
Different Types of Threat Intelligence: What is It & Who is It for?
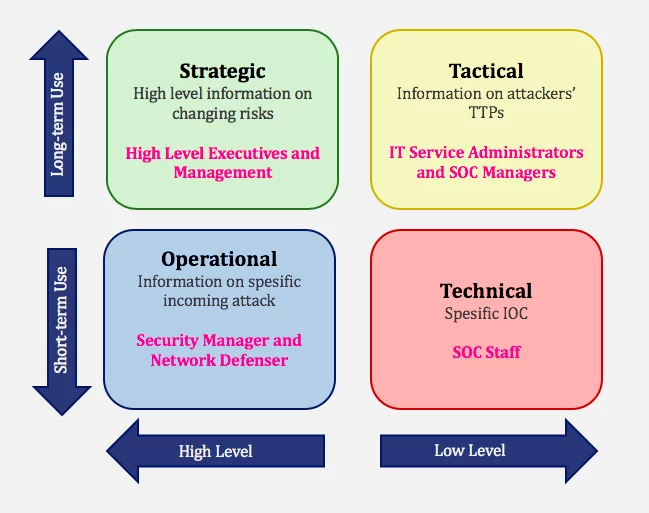
The information provided by the threat intelligence, it makes a significant contribution to various business decisions in organizations. The information presented to the organization from an outside perspective is important to require action in internal processes. It is crucial to categorize intelligence for the best management of information collected from different sources. Categorization is necessary for intelligence to reach the target. Threat intelligence falls into 4 categories within the framework of applicable information: Strategic, Tactical, Operational, and Technical. For these 4 types of intelligence, data collection, analysis, and consumption of intelligence differ. SOCRadar® generates intelligence at different levels with the information it collects and ensures the best use of information.
Strategic threat intelligence
Strategic Threat Intelligence provides a high level of information on the cybersecurity posture, threats, financial impact of cyber activities, attack trends, and their impact on business decisions. The information obtained can be used by senior executives at the company, such as CISO. The purpose of Strategic Threat Intelligence is to manage existing cyber risks and unknown future risks. This intelligence offers a risk-based approach. It focuses on the effects and possibilities of risks. The information provided here is suitable for long-term use. It helps in making strategic business decisions. For example, it can evaluate these results when deciding on budget / employee / product balance in protecting critical assets. Data collection sources for strategic intelligence are also high-level sources: OSINT, CTI vendors, and ISAO / ISACS.
- Strategic intelligence provides a high level of information.
- Information provided by intelligence can be used by high-level managers.
- This information is suitable for long-term use.
Strategic intelligence provides to answer questions such as:
- What is the financial impact of cyber attack?
- What are Trend Threat actors and attack trends?
- What are the statistical information about data breaches?
- What are the cyber attacks for companies in the same industry?
- Have there been cyber attacks against our organization in the past, what has been the effect?
SOCRadar® provides reports that include past leaks, phishing domains, SSL grades, and more, available to high-level cybersecurity administrators. It also offers areas where threat actors can be monitored.
Tactical threat intelligence
Tactical threat intelligence provides detailed information on the tactics, techniques, and procedures of threat actors. It is predominantly for a technical audience and helps them to understand how their networks are attacked based on the latest methods attackers used to achieve their goals. It provides information that can be consumed by security experts such as IT managers, SOC managers, NOC managers. These employees use tactical cyber intelligence to understand the technical capability and objectives of the offensive and identify their detection and mitigation strategies. Tactical cyber intelligence is collected through malware and incident reports, attack group reports, human Intelligence, and campaign reports.
- Information provided by intelligence can be used by technical managers.
- This information is suitable for long-term use.
- Tactical intelligence provides low-level information.
Tactical intelligence provides to answer questions such as:
- What is the cyber attacker’s TTP?
- What are the goals of the cyber attacker?
- What mitigation strategies can be provided for incoming attacks?
SOCRadar® keeps track of cybersecurity incidents and informs organizations about attackers’ TTP. It also provides companies with incident reports.
Operational threat intelligence provides information to the managers of the defense teams about the specific threat to the company. People like head of network defenders, fraud detection manager incident response team manager understand the attack effect With incoming intelligence, it is attempted to identify the threat actor and to determine his capabilities and threatened IT assets.
In operational threat intelligence, information is collected through hacker forums, chat rooms, social media, and the current cyber attack. The attack that may come with the collected information is estimated, and protection planning is issued.
- Operational threat intelligence provides high-level information.
- The information provided by the intelligence can be used by the managers of the defense teams.
- This information is suitable for short-term use.
Operational threat intelligence provides to answer questions such as:
- What is the specific threat to the organization?
- What are the IT assets with weaknesses?
- What will be the effect if the incoming attack is successful?
SOCRadar® monitors thousands of hacker forums and Blackmarket at Surface/Dark Web. Also, SOCRadar® follows published weaknesses for company products detected by digital footprint and generates an alarm by providing information about it with its. It helps organizations to be more informed and resilient against cyber-attacks and protects them against potential attacks they may experience.
Technical threat intelligence
With technical cyber intelligence, information about the attacker’s resources such as command and control channel, tools are collected. For example, it focuses on phishing emails or technical tips that indicate the cybersecurity threat to fraudulent URLs. The aim is to collect information about specific IOCs (IP address, phishing email header, hash checksum). This type of threat intelligence is important because it allows to analyze attacks. However, the value of technical threat intelligence is short-lived, as hackers often change their tactics. IOCs that are detected and analyzed at the right time are important. Tactical intelligence is used by employees in the SOC team. Thanks to the information obtained here, new rules are written in the current security products of the organization (such as IDS / IPs, firewall, endpoint security system). Also, suspicious IPs are detected by spam emails. The information obtained here feeds the products of the organization directly.
- Technical threat intelligence provides low-level information.
- Technical threat intelligence provides low-level information.
- Information provided by the intelligence can be used by SOC employees and IR employees.
- This information is suitable for short-term use.
Technical threat intelligence provides to answer questions such as:
- What are IOCs in Active Attack?
- What are IOCs in active attacks on similar organizations?
- Can defense systems be fed with the indicators taken?
SOCRadar constantly searches the open wide internet for malicious file hashes, domain registrations, suspicious IPs collects them, and presents them to SOC teams with an easy-to-use API.
Try for free SOCRadar® Community Edition
With SOCRadar® Community Edition, you’ll be able to:
- Spot malicious/typo-squatted domains targeting your business
- Know if your employees’ credentials have been compromised in the latest data breach
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.


































