 through 9.18.21-S1.
CVE-2023-5680 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.12 OUT-OF-BOUNDS WRITE CWE-787
The POLY1305 MAC (message authentication code) implementation contains a bug that might corrupt the internal state of applications running on PowerPC CPU based platforms if the CPU provides vector instructions. If an attacker can influence whether the POLY1305 MAC algorithm is used, the application state might be corrupted with various application dependent consequences. The POLY1305 MAC (message authentication code) implementation in OpenSSL for PowerPC CPUs restores the contents of vector registers in a different order than they are saved. Thus the contents of some of these vector registers are corrupted when returning to the caller. The vulnerable code is used only on newer PowerPC processors supporting the PowerISA 2.07 instructions. The consequences of this kind of internal application state corruption can be various - from no consequences, if the calling application does not depend on the contents of non-volatile XMM registers at all, to the worst consequences, where the attacker could get complete control of the application process. However unless the compiler uses the vector registers for storing pointers, the most likely consequence, if any, would be an incorrect result of some application dependent calculations or a crash leading to a denial of service. The POLY1305 MAC algorithm is most frequently used as part of the CHACHA20-POLY1305 AEAD (authenticated encryption with associated data) algorithm. The most common usage of this AEAD cipher is with TLS protocol versions 1.2 and 1.3. If this cipher is enabled on the server a malicious client can influence whether this AEAD cipher is used. This implies that TLS server applications using OpenSSL can be potentially impacted.
CVE-2023-6129 has been assigned to this vulnerability. A CVSS v3 base score of 6.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:L/A:H).
3.2.13 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
Checking excessively long invalid RSA public keys may take a long time. Applications that use the function EVP_PKEY_public_check() to check RSA public keys may experience long delays. Where the key that is being checked has been obtained from an untrusted source this may lead to a denial of service. When function EVP_PKEY_public_check() is called on RSA public keys, a computation is done to confirm that the RSA modulus, n, is composite. For valid RSA keys, n is a product of two or more large primes and this computation completes quickly. However, if n is an overly large prime, then this computation would take a long time. An application that calls EVP_PKEY_public_check() and supplies an RSA key obtained from an untrusted source could be vulnerable to a denial-of-service attack. The function EVP_PKEY_public_check() is not called from other OpenSSL functions however it is called from the OpenSSL pkey command line application. For that reason that application is also vulnerable if used with the '-pubin' and '-check' options on untrusted data. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are affected by this issue.
CVE-2023-6237 has been assigned to this vulnerability. A CVSS v3 base score of 5.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.14 MEMORY ALLOCATION WITH EXCESSIVE SIZE VALUE CWE-789
To keep its cache database efficient, named running as a recursive resolver occasionally attempts to clean up the database. It uses several methods, including some that are asynchronous: a small chunk of memory pointing to the cache element that can be cleaned up is first allocated and then queued for later processing. It was discovered that if the resolver is continuously processing query patterns triggering this type of cache-database maintenance, named may not be able to handle the cleanup events in a timely manner. This in turn enables the list of queued cleanup events to grow infinitely large over time, allowing the configured max-cache-size limit to be significantly exceeded. This issue affects BIND 9 versions 9.16.0 through 9.16.45 and 9.16.8-S1 through 9.16.45-S1.
CVE-2023-6516 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.15 HEAP-BASED BUFFER OVERFLOW CWE-122
A vulnerability was found in SQLite SQLite3 up to 3.43.0 and classified as critical. This issue affects the function sessionReadRecord of the file ext/session/sqlite3session.c of the component make all test Handler. The manipulation leads to heap-based buffer overflow. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-248999.
CVE-2023-7104 has been assigned to this vulnerability. A CVSS v3 base score of 5.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L).
3.2.16 MISSING ENCRYPTION OF SENSITIVE DATA CWE-311
The use of Module._load() can bypass the policy mechanism and require modules outside of the policy.json definition for a given module. This vulnerability affects all users using the experimental policy mechanism in all active release lines: 16.x, 18.x and, 20.x. Note that at the time this CVE was issued, the policy was an experimental feature of Node.js.
CVE-2023-32002 has been assigned to this vulnerability. A CVSS v3 base score of 9.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
3.2.17 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
fs.mkdtemp() and fs.mkdtempSync() can be used to bypass the permission model check using a path traversal attack. This flaw arises from a missing check in the fs.mkdtemp() API and the impact is a malicious actor could create an arbitrary directory. This vulnerability affects all users using the experimental permission model in Node.js 20. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-32003 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N).
3.2.18 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
A vulnerability has been discovered in Node.js version 20, specifically within the experimental permission model. This flaw relates to improper handling of buffers in file system APIs causing a traversal path to bypass when verifying file permissions. This vulnerability affects all users using the experimental permission model in Node.js 20. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-32004 has been assigned to this vulnerability. A CVSS v3 base score of 8.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.19 INCORRECT PERMISSION ASSIGNMENT FOR CRITICAL RESOURCE CWE-732
A vulnerability has been identified in Node.js version 20, affecting users of the experimental permission model when the --allow-fs-read flag is used with a non-* argument. This flaw arises from an inadequate permission model that fails to restrict file stats through the fs.statfs API. As a result, malicious actors can retrieve stats from files that they do not have explicit read access to. This vulnerability affects all users using the experimental permission model in Node.js 20. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-32005 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N).
3.2.20 MISSING ENCRYPTION OF SENSITIVE DATA CWE-311
The use of module.constructor.createRequire() can bypass the policy mechanism and require modules outside of the policy.json definition for a given module. This vulnerability affects all users using the experimental policy mechanism in all active release lines: 16.x, 18.x, and, 20.x. Note that at the time this CVE was issued, the policy was an experimental feature of Node.js.
CVE-2023-32006 has been assigned to this vulnerability. A CVSS v3 base score of 8.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.21 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
The use of the deprecated API process.binding() can bypass the permission model through path traversal. This vulnerability affects all users using the experimental permission model in Node.js 20.x. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-32558 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N).
3.2.22 MISSING ENCRYPTION OF SENSITIVE DATA CWE-311
A privilege escalation vulnerability exists in the experimental policy mechanism in all active release lines: 16.x, 18.x and, 20.x. The use of the deprecated API process.binding() can bypass the policy mechanism by requiring internal modules and eventually take advantage of process.binding('spawn_sync') run arbitrary code, outside of the limits defined in a policy.json file. Note that at the time this CVE was issued, the policy was an experimental feature of Node.js.
CVE-2023-32559 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.23 IMPROPER INPUT VALIDATION CWE-20
When the Node.js policy feature checks the integrity of a resource against a trusted manifest, the application can intercept the operation and return a forged checksum to the node's policy implementation, thus effectively disabling the integrity check. This vulnerability affects all users using the experimental policy mechanism in all active release lines: 18.x and, 20.x. At the time this CVE was issued, the policy mechanism was an experimental feature of Node.js.
CVE-2023-38552 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N).
3.2.24 IMPROPER INPUT VALIDATION CWE-20
A previously disclosed vulnerability (CVE-2023-30584) was patched insufficiently in commit 205f1e6. The new path traversal vulnerability arises because the implementation does not protect itself against the application overwriting built-in utility functions with user-defined implementations. Note that at the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-39331 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N).
3.2.25 IMPROPER INPUT VALIDATION CWE-20
Various node:fs functions allow specifying paths as either strings or Uint8Array objects. In Node.js environments, the Buffer class extends the Uint8Array class. Node.js prevents path traversal through strings (see CVE-2023-30584) and Buffer objects (see CVE-2023-32004), but not through non-Buffer Uint8Array objects. This is distinct from CVE-2023-32004 which only referred to Buffer objects. However, the vulnerability follows the same pattern using Uint8Array instead of Buffer. At the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2023-39332 has been assigned to this vulnerability. A CVSS v3 base score of 9.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
3.2.26 IMPROPER INPUT VALIDATION CWE-20
Maliciously crafted export names in an imported WebAssembly module can inject JavaScript code. The injected code may be able to access data and functions that the WebAssembly module itself does not have access to, similar to as if the WebAssembly module was a JavaScript module.
CVE-2023-39333 has been assigned to this vulnerability. A CVSS v3 base score of 6.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N).
