An overview of Verizon’s 2020 Data Breach Investigation Report: A Deep Look into Attacks, Attackers and Victims
For a better security posture, you need to be aware of what is going on around your industry vector and not just around your company. Thousands of breaches and millions of attacks can occur every year. Yesterday and today might have been any company, tomorrow it can be you who gets attacked. You would do great to follow up who is behind those attacks, and what was the goal of those threat actors.
Once again, for the 13th year annually, Verizon has prepared a comprehensive report with cybersecurity data.
The report itself is actually fun-to-read and does not let you get bored. But in case you don’t have time to read the whole thing (over 100 pages) and also don’t want to skip straight to your industry – here is our blog with the key findings.
A quick look into the 2020 DBIR report
Before we dig into the real findings, here are a few things about this year’s report:
- This is the 13th edition of the annual Verizon Data Breach Investigation Report (DBIR).
- The report includes incidents from the end of 2018 to the end of 2019. As you can see, it is pre-pandemic data. Next year we’ll probably have a completely different report considering the sudden changes in the digital world.
- It includes 157,525 incidents, out of which 3,950 turned out to be data breaches. It is a detailed report with over 100 pages – even without the appendices, so imagine the vast and valuable information it contains.
- The report presents a tailored analysis of different regions of the world:
- Asia and Pacific (APAC)
- Europe Middle East and Africa (EMEA)
- Latin American and Caribbean (LAC)
- North America (NA)
- The most extensive part of the report consists of incidents and data breach analysis of different industries. There are precisely sixteen industries analyzed.
Attacks: Top 5 actions
Be careful of those errors!
Now let’s get started with the real stuff. What are attackers leveraging mostly to cause incidents? Which actions help threat actors to cause breaches? Are you doing something wrong that attracts cybercriminals towards you? – These and many other questions are answered in the report.
DBIR reveals some interesting facts about Actions. Until 2017 the order of these actions used by threat actors was the same one, with a few changes in percentage. In the graph, you can see what cybercriminals utilized in breaches last year.
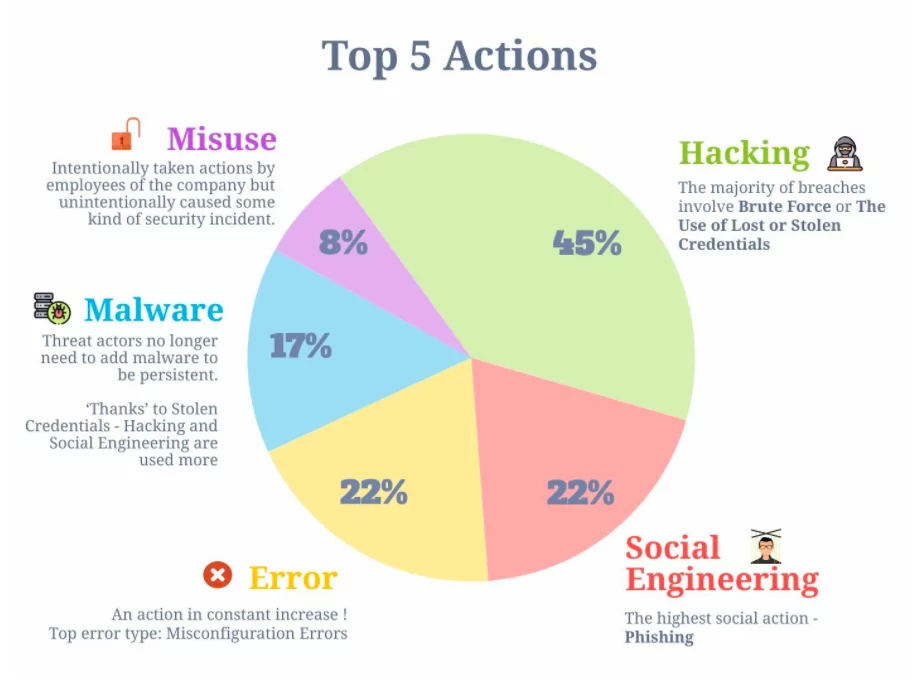
Two things require your attention:
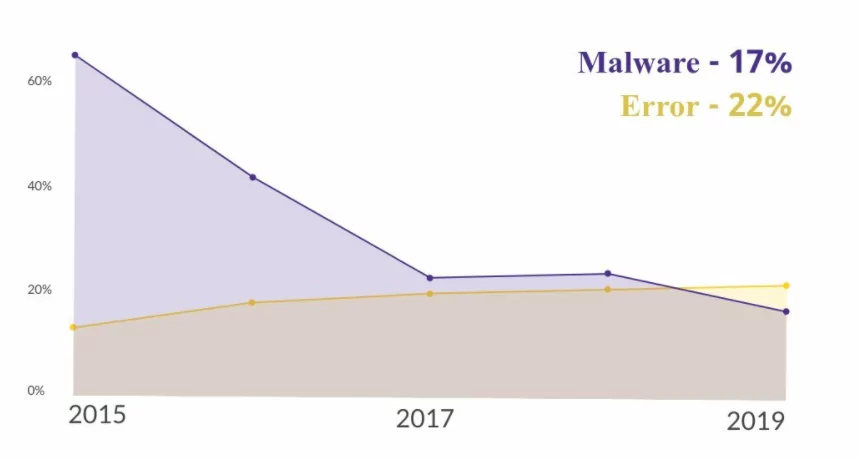
- The constant increase of errors – they are not exactly the top action that causes breaches but might be in the future. In normal circumstances and regular offices, the frequency of errors has been constantly going up. Now imagine these numbers after months of working remotely. Well, let’s wait for the next report.
