Did Zoom really get hacked?
Zoom Video Communications Inc.’s video conferencing app, has seen booming popularity since COVID-19 outbreaks began in January 2020. Zoom usage rose after lockdowns with corporate office workers, students, millions of people who #stayhome, and even football teams like Liverpool FC. This makes a perfectly good target for threat actors, but it could be fixed with a risk-based approach.
Liverpool FC’s tweet including manager Jürgen Klopp’s interview, shows the importance of nZoom calls to maintain the team spirit during the unprecedented pandemic crisis
Not only have daily average users skyrocketed from 10 million to 200 million but so have the number of headlines showing up its security loopholes. However very few of them were about the risk of volumetric credential stuffing attack, probably because the root cause of this attack is addressing the weakest link on the chain: “users” For users, the best technology is easy-to-use. Zoom knows this rule very well by putting this message at the center of its marketing campaigns to survive and become profitable in the highly-competitive video conferencing market. Signing up to the platform without any friction such as two-factor authentication or complex password requirements, is — ready to hear this? — one of the competitive advantages. Less friction means more users, more profit. But there is a dark side.
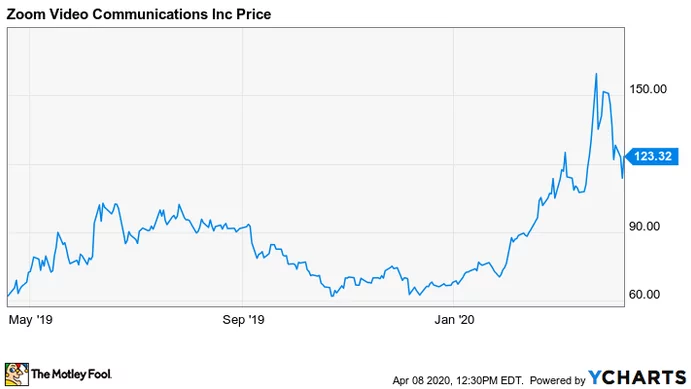
ZOOM (NASDAQ: ZM) stock has risen by about 75% year-to-date
How did it happen?
First of all, this is not unique to Zoom, and there is no end in sight for this variety of cybercrime activity. Consumer-facing businesses operating in a variety of sectors from E-commerce to Finance are at high risk of facing such an attack.
Threat actors’ primary motivation is financial, but it can lead to identity theft or gaining reputation in the dark web which opens doors to new profitable jobs. From the business perspective, as Zoom experienced lately, it can cause a huge loss of brand reputation. A Forbes Insight report found that 46 percent of organizations had suffered damage to their reputations and brand value as a result of a breach. The technical cause does not matter so much since many consumers don’t have sufficient information on handling this incident right. After the data privacy scandals in recent years, consumers are skeptical and now, more than ever, paying attention to what is happening with their data.
Credential stuffing attack is in principle very simple, like a numbers game with a very low success rate. Threat actors leverage freshly-leaked combo lists containing pairs of username-password to perform automated login action against an online platform. The credential lists used in these attacks are acquired from a variety of sources, including black markets of data breach content. The main problem is that users sign up for multiple web applications with the same login credentials. That makes it harder to contain because it’s highly dependent upon user behavior, however, this is just one aspect.
What can be done?
At SOCRadar, we have been working closely with E-commerce giants and Financial institutions to reduce their attack surface by providing them with a multi-functional, automated digital risk protection technology as well as on-demand TIA services. Based on our years of experience and hands-on research, we see how valuable it can be to adopt a risk-based, proactive, and intelligence-driven approach to cybersecurity.
Zoom experience has shown us once again that the infrastructure scalability and stability need to be empowered by intelligence-driven security scalability.
There are a couple of aspects affecting the success of credential stuffing attacks and the advantageous position of the adversaries: automation and anonymity. From a Threat Intelligence perspective, understanding the mechanisms behind these aspects can create a positive difference to mitigate the possible harmful results. The first aspect is automation which is a challenge from threat actors’ perspective. They need software — called Account Checker or Config File — that would check the massive list of credentials against the targeted web application and detect the valid ones. It needs to have the capability to bypass security mechanisms which makes it harder. Proactively monitoring dark web and black markets where the software and techniques are heavily traded or threat campaigns are promoted can provide valuable insights on the upcoming attack techniques.