3.2.27 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
CVE-2023-44487 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.28 EXPOSURE OF SENSITIVE INFORMATION TO AN UNAUTHORIZED ACTOR CWE-200
Undici is an HTTP/1.1 client written from scratch for Node.js. Prior to version 5.26.2, Undici already cleared authorization headers on cross-origin redirects, but did not clear cookie headers. By design, cookie headers are forbidden request headers, disallowing them to be set in RequestInit.headers in browser environments. Since undici handles headers more liberally than the spec, there was a disconnect from the assumptions the spec made, and undici's implementation of fetch. As such this may lead to accidental leakage of cookie to a third-party site or a malicious attacker who can control the redirection target (ie. an open redirector) to leak the cookie to the third party site. This was patched in version 5.26.2. There are no known workarounds.
CVE-2023-45143 has been assigned to this vulnerability. A CVSS v3 base score of 3.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:U/C:L/I:L/A:L).
3.2.29 COVERT TIMING CHANNEL CWE-385
Node.js versions which bundle an unpatched version of OpenSSL or run against a dynamically linked version of OpenSSL which are unpatched are vulnerable to the Marvin Attack - https://people.redhat.com/~hkario/marvin/, if PCKS #1 v1.5 padding is allowed when performing RSA descryption using a private key.
CVE-2023-46809 has been assigned to this vulnerability. A CVSS v3 base score of 7.4 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N).
3.2.30 OUT-OF-BOUNDS WRITE CWE-787
A vulnerability was found in perl 5.30.0 through 5.38.0. This issue occurs when a crafted regular expression is compiled by perl, which can allow an attacker controlled byte buffer overflow in a heap allocated buffer.
CVE-2023-47038 has been assigned to this vulnerability. A CVSS v3 base score of 7.0 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.31 HEAP-BASED BUFFER OVERFLOW CWE-122
This security issue occurs while Perl for Windows relies on the system path environment variable to find the shell (cmd.exe). When running an executable that uses the Windows Perl interpreter, Perl attempts to find and execute cmd.exe within the operating system. However, due to path search order issues, Perl initially looks for cmd.exe in the current working directory. This flaw allows an attacker with limited privileges to placecmd.exe in locations with weak permissions, such as C:\ProgramData. By doing so, arbitrary code can be executed when an administrator attempts to use this executable from these compromised locations.
CVE-2023-47039 has been assigned to this vulnerability. A CVSS v3 base score of 7.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.32 IMPROPER INPUT VALIDATION CWE-20
In Perl before 5.38.2, S_parse_uniprop_string in regcomp.c can write to unallocated space because a property name associated with a \p{...} regular expression construct is mishandled. The earliest affected version is 5.30.0.
CVE-2023-47100 has been assigned to this vulnerability. A CVSS v3 base score of 9.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
3.2.33 TRUNCATION OF SECURITY-RELEVANT INFORMATION CWE-222
The SSH transport protocol with certain OpenSSH extensions, found in OpenSSH before 9.6 and other products, allows remote attackers to bypass integrity checks such that some packets are omitted (from the extension negotiation message), and a client and server may consequently end up with a connection for which some security features have been downgraded or disabled, aka a Terrapin attack. This occurs because the SSH Binary Packet Protocol (BPP), implemented by these extensions, mishandles the handshake phase and mishandles use of sequence numbers. For example, there is an effective attack against SSH's use of ChaCha20-Poly1305 (and CBC with Encrypt-then-MAC). The bypass occurs in [email protected] and (if CBC is used) the [email protected] MAC algorithms. This also affects Maverick Synergy Java SSH API before 3.1.0-SNAPSHOT, Dropbear through 2022.83, Ssh before 5.1.1 in Erlang/OTP, PuTTY before 0.80, AsyncSSH before 2.14.2, golang.org/x/crypto before 0.17.0, libssh before 0.10.6, libssh2 through 1.11.0, Thorn Tech SFTP Gateway before 3.4.6, Tera Term before 5.1, Paramiko before 3.4.0, jsch before 0.2.15, SFTPGo before 2.5.6, Netgate pfSense Plus through 23.09.1, Netgate pfSense CE through 2.7.2, HPN-SSH through 18.2.0, ProFTPD before 1.3.8b (and before1.3.9rc2), ORYX CycloneSSH before 2.3.4, NetSarang XShell 7 before Build 0144, CrushFTP before 10.6.0, ConnectBot SSH library before 2.2.22, Apache MINA sshd through 2.11.0, sshj through 0.37.0, TinySSH through 20230101, trilead-ssh2 6401, the net-ssh gem 7.2.0 for Ruby, the mscdex ssh2 module before 1.15.0 for Node.js, the thrussh library before 0.35.1 for Rust, and the Russh crate before 0.40.2 for Rust; and there could be effects on Bitvise SSH through 9.31.
CVE-2023-48795 has been assigned to this vulnerability. A CVSS v3 base score of 5.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:H/A:N).
3.2.34 IMPROPER INPUT VALIDATION CWE-20
Certain DNSSEC aspects of the DNS protocol (in RFC 4033, 4034, 4035, 6840, and related RFCs) allow remote attackers to cause a denial of service (CPU consumption) via one or more DNSSEC responses, aka the "KeyTrap" issue. One of the concerns is that, when there is a zone with many DNSKEY and RRSIG records, the protocol specification implies that an algorithm must evaluate all combinations of DNSKEY and RRSIG records.
CVE-2023-50387 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.35 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
The Closest Enclosure Proof aspect of the DNS protocol (in RFC 5155 when RFC 9276 guidance is skipped) allows remote attackers to cause a denial of service (CPU consumption for SHA-1 computations) via DNSSEC responses in a random subdomain attack, aka the "NSEC3" issue. The RFC 5155 specification implies that an algorithm must perform thousands of iterations of a hash function in certain situations.
CVE-2023-50868 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.36 INTEGER OVERFLOW OR WRAPAROUND CWE-190
UTF32Encoding.cpp in POCO has a Poco::UTF32Encoding integer overflow and resultant stack buffer overflow because Poco::UTF32Encoding::convert() and Poco::UTF32::queryConvert() may return a negative integer if a UTF-32 byte sequence evaluates to a value of 0x80000000 or higher. This is fixed in 1.11.8p2, 1.12.5p2, and 1.13.0.
CVE-2023-52389 has been assigned to this vulnerability. A CVSS v3 base score of 9.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
3.2.37 USE AFTER FREE CWE-416
A heap use-after-free issue has been identified in SQLite in the jsonParseAddNodeArray() function in sqlite3.c. This flaw allows a local attacker to leverage a victim to pass specially crafted malicious input to the application, potentially causing a crash and leading to a denial of service.
CVE-2024-0232 has been assigned to this vulnerability. A CVSS v3 base score of 4.7 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:H/PR:N/UI:R/S:U/C:N/I:N/A:H).
3.2.38 IMPROPER INPUT VALIDATION CWE-20
Processing a maliciously formatted PKCS12 file may lead OpenSSL to crash leading to a potential denial-of-service attack. Applications loading files in the PKCS12 format from untrusted sources might terminate abruptly. A file in PKCS12 format can contain certificates and keys and may come from an untrusted source. The PKCS12 specification allows certain fields to be NULL, but OpenSSL does not correctly check for this case. This can lead to a NULL pointer dereference that results in OpenSSL crashing. If an application processes PKCS12 files from an untrusted source using the OpenSSL APIs then that application will be vulnerable to this issue. OpenSSL APIs that are vulnerable to this are: PKCS12_parse(), PKCS12_unpack_p7data(), PKCS12_unpack_p7encdata(), PKCS12_unpack_authsafes() and PKCS12_newpass(). We have also fixed a similar issue in SMIME_write_PKCS7(). However since this function is related to writing data we do not consider it security significant. The FIPS modules in 3.2, 3.1 and 3.0 are not affected by this issue.
CVE-2024-0727 has been assigned to this vulnerability. A CVSS v3 base score of 5.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H).
3.2.39 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
Some non-default TLS server configurations can cause unbounded memory growth when processing TLSv1.3 sessions. An attacker may exploit certain server configurations to trigger unbounded memory growth that would lead to a denial of service. This problem can occur in TLSv1.3 if the non-default SSL_OP_NO_TICKET option is being used (but not if early_data support is also configured and the default anti-replay protection is in use). In this case, under certain conditions, the session cache can get into an incorrect state and it will fail to flush properly as it fills. The session cache will continue to grow in an unbounded manner. A malicious client could deliberately create the scenario for this failure to force a denial of service. It may also happen by accident in normal operation. This issue only affects TLS servers supporting TLSv1.3. It does not affect TLS clients. The FIPS modules in 3.2, 3.1 and 3.0 are not affected by this issue. OpenSSL 1.0.2 is also not affected by this issue.
