
What is the Role of Single Sign-On in Security Measures? – Part 1
By SOCRadar Research
Identity and Access Management (IAM) can be challenging in an enterprise environment. For users and administrators, there can be dozens of credentials to manage, leading to frustration and vital problems for the organization. Users can use the same password for all the services. In return, this can lead to a position where a compromised credential obtained through a vulnerable application means access to all the resources available to that credential. According to a Verizon report, 61% of all breaches involve credentials, which can be obtained through social engineering or brute force techniques.
How can these concerns be addressed? A07:2021 – Identification and Authentication Failures topic is listed in OWASP Top 10. It is stated that to have protection against authentication-related threats, the confirmation of the user’s identity, authentication, and session management is critical. Single Sign-On might be the answer to these types of challenges. With Single Sign-On, authentication and authorization processes can be managed from a center, improving security capabilities, and reducing the organization’s attack surface.
IAM is the broader concept of enabling authenticated individuals to access authorized resources for the right reasons. It is the management of people, processes, and procedures used to create, manage, and destroy identities of all kinds. SSO is just one of the components of a more comprehensive IAM.
What is Single Sign-On, and How Does it Work?
The groundwork for Single Sign-On is the federated identity concept. It is the sharing of identity attributes across trusted autonomous systems. When a user provides SSO credentials and establishes a connection with the SSO server, they are granted access to other services in the environment. The connection can be formed by generating a token for the services to trust the user or simply passing on the credentials to services in the background without needing the user to reenter them.
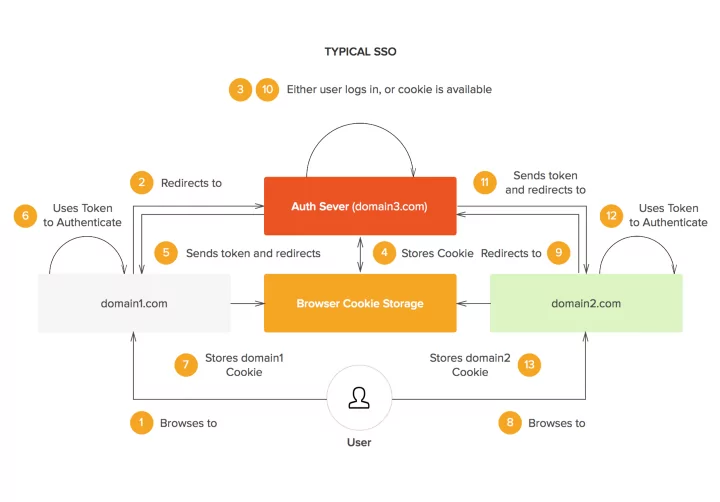
Types of Single Sign-On
FIM-based SSO
Federated Identity Management (Identity Federation) allows users from different domains to access all their applications and networks using the same credentials. It is based on mutual trust between identity brokers and organizations. FIM builds trust through standards such as SAML, OAuth, or OpenID Connect. With FIM, users only need to authenticate themselves to their main domain when accessing a service or an application outside their domain.
Active Directory Federation Services (ADFS) is a Federated Identity Management system that provides Single Sign-on capabilities through SAML and OIDC. ADFS is primarily used to establish trust between ADDS and other systems such as Azure AD or other ADDS forests.
Claim-based SSO
Claim-based SSO is built upon a trusted Identity Provider (IdP) and a token that contains the claims/attributes of the user. Through IdP, a user requests to access an application maintained by a Service Provider (SP). The IdP provides the required token through Security Token Service (STS) and asserts to the SP that the user has proper access to the resources. The tokens generally use SAML.
Cookie-based SSO
Cookie-based SSO systems work by transporting user credentials from browser to server via Web-based HTTP Cookies without input from the user. Before the cookie transaction to the destination server, credentials stored in the user’s machine are encrypted. After extracting and decrypting the credentials, the server validates them against the authentication server.
