How Credential Stuffing Let To Hack Trump Campaign Website?
The billions of login credentials available on the dark web make it easy for cybercriminals to steal login credentials. It has been widely reported that automated access data – the plug-in attack has found its way onto the internet – is hitting systems such as bank accounts, and credit card numbers.

With billions of compromised credentials already circulating on the dark web, attacks to cram credentials can be easily carried out. Restriction of access is the use of stolen access data to several other websites and is one of the most common forms of access theft on the darknet. With the ability to steal credentials, a criminal who carries out an attack with credentials stuffed with a tool like Sentry MBA could expect to compromise approximately 10,000 accounts on targeted, compromised websites.
What’s credential stuffing?
Credential Stuffing is a technique that involves an automatic injection attack to access online services with stolen credentials. In an attack on the login data, fraudsters use to access consumer accounts to make fraudulent purchases, carry out phishing attacks, and steal information and money.

While credentialing is an automated process used in botnets, login systems for websites can add another layer of security by recognizing which platform the login request originates from. Hackers can then create automated scripts and use configurable credentials – and use software to systematically test whether the stolen credentials successfully log in to the landing page.
However, the credential stuffing uses known password-login-credentials combinations to make the process successful, not the references that make it successful.
How credential stuffing works?
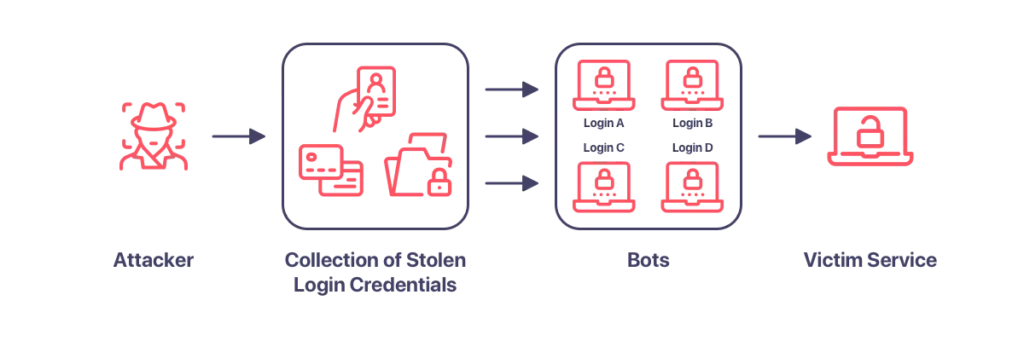
To carry out a large-scale attack on the credentials, malicious hackers use bots that fake different IP addresses and can automatically enter multiple accounts in parallel.
Credential Stuffing attacks take advantage of this behavior, relying on people to use matching passwords for multiple online accounts. A single character – one (SSO) minimizes the number of credentials – thwarted attacks because users must log in with only one set of credentials and then log in to other accounts. Login Data – The fill-up tactic is driven by many people using the same username and password combinations on multiple websites.
When confirming access, a user’s password combination is only tried once before they continue, ergo only once per login. A single failed login will prove to be a repeat attempt, but if you log in multiple times in a row with the same combination, you will likely experience an attack with raw credentials.
Stolen references have become the fuel that allows a credential – a stopper attack – to launch on a scale and scale that is nothing more or less unprecedented in terms of the number of attacks and level of sophistication. Although the attacks with credentials are due to a human problem, there are a number of educational and technological solutions that organizations can implement to reduce the risk of falsification.
What are the differences between password spraying and credential stuffing?
Unlike password spraying, “credential stuffing” is a brutal attack defined as a technique for taking over accounts that involves automated password permutations. Simply put, cybercriminals acquire stolen usernames and passwords in any way, usually on the darknet, and then use botnets or other automation tools to gain unauthorized access to user accounts with the stolen login credentials. In short, filling in credentials is an automatic injection of credentials to gain unauthorized control over a user’s account, such as credentials. Attacks on access authorization can use a botnet that uses automated scripts to try to access accounts with legitimate credentials that allow the hijacking of at least one account.
Real-life scenario: Hacking Trump campaign website
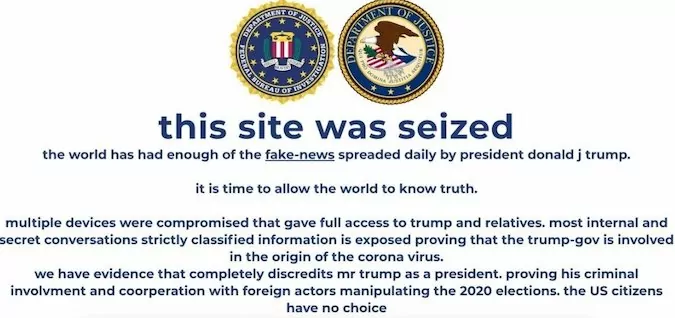
On the 27th of October 2020, hackers succeeded in breaking in and modifying the website content of donaldjtrump.com. The message “This site was seized” was seen on the website for a brief amount of time.
Trump spokeswoman for campaign Tim Murtaugh announced the incident. He also showed that law enforcement officials have been called in to carry out inquiries. He also said that there was no compromise in classified material.
Even though the content of the website has been rapidly restored, the “Privacy Policy” and the “Terms and Conditions” pages still have returned a “404 page not found” error for some period of time.
Security researchers suspect that hackers have breached the content management system (CMS) behind Donald Trump’s campaign website using the credential stuffing method.
The platform uses Cloudflare as a content delivery network (CDN), and it could be used as an access point only if the attackers knew the IP of the server. Another probability could be to use compromised account passwords where the Donaldjtrump.com domains were logged. Access to them via FTP or SSH or access through Expression Engine with zero-day defect, which has little documented bugs and would include not only FTP or SSH credentials but also knowledge of the IP address of the site’s root.
How to detect and prevent credential stuffing attacks?
To detect an attack on the credentials, organizations must be aware of the number of failed login attempts and the duration of each login attempt. Attacks with credentials create a list of credentials up to a list of valid accounts that prepare them for further attacks.
Credit card completion is particularly dangerous when consumers use the same usernames and password combinations for multiple accounts, giving a cyber thief access to all of these accounts in one go. Password reuse is a key factor in attacks on access data and this practice should be strongly discouraged at work or at home. The best way to protect your account details from fraudsters is to stop using the same passwords for multiple accounts.