CVE-2024-2511 has been assigned to this vulnerability. A CVSS v3 base score of 3.7 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.40 USE AFTER FREE CWE-416
Calling the OpenSSL API function SSL_free_buffers may cause memory to be accessed that was previously freed in some situations
CVE-2024-4741 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.41 EXPOSURE OF SENSITIVE INFORMATION TO AN UNAUTHORIZED ACTOR CWE-200
Calling the OpenSSL API function SSL_select_next_proto with an empty supported client protocols buffer may cause a crash or memory contents to be sent to the peer. A buffer overread can have a range of potential consequences such as unexpected application behavior or a crash. In particular this issue could result in up to 255 bytes of arbitrary private data from memory being sent to the peer leading to a loss of confidentiality. However, only applications that directly call the SSL_select_next_proto function with a 0 length list of supported client protocols are affected by this issue. This would normally never be a valid scenario and is typically not under attacker control but may occur by accident in the case of a configuration or programming error in the calling application. The OpenSSL API function SSL_select_next_proto is typically used by TLS applications that support ALPN (Application Layer Protocol Negotiation) or NPN (Next Protocol Negotiation). NPN is older, was never standardized and is deprecated in favor of ALPN. We believe that ALPN is significantly more widely deployed than NPN. The SSL_select_next_proto function accepts a list of protocols from the server and a list of protocols from the client and returns the first protocol that appears in the server list that also appears in the client list. In the case of no overlap between the two lists it returns the first item in the client list. In either case it will signal whether an overlap between the two lists was found. In the case where SSL_select_next_proto is called with a zero length client list it fails to notice this condition and returns the memory immediately following the client list pointer (and reports that there was no overlap in the lists). This function is typically called from a server side application callback for ALPN or a client side application callback for NPN. In the case of ALPN the list of protocols supplied by the client is guaranteed by libssl to never be zero in length. The list of server protocols comes from the application and should never normally be expected to be of zero length. In this case if the SSL_select_next_proto function has been called as expected (with the list supplied by the client passed in the client/client_len parameters), then the application will not be vulnerable to this issue. If the application has accidentally been configured with a zero length server list, and has accidentally passed that zero length server list in the client/client_len parameters, and has additionally failed to correctly handle a "no overlap" response (which would normally result in a handshake failure in ALPN) then it will be vulnerable to this problem. In the case of NPN, the protocol permits the client to opportunistically select a protocol when there is no overlap. OpenSSL returns the first client protocol in the no overlap case in support of this. The list of client protocols comes from the application and should never normally be expected to be of zero length. However if the SSL_select_next_proto function is accidentally called with a client_len of 0 then an invalid memory pointer will be returned instead. If the application uses this output as the opportunistic protocol then the loss of confidentiality will occur. This issue has been assessed as Low severity because applications are most likely to be vulnerable if they are using NPN instead of ALPN - but NPN is not widely used. It also requires an application configuration or programming error. Finally, this issue would not typically be under attacker control making active exploitation unlikely. The FIPS modules in 3.3, 3.2, 3.1 and 3.0 are not affected by this issue. Due to the low severity of this issue we are not issuing new releases of OpenSSL at this time. The fix will be included in the next releases when they become available.
CVE-2024-5535 has been assigned to this vulnerability. A CVSS v3 base score of 5.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N).
3.2.42 IMPROPER AUTHENTICATION CWE-287
The Node.js Permission Model does not clarify in the documentation that wildcards should be only used as the last character of a file path. For example: --allow-fs-read=/home/node/.ssh/*.pub will ignore pub and give access to everything after .ssh/. This misleading documentation affects all users using the experimental permission model in Node.js 20 and Node.js 21. At the time this CVE was issued, the permission model was an experimental feature of Node.js.
CVE-2024-21890 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N).
3.2.43 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
Node.js could allow a remote attacker to bypass security restrictions, caused by improper path traversal sequence sanitization. By using a path traversal attack, an attacker could exploit this vulnerability leading to filesystem permission model bypass.
CVE-2024-21891 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N).
3.2.44 IMPROPER CONTROL OF GENERATION OF CODE ('CODE INJECTION') CWE-94
Node.js could allow a local authenticated attacker to gain elevated privileges on the system, caused by a bug in the implementation of the exception of CAP_NET_BIND_SERVICE. An attacker could exploit this vulnerability to inject code that inherits the process's elevated privileges.
CVE-2024-21892 has been assigned to this vulnerability. A CVSS v3 base score of 7.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.45 PATH TRAVERSAL: 'DIR/../../FILENAME' CWE-27
Node.js could allow a remote attacker to traverse directories on the system. By monkey-patching buffer internals, namely, Buffer.prototype.utf8Write, an attacker could send a specially crafted URL request containing "dot dot" sequences (/../) to read arbitrary files on the system.
CVE-2024-21896 has been assigned to this vulnerability. A CVSS v3 base score of 7.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:N).
3.2.46 EXECUTION WITH UNNECESSARY PRIVILEGES CWE-250
setuid() does not affect libuv's internal io_uring operations if initialized before the call to setuid(). This allows the process to perform privileged operations despite presumably having dropped such privileges through a call to setuid(). This vulnerability affects all users using version greater or equal than Node.js 18.18.0, Node.js 20.4.0 and Node.js 21.
CVE-2024-22017 has been assigned to this vulnerability. A CVSS v3 base score of 7.3 has been calculated; the CVSS vector string is (CVSS:3.0/AV:L/AC:L/PR:H/UI:N/S:C/C:L/I:H/A:L).
3.2.47 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
A vulnerability in Node.js HTTP servers allows an attacker to send a specially crafted HTTP request with chunked encoding, leading to resource exhaustion and denial of service. The server reads an unbounded number of bytes from a single connection, exploiting the lack of limitations on chunk extension bytes. The issue can cause CPU and network bandwidth exhaustion, bypassing standard safeguards like timeouts and body size limits.
CVE-2024-22019 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.48 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
Node.js is vulnerable to a denial of service, caused by a resource exhaustion vulnerability in fetch() brotli decoding . By sending a specially crafted request, a remote attacker could exploit this vulnerability to cause a denial-of-service condition.
CVE-2024-22025 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.49 EXPOSURE OF SENSITIVE INFORMATION TO AN UNAUTHORIZED ACTOR CWE-200
Undici is an HTTP/1.1 client, written from scratch for Node.js. Undici already cleared authorization headers on cross-origin redirects, but did not clear Proxy-Authentication headers. This issue has been patched in versions 5.28.3 and 6.6.1. Users are advised to upgrade. There are no known workarounds for this vulnerability.
CVE-2024-24758 has been assigned to this vulnerability. A CVSS v3 base score of 3.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:U/C:L/I:L/A:L).
3.2.50 SERVER-SIDE REQUEST FORGERY (SSRF) CWE-918
libuv is a multi-platform support library with a focus on asynchronous I/O. The uv_getaddrinfo function in src/unix/getaddrinfo.c (and its windows counterpart src/win/getaddrinfo.c), truncates hostnames to 256 characters before calling getaddrinfo. This behavior can be exploited to create addresses like 0x00007f000001, which are considered valid by getaddrinfo and could allow an attacker to craft payloads that resolve to unintended IP addresses, bypassing developer checks. The vulnerability arises due to how the hostname_ascii variable (with a length of 256 bytes) is handled in uv_getaddrinfo and subsequently in uv__idna_toascii. When the hostname exceeds 256 characters, it gets truncated without a terminating null byte. As a result attackers may be able to access internal APIs or for websites (similar to MySpace) that allows users to have username.example.com pages. Internal services that crawl or cache these user pages can be exposed to SSRF attacks if a malicious user chooses a long vulnerable username. This issue has been addressed in release version 1.48.0. Users are advised to upgrade. There are no known workarounds for this vulnerability.
CVE-2024-24806 has been assigned to this vulnerability. A CVSS v3 base score of 7.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L).
3.2.51 IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN AN OS COMMAND ('OS COMMAND INJECTION') CWE-78
Node.js could allow a remote attacker to execute arbitrary commands on the system, caused by the improper handling of batch files in child_process.spawn / child_process.spawnSync. By sending a specially crafted command line argument using args parameter, an attacker could exploit this vulnerability to inject and execute arbitrary commands on the system.
