
The Week in Dark Web – February 27, 2023 – Access Sales and Data Leaks
Powered by DarkMirror™
The most sophisticated attacks can be based on data put up for sale on the dark web by threat actors. A piece of simple information seemingly insignificant to an ordinary person can become a dangerous weapon for attackers. Since the actors in the cybercrime ecosystem know this very well, they regularly put the database up for sale on the dark web. Even if some of them are outdated, the clues they contain can be critical.
Last week, the most database sales were on our radar. Here are them and other notable posts.
Find out if your data has been exposed.
Unauthorized Database Access Sale is Detected for a Turkish Payment Gateway
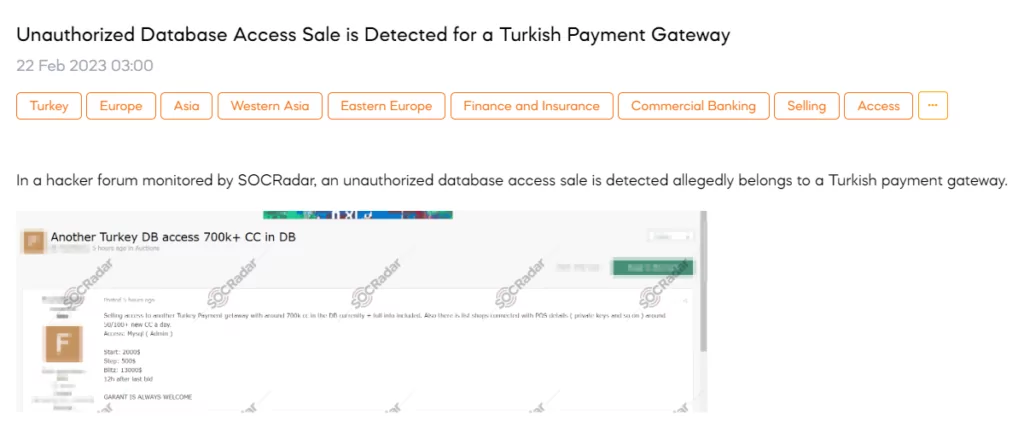
On February 22, a SOCRadar dark web researcher found a post that a threat actor declared their intention to sell unauthorized access to a MySQL database. According to the post, the database contains 700,000 credit card details of a Turkish payment company and includes a list of shops linked with Point of Sale (POS) details such as private keys. The threat actor has set the starting price at $2000.
Customer Database of the World Trade Center is Leaked
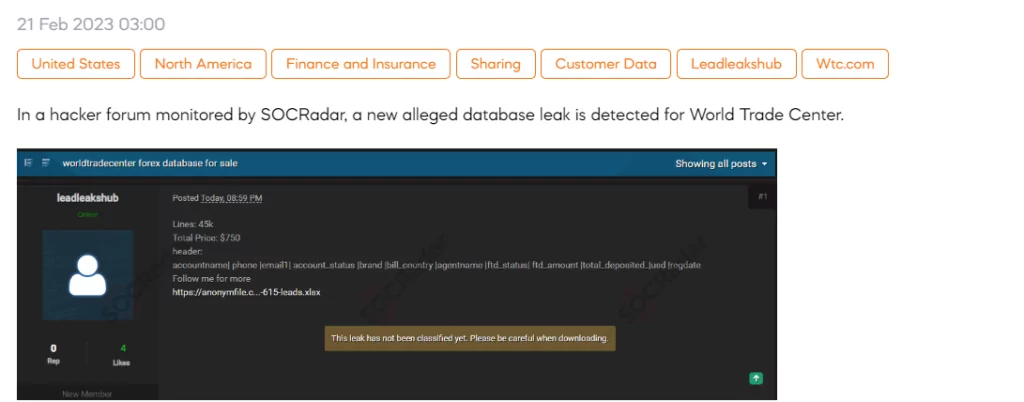
SOCRadar dark web team has detected a new post on a hacker forum that claims to be selling a forex database allegedly belonging to the World Trade Center. The database reportedly includes 45,000 lines of data, with sensitive customer information believed to be among the contents. According to the seller, the data contains details such as account name, phone number, email address, account status, and brand. The price for this information is $750.
