
How Pandemic Affected Information Security

New work order: Remote workforce
The COVID-19 virus, which emerged in the last months of 2019 and caused the announcement of a pandemic, led to a sudden change in daily norms for companies and employees, and the whole life was deeply affected. Many companies either didn’t have “Business Continuity Plans” or were not prepared to implement them with all their workforce and operations. In order to prevent the spread of the pandemic, strict measures were implemented one by one all over the world and new methods enable employees to contribute to the workforce remotely for the continuation of daily operations and business continuity. Among these, there are examples such as conducting meetings in online environments with teleconference solutions, using cloud-based infrastructures to provide easy access to data, and adapting VPN-based technologies to protect confidential data. Perhaps cyber attackers adapted first to this new working order and developed new strategies to exploit the vulnerabilities of these applications whose use has increased in this process.
Information security during pandemic

The pillars of information security policies are confidentiality, integrity, and availability, known as the CIA triad. Information security experts work to ensure the confidentiality, integrity, and availability of personally identifiable information (PII) and sensitive information.
However, moments of crisis often cause an increase in cyberattacks and security breaches. It has also been observed during the time of the COVID-19 pandemic when cybercriminals took advantage of the crisis to steal many sensitive and confidential information, including credit card data, username, and passwords.
The spread of the coronavirus was accompanied by a further increase in cyber attacks against individuals who work remotely, government agencies, and national and international medical facilities. With the increase in the number and impact of the threats, more warnings were made by the intelligence and law enforcement agencies, and measures were taken in this context.
In a joint declaration published by the relevant cyber security units of the USA and the UK, attention was drawn to the activities of hackers who wanted to turn the crisis environment into an opportunity. Among these activities, particular emphasis was placed on the increase in the pandemic process of digital phishing and ransomware attacks, as well as distributing malware through fake video conferencing and remote access applications. Also recently, the FBI and Interpol have issued recommendations warning of ransomware attacks and cyber-espionage operations targeting medical institutions that openly participated in research on government-sponsored hackers. Internal warnings have been reported by NASA to its employees by conveying information about the attacks in this process. According to the FBI and India’s national CERTs, malicious actors interrupted online school classes and collected personal data from these recordings. In response to the warnings, many government agencies and global companies have implemented security restrictions, including Google, SpaceX, the US Senate, the Taiwan government, the German Foreign Office, and the Australian Department of Defense banned the use of certain applications.
Cyber attacks during pandemic
Ransomware attacks

Cybercriminals are becoming more and more subject to COVID-19, which abuses the fears of customers about the pandemic and the welfare of their loved ones.
Remote working increases the risk of a successful ransomware attack significantly since with remote work it is hard to ensure security at home and a higher likelihood of users clicking on COVID-19 themed ransomware emails. Security researchers reported that 4,000 cyberattacks a day since the COVID-19 pandemic.
Skybox Security published the mid-year update to its 2020 Vulnerability and Threat Trends Report.
Key findings from the report include:
- 20,000+ new vulnerability reports predicted for 2020, shattering previous records
- 50 percent increase in mobile vulnerabilities highlights the dangers of blurring the line between corporate and personal networks
- Ransomware thrives during the COVID-19 pandemic, with new samples increasing by 72 percent
- Attacks on critical infrastructure, including healthcare companies and research labs, have added to the chaos
In early June 2020, Honda reported technical difficulties for its customer support and financial services units and later confirmed cyberattacks. Garmin users claimed in July that there were widespread outages, which it would later claim were the result of a cyber attack. The attack was claimed to be the work of the Evil Corp, the Russian group. The Maze ransomware gang in an attack that stole “10 terabytes of data, private databases, etc.’” allegedly targeted Canon in August.
Fake domains and web pages

US President Donald Trump mentioned some drug names (hydroxy-chloroquine, Plaquenil, azithromycin, etc.) that could be used in the treatment of COVID-19 at a briefing on March 19. Immediately, hackers began to build websites by using fake domain names containing these drug names. There has been a tremendous increase in the number of fake websites created during the pandemic. Although these fake web pages were taken down as soon as they are detected by national CERTs, the attackers try to continue their activities by acquiring other similar domain names.
Phishing attacks

According to a report named “COVID-19 Clicks: How Phishing Capitalized on a Global Crisis” by OpenText;
- On average, survey respondents receive approximately 70 emails per day, a 34% increase over last year. More emails mean more opportunities for attack and more cognitive load to discern what’s legitimate and what’s a fraudulent request.
- One in five respondents received a phishing email related to COVID-19.
- 45% of people are shopping online more often, although 68% believe that there is a greater risk their credit and financial information could be exposed.
- 42% have accessed their backed-up data to recover a file since COVID-19 began, as more people connect from home on new or additional devices and need to retrieve their files.
End-point attacks

