2020: The Year in Cybersecurity
One of the trends in cybersecurity that should be noted is the continuing need to further improve the relevant cybersecurity rules. As technology companies operate with big data, it is up to cybersecurity experts to defy cybersecurity trends to prevent these attacks. Here we want to include the statistics that give us an idea of how the number of cyber attacks will increase in 2020. Cybersecurity threats are everywhere, as cybersecurity statistics show, and the only thing that can help organizations and individuals deal with them is to educate Internet users about the threats. If we look at the possible trends in cybersecurity in 2020, it becomes clear that 2021 will be an interesting year for all things cybersecurity.
- Ransomware attacks
- Data breaches
- Third-party attacks
- Vulnerabilities
- DDoS attacks
Ransomware attacks
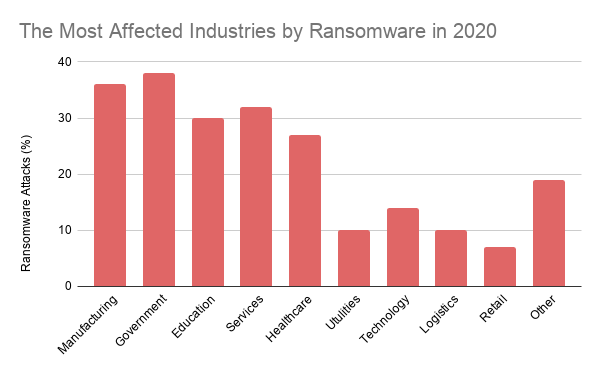
Most affected industries by ransomware in 2020
According to statistics for 2020, about 38% of ransomware attacks target governments as the most targeted sector. The second most targeted sector stands out as the manufacturing industry with 36 percent.[1]
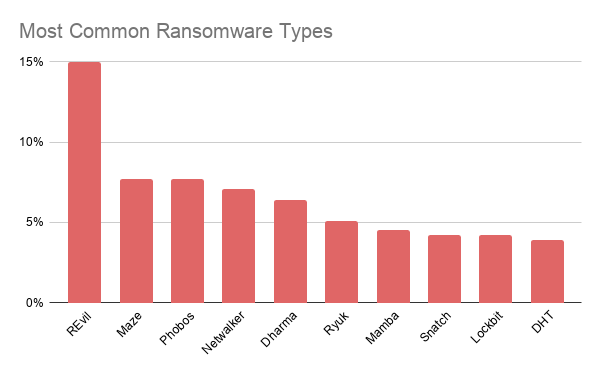
Types of ransomware attacks
More than one form of ransomware is available, and it is difficult to follow up on them all with new ransomware attacks still emerging. Recently, Coveware published a report about the most common ransomware types. According to this report the most common ransomwares are REvil (Sodinokibi), Maze, Phobos, Netwalker, and Dharma. While REvil is responsible for 15 percent of all ransomware attacks, Maze and Phobos each caused 7.7 percent of attacks.[2]
Data breaches
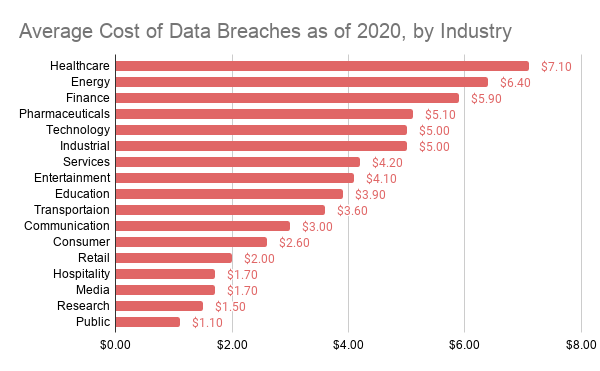
Most affected industries by data breaches in 2020
Healthcare organizations have had the highest costs associated with a data breach. Healthcare, Pharma, and Biotech had 352,771 exposed sensitive files on average which is the highest when comparing industries. 15% of breaches involved Healthcare organizations, 10% in the Financial industry.
Third-party attacks
Third-parties are companies that support your organization and often have access to, share, or maintain data critical to your operations. Third-parties include a broad range of companies such as data management companies, law firms, email providers, web hosting companies, subsidiaries, vendors, service providers, subcontractors. Essentially any company whose employees or systems have access to your systems or your data is considered a third party. However, third-party cyber risk is not limited to these entities. Any external software, hardware, or firmware that you use for your business can also pose a cyber risk.
Top third-party attacks in 2020
SolarWinds
At the end of 2020, malicious SolarWinds software has also infected more than a dozen critical infrastructure companies in the electric, oil, and manufacturing industries that were also running the software.
Original Equipment Manufacturers (OEMs) have remote access to critical parts of customer networks, as well as privileges that let them make changes to those networks, install new software, or even control critical operations. This means that hackers who breached the OEMs could potentially use their credentials to control critical customer processes. Here are reported victims of the SolarWinds hack so far;
- US Department of Defense
- US Department of Energy
- US Department of Commerce
- US Department of Health and Human Services
- US Department of Homeland Security
- US Department of State
- US Department of Treasury
- Belkin International
- California Department of State Hospitals
- Cisco
- Cox Communications
- Deloitte
- Digital Sense
- FireEye
- Intel
- ITPS
- Kent State University
- Microsoft
- Netdecisions
- Nvidia
- Pima County, State of Arizona
- SolarWinds
- Stratus Networks
- VMware
Vulnerabilities
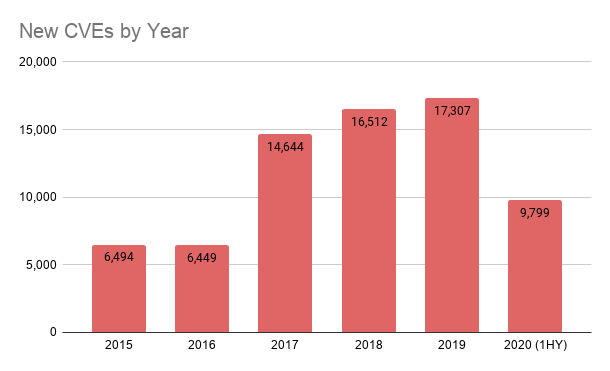
In the first half of 2020, new vulnerability reports increased significantly (9,799 in 2020, up from 7,318 in 2019, a rise of 34%). This number further beats the previous high for the first six months of 2018 (8,485) and suggests a record-breaking figure for 2020.[2]
- 20,000+ New Vulnerability Reports Likely in 2020
- 50% Increase in Mobile Vulnerabilities Highlights Dangers of Blurring Line Between
- Corporate and Personal Networks
- Ransomware and Trojans Thrive During COVID–19 Crisis
- Attacks on Critical Infrastructure Adding to the Chaos
DDoS attacks
DDoS attacks increase dramatically in 2020. Even though DDoS Intelligence statistics are limited to botnets detected, it can give us an idea of how these kinds of attacks are still effective.[3]
- 4.83 million DDoS attacks took place in the first half of 2020.
- 77% growth in attack size in 1HY 2020 from 2019.
- 92% of attacks were less than an hour.
- DDoS botnet flooding was most active on Thursdays, with a noticeable dip on Fridays.
- Linux botnets still dominate over their Windows counterparts, accounting for 95.39% of attacks.
Most affected countries by DDoS attacks in 2020
The top 3 by number of attacks and targets remain unchanged: China (71.20 and 72.83%), the US (15.30 and 15.75%), and the Hong Kong Special Administrative Region (4.47 and 4.27%).