- The decrease in the frequency of Malware is a bit misleading. It looks like an improvement for cybersecurity, right? Well, it is not. According to Verizon, stolen credentials used in Hacking and Social Actions has simplified threat actors’ job, so they do not need extra malware to be persistent.
Attackers: Threat actors and their motivations
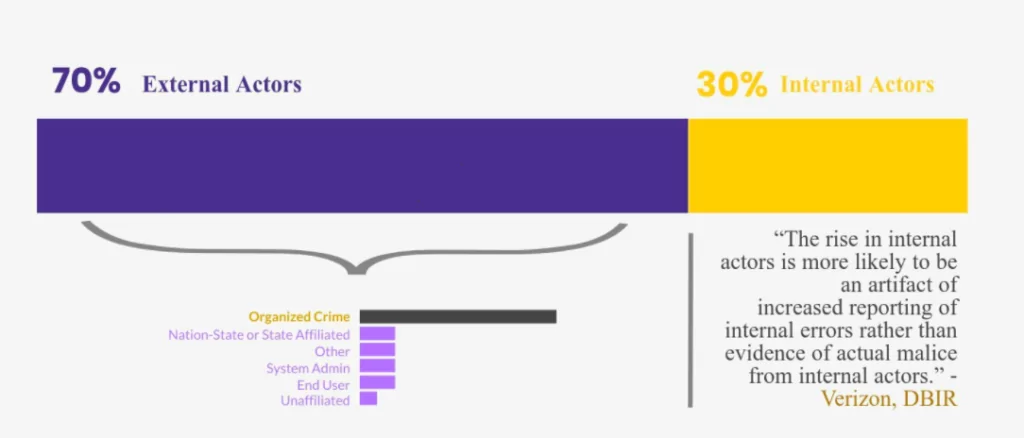
Threat actors behind the breaches can be classified into two major groups:
- External threat actors: everyone out of the company
- Internal threat actors: everyone inside the company
The DBIR report points out that many companies consider internal actors to be the biggest threat to their security, but that is wrong.
The bar graph below shows that the majority of breaches involved external actors, and the most frequent external actor variety, as you can see, is organized, criminal groups.
When it comes to threat actor motivation they can also be grouped into two:
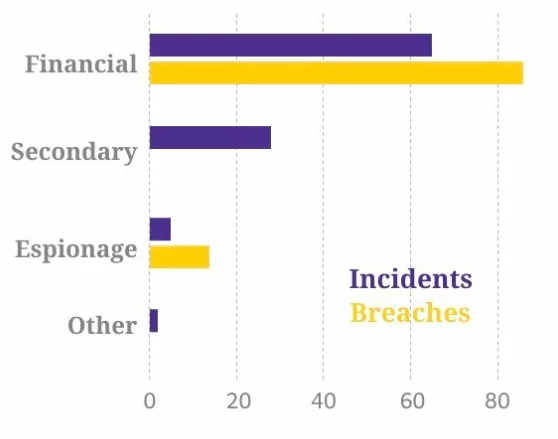
Financial motivation:both in incidents and breaches, financial motives take the lead. Although Espionage is a pretty popular motive to be attached to hackers (in books and cinema, as Verizon writes), they only cause a low percentage of the total breaches.
Secondary motivation: – Here, you are the third-party of the targeted company, but for the threat actor to reach the target, it needs to attack you first. In simpler words, it means that you are just an in-between target, not the real one.
Victims: Top 5 industries with the most breaches
At the very beginning, the number of collected breaches was a lot much higher, and Verizon points out that “100,000+ of those breaches were credentials of individual users being compromised to target bank accounts, cloud services, etc.”
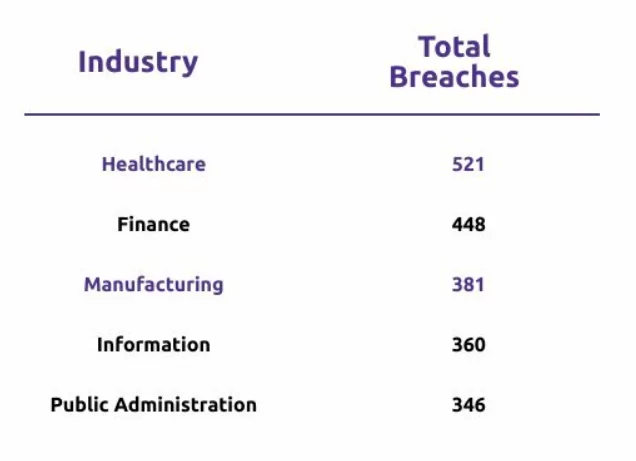
From the overall collected breaches, only 3,950 were confirmed, and not surprisingly, the highest number has occurred in Healthcare.
There is a high frequency of incidents in almost all industries (given in the table below). However, a more important number is the frequency of breaches.
More than half of the incidents that resulted in the Healthcare industry somehow managed to become breaches. A similarly high proportion is seen in the Manufacturing industry as well.
Stay prepared for 2021!
As we mentioned in the beginning, the 2020 DBIR contains information about breaches that occurred in 2019. However, the pandemic we are still fighting has made enormous changes in the world. You can guess even the way threat actors do their job has had changes.
The 2021 DBIR will probably bring different numbers.
SOCRadar detects the data breaches and informs you if any data leakage that belongs to your company will be encountered amongst those breach datasets.
Be one step ahead of attackers, and do not become a victim.