Endpoints are the access point to an organization’s data, credentials, and environment. During the pandemic, endpoints for remote access have increased due to remote work, so the targeted surface areas for cybercriminals have also increased. Endpoint security is a critical issue as most data breaches and malware infections occur on end-user devices.
Phishing attacks from 2,000 to 90,000 between March 8 and April 12 alone and this 4,500 percent increase in attempted endpoint attacks is an unfortunate side effect of the “new normal.”
Attacks on e-learning systems

During the pandemic, many schools and training centers have started to use the distance learning system and use the technological infrastructures for it. These systems have also been exposed to the increasing attacks of cybercriminals and many data including the records of training sessions have started to be shared on the Internet. Most of the videos contain voices, faces, and contact numbers of the participants, and other personal data. In addition, in this period grades are also required to be kept online, some cyber hackers have started to offer services to increase the course grades by infiltrating the systems for a fee.
In September 2020, Rialto California schools were shut down for a week due to a cyber attack.
The attack was conceived in order to interrupt or obtain access to a school network, and the 25,500 student district even forced thousands of computers issued by the school to collect and restore.
DDoS attacks

Cyber attacks on health ministries, research laboratories, and hospitals have increased significantly, security units around the world said that hackers are trying to obtain intelligence on national and international health policy or to obtain sensitive data on COVID-19 related research. Some attackers either blocked access to the web pages of these medical institutions and organizations by DDoS attacks in order to gain financial income or they encrypted sensitive patient/hospital data with ransomware attacks and demanded money to access this data.
While hospitals in the Czech Republic announced that they had prevented cyber attacks on their systems, access to Italy’s social security site was blocked for a while. The World Health Organization reported that cyber attacks on its networks increased five times compared to the same period last year.
Dark web sales

Cybersecurity researchers have discovered several virtual marketplaces on the DarkWeb where counterfeit COVID-19 vaccines, diagnostic kits, and plasmas allegedly obtained from people who had survived the disease were offered for sale. It has also been observed in these markets that vendors have also diversified their lists to include sales of face masks, hand sanitizer, and now chloroquine.
Attacks on teleconference applications

Recently, thousands of online meeting recordings have been found to be accessible on the internet without any protection. It is also known that much sensitive information is shared in these records. In addition, following the attacks on these teleconferencing applications where user information (username and password) was captured, it was put up for sale on the internet.
Just after the COVID-19 outbreak Zoom’s daily active users increased from around 10 million to 300 million. One of the biggest problems with Zoom has been “Zoom bombing,” in which uninvited participants crash a Zoom meeting and disrupt it. Many sensitive data was stolen during these meetings.
COVID-19 malware
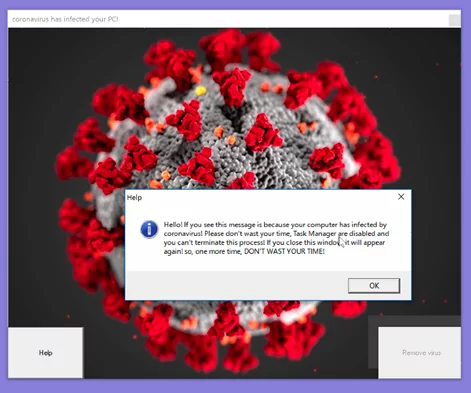
Security researchers recently analyzed a coronavirus-themed malware that invalidates a system’s boot record (MBR) and renders it non-bootable. When this malware runs, it automatically reboots the machine and then displays a virus-themed window that cannot be closed. The normal exit button at the top right of the window is not functional.
VPN attacks
According to recent reports RDP and VPN use skyrocket during the pandemic. RDP use is up by 41%, enterprise VPN use is up by 33%.
Existing VPN encryption protocols can be robust and provide important protection. However, nothing is 100% immune to attack. Traditionally, Internet Key Exchange (IKE) used in VPNs is among the targets of attackers.
Most VPN service providers recommend storing authentication data for their customers, which can pose security risks that contain important information such as usernames and passwords. This situation is very critical and undesirable in terms of information security. In addition, error messages and packet headers can give attackers very important information about the type and version of the VPN version.
SOCRadar can help
Threat actors are closely monitoring vulnerability trends as much as your public-facing services and technology to find the easy way in. To prevent them disrupt your business, get alerted whenever there’s a new critical vulnerability or exploit for the pre-defined product components and technologies associated with your auto-discovered digital footprint. See which vulnerabilities are being leveraged by threat actors. Get actionable insights and context on potentially vulnerable technologies to speed up the assessment and verification processes.
SOCRadar notifies and informs you immediately when;
- Critical ports are opened such as RDP port,
- There is a critical vulnerability for your attack surface,
- Any sensitive information or data are available about your organization on the dark web.
SOCRadar vulnerability intelligence;
- Tailored for you: Select products and technologies you’d like to monitor.
- CVE trends: See the worldwide vulnerability trends by monitoring millions of tweets.
- Instant alerting: Rapid data collection, structuring, and analysis to notify on-time.
- Filter and search: Find vulnerability information by filtering based on keyword, CVSS score, or report time.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.



