CVE-2024-27980 has been assigned to this vulnerability. A CVSS v3 base score of 7.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L).
3.2.52 INCONSISTENT INTERPRETATION OF HTTP REQUESTS ('HTTP REQUEST/RESPONSE SMUGGLING') CWE-444
A vulnerability in the http server, where malformed headers can lead to HTTP request smuggling. Specifically, if a space is placed before a content-length header, it is not interpreted correctly, enabling attackers to smuggle in a second request within the body of the first.
CVE-2024-27982 has been assigned to this vulnerability. A CVSS v3 base score of 6.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N).
3.2.53 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
Node.js is vulnerable to a denial of service, caused by an assertion failure in node::http2::Http2Session::~Http2Session(). By sending a small amount of HTTP/2 frames packets with a few HTTP/2 frames inside, an attacker could exploit this vulnerability to cause the HTTP/2 server to crash.
CVE-2024-27983 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.54 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
The affected application does not properly sanitize user provided paths for SFTP-based file up- and downloads. This could allow an authenticated remote attacker to manipulate arbitrary files on the filesystem and achieve arbitrary code execution on the device.
CVE-2024-46888 has been assigned to this vulnerability. A CVSS v3 base score of 9.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H).
3.2.55 USE OF HARD-CODED CRYPTOGRAPHIC KEY CWE-321
The affected application uses hard-coded cryptographic key material to obfuscate configuration files. This could allow an attacker to learn that cryptographic key material through reverse engineering of the application binary and decrypt arbitrary backup files.
CVE-2024-46889 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N).
3.2.56 IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN AN OS COMMAND ('OS COMMAND INJECTION') CWE-78
The affected application does not properly validate input sent to specific endpoints of its web API. This could allow an authenticated remote attacker with high privileges on the application to execute arbitrary code on the underlying OS.
CVE-2024-46890 has been assigned to this vulnerability. A CVSS v3 base score of 9.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H).
3.2.57 UNCONTROLLED RESOURCE CONSUMPTION CWE-400
The affected application does not properly restrict the size of generated log files. This could allow an unauthenticated remote attacker to trigger a large amount of logged events to exhaust the system's resources and create a denial-of-service condition.
CVE-2024-46891 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
3.2.58 INSUFFICIENT SESSION EXPIRATION CWE-613
The affected application does not properly invalidate sessions when the associated user is deleted or disabled or their permissions are modified. This could allow an authenticated attacker to continue performing malicious actions even after their user account has been disabled.
CVE-2024-46892 has been assigned to this vulnerability. A CVSS v3 base score of 4.9 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:N).
3.2.59 EXPOSURE OF SENSITIVE INFORMATION TO AN UNAUTHORIZED ACTOR CWE-200
The affected application does not properly validate authorization of a user to query the "/api/sftp/users" endpoint. This could allow an authenticated remote attacker to gain knowledge about the list of configured users of the SFTP service and also modify that configuration.
CVE-2024-46894 has been assigned to this vulnerability. A CVSS v3 base score of 6.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Siemens reported these vulnerabilities to CISA.
4. MITIGATIONS
Siemens has released SINEC INS V1.0 SP2 Update 3 and recommends updating to the latest version.
Siemens has identified the following specific workarounds and mitigations users can apply to reduce risk:
As a general security measure, Siemens recommends protecting network access to devices with appropriate mechanisms. To operate the devices in a protected IT environment, Siemens recommends configuring the environment according to Siemens' operational guidelines for industrial security and following recommendations in the product manuals.
Additional information on industrial security by Siemens can be found on the Siemens industrial security webpage
For more information see the associated Siemens security advisory SSA-915275 in HTML and CSAF.
CISA recommends users take defensive measures to minimize the risk of exploitation of these vulnerabilities. CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov in the technical information paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
5. UPDATE HISTORY
- November 14, 2024: Initial Publication
The social network Bluesky just announced that it has gained over 1 million new users in the past week. Like Twitter (now known as X), Bluesky is a microblogging platform, except it’s built on a decentralized architecture so it isn’t controlled by any single entity.
In other words, Bluesky users can create their own servers with specific rules and communities, allowing greater control over data and interactions. Those servers are all networked together, and that overall network is known as Bluesky.
While that sounds awesome in theory — no megalomaniac can hijack the entire platform and bend it to his or her own purposes — one of the downsides of Bluesky is that it’s technically more complicated. That’s been one of its biggest hurdles to growth and adoption.
Which is why this news of a population influx is so exciting. Bluesky now boasts over 14.5 million users, compared to competitors like Meta-owned Threads (which has 275 million users) and X, formerly Twitter (which has over 318 million users).
Speaking to The Verge, Bluesky COO Rose Wang says the majority of new users are from the US, coming in the wake of our high-profile presidential election. During said election, Elon Musk, who owns X, actively supported and boosted Donald Trump’s campaign.
OWASP Nettacker project is created to automate information gathering, vulnerability scanning, and eventually generating a report for networks, including services, bugs, vulnerabilities, misconfigurations, and other information. This software will utilize TCP SYN, ACK, ICMP,...
The post OWASP Nettacker: Automated Penetration Testing Framework appeared first on Penetration Testing Tools.
Newly Added (103)
- Atlassian Confluence Server CVE-2019-20406 Privilege Escalation Vulnerability
- Atlassian Confluence Server CVE-2023-22505 Remote Code Execution Vulnerability
- Atlassian Confluence Server CVE-2024-21674 Code Injection Vulnerability
- Atlassian Confluence Server CVE-2020-29450 Denial of Service Vulnerability
- Atlassian Confluence Server CVE-2019-3395 Server Side Request Forgery Vulnerability
- Atlassian Confluence Server CVE-2023-22522 Arbitrary Code Execution Vulnerability
- Atlassian Confluence Server CVE-2019-3398 Path Traversal Vulnerability
- Atlassian Confluence Server CVE-2023-22515 Authentication Bypass Vulnerability
- Atlassian Confluence Server CVE-2020-29445 Server Side Reqeust Forgery Vulnerability
- Atlassian Confluence Server CVE-2021-26072 Server Side Reqeust Forgery Vulnerability
- Atlassian Confluence Server CVE-2022-26137 Denial of Service Vulnerability
- Atlassian Confluence Server CVE-2023-22508 Remote Code Execution Vulnerability
- Atlassian Confluence Server CVE-2022-26136 Authentication Bypass Vulnerability
- Atlassian Confluence Server CVE-2021-26084 Arbitrary Code Execution Vulnerability
- Atlassian Confluence Server CVE-2022-26134 Arbitrary Code Execution Vulnerability
- Atlassian Confluence Server CVE-2018-20239 Cross Site Scripting Vulnerability
- Atlassian Confluence Server CVE-2019-3394 Path Traversal Vulnerability
- Atlassian Confluence Server CVE-2020-29448 Arbitrary File Read Vulnerability
- Atlassian Confluence Server CVE-2023-22518 Authorization Bypass Vulnerability
- Atlassian Confluence Server CVE-2020-29444 Cross Site Scripting Vulnerability
- Atlassian Confluence Server CVE-2020-4027 Arbitrary Code Execution Vulnerability
- Atlassian Confluence Server CVE-2019-3396 Path Traversal Vulnerability
- Atlassian Confluence Server CVE-2019-15006 Information Disclosure Vulnerability
- Atlassian Confluence Server CVE-2024-21683 Remote Code Execution Vulnerability
- Atlassian Confluence Server CVE-2018-20237 Information Disclosure Vulnerability
- Security Vulnerabilities fixed in Google Chrome 131.0.6778.69
- Microsoft Windows Update Stack CVE-2024-43530 Elevation of Privilege Vulnerability
- Microsoft Windows NT OS Kernel CVE-2024-43623 Elevation of Privilege Vulnerability
- Microsoft Windows VMSwitch CVE-2024-43625 Elevation of Privilege Vulnerability