NTLM-based SSO
New Technology LAN Manager (NTLM) is an authentication protocol used to authenticate a client to a resource on an Active Directory domain. It acts as an SSO tool through a challenge-response protocol to authenticate the user with a password hash, avoiding the need to send unprotected passwords over the network.
Kerberos-based SSO
Kerberos is a protocol that enables trusted host authentication over untrusted networks with mutual authentication. That is, both the user and the server verify the other’s identity. Kerberos is typically used in an enterprise LAN. It enables users to log into their Windows domain accounts and provides SSO to internal applications. It has three components Client, Network Resource (Application Server), and Key Distribution Center (KDC). When a Client authenticates to the server, Kerberos, through its ticket-granting service KDC, provides a ticket for the Client. With this ticket, the Client has access to the authorized resources.
Protocols of Single Sign-On
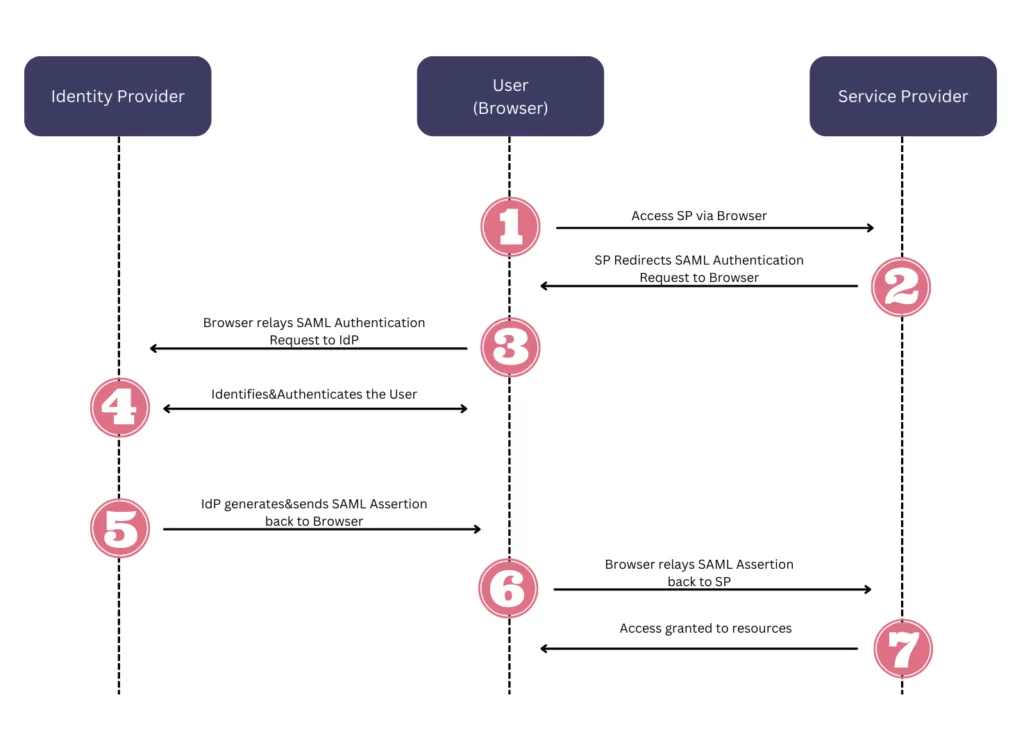
Security Assertion Markup Language (SAML)
SAML is an open standard that provides two important features: cross-domain single sign-on and identity federation. SAML became one of SSO’s core standards because it helps standardize authentication and authorization requests. An identity provider grants the authentication requests of clients. Below you can see the workflow of SAML.
