
The Week in Dark Web – 18 October 2021 – Ransomware Attacks and Data Leaks
Powered by DarkMirror™
This week’s edition covers the latest dark web news from the past week. Again, rise of ransomware attacks, some database thefts, and stealing customer data, that took their place on the headlines this week. Click here to read the last weeks post.
Find out if your data has been exposed on the deep web.
The New Ransomware Victim Hit By The Conti Ransomware Gang
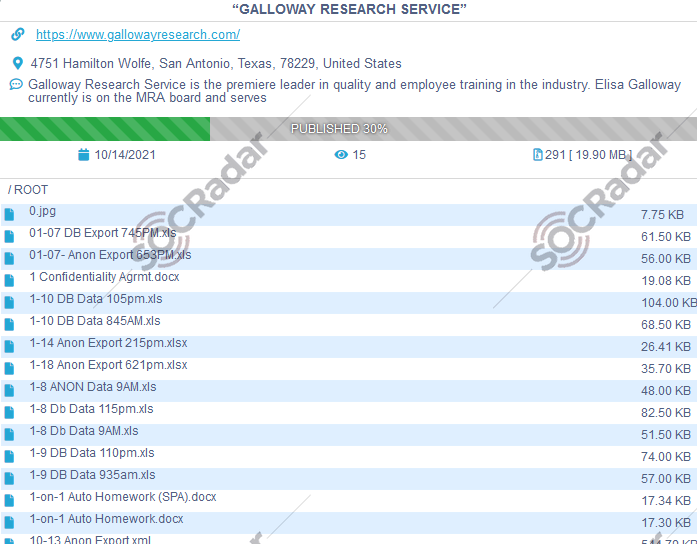
On October 14, SOCRadar found a post allegedly announcing a ransomware attack targeting a research firm from the US on the Conti groups’ website. Established in 1967, the victim organization serves as research incorporated.
The group behind the attack known as Conti is also responsible for last month’s ransomware attack on JVC Kenwood, a Japanese multinational electronics giant. If the victim organization would not cooperate with the ransomware group, the ransom gang threatened to leak banking data, licenses, certificates, agreements, contracts, and similar sensitive information belonging to the victim organization.
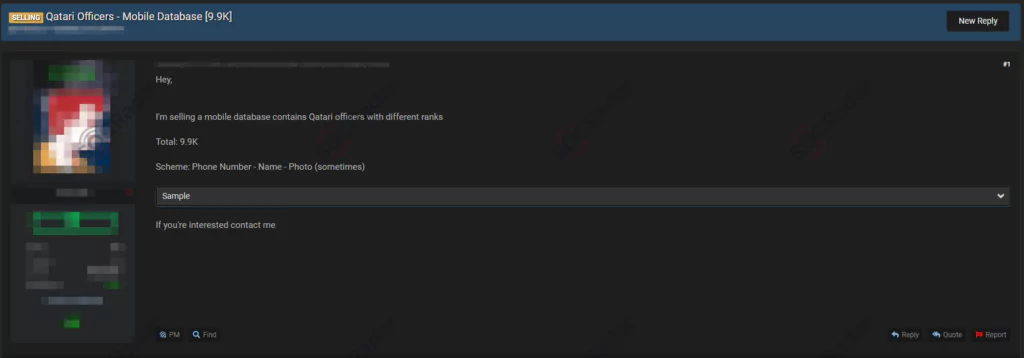
Customer Database of A Crypto Company Leaked On The Dark Web
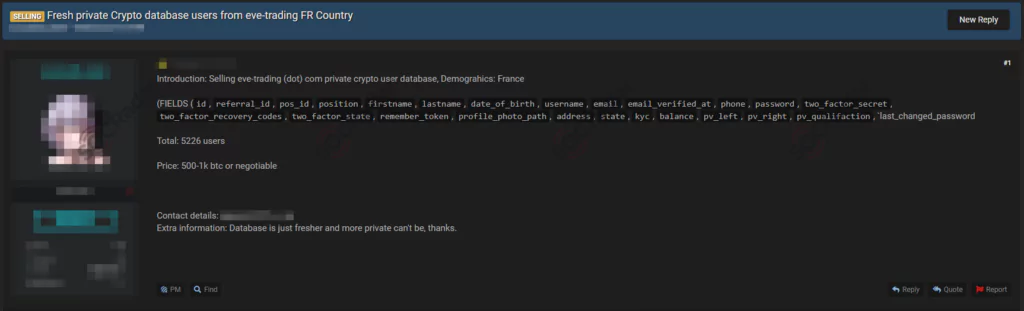
On October 12, a vendor claimed to have a customer database allegedly belonging to a crypto company from France on a dark web forum monitored by SOCRadar. According to the dark web post, while it is unclear how dark web actors obtained the database, the surfaced details comprise full names, emails, and phone numbers of over 5 thousand users. Also, there are transaction recordings and passwords available.