- Microsoft Windows Telephony Service CVE-2024-43626 Elevation of Privilege Vulnerability
- Microsoft Windows Telephony Service CVE-2024-43627 Remote Code Execution Vulnerability
- Microsoft Windows Telephony Service CVE-2024-43628 Remote Code Execution Vulnerability
- Microsoft Windows Kernel CVE-2024-43630 Elevation of Privilege Vulnerability
- Microsoft Windows Secure Kernel Mode CVE-2024-43631 Elevation of Privilege Vulnerability
- Microsoft Windows USB Video Class System Driver CVE-2024-43634 Elevation of Privilege Vulnerability
- Microsoft Windows USB Video Class System Driver CVE-2024-43637 Elevation of Privilege Vulnerability
- Microsoft Windows USB Video Class System Driver CVE-2024-43638 Elevation of Privilege Vulnerability
- Microsoft Windows USB Video Class System Driver CVE-2024-43643 Elevation of Privilege Vulnerability
- Microsoft Windows Client-Side Caching CVE-2024-43644 Elevation of Privilege Vulnerability
- Microsoft Windows Defender Application Control CVE-2024-43645 Security Feature Bypass Vulnerability
- Microsoft Windows Secure Kernel Mode CVE-2024-43646 Elevation of Privilege Vulnerability
- Microsoft Windows SMBv3 Server CVE-2024-43447 Remote Code Execution Vulnerability
- Microsoft Windows USB Video Class System Driver CVE-2024-43449 Elevation of Privilege Vulnerability
- Microsoft Windows DNS CVE-2024-43450 Spoofing Vulnerability
- Microsoft NTLM Hash Disclosure CVE-2024-43451 Spoofing Vulnerability
- Microsoft Windows Registry CVE-2024-43452 Elevation of Privilege Vulnerability
- Microsoft SQL Server Native Client CVE-2024-38255 Remote Code Execution Vulnerability
- Microsoft Virtual Hard Disk CVE-2024-38264 Denial of Service Vulnerability
- Microsoft SQL Server Native Client CVE-2024-43459 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-43462 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-48994 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-48995 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-48996 Remote Code Execution Vulnerability
- Microsoft Exchange Server CVE-2024-49040 Spoofing Vulnerability
- Microsoft.SqlServer.XEvent.Configuration.dll CVE-2024-49043 Remote Code Execution Vulnerability
- Microsoft Windows Win32 Kernel Subsystem CVE-2024-49046 Elevation of Privilege Vulnerability
- Microsoft Windows Telephony Service CVE-2024-43620 Remote Code Execution Vulnerability
- Microsoft Windows Telephony Service CVE-2024-43621 Remote Code Execution Vulnerability
- Microsoft Windows Telephony Service CVE-2024-43622 Remote Code Execution Vulnerability
- Microsoft Windows Hyper-V Shared Virtual Disk CVE-2024-43624 Elevation of Privilege Vulnerability
- Microsoft Windows DWM Core Library CVE-2024-43629 Elevation of Privilege Vulnerability
- Microsoft Windows Hyper-V CVE-2024-43633 Denial of Service Vulnerability
- Microsoft Windows Telephony Service CVE-2024-43635 Remote Code Execution Vulnerability
- Microsoft Win32k CVE-2024-43636 Elevation of Privilege Vulnerability
- Microsoft Windows Kerberos CVE-2024-43639 Remote Code Execution Vulnerability
- Microsoft Windows Kernel-Mode Driver CVE-2024-43640 Elevation of Privilege Vulnerability
- Microsoft Windows Registry CVE-2024-43641 Elevation of Privilege Vulnerability
- Microsoft Windows SMB CVE-2024-43642 Denial of Service Vulnerability
- Microsoft Windows Package Library Manager CVE-2024-38203 Information Disclosure Vulnerability
- Microsoft SQL Server Native Client CVE-2024-48993 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-48997 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-48998 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-48999 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49000 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49001 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49002 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49003 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49004 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49005 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49007 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49006 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49008 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49009 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49010 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49011 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49012 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49013 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49014 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49015 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49016 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49017 Remote Code Execution Vulnerability
- Microsoft SQL Server Native Client CVE-2024-49018 Remote Code Execution Vulnerability
- Microsoft Active Directory Certificate Services CVE-2024-49019 Elevation of Privilege Vulnerability
- Microsoft SQL Server CVE-2024-49021 Remote Code Execution Vulnerability
- Microsoft Excel CVE-2024-49026 Remote Code Execution Vulnerability
- Microsoft Excel CVE-2024-49027 Remote Code Execution Vulnerability
- Microsoft Excel CVE-2024-49028 Remote Code Execution Vulnerability
- Microsoft Excel CVE-2024-49029 Remote Code Execution Vulnerability
- Microsoft Excel CVE-2024-49030 Remote Code Execution Vulnerability
- Microsoft Office Graphics CVE-2024-49031 Remote Code Execution Vulnerability
- Microsoft Office Graphics CVE-2024-49032 Remote Code Execution Vulnerability
- Microsoft Word CVE-2024-49033 Security Feature Bypass Vulnerability
- Microsoft Windows Task Scheduler CVE-2024-49039 Elevation of Privilege Vulnerability
There are thousands of “WordPress security plugins” listed on the official WordPress plugin repository, which claim to offer some security-related functionality and serve some purpose related to securing WordPress. This is not surprising. In our state of WordPress security report, we highlighted that nearly 42% of WordPress sites have at least one vulnerable software component. […]
The post The 6 Best WordPress Security Plugins (+ Do You Really Need One?) appeared first on Patchstack.
Researchers discovered GoIssue, a new phishing tool targeting GitHub users, designed to extract email addresses from public profiles and launch mass email attacks. Marketed on a cybercrime forum, GoIssue allows attackers to send bulk emails while keeping their identity hidden using proxies. The tool’s capabilities extend beyond simple phishing, posing a threat to entire organizations by potentially hijacking developer accounts and accessing private repositories. GoIssue may be linked to the GitLoker extortion campaign, which uses … More
The post GoIssue phishing tool targets GitHub developer credentials appeared first on Help Net Security.
- 4Critical
- 82Important
- 1Moderate
- 0Low
Microsoft addresses 87 CVEs and one advisory (ADV240001) in its November 2024 Patch Tuesday release, with four critical vulnerabilities and four zero-day vulnerabilities, including two that were exploited in the wild.
Microsoft patched 87 CVEs in its November 2024 Patch Tuesday release, with four rated critical, 82 rated important and one rated moderate.
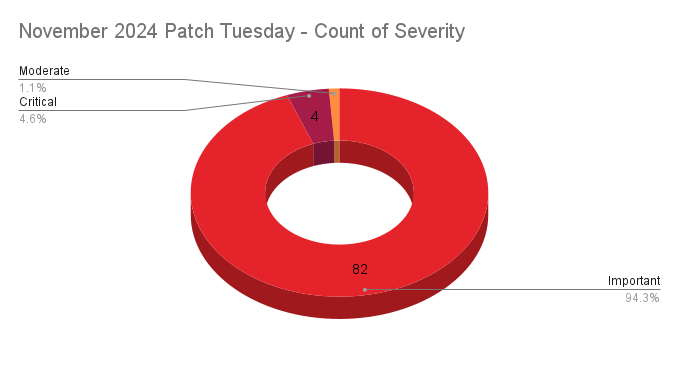
This month’s update includes patches for:
- .NET and Visual Studio
- Airlift.microsoft.com
- Azure CycleCloud
- Azure Database for PostgreSQL
- LightGBM
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Office Excel
- Microsoft Office Word
- Microsoft PC Manager
- Microsoft Virtual Hard Drive
- Microsoft Windows DNS
- Role: Windows Hyper-V
- SQL Server
- TorchGeo
- Visual Studio
- Visual Studio Code
- Windows Active Directory Certificate Services
- Windows CSC Service
- Windows DWM Core Library
- Windows Defender Application Control (WDAC)
- Windows Kerberos
- Windows Kernel
- Windows NT OS Kernel
- Windows NTLM
- Windows Package Library Manager
- Windows Registry
- Windows SMB
- Windows SMBv3 Client/Server
- Windows Secure Kernel Mode
- Windows Task Scheduler
- Windows Telephony Service
- Windows USB Video Driver
- Windows Update Stack
- Windows VMSwitch
- Windows Win32 Kernel Subsystem
Remote code execution (RCE) vulnerabilities accounted for 58.6% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 29.9%.
CVE-2024-43451 | NTLM Hash Disclosure Spoofing Vulnerability
CVE-2024-43451 is a NTLM hash spoofing vulnerability in Microsoft Windows. It was assigned a CVSSv3 score of 6.5 and is rated as important. An attacker could exploit this flaw by convincing a user to open a specially crafted file. Successful exploitation would lead to the unauthorized disclosure of a user’s NTLMv2 hash, which an attacker could then use to authenticate to the system as the user. According to Microsoft, CVE-2024-43451 was exploited in the wild as a zero-day. No further details about this vulnerability were available at the time this blog post was published.
