
5 Stages of The Threat Intelligence Lifecycle
Real-time and reliable cyber threat intelligence is essential for the security functions of organizations. It is leveraged by organizations of different sizes to understand adversary behavior and stay prepared for emerging threats. Producing it is not quite easy, though. It does not come served to you in a ready-to-use form. Threat intelligence comes as an output of a 5-staged cycle.
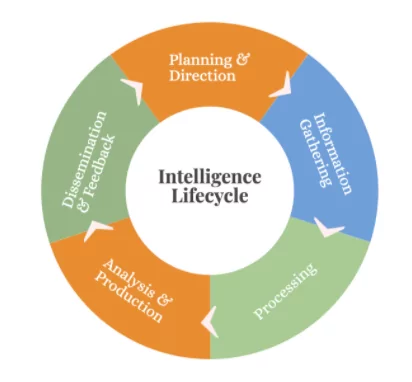
The first things you need to make clear as you start with this cycle are to identify your use cases and define your organizational objectives. Then you go on with collecting the right threat data or information, processing, and analyzing it, then finally finding the right way to deliver it to internal or external stakeholders.
Do not forget one thing! For more effective intelligence – this cycle needs to be iterative. This way, you go to the first stage again – set new objectives and find new requirements.
The five stages of the threat intelligence lifecycle are as follows: planning & direction, information gathering, processing, analysis & production, and dissemination feedback.
In this blog, we will explain in detail these five stages. Let’s start with the first one.
1. Planning and direction
The threat intelligence lifecycle starts with planning & direction. Organizations need to understand what awaits them in the following stages. They need to ask – who will benefit from the finished intelligence? Is it an analyst team, or the executive board? The answer to this question helps them prepare for what’s coming next.
Before any intel operation, organizations need to decide their objectives and ask the right questions regarding an event or action.
For instance, let’s say your organization has lately been prone to many phishing attacks. Questions you need to answer include these:
- Have these attacks ever been successful, and what is their success rate?
- What is the frequency of these attacks happening?
- Which of your employees are targets of these attacks?
- Are other organizations experiencing similar attacks?
Understanding the importance of timeliness, and prioritizing your requirements accordingly, is also part of this stage.
The direction part of the cycle indicates the goals an organization sets. Goals include the most important thing – a prioritized list of assets that need to be protected. Not just that, goals also help you define which data collection sources the company needs to leverage for more accurate and reliable results.
2. Information gathering (Collection)
Now that you know your organizational requirements, and what assets you want to protect, you can start to think about information-gathering. You can gather raw data from a variety of sources. For more accurate intelligence, you should collect both internal and external data.
Examples can be:
- Data collected from Firewalls, IDS/IPS, SIEM, etc.
- Content from news and blogs in the surface web
- Content from deep/dark web (criminal) forums
- Threat data feeds from third parties
- Threat research and reports
- IoCs (malicious IP addresses, file hashes, domains, etc.)
- Trend posts on social media about your industry
- Online interaction with cybercriminals, etc.
As you can see, the volume of this data is going to be tremendous, but the following steps will help you reduce it dramatically. For more accurate data, it is crucial to select the right tools for information gathering.
So, in this step, the analysts’ team needs to determine which types of sources, which methodologies, and which tools they need so that they can satisfy the requirements set in the first step.
3. Processing
The next step is processing the collected raw data and fitting it in a suitable format for further analysis. The large volume of data collections needs to go through a variety of processes (not necessarily all of them) so that it can be consumable for security operations:
- Organize the content with metadata tags
- Filter out as many false positives as you can
- Perform data correlation
- Decrypt
- Translate languages
- Aggregate data into suitable formats, etc.
This stage can be fully manual, automated, or semi-automated. Because manual operation can result in a waste of time, many organizations choose to leverage threat intelligence platforms (TIPs).
4. Analysis and production

The analysis production stage gives sense to the processed data. It answers the most important question: Why did an event occur?
The production part of this stage is the final output. After analyzing processed information, the CTI team presents the finished intelligence to the decision-makers of the organization. These reports must be easy to understand and consumable. Otherwise, they are useless.
It is strictly important to produce unbiased and objective analysis and to include an appropriate course of action in your reports.
Since the decision-makers can either be staff with technical skills, or non-technical stakeholders of the organizations, the CTI team needs to prepare the reports accordingly.
Various analytical frameworks are often time used to make these presentations more consumable. The Cyber Kill Chain is a very well-known framework in the cybersecurity sector. There is also MITRE ATT&CK, which extends the Cyber Kill Chain.
5. Dissemination and feedback
All the pieces of the puzzle are in place. Now it is time to share your achievements with your peers.
You may have produced intelligence but shouldn’t avoid one last thing. The final stage is the dissemination of the finished threat intelligence, and it involves getting the intel to the targeted audience through secure channels.
It is very important to use the right language when sharing the finished threat intelligence. A lack of understanding between the CTI team and the decision-makers can lead to bad results. While tactical or technical threat intelligence is for a more technical audience, strategic or operational threat intelligence is for business executives.
Another part of this stage is getting feedback on the reports you share. Feedback will boost the outcome of the next iteration of the cycle. It will also improve your security operations, as well as the overall security strategy of the organization. How is that possible? Well, whoever asked for that intelligence will review the outputs, and determine whether all requirements were met. What is next is to set new requirements for the next iteration and go on around the cycle.
SOCRadar: The best decisions in the threat intelligence lifecycle for better results
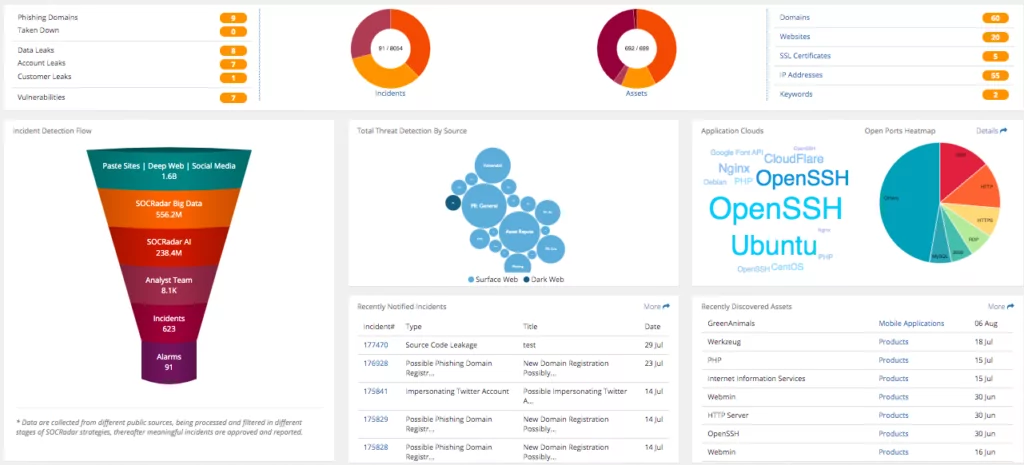
Any organization can incorporate threat data feeds into its network, but managing the analysis of all that data can be challenging. Analysts might not be sure what to prioritize, so they can end up making the wrong decisions in the end.
Every threat intelligence product aims to produce relevant intelligence and recommend mitigation.
To access reliable data, SOCRadar plans the sources from which data will be collected and keeps them updated. It has a robust AI mechanism that transforms the collected data into intelligence by analyzing it. The analysts’ team filters that information and processes it into actionable threat intelligence.
Get relevant and actionable threat intelligence. Try it now!


