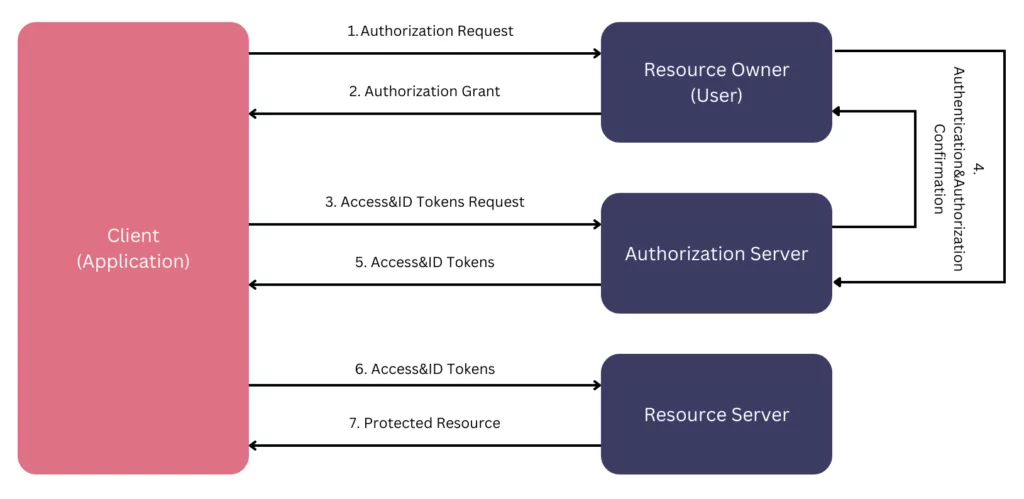
OAuth
OAuth is an open standard for developers to implement authorization across applications. OAuth only provides authorization to call third-party APIs. OAuth uses Access Tokens, which represent the authorization to access the resources on behalf of the end-user. Though there is no specific format for the Access Tokens, the JSON Web Token (JWT) format is the most common. These tokens have expiration dates for security concerns because of the potential of important data included in the token.
OpenID Connect (OIDC)
OIDC is built upon the OAuth standard. As mentioned before, OAuth provides authorization through Access Tokens containing scopes. OIDC adds another token, which is the ID token, on top of that to authenticate the user with a new set of scopes specific for identity. Like OAuth, the ID Token is utilized through Jason Web Token (JWT).
Below you can see the workflow of OAuth&OIDC.
Single Sign-On Cloud Solutions

Many enterprises are either moving or have already moved their infrastructure to the cloud. Enterprises accessing cloud-based applications or services are usually exposed to security vulnerabilities because many employees access the applications hosted on the cloud. Leveraging SSO with the same credentials, enterprises can enable users to sign into their desktop as well as cloud applications.
Key Features of an SSO Solution
- Easy-to-control Centralized Management
- Support for Third-party integrations
- Cloud-readiness
- Smooth End-user Experience
- Strict security policies
Top Solutions
- AWS Single Sign-On
- Azure Active Directory
- Okta
Benefits of Single Sign-On
Single Sign-On provides easy and secure access to resources necessary to carry out tasks in a work environment. Users and administrators overcome the hardship of remembering and managing dozens of credentials with one credential to remember and manage.
- Benefits for Users: With Single Sign-On, users can easily navigate through services and resources. With a single point of authentication, users are not required to authenticate each resource they need access to. This can help reduce password fatigue.
- Benefits for Administrators: Single Sign-On makes life easier for administrators regarding Identity and Access Management. It reduces the overload on administrators because they can focus on a smaller area to secure. Without SSO, there would be multiple credentials to manage for each user, but with SSO, the overhead can be shaved to the benefit of administrators.
- Benefits for App Developers: With SSO comes standardization for Identity and Access Management. Developers can follow the standards and easily implement them, otherwise costly processes, on their multi-tiered, cross-platform applications.
- Reduced Attack Surface: It is common for users to use the same credentials or weak passwords for different services. This can create weak points in the organization’s security. With SSO, the organization’s attack surface can be reduced because all the doors except one are closed to entry. If this point of entry is implemented with better security measures, such as MFA, the organization, in return, would have reduced attack surface.



































