
What Do You Need to Know About Spring4Shell Zero-Day Vulnerability?
A zero-day vulnerability that affects the Spring Core Java framework called Spring4Shell and allows RCE has been disclosed. Vulnerability coded as CVE-2022-22965 and rated as critical. Spring is a very popular framework for Java developers. This increases the potential for threats to vulnerable applications.
CISA Adds Spring4Shell to Its Catalogue
On Monday, the US Cybersecurity and Infrastructure Security Agency (CISA) added the Spring4Shell RCE vulnerability to its Known Exploited Vulnerabilities Catalogue. You can access the catalog here.
While details about the exploit are unclear, active scans show that the suspects are using Russian and Chinese IPs.
1. What is Spring4Shell, When was Spring4Shell Released, What is it Used For, and Why is it so Important?
A zero-day remote code execution vulnerability in the Spring Core Framework is named as Spring4Shell, or SpringShell by cybersecurity researchers.
The vulnerability, which is being considered the next Log4Shell by some researchers, has the potential to affect various software.
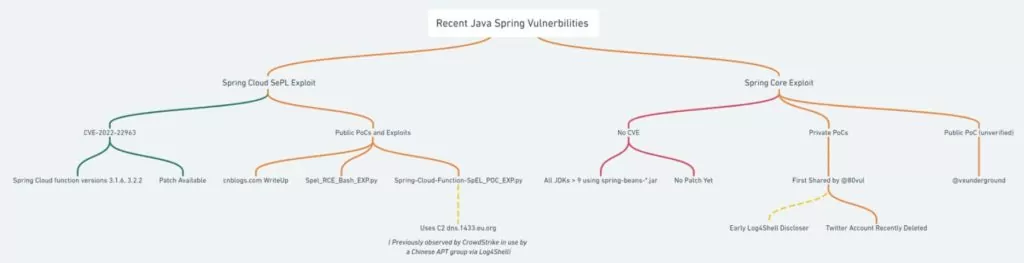
The 0-day vulnerability was exposed with the POC on a Chinese Twitter account on March 29, 2022. Although the tweets were deleted, cybersecurity experts determined that the vulnerability was open to exploitation. For the time being, there is no patch for Spring4Shell which has not been assigned any CVE ID at the moment, is still being worked on.
It is stated that the vulnerability discovered by cyber security researchers yesterday is different from the Spring Cloud RCE vulnerability with the code CVE-2022-22963, which was also announced.
2. How Critical is Spring4Shell Vulnerability?
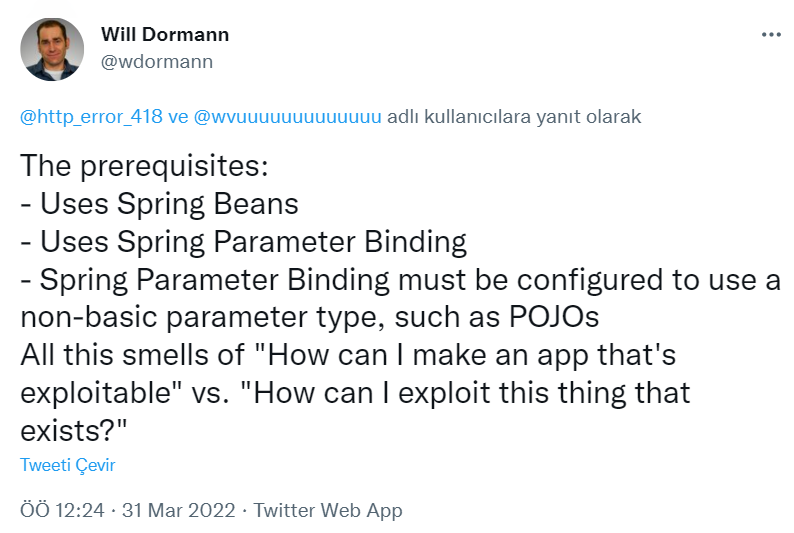
To exploit Spring4Shell, attackers need to make specially developed requests to the vulnerable server. It is worth noting that certain prerequisites are required to benefit from Sprin4Shell. That is, the code needs to be exploitable.
3. Which Products and Systems that You Use May be Affected by this Vulnerability?
For CVE-2022-22963, those running earlier than the following Spring Cloud versions may be at risk:
- 3.1.7
- 3.2.3
For the Spring4Shell vulnerability, those who use the following may be at risk:
- Java Development Kit 9 and higher
- Spring-Beans package
- Spring parameter binding
- Spring parameter binding using non-basic parameter types like POJOs
As of the day it appeared, threat actors have started targeting organizations with their attempts to exploit the Spring4Shell vulnerability. Reports show that one of the six organizations affected by the vulnerability was targeted.
According to data published by Check Point on its blog, around 37,000 exploits were detected in the past weekend alone. The firm points to software vendors as the most affected sector.
Microsoft 365 Defender Threat Intelligence Team stated that it detected exploit attempts in cloud services and underlined that it is on the alert for potential threats by regularly monitoring the cloud infrastructure.
CERT/CC also added a list of companies affected by the vulnerability to its note with VU#970766. VMware, mentioned in the list, released patches for some of its products yesterday.
| Blueriq |
| Cisco |
| JAMF Software |
| NetApp |
| PTC |
| Red Hat |
| Spring |
| VMware |
Resource: CERT/CC
4. Is There Any Patch or Mitigations About These Vulnerabilities?
For the CVE-2022-22963 vulnerability, it is necessary to upgrade Spring Cloud Function to 3.1.7 (and higher) or 3.2.3 (and higher).
Spring announced in today’s advisory that it had made fixes for the following versions:
- Spring Framework 5.3.18 and Spring Framework 5.2.20
- Spring Boot 2.5.12
- Spring Boot 2.6.6
Since reports are circulating the vulnerability is actively exploited in the wild, updates are highly recommended as soon as possible.
5. How to Exploit Spring4Shell Vulnerability? Is There Any Example of Exploit Code?
Theader for a typical exploit is:
- spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec(“{cmd}”)’
Various PoC exploits for both Spring4Shell and CVE-2022-22963 are available in GitHub repositories.
Resources:
https://www.cyberkendra.com/2022/03/springshell-rce-0-day-vulnerability.html?m=1
https://www.lunasec.io/docs/blog/spring-rce-vulnerabilities/
https://www.cyberkendra.com/2022/03/spring4shell-details-and-exploit-code.html
https://tanzu.vmware.com/security/cve-2022-22947
https://www.riskbasedsecurity.com/2022/03/30/springshell-vulnerability/
https://github.com/dinosn/CVE-2022-22963
https://www.rapid7.com/blog/post/2022/03/30/spring4shell-zero-day-vulnerability-in-spring-framework/
https://isc.sans.edu/diary/28500
https://www.tenable.com/blog/spring4shell-faq-spring-framework-remote-code-execution-vulnerability
https://blog.sonatype.com/new-0-day-spring-framework-vulnerability-confirmed
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.

































