
Different Definitions of Threat Intelligence and Gartner’s Perspective
Cyber threat intelligence defined
Cyber threat intelligence is information and intelligence gathered from outside sources, required in taking internal actions. With relevant and real-time intelligence, it helps organizations of different sizes, carry out protective measures, and keep their confidentiality. Being used to understand adversary behavior, TI helps organizations be prepared for emerging threats, this way it creates an essential contribution to overall security functions.
These days, creating a threat intelligence environment or leveraging real-time, ready-to-use feeds from vendors are one of the most critical decisions organizations should take. Threat intelligence definitions can be slightly different from vendor to vendor, however, in essence, they go around the same idea – TI is the basic intelligence source for protective measures against evolving cyber threats.
FireEye states that cyber threat intelligence is “evidence-based knowledge about adversaries – their motives, intents, capabilities, enabling environments and operations – focused on an event, series of events or trends, and providing a ‘decision’ advantage to the defender.” As we can see FireEye focuses on adversary actions and capabilities and emphasizes it being the decisive threat intelligence that organizations ought to leverage, for better security functioning.

Crowdstrike focuses on a similar case just like FireEye. It defines it as the required intelligence “to understand a threat actor’s motives, targets, and attack behaviors”.
Digital Guardian makes sure organizations understand that “…it’s not the same as raw data, which has to be analyzed first for gaining actionable insights.” They define threat intelligence as “…what becomes of raw data after it has been collected, processed, and analyzed so it can be used for making informed decisions. It is accurate, actionable, relevant, and timely.”By saying that TI is “information an organization uses to understand the threats that have, will, or are currently targeting the organization”.
Forcepoint emphasizes that it is leveraged to get intelligence relevant only to the organization.
Ec-council has a similar approach to what threat intelligence is. More specifically, they use the phrase “…meaningful information about existing or emerging threats targeting the organization that helps mitigate risks.”
Gartner’s definition
“Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications, and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.”
Gartner gives a better ‘big-picture’ of what threat intelligence is by gathering the technical detail, contextuality, and mitigation in one place, to describe a threat and direct you towards proactive measures.
Four threat intelligence types
Threat intelligence is gathered through different sources and different tools, however, depending on the functions needed to be served, TI falls into four categories:
- Strategic
- Tactical
- Operational
- Technical
However, hackers are not the only users and shouldn’t be. The reason behind this amazing tool is to help organizations protect their data. So, just like attackers find information to attack, enterprises can find information to protect. Everything mentioned above (sensitive information, credentials, and so on), if first found by the owner, will be in safe hands. It means that something important has leaked, and you finding this security hole before the hacker, will prevent the risk.
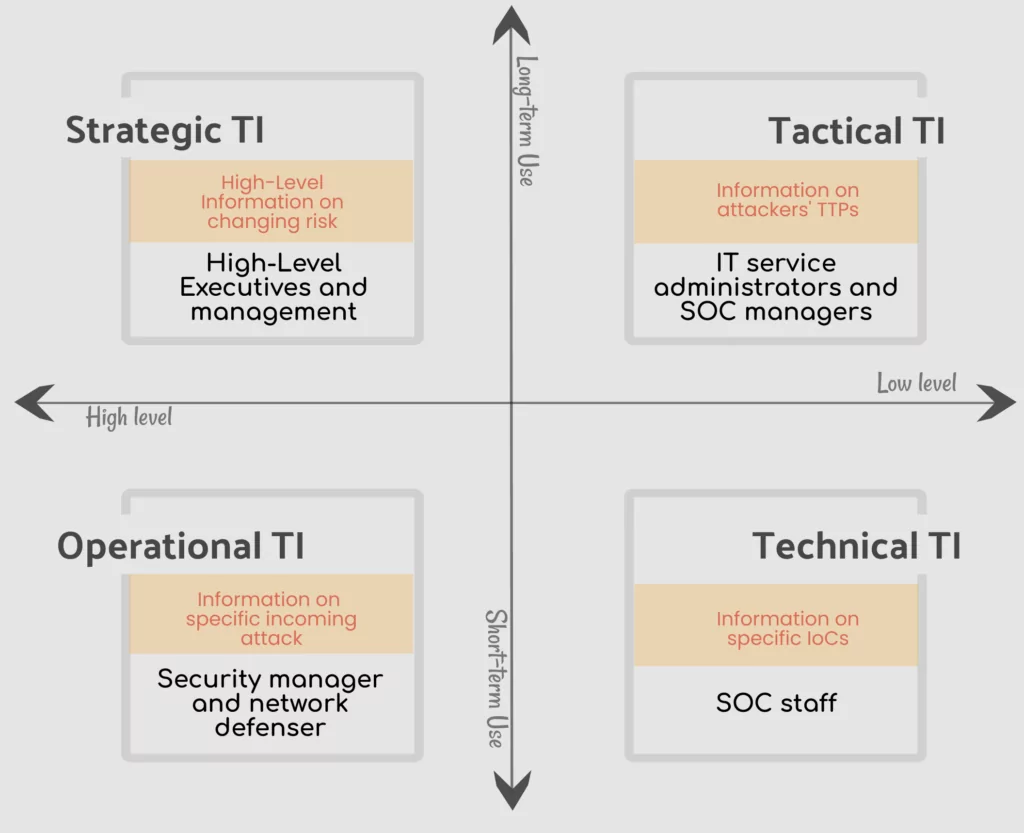
1. Strategic TI
It gives a higher level of information – providing a general overview of the threat landscape. It also provides information about the impact of attack trends on business decisions and finances. This makes it more relevant for higher executives, to help them with defining new strategies for the security functions of the organization. It offers a risk-based approach, by focusing on the effect and possibilities of risk.
