
The Week in Dark Web – 10 January 2022 – Access Sales and Data Leaks
Powered by DarkMirror™
This week’s edition covers the latest dark web news from the past week. Again, rise of ransomware attacks, some database thefts, and stealing customer data, that took their place on the headlines this week. Click here to read the last weeks post.
Find out if your data has been exposed on the deep web.
The New Ransomware Victim of Lapsus$
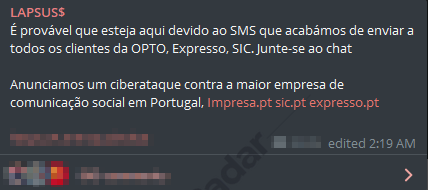
On January 4, a ransomware post allegedly announcing an attack that targeted the media giant of Portugal was detected in the Lapsus$ ransomware group telegram channel monitored by SOCRadar. Established in Lisbon, the victim group has a TV channel, a newspaper and various magazines with a revenue of $196 million. The ransomware group could leak all their data if the victim organisation refuses to negotiate. Lapsus$ Group made its debut on the ransomware scene in 2021. It became famous with the Brazil Ministry of Health attack last month.
Unauthorized Webmail Access Sale Detected For An Insurance Firm from Colombia On The Dark Web
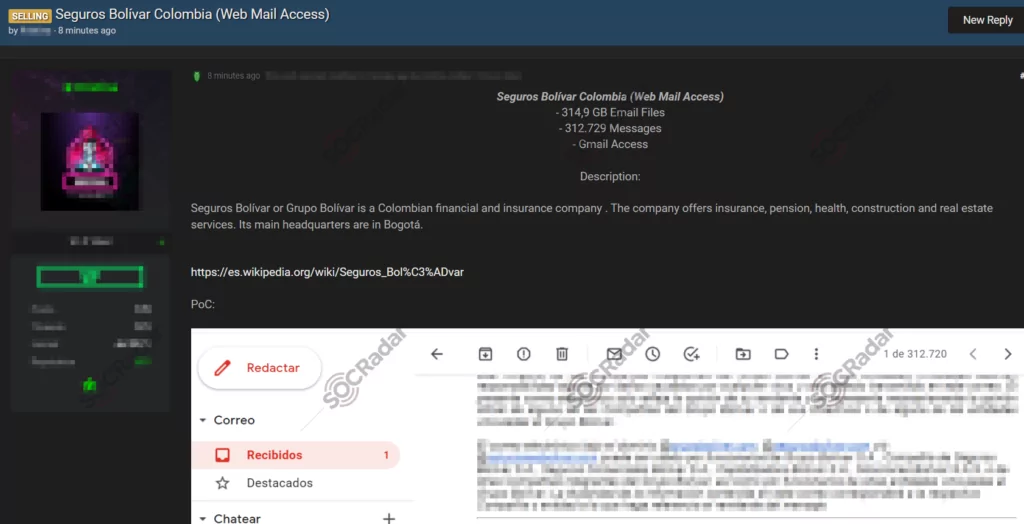
On January 3, a dark web vendor attempted to sell unauthorized webmail access for an insurance and financial firm on a dark web forum monitored by SOCRadar. According to the dark web post, the buyer would have access to 315 GB of email files and over 300 thousand messages as well as Gmail access. Headquartered in Bogotá, the victim company is engaged in insurance, construction, health and real estate services. The vendor also shared a screenshot as PoC.
Database of Canada-Saskatoon City Airport Publised On The Dark Web
On January 5, SOCRadar detected a post allegedly publishing a stolen database of Skyxe Saskatoon Airport. The vendor shared samples demonstrating the content of the database. According to the underground market post and samples, there are documents including airport plans, financial sheets, and sensitive contracts in the shared database. The vendor also stated that the database was obtained on December 3, 2021, and is up to date.
Unauthorized Camera Access For A Lot Of Countries Put On Sale
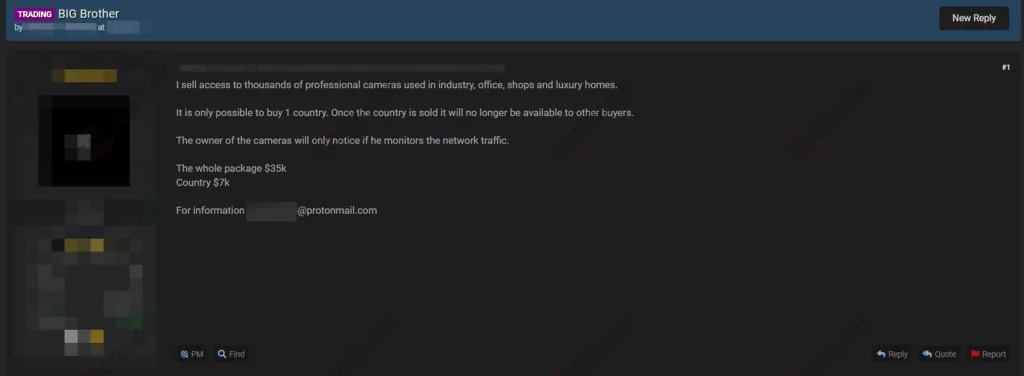
On January 4, on a dark web forum tracked by SOCRadar, a vendor offered to sell unauthorised camera accesses allegedly for countries. While the dark web vendor did not detail how this access has been seized, claimed to sell access to thousands of professional cameras used in different places varying from offices to shops and luxury homes. Moreover, the vendor stated that it is possible to buy access for only one country. Once the access for a country is sold, it will no longer being sold to different buyers. The vendor also said owners of the cameras will only notice the intrusion if they monitor the network traffic and set prices $7 thousand for a country or $35 thousand for all countries.
Database of Kenya Vaccination System Are Being Traded On The Dark Web
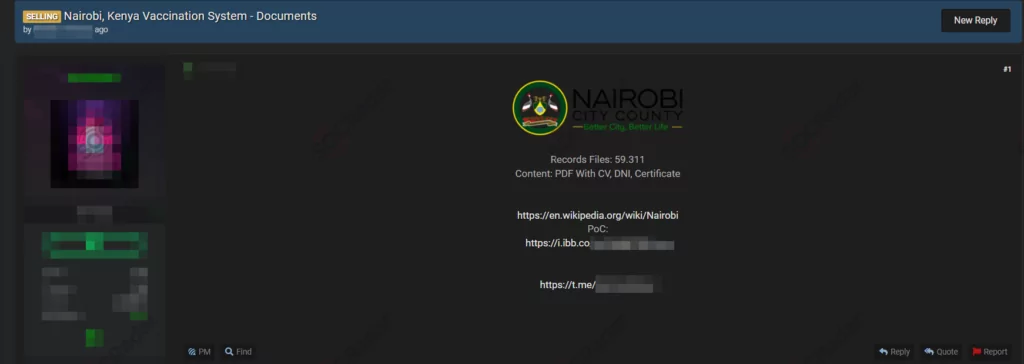
On January 6, a vendor claimed to have databases allegedly belonging to the vaccination system of Kenya on a dark web forum monitored by SOCRadar. The dark web vendor stated that the breached database contains more than 50 thousand documents comprising PDFs, certificates and ID cards. According to the SOCRadar Analyst Team, information obtained from these documents could be used in sophisticated social engineering attacks.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, it is simply not feasible to monitor all sources which can be time-consuming as well as challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.

