This is the second NTLM spoofing vulnerability disclosed in 2024. Microsoft patched CVE-2024-30081 in its July Patch Tuesday release.
CVE-2024-49039 | Windows Task Scheduler Elevation of Privilege Vulnerability
CVE-2024-49039 is an EoP vulnerability in the Microsoft Windows Task Scheduler. It was assigned a CVSSv3 score of 8.8 and is rated as important. An attacker with local access to a vulnerable system could exploit this vulnerability by running a specially crafted application. Successful exploitation would allow an attacker to access resources that would otherwise be unavailable to them as well as execute code, such as remote procedure call (RPC) functions.
According to Microsoft, CVE-2024-49039 was exploited in the wild as a zero-day. It was disclosed to Microsoft by an anonymous researcher along with Vlad Stolyarov and Bahare Sabouri of Google's Threat Analysis Group. At the time this blog post was published, no further details about in-the-wild exploitation were available.
CVE-2024-49019 | Active Directory Certificate Services Elevation of Privilege Vulnerability
CVE-2024-49019 is an EoP vulnerability affecting Active Directory Certificate Services. It was assigned a CVSSv3 score of 7.8 and is rated as important. It was publicly disclosed prior to a patch being made available. According to Microsoft, successful exploitation would allow an attacker to gain administrator privileges. The advisory notes that “certificates created using a version 1 certificate template with Source of subject name set to ‘Supplied in the request’” are potentially impacted if the template has not been secured according to best practices. This vulnerability is assessed as “Exploitation More Likely” according to Microsoft’s Exploitability Index. Microsoft’s advisory also includes several mitigation steps for securing certificate templates which we highly recommend reviewing.
CVE-2024-49040 | Microsoft Exchange Server Spoofing Vulnerability
CVE-2024-49040 is a spoofing vulnerability affecting Microsoft Exchange Server 2016 and 2019. It was assigned a CVSSv3 score of 7.5 and rated as important. According to Microsoft, this vulnerability was publicly disclosed prior to a patch being made available. After applying the update, administrators should review the support article Exchange Server non-RFC compliant P2 FROM header detection. The supplemental guide notes that as part of a “secure by default” approach, the Exchange Server update for November will flag suspicious emails which may contain “malicious patterns in the P2 FROM header.” While this feature can be disabled, Microsoft strongly recommends leaving it enabled to provide further protection from phishing attempts and malicious emails.
CVE-2024-43639 | Windows Kerberos Remote Code Execution Vulnerability
CVE-2024-43639 is a critical RCE vulnerability affecting Windows Kerberos, an authentication protocol designed to verify user or host identities. It was assigned a CVSSv3 score of 9.8 and is rated as “Exploitation Less Likely.”
To exploit this vulnerability, an unauthenticated attacker needs to leverage a cryptographic protocol vulnerability in order to achieve RCE. No further details were provided by Microsoft about this vulnerability at the time this blog was published.
29 CVEs | SQL Server Native Client Remote Code Execution Vulnerability
This month's release included 29 CVEs for RCEs affecting SQL Server Native Client. All of these CVEs received CVSSv3 scores of 8.8 and were rated as “Exploitation Less Likely.” Successful exploitation of these vulnerabilities can be achieved by convincing an authenticated user into connecting to a malicious SQL server database using an affected driver. A full list of the CVEs are included in the table below.
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2024-38255 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-43459 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-43462 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-48993 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-48994 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-48995 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-48996 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-48997 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-48998 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-48999 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49000 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49001 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49002 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49003 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49004 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49005 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49006 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49007 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49008 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49009 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49010 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49011 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49012 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49013 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49014 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49015 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49016 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49017 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-49018 | SQL Server Native Client Remote Code Execution Vulnerability | 8.8 |
CVE-2024-43602 | Azure CycleCloud Remote Code Execution Vulnerability
CVE-2024-43602 is a RCE vulnerability in Microsoft’s Azure CycleCloud, a tool that helps in managing and orchestrating High Performance Computing (HPC) environments in Azure. This flaw received the highest CVSSv3 score of the month, a 9.9 and was rated as important. A user with basic permissions could exploit CVE-2024-43602 by sending specially crafted requests to a vulnerable AzureCloud CycleCloud cluster to modify its configuration. Successful exploitation would result in the user gaining root permissions, which could then be used to execute commands on any cluster in the Azure CycleCloud as well as steal admin credentials.
Tenable Solutions
A list of all the plugins released for Microsoft’s November 2024 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's November 2024 Security Updates
- Tenable plugins for Microsoft November 2024 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

The post Microsoft’s November 2024 Patch Tuesday Addresses 87 CVEs (CVE-2024-43451, CVE-2024-49039) appeared first on Security Boulevard.
Where there’s a gift to be bought, there’s also a scammer out to make money. Here's how to stay safe this shopping season.
Chinese state-sponsored hackers recently compromised two prominent Tibetan websites in a sophisticated cyber-espionage campaign to distribute the notorious Cobalt Strike malware. The attack, attributed to the threat group TAG-112, highlights the ongoing digital threats faced by ethnic and religious minorities in China. Recorded Future observed that hackers attacked the targeted websites, Tibet Post and Gyudmed […]
The post China-Nexus Hackers Hijack Websites to Deliver Cobalt Strike Malware appeared first on Cyber Security News.
Microsoft released its latest Patch Tuesday update, addressing 89 security vulnerabilities across its software portfolio. Four of these are classified as zero-day vulnerabilities, with two actively exploited in the wild. This patch release underscores the critical importance of timely updates to protect against potential cyber threats. Zero-Day Vulnerabilities Patched The four zero-day vulnerabilities patched in […]
The post Microsoft November Patch Tuesday: 4 Zero-Days & 89 Vulnerabilities Patched appeared first on Cyber Security News.
It’s not quite the holiday season, despite what some early decorators will have you believe. It is the second Tuesday of the month, and that means Adobe and Microsoft have released their regularly scheduled updates. Take a break from your regular activities and join us as we review the details of their latest security alerts.If you’d rather watch the full video recap covering the entire release, you can check it out here:
Adobe Patches for November 2024
For November, Adobe released eight patches addressing 48 CVEs in Adobe Bridge, Audition, After Effects, Substance 3D Painter, Illustrator, InDesign, Photoshop, and Commerce. The largest of these fixes is for Substance 3D Painter with 22 Critical and Important CVEs. The next largest is the patch for Illustrator, with nine CVEs addressed. The fix for After Effects addresses six bugs – three Critical and three Important. The worst of these could allow arbitrary code execution. That’s the same story for the InDesign patch. There’s a single server-side request forgery (SSRF) in Commerce, but it requires authentication. There’s also a single, Critical-rated CVE in Photoshop, which requires user interaction in the form of opening a file. The remaining fixes from Adobe are only Important rated, with two bugs in Adobe Bridge and a single bug in Adobe Audition.
None of the bugs fixed by Adobe this month are listed as publicly known or under active attack at the time of release. Adobe categorizes these updates as a deployment priority rating of 3.
Microsoft Patches for November 2024
This month, Microsoft released 89 new CVEs in Windows and Windows Components; Office and Office Components; Azure; .NET and Visual Studio; LightGBM; Exchange Server; SQL Server; TorchGeo; Hyper-V; and Windows VMSwitch. One of these vulnerabilities was reported through the ZDI program. With the addition of the third-party CVEs, the entire release tops out at 92 CVEs.
Of the patches released today, four are rated Critical, 84 are rated Important, and one is rated Moderate in severity. This represents another large month of fixes from the Redmond giant and puts them at 949 CVEs addressed so far this year. Even before counting the fixes in December, 2024 is Microsoft's second-largest year for fixes.
Microsoft lists three of these CVEs as publicly known, but I disagree and put the count at five (more on that later). They also list two as being exploited in the wild at the time of release. Let’s take a closer look at some of the more interesting updates for this month, starting with the vulnerabilities currently under active attack:
CVE-2024-43451 - NTLM Hash Disclosure Spoofing Vulnerability
It seems we can never fully escape Internet Explorer. Despite it being retired by Microsoft, it still remains in the form of MSHTML and is accessible through the WebBrowser control and other means. That is what is being abused by attackers here to disclose the victim’s NTLMv2 hash, which could then be used by the attacker to authenticate as the user. User interaction is required, but that doesn’t seem to stop these attacks from being effective. As always, Microsoft does not give any indication of how widespread these attacks are, but I would not wait to test and deploy this update.