Database of an American Real Estate Company is on Sale
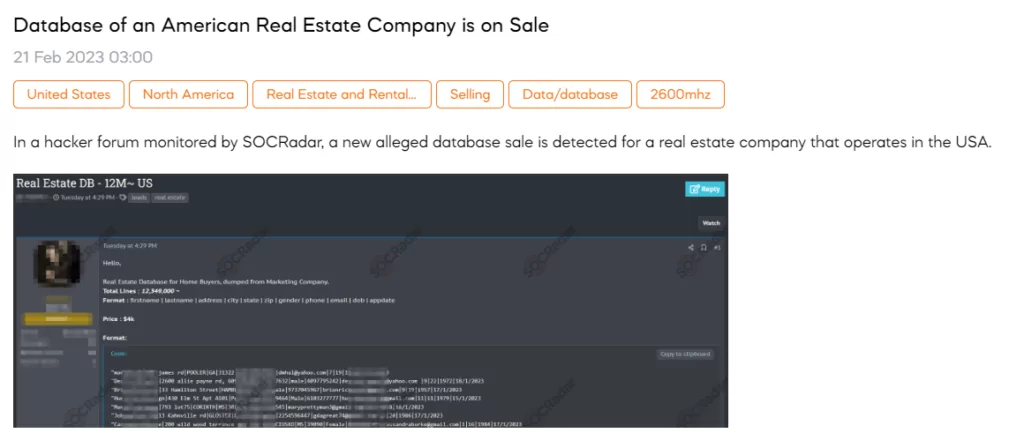
SOCRadar detected a post-selling database of an American Real Estate Company. The threat actor claims to have obtained a database of American real estate firm clients from a marketing company. The threat actor shared a sample of 12,349,000 lines of data containing sensitive data such as first name, last name, address, city, state, zip, gender, phone, email, dob, and app date. The threat actor shared his Telegram account and qTox ID to communicate with those interested in purchasing the database. qTox is a peer-to-peer instant-messaging and video-calling protocol that offers end-to-end encryption. The project’s stated goal is to provide secure yet easily accessible communication for everyone. The price for the database is $4000.
Unauthorized Access Sale is Detected for an African Logistics Company
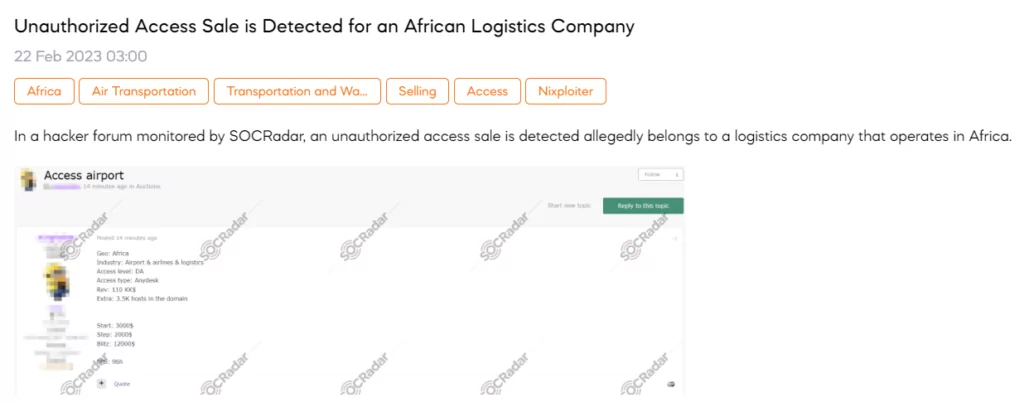
On February 22, a SOCRadar dark web researcher detected a post an unauthorized access sale is detected allegedly belonging to a logistics company that operates in Africa. The threat actor behind the post claims to have obtained Anydesk access to the company, which reportedly generates $110k in revenue. The access is being auctioned for $3000, $2000, and $12000.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