An important factor in creating credentials is the fact that users reuse passwords for more than one application. The success of a credential stuffing attack depends on whether the user has poor password hygiene.
Since a key function of the login data is to detect successful logins from multiple websites, make sure that usernames are generated that are unique to each website, and avoid using email addresses as a user ID. A significant number of websites use an email address as their username, so make it clear that most users will have difficulty using a single email address for all their accounts. Since many of the available login lists contain only email addresses, it is difficult for an attacker to obtain a valid username-password pair – by filling in credentials.
Get proactive to prevent credential stuffing
Compromised credentials found in combo lists are often used in credential stuffing campaigns, phishing, and account takeover attacks to support other crimes such as banking fraud. Millions of users of Netflix, Spotify, Zoom, and many major e-commerce platforms are frequently targeted which leads the way for your adversaries.
To reduce the negative effect of combo lists on your online business and brand reputation, SOCRadar’s Fraud Protection module allows you to monitor newly-detected fresh combo lists, username password combinations of millions of users, found on the dark web. By processing and analyzing these massive datasets, it provides you statistics on heavily used credentials that can be used to enhance your fraud prevention and password policies.
SOCRadar provides;
- Daily updates: Get fresh combo lists daily aggregated from dark web forums.
- Authenticity rate: Know in-depth details like the source and authenticity rate.
- Geolocation-awareness: Classifiable based on the geographical region your customers exist.
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.

































