
What is Tactical Cyber Threat Intelligence and How to Use it
As cyber threats become more complex than ever, many organizations devote more resources to their security programs. Almost every organization creates security teams to deploy network solutions and address threats. A vital component of the success of these initiatives is their access to up-to-date cyber threat intelligence. This blog attempts to explain the importance of tactical cyber threat intelligence for organizations.
What is Cyber Threat Intelligence (CTI)
Firstly, it is necessary to know what Cyber Threat Intelligence (CTI) is. CTI is all information that helps mitigate harmful events from now or in the future by threat actors. It is also within the definition of CTI to collect, analyze, and classify this information, communicate their security vulnerabilities to organizations, and list what can be done to mitigate risks. To better understand the subject, you need to know about different types of threats.
What are the different types of CTI?
Threat intelligence falls into four categories: Strategic, Tactical, Operational, and Technical. The data collection, analysis, and intelligence consumption for these four types are different. SOCRadar generates different levels of intelligence with the information it collects and ensures the best use of the data.
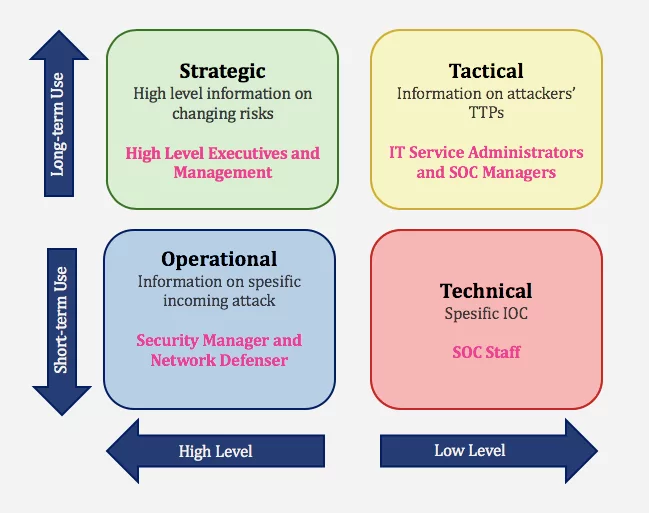
- Strategic Cyber Intelligence: It is high-level information about changing risks. Senior decision-makers use high-level information on risk-based intelligence in management. White papers, policy documents, and publications are some examples of this cyber threat intelligence strategic operational and tactical cyber threat intelligence category.
- Operational Cyber Intelligence: Actionable information about incoming identified attacks.
- Tactical Cyber Intelligence: Details of threat actor tactics, techniques, and procedures (TTPs).
- Technical Cyber Intelligence: Technical threat indicators. Such as specific Indicators of Compromise (IOC) for SOC Staff.
Definition of Tactical Cyber Threat Intelligence
Tactical CTI is meant as information about “Tactics, Techniques, and Procedures (TTPs)” ttps within cyber threat intelligence and Indicators of Compromise (IOCs) tactical cyber threat intelligence is used to threat actors. It also examines what’s happening on an organization’s network, focusing on the strengths and weaknesses of an organization’s network defenses. Therefore, tactical CTI directly feeds your organization to protect your brand and systems.
Tactical CTI seeks to identify how a Threat Actor plans to attack an organization and match that with detection and mitigation strategies. Examples of Tactical CTI are malware signatures, IP and URL blacklists, traffic patterns, log files, and credentials found in APT, ransomware, and phishing campaigns.
Who Uses Tactical CTI, Why, and How?
It is primarily aimed at a technical audience, helping them understand how their networks are being attacked based on the latest methods attackers use to achieve their goals. It provides information that can be used by security professionals such as IT, SOC, and NOC managers.
Personnel use tactical cyber intelligence data to understand attackers’ technical capabilities and objectives and determine their detection and remediation strategies. Tactical CTI is low-level information for long-term usage to technical managers.
Tactical CTI provides to answer questions such as:
- What is the cyber attacker’s TTP?
- What are the goals of the cyber attacker?
- What mitigation strategies are provided for incoming attacks?
The source of Tactical CTI is OSINT;
- Malware Samples and Analysis
- Attack Group Report
- Malware and Incident Reports
- Campaign Reports
- Human Intelligence in Deep & Dark Web
How Does Tactical CTI Benefit Organizations?
- Provides context to Big Data
Methodical approaches that help manage incoming disparate data sets and transform them into meaningful and actionable information that meets the information needs of the business.
- Build and improve a proactive cybersecurity structure and minimize its risks
By identifying overall vulnerabilities and attacker behavior patterns, tactical cyber intelligence can provide insight into an attack model and reveal the highest risk areas. It can also identify technical, business, or mission vulnerabilities and define and mitigate an organization’s enterprise risk.
- Incident response support
Responders need tactical threat intelligence to ensure that their investigations and defenses are strong enough to withstand current adversary tactics. A proper understanding of the TTP in use at any given time significantly improves the ability of incident responders to detect, prioritize, and resolve serious security incidents.
- Impetus for a cybersecurity posture that is forward-looking, not merely reactive
A mature, comprehensive, and flexible cybersecurity framework lets the organization collect and analyze more data sets while complementing the tactical cyber intelligence process. The more extensive the data analyzed, the more comprehensive the insights and the better equipped an organization’s cyber defenses are against all attackers.
Tactical CTI Use Case: Triage
CTI can help quickly determine whether or not there is cause for concern. In a triage case, tactical users first check their local CTI store or call the APIs of their CTI sources. If there is an IOC match, they proceed with their incident handling process. If there is no match, they move on to the following message. Using CTI on a “check first, trust later” basis can significantly reduce the number of time analysts spend at the tactical level trying to distinguish between trusted and malicious information.
What SOCRadar Provides
- Phishing domain lists
- Keeps track of cybersecurity incidents and informs organizations about attackers’ TT
- Malicious domain lists, IPs, hashes, etc.
- Integrate its feeds with the existing security system to support incident triage
- Provide malware analysis
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































