How To Detect and Prevent Business Email Compromise (BEC) Attacks?
What’s business email compromise and why is it dangerous?
BEC is an attack in which an attacker gains access to a business email account and imitates the identity of the owner in order to defraud the company, its employees, customers, and partners.
Unlike phishing attacks, high-level employees involved in finance or wire transfers can be compromised or falsified to make fraudulent transfers, resulting in losses of hundreds of thousands of dollars.
In 2016, BEC attacks led to losses for companies worldwide averaging $140,000. According to a National Security Agency (NSA) report, casualties in the US alone amount to more than $1.5 billion.
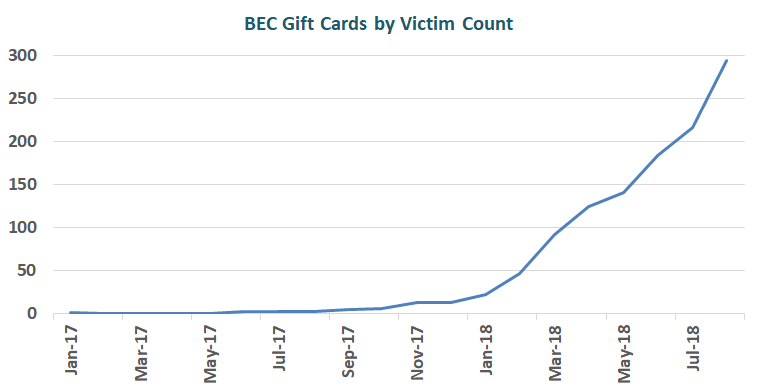
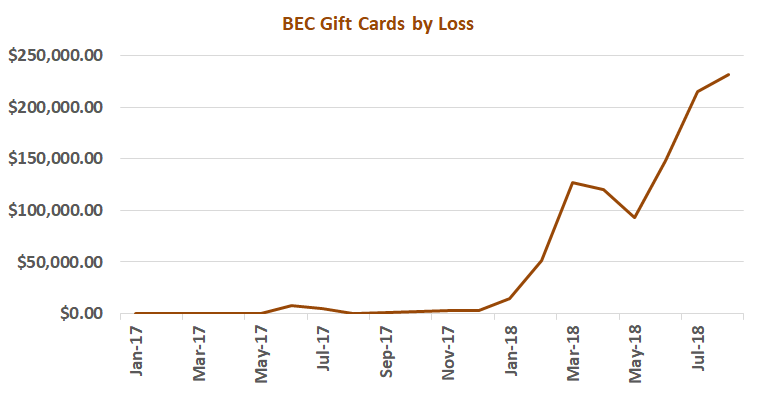
Increased BEC cases for victims to buy gift cards were obtained from the Internet Crime Complaint Center (IC3) in 2017.For any personal or business purposes, the victims got a spoofed email or telephone call from an official who ordered the individual to buy several gift cards.
A total of 1,164 complaints were filed with IC3 between January 1st, 2017, and August 31st, 2018 with an adjusted loss of $1,021,919. Although the average reported loss per incident was less than $900, the number of complaints reporting fraudulent gift card requests increased by over 1,240% between January 1st, 2017 and August 31st, 2018, with over 90% of incidents reported between March and August 2018. This scenario did not register as a measurable trend in 2017.
In 2019, things were getting very serious about BEC attacks. The following statistics were reported in victim complaints to the IC3 between June 2016 and July 2019:
| Domestic and international incidents | 166,349 |
| Domestic and international exposed dollar loss | $26,201,775,589 |
The following BEC/EAC statistics were reported in victim complaints to the IC3 between October 2013 and July 2019:
| Total U.S. victims | 69,384 |
| Total U.S. exposed dollar loss | $10,135,319,091 |
| Total non-U.S. victims | 3,624 |
| Total non-U.S. exposed dollar loss | $1,053,331,166 |
The following statistics were reported in victim complaints to the IC3 between June 2016 and July 2019:
| Total U.S. financial recipients | 32,367 |
| Total U.S. financial recipient exposed dollar loss | $3,543,308,220 |
| Total non-U.S. financial recipients | 14,719 |
| Total non-U.S. financial recipient exposed dollar loss | $4,843,767,489 |
Between Jan. 1, 2018, and June 30, 2019, with a total reported loss of $8,323,354. The average dollar loss reported in a complaint was $7,904. The dollar loss of direct deposit change requests increased more than 815 percent between Jan. 1, 2018, and June 30, 2019.
Adversaries exploit cloud-based email services by using BEC scams that cause more than $2 Billion costs just in the US. Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling more than $2.1 billion in actual losses from BEC scams using two popular cloud-based email services.
How adversaries carry out BEC scams?
The scam is frequently carried out when a subject compromises legitimate business or personal email accounts through social engineering or computer intrusion to conduct unauthorized transfers of funds.
The attackers use advanced social engineering tactics and techniques, including spear phishing, to gain access to corporate email accounts and send fraudulent emails to steal money from the target company. The first part of the scam usually consists of targeted phish attacks on the email addresses of senior executives. For example, a C-Suite manager could be targeted by a phishing attack that installs a Remote Access Trojan (RAT) to obtain access data and other useful business information.