CVE-2024-49039 - Windows Task Scheduler Elevation of Privilege Vulnerability
Here’s another local privilege escalation bug being used in the wild. However, this isn’t the straightforward EoP we typically see. In this case, the bug allows an AppContainer escape – allowing a low-privileged user to execute code at Medium integrity. You still need to be able to execute code on the system for this to occur, but container escapes are still quite interesting as they are rarely seen in the wild. This was reported by multiple researchers, which indicates the bug is being exploited in multiple regions. Hopefully one of the researchers will provide additional details about the vulnerability now that a fix is available.
CVE-2024-43639 - Windows Kerberos Remote Code Execution Vulnerability
I don’t often get excited about bugs (ok – that’s a lie – I totally do), but this CVSS 9.8 bug excites me. The vulnerability allows a remote, unauthenticated attacker to run code on an affected system by leveraging a bug in the cryptographic protocol. No user interaction is required. Since Kerberos runs with elevated privileges, that makes this a wormable bug between affected systems. What systems are impacted? Every supported version of Windows Server. I somehow doubt this will actually be seen in the wild, but I wouldn’t take that chance. Test and deploy this fix quickly.
CVE-2024-43498 - .NET and Visual Studio Remote Code Execution Vulnerability
This is one of the bugs I say is public even though Microsoft doesn’t, as it sure looks like this issue. This is another CVSS 9.8 and would allow attackers to execute code by sending a specially crafted request to an affected .NET webapp. The attacker could also convince a target to load a specially crafted file from an affected desktop app. Either way, the resulting code execution would occur at the level of the application, so it may be paired with an EoP if it were to be seen in the wild. Definitely check your .NET and Visual Studio apps and patch them as needed.
Here’s the full list of CVEs released by Microsoft for November 2024:
| CVE | Title | Severity | CVSS | Public | Exploited | Type |
| CVE-2024-43451 | NTLM Hash Disclosure Spoofing Vulnerability | Important | 6.5 | Yes | Yes | Spoofing |
| CVE-2024-49039 | Windows Task Scheduler Elevation of Privilege Vulnerability | Important | 8.8 | No | Yes | EoP |
| CVE-2024-43498 | .NET and Visual Studio Remote Code Execution Vulnerability | Critical | 9.8 | Yes ** | No | RCE |
| CVE-2024-5535 * | OpenSSL: CVE-2024-5535 SSL_select_next_proto buffer overread | Important | 9.1 | Yes** | No | RCE |
| CVE-2024-49019 | Active Directory Certificate Services Elevation of Privilege Vulnerability | Important | 7.8 | Yes | No | EoP |
| CVE-2024-49040 † | Microsoft Exchange Server Spoofing Vulnerability | Important | 7.5 | Yes | No | Spoofing |
| CVE-2024-49056 | Airlift.microsoft.com Elevation of Privilege Vulnerability | Critical | 7.3 | No | No | EoP |
| CVE-2024-43625 | Microsoft Windows VMSwitch Elevation of Privilege Vulnerability | Critical | 8.1 | No | No | EoP |
| CVE-2024-43639 | Windows Kerberos Remote Code Execution Vulnerability | Critical | 9.8 | No | No | RCE |
| CVE-2024-43499 | .NET and Visual Studio Denial of Service Vulnerability | Important | 7.5 | No | No | DoS |
| CVE-2024-43602 | Azure CycleCloud Remote Code Execution Vulnerability | Important | 9.9 | No | No | RCE |
| CVE-2024-43613 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Privilege Vulnerability | Important | 7.2 | No | No | EoP |
| CVE-2024-49042 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Privilege Vulnerability | Important | 7.2 | No | No | EoP |
| CVE-2024-43598 | LightGBM Remote Code Execution Vulnerability | Important | 7.5 | No | No | RCE |
| CVE-2024-49026 | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2024-49027 | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2024-49028 | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2024-49029 | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2024-49030 | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2024-49031 | Microsoft Office Graphics Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2024-49032 | Microsoft Office Graphics Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2024-49051 | Microsoft PC Manager Elevation of Privilege Vulnerability | Important | 8.4 | No | No | EoP |
| CVE-2024-49021 | Microsoft SQL Server Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2024-38264 | Microsoft Virtual Hard Disk (VHDX) Denial of Service Vulnerability | Important | 5.9 | No | No | DoS |
| CVE-2024-49033 | Microsoft Word Security Feature Bypass Vulnerability | Important | 7.5 | No | No | SFB |
| CVE-2024-49043 † | Microsoft.SqlServer.XEvent.Configuration.dll Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2024-38255 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-43459 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-43462 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-48993 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-48994 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-48995 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-48996 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-48997 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-48998 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-48999 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49000 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49001 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49002 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49003 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49004 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49005 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49006 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49007 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49008 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49009 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49010 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49011 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49012 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49013 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49014 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49015 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49016 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49017 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49018 | SQL Server Native Client Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49048 | TorchGeo Remote Code Execution Vulnerability | Important | 8.1 | No | No | RCE |
| CVE-2024-49050 | Visual Studio Code Python Extension Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-49044 | Visual Studio Elevation of Privilege Vulnerability | Important | 6.7 | No | No | EoP |
| CVE-2024-43636 | Win32k Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-43644 | Windows Client-Side Caching Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-43645 | Windows Defender Application Control (WDAC) Security Feature Bypass Vulnerability | Important | 6.7 | No | No | SFB |
| CVE-2024-43450 | Windows DNS Spoofing Vulnerability | Important | 7.5 | No | No | Spoofing |
| CVE-2024-43629 | Windows DWM Core Library Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-43633 | Windows Hyper-V Denial of Service Vulnerability | Important | 6.5 | No | No | DoS |
| CVE-2024-43624 | Windows Hyper-V Shared Virtual Disk Elevation of Privilege Vulnerability | Important | 8.8 | No | No | EoP |
| CVE-2024-43630 | Windows Kernel Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-43640 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-43623 | Windows NT OS Kernel Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-38203 | Windows Package Library Manager Information Disclosure Vulnerability | Important | 6.2 | No | No | Info |
| CVE-2024-43641 | Windows Registry Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-43452 | Windows Registry Elevation of Privilege Vulnerability | Important | 7.5 | No | No | EoP |
| CVE-2024-43631 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability | Important | 6.7 | No | No | EoP |
| CVE-2024-43646 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability | Important | 6.7 | No | No | EoP |
| CVE-2024-43642 | Windows SMB Denial of Service Vulnerability | Important | 7.5 | No | No | DoS |
| CVE-2024-43447 | Windows SMBv3 Server Remote Code Execution Vulnerability | Important | 8.1 | No | No | RCE |
| CVE-2024-43626 | Windows Telephony Service Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-43620 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-43621 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-43622 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-43627 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-43628 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-43635 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2024-43530 | Windows Update Stack Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-43449 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability | Important | 6.8 | No | No | EoP |
| CVE-2024-43634 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability | Important | 6.8 | No | No | EoP |
| CVE-2024-43637 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability | Important | 6.8 | No | No | EoP |
| CVE-2024-43638 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability | Important | 6.8 | No | No | EoP |
| CVE-2024-43643 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability | Important | 6.8 | No | No | EoP |
| CVE-2024-49046 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2024-49049 | Visual Studio Code Remote Extension Elevation of Privilege Vulnerability | Moderate | 7.1 | No | No | EoP |
| CVE-2024-10826 * | Chromium: CVE-2024-10826 Use after free in Family Experiences | High | N/A | No | No | RCE |
| CVE-2024-10827 * | Chromium: CVE-2024-10827 Use after free in Serial | High | N/A | No | No | RCE |
* Indicates this CVE had been released by a third party and is now being included in Microsoft releases.
** Indicates this bug is not listed as public by Microsoft but considered to be public for the purposes of this blog.
† Indicates further administrative actions are required to fully address the vulnerability.
There are only two other Critical-rated bugs receiving fixes this month, and both involve privilege escalations. The bug in VMSwitch could allow a low-privileged user on a guest OS to execute their code at SYSTEM on the underlying host OS. That’s officially a Bad Thing™. The other Critical-rated bug resides in a cloud service, so the vulnerability has already been mitigated and is now being documented.