Unauthorized Access Sale Detected For A Company From Singapore On The Dark Web
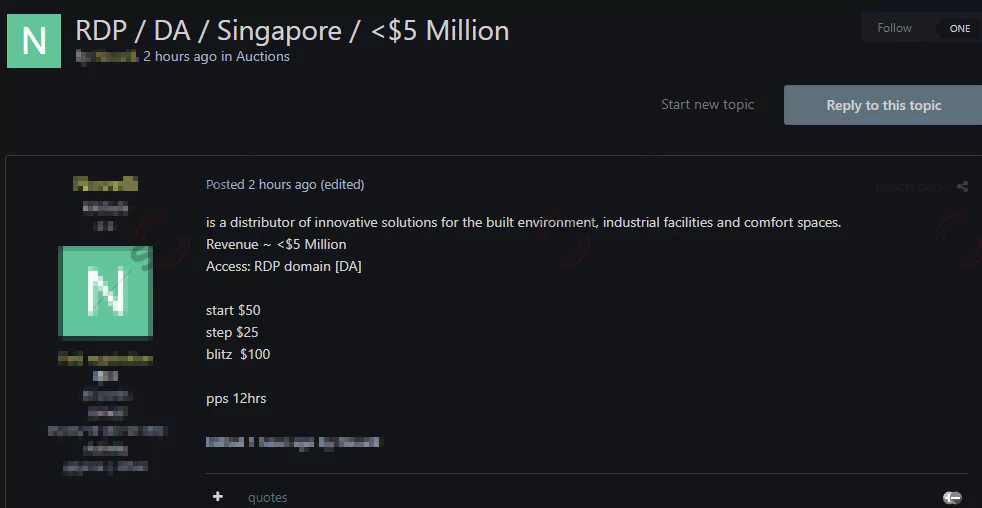
On October 13, on a dark web forum monitored by SOCRadar, a vendor attempted to sell unauthorized access allegedly for a company from Singapore. While the dark web vendor did not give the firm’s name, it is stated that the victim company is engaged in industrial facilities and has a revenue of $5 million. The vendor also noted that the buyer would have RDP access to the devices on the system.
The New Ransomware Victim of LockBit 2.0

On October 13, SOCRadar detected a post allegedly announcing a ransomware attack that targeted a residential construction firm from Italy on the LockBit 2.0 groups’ website. Established in Stockholm, the victim corporation is engaged in brokerage and finance with over $6 million in revenue.
The group behind the attack known as LockBit 2.0 is also responsible for the ransomware attack on Accenture, and the victim firm tied up in $50 million. If the victim organization would not cooperate with the ransomware group, the ransom gang threatened to leak banking data, licenses, certificates, agreements, contracts, and similar sensitive information belonging to the victim organization.
User Database of a Digital Game Distribution Giant Leaked On The Dark Web
On October 9, a vendor claimed to have a user database allegedly belonging to a digital distribution platform operating globally on a dark web forum monitored by SOCRadar. The victim platform is engaged in purchasing and playing games. According to the dark web post, the shared database contains 2.3 GB of data, including full names, emails, phone numbers, and passwords.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, it is simply not feasible to monitor all sources which can be time-consuming as well as challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.

