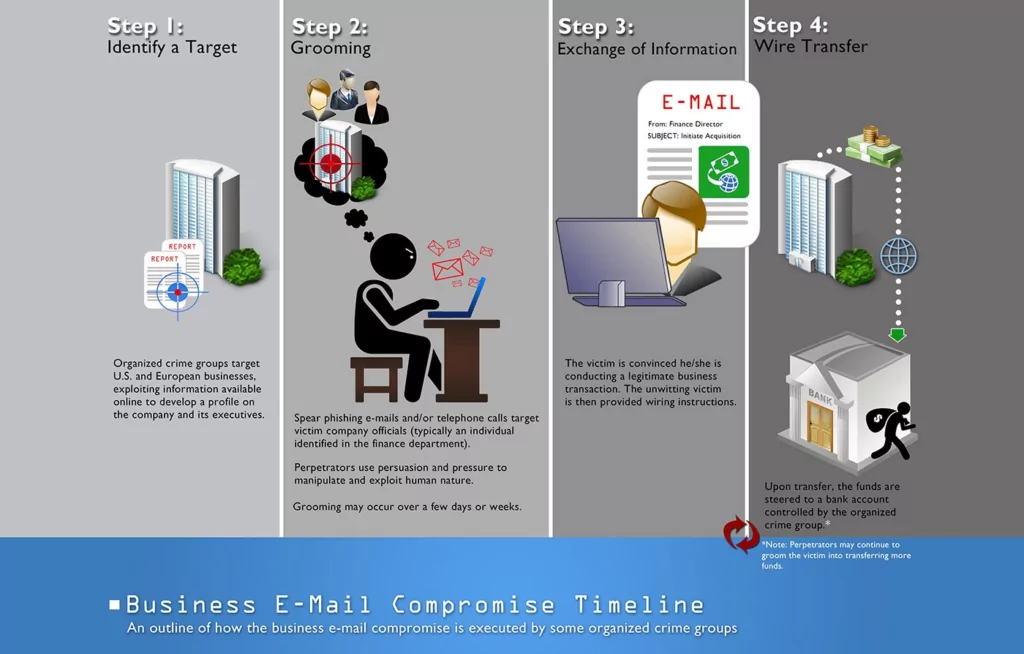
Basically, BEC takes a place in 4 steps;
- Identify Target
- Creating typosquat domain: Adversaries make people believe that an email address or a website is authentic creating slightly different variations of original ones. Such as arnazon.com, faceb00k.com, netvvorksolutions.com, etc. They can use leaked email accounts for this step to make it even more realistic.
- Send spear-phishing emails: These emails seem to be sent from a trustworthy source to make victims disclose sensitive information. This knowledge helps offenders to access BEC profiles, schedules, and data and supply them with specifics.
- Using malicious software: Finally, adversaries inject malware to organizations that let them gain undetected access to sensitive data, including passwords and business secrets.

SOCRadar is ready to help
Just using firewalls or antivirus software won’t protect you from BEC scams but sophisticated and advanced cyber threat intelligence (CTI) can. SOCRadar provides big-data powered and AI-based solutions.
How SOCRadar can help you against BEC scams
Identifying typo-squat domains
AI-enabled SOCRadar Digital Risk Protection platform analyzes millions of domains across most major domain registrars to detect malicious domains targeting your brand and entire business network. Alerts are triggered whenever anything changes on the detected suspicious domain. Machine learning algorithms allow SOCRadar to analyze a vast collection of domain data to unveil lookalike domains. At the same time, real-time alerts will enable you to get notified before your domains and SSL certificates are expiring keeping your digital presence secure.
SOCRadar not only analyzes registered domain names for fakes and look-alikes but also tracks whether they get an SSL certificate. That can also be a significant sign of attack initiation.
Detecting email leaks
SOCRadar draws on a growing collection of data then through advanced analytics algorithms and a team of talented analysts, it helps organizations to know if their employee email addresses, credit card information, or customer’s user account login details have been compromised. Regularly, the credit card information is traded on the Internet, especially on the dark web. You can take action against fraud beforehand with the SOCRadar Credit Card Leakage monitoring module and its on-time alarms.
If email addresses and passwords of employees of an organization are in a leak in the deep web, SOCRadar generates and sends alarms to those organizations to take necessary measurements and steps without losing any time.
Threat Feed
Threat actors are closely monitoring vulnerability trends as much as your public-facing services and technology to find the easy way in. To prevent them disrupt your business, get alerted whenever there’s a new critical vulnerability or exploit for the pre-defined product components and technologies associated with your auto-discovered digital footprint. See which vulnerabilities are being leveraged by threat actors. SOCRadar can help you to get actionable insights and context on potentially vulnerable technologies to speed up the assessment and verification processes.
With Threat Feed, by blocking newly purchased domains via Firewall, Antispam GW, etc. It prevents mail from suspicious domains to be sent and received.
To protect your organization from BEC scams, you can register 1 domain for free to SOCRadar community edition.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.