There are more than 50 other code execution bugs this month, but most of these impact SQL Server. These require an affected system to connect to a malicious SQL database, so the likelihood of exploitation is pretty low. There is one SQL bug that requires additional attention. CVE-2024-49043 requires an update to OLE DB Driver 18 or 19, but may also require third-party fixes, too. Ensure you read that one carefully and apply all the needed fixes. There are also quite a few open-and-own bugs in Office components, but none involve the Preview Pane. There are a half-dozen RCE bugs in the Telephony service. These all require the target to connect to a malicious server, but this could be done by tricking the user into sending a request to the attacker-controlled server.
Of the more interesting RCE bugs, the SMBv3 bug stands out. An attacker could exploit this by using a malicious SMB client to mount an attack against an affected SMB server. Interestingly, this is only applicable to SMB over QUIC, which might not be a common setup. Another interesting bug is a CVSS 9.9 vulnerability in the Azure CycleCloud. This does require basic permissions but could be used to gain root-level permissions and allow them to execute commands on any Azure CycleCloud cluster in the current instance. Neat. There’s an RCE in TouchGeo, which is a PyTorch domain library for use with machine learning. There’s no real information about the vulnerability, but it can be hit remotely and doesn’t require user interaction. Finally, there’s the Microsoft update for OpenSSL. They do not list this as public, but this bug was documented back in June. Even though this is a third-party update, I find not listing this as public is disingenuous.
There are more than two dozen fixes for privilege escalation bugs in this release. However, most of these either lead to SYSTEM-level code execution or administrative privileges if an authenticated user runs specially crafted code. However, there are a few that stand out. The bugs in the USB Video Class System require physical access as the attacker needs to plug in a USB device. This would also lead to SYSTEM-level code execution. The escalation in Active Directory Certificates would allow an attacker to gain administrative privileges, but only if your PKI environment is set to specific parameters, so read the bulletin for details. The bugs in Azure Database for PostgreSQL could lead to the same privileges as the SuperUser role. The bug in PC Manager allows attackers to delete files, which can be used to elevate privileges. The Visual Studio bug just gets to the privileges of the current user. Finally, the bug in Hyper-V could allow a guest-to-host code execution at SYSTEM on the host OS. Microsoft lists this as a CVSS 8.8, but considering this could be viewed as a scope change (going from guest OS to SYSTEM), I would rate it at a 9.9.
There are only two Security Feature Bypass (SFB) bugs in the November release. The bug in Word could allow attackers to bypass Office Protected View. Not surprisingly, the bypass in the Windows Defender Application Control (WDAC) allows attackers to bypass WDAC enforcement and run unauthorized apps.
There’s only a single information disclosure bug getting fixed this month, and it resides in the Windows Package Library Manager. It allows attackers to expose privileged information belonging to the user of the affected application.
There are a couple of spoofing bugs being addressed, and the first is in Exchange Server. Microsoft doesn’t list what is being spoofed, but with Exchange Server, this often leads to NTLM relays. And you’ll need to do more than patch this bug. You need to take the additional actions listed here to be fully protected, which is just what every Exchange admin wants to hear. The other spoofing bug is in DNS. Again, no real information is given by Microsoft, but DNS spoofing bugs typically lead to altered DNS responses.
The November release is rounded out by four denial-of-service (DoS) bugs. As usual, Microsoft provides next to no information about these bugs or their impact. The only exception to this is the DoS bug in Hyper-V, which could be used to execute a cross-VM attack – allowing one guest VM to impact other guest VMs on the same hypervisor.
There are no new advisories in this month’s release.
Looking Ahead
The final Patch Tuesday of 2024 will be on December 10, and I’ll return with details and patch analysis at that time. Until then, stay safe, happy patching, and may all your reboots be smooth and clean!
4 zero-days. AD CS ESC15 aka EKUwu. NTLMv2 disclosure. Exchange sender spoofing. Task scheduler EoP. .NET & Kerberos critical RCEs. Welcome Server 2025.
This month, Microsoft is addressing a total of 83 vulnerabilities. Among these, 3 are classified as critical, 2 have been exploited in the wild, and another 2 have been disclosed prior to Patch Tuesday. Organizations are encouraged to prioritize these updates to mitigate potential risks and enhance their security posture.


 Notable Vulnerabilities:


 NTLM Hash Disclosure Spoofing Vulnerability (CVE-2024-43451)

 This vulnerability, identified as CVE-2024-43451, has been exploited and disclosed, carrying an Important severity rating with a CVSS score of 6.5. It allows an attacker to disclose a user's NTLMv2 hash, enabling them to authenticate as that user, which could lead to a total loss of confidentiality. Exploitation requires minimal user interaction, such as selecting or inspecting a malicious file. The vulnerability affects all supported versions of Microsoft Windows, and while Internet Explorer has been retired on certain platforms, updates addressing this vulnerability are included in the IE Cumulative Updates to ensure continued protection.
The company advises users replace affected endpoints with newer models.
A vulnerability was found in Shell in a Box up to 2.18. It has been classified as critical. Affected is an unknown function of the file /plain of the component HTTPS Fallback. The manipulation leads to 7pk security features (DNS Rebinding). This vulnerability is traded as CVE-2015-8400. It is possible to launch the attack remotely. There is no exploit available. It is recommended to upgrade the affected component.
 Welcome to this week's Data Breaches Digest, a catalogue of links concerning Data Breaches and Cyber Security that were published on the Internet during the period between 11th November and 17th November 2024.
Welcome to this week's Data Breaches Digest, a catalogue of links concerning Data Breaches and Cyber Security that were published on the Internet during the period between 11th November and 17th November 2024.11th November
4 reasons why veterans thrive as cybersecurity professionals
A surge in Pro-Russia cyberattacks after decision to monitor North Korean Troops in Ukraine
Anti-Israel hacker claims hack on Ministry of National Security, posts settler IDs online
Are You Googling This? You Could Be Walking Into a Cyber Trap
City of Sheboygan Hit by Cyberattack – Here’s the Latest on the Ransom Threat
Combating the Ransomware Menace: How to Safeguard and Respond Effectively
'Cyber attack' council working to ease backlog
Cyberattack Disrupts Israel’s Gas Stations and Payment Systems - Here’s What We Know
Cybercriminals Use Excel Exploit to Spread Fileless Remcos RAT Malware
Hackers Exploiting Veeam RCE Flaw to Deploy New Frag Ransomware
How human ingenuity continues to outpace automated security tools
Mass Telegram account hijacking via supply-chain phishing campaign
OpenText reveals 2024 nastiest malware, LockBit leads list
Strategies for CISOs navigating hybrid and multi-cloud security
The Importance of Effective Incident Response
Wayback Machine cyber attacks: Everything you need to know
Why Business Email Compromise (BEC) Impersonation is the Weapon of Choice for Cybercriminals
World Health Organization (WHO), 50 countries warn UN of rising ransomware attacks on hospitals
A vulnerability was found in ReadyNet WRT300N-DD 1.0.26. It has been rated as critical. Affected by this issue is some unknown functionality of the component DNS Query Handler. The manipulation of the argument PORT leads to improper input validation. This vulnerability is handled as CVE-2015-7282. The attack may be launched remotely. There is no exploit available.
US CFPB warns employees to avoid work-related mobile calls and texts following China-linked Salt Typhoon hack over security concerns. The US government’s Consumer Financial Protection Bureau (CFPB) advises employees to avoid using cellphones for work after China-linked APT group Salt Typhoon hackers breached major telecom providers. The Consumer Financial Protection Bureau (CFPB) is a U.S. […]
IVRE IVRE is an open-source framework for network recon. It relies on open-source well-known tools (Nmap, Zmap, Masscan, Bro, and p0f) to gather data (network intelligence), stores it in a database (MongoDB), and provides tools to analyze it....
The post ivre: open source network recon framework appeared first on Penetration Testing Tools.
Authorities arrest data thief and disrupt cybercrime infrastructure, North Korean APT targets Macs for crypto, and AWS keys stolen via fake PyPi package.






















































