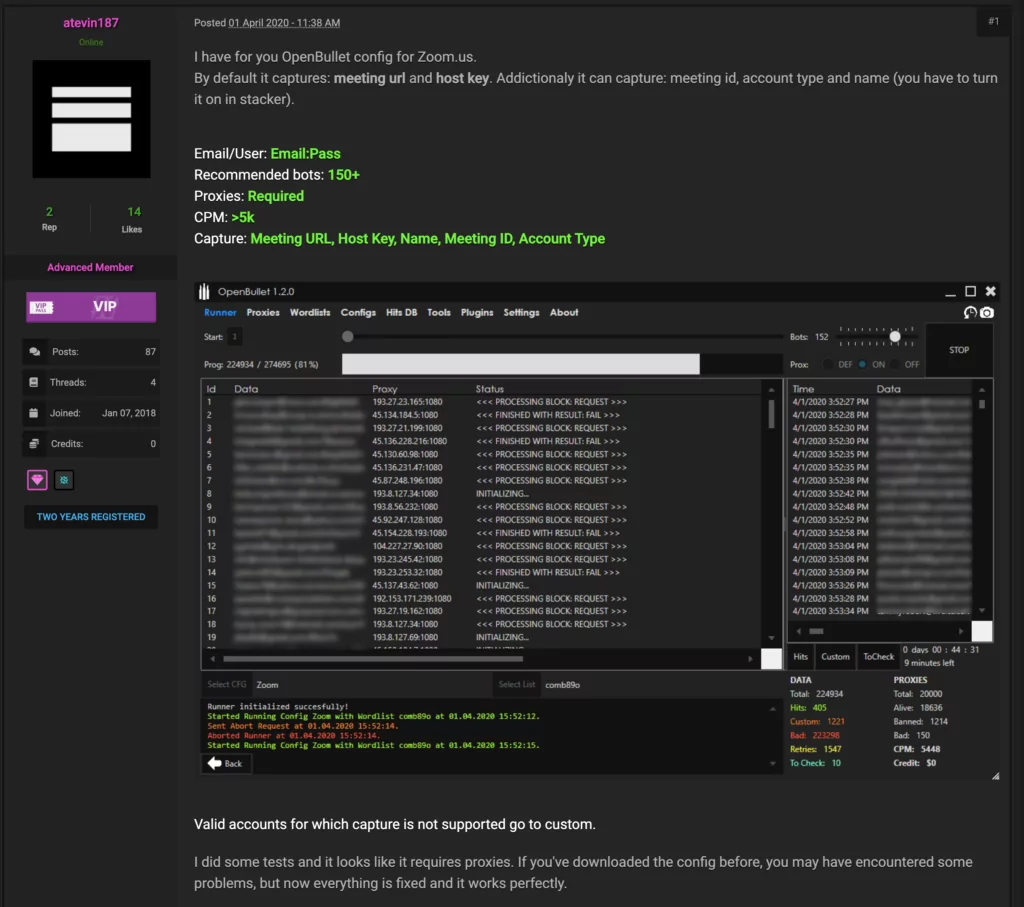
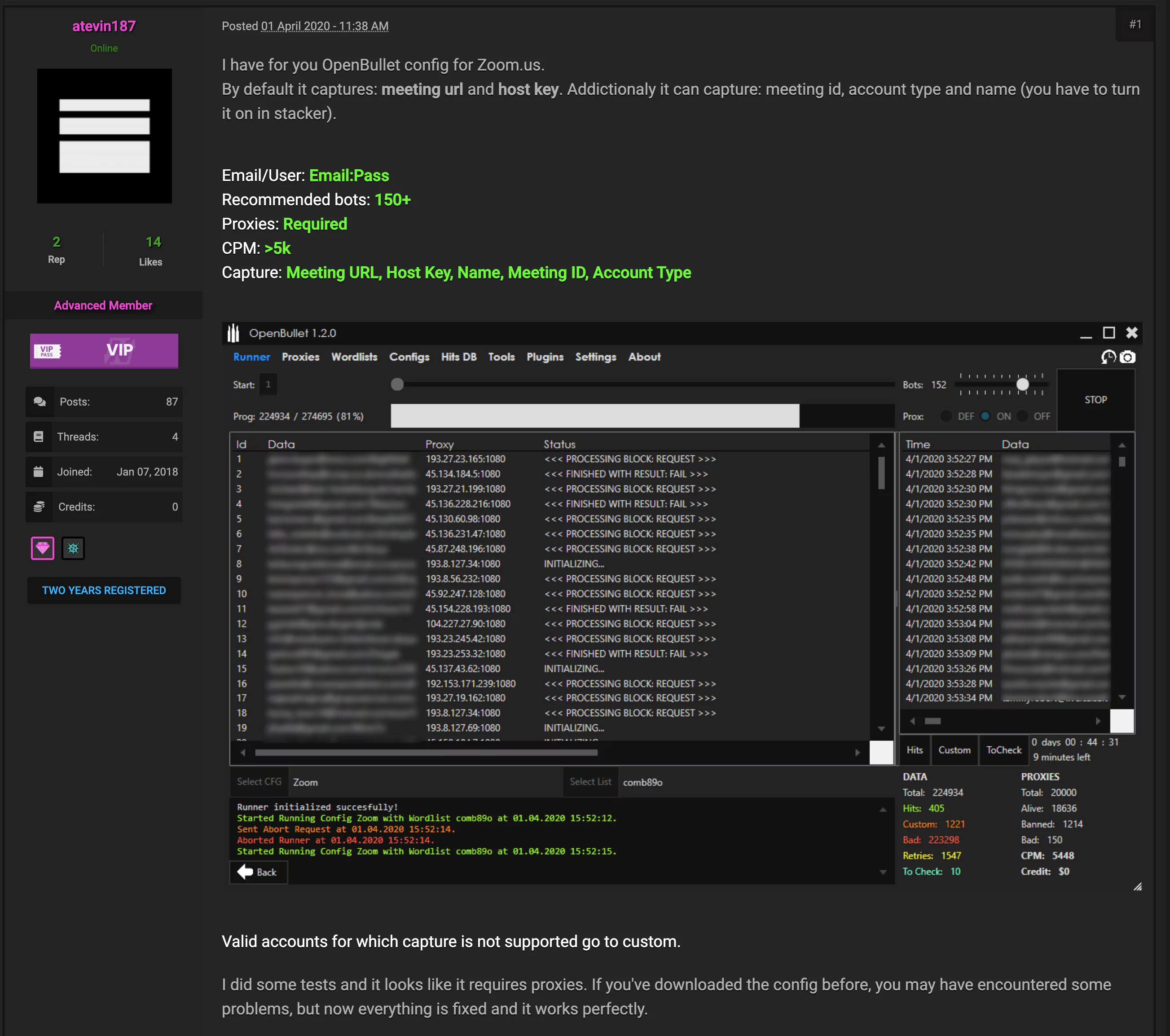
Snapshot from a dark web forum where a threat actor is promoting the specific software needed for automated login action to Zoom Platform. This was posted on April 1st, 2020.
The second aspect is anonymity where the threat actors leverage the bot-infected devices and proxy infrastructures to perform login attempts without creating unusual traffic which will catch attention. Having a Threat Intelligence Programme providing possible malicious IP addresses and IOCs from recent similar campaigns could help a lot to detect suspicious login attempts.
The third aspect could be monitoring the combo lists proactively traded on the dark web. This can be highly useful to detect potential suspicious login attempts.
Feel free to reach us out on how SOCRadar can help to mitigate the associated risks by considering the aspects described above.


