2. Operational TI
It is another higher level of intelligence source, which focuses on knowledge about a specific threat to the company. It provides detailed insights to network defenders, fraud detection manager, IT team managers, and similar higher roles in the security operations. Operation TI is provided from information gathered in hacker forums, chat rooms, discussions, etc. which as a result describes how an attacker operates, and how a specific cybercrime is carried out.
3. Tactical TI
This is a lower level, more detailed information. More specifically it gives insight into the technical capabilities of an adversary – its TTPs. Being more detailed, it is intended for a more technical team – IT managers, SOC managers, NOC managers, and similar roles. It is essential, to help them create or update their defense strategy. Just like the result is detailed and technical, the sources where it is gathered are too. It is gathered from malware and incident reports, or different attack group reports, and human intelligence.
4. Technical TI
It is a slightly more detailed intelligence resource than Tactical TI. It gives specific indicators on an attack and helps security professionals analyze those attacks to write new rules in the current security products, like firewalls or endpoint security systems. Technical TI includes reported IP addresses, phishing information, malware samples, malicious URLs, hashes, etc. However, this is short-term information, because threat actors tend to constantly change their tactics.
SOCRadar – Cyber threat intelligence capabilities
SOCRadar collects information from a range of sources and generates intelligence at different levels. It provides reports intended for higher-level security admins, about data leaks, phishing information, and similar significant information. It collects vulnerability information and presents it in an intuitive dashboard.
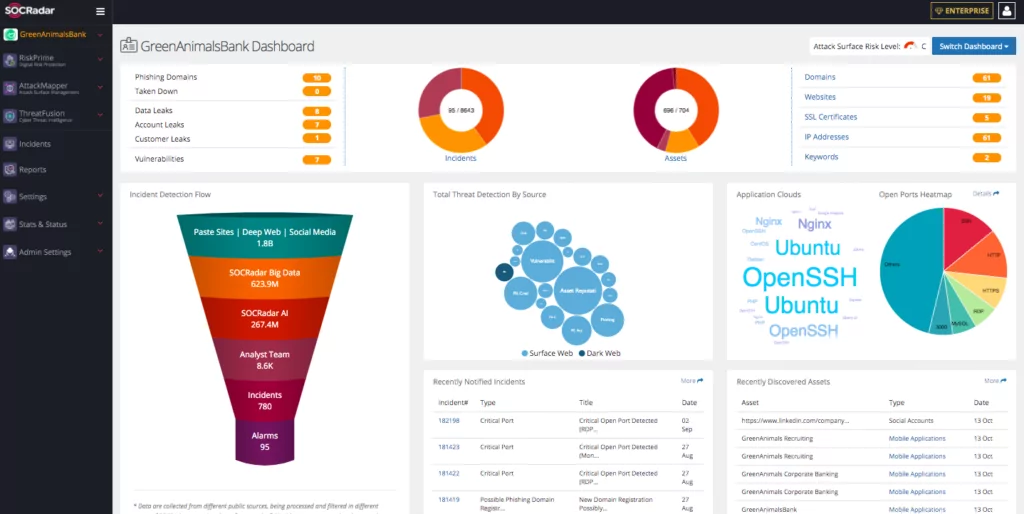
SOCRadar updates adversary TTP and provides companies with incident reports to be prepared for emerging threats. It also presents malicious file hashes, URLs, domain registrations, suspicious IPs, hacked websites, botnets, and similar indicators, which can also be integrated into other security technologies through a ready-to-use API.
Gartner is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s Research & Advisory organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.


































