
Dark Web Sales: Estée Lauder, Vivo Databases, and 2 Billion Lines of Stealer Logs
In the ever-evolving world of cyber threats, the SOCRadar Dark Web Team has unveiled a disconcerting series of illicit activities that threaten the digital realm. These incidents span across the globe and encompass well-known companies, in telecommunications, beauty, and finance industries. The latest incidents involve Estée Lauder, Vivo databases, and a staggering 2 billion lines of stealer logs.
The underground market for stolen data continues to thrive, with threat actors constantly finding new targets and opportunities for their malicious endeavors.
Here’s last week’s glimpse into the shadowy world of dark web.
Find out if your data has been exposed.
Databases of Clinique and Estée Lauder are on Sale
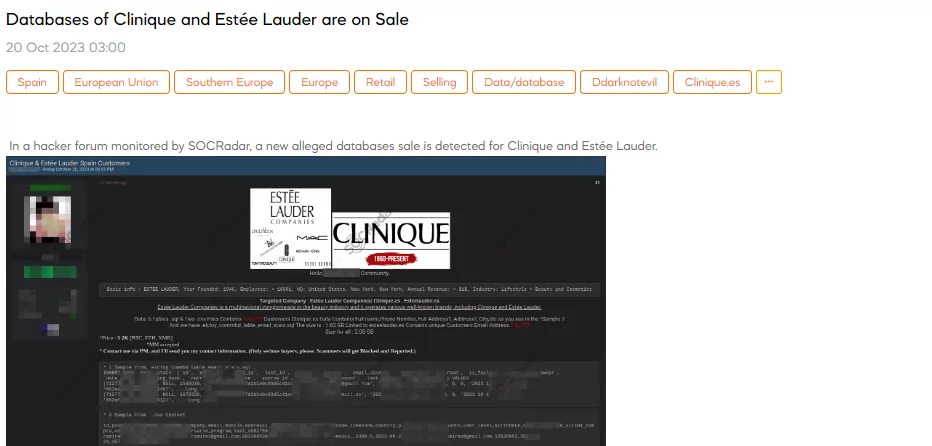
The SOCRadar Dark Web Team has identified a post in a hacker forum where a threat actor claims to be selling databases related to Clinique and Estée Lauder, both well-known brands under the Estée Lauder Companies conglomerate in the beauty industry.
According to the threat actor, The alleged data being offered for sale consists of 6 SQL tables and two CSV files containing information from 276,027 customers of clinique[.]es. This data includes full names, phone numbers, addresses, and more. A separate SQL file called “elcloy_commbd_table_email_stats.sql” is linked to esteelauder[.]es, containing unique customer e-mail addresses totaling 712,771 records. The combined size of all the data is 2.08 GB.
The combined size of these databases is approximately 2.08 GB. The threat actor is requesting a price of $2,000, with payment options including Bitcoin (BTC), Ethereum (ETH), and Monero (XMR).
Database of Vivo is Leaked
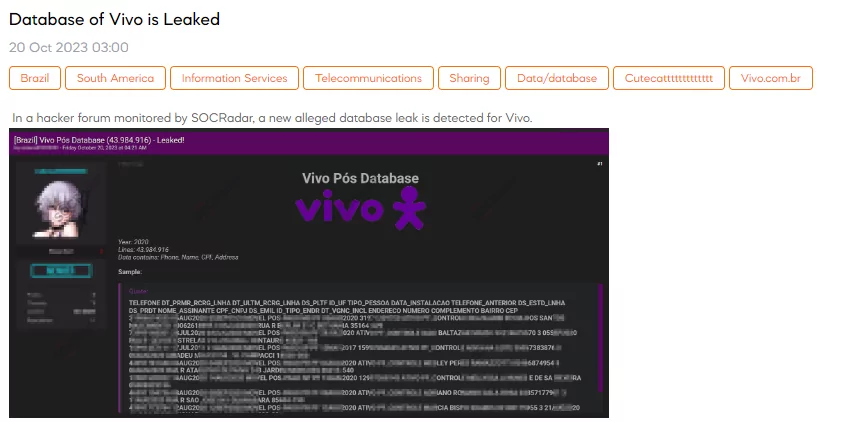
The SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor claims leaked a database related to Vivo, a telecommunications company in Brazil. The alleged database leak is said to have occurred in 2020 and contains a substantial amount of data, specifically 43,984,916 records. The threat actor claims the data includes sensitive information such as phone numbers, names, CPF (Cadastro de Pessoas Físicas, a Brazilian taxpayer identification number), and addresses.
Unauthorized Network Access Sale is Detected for a Mexican Finance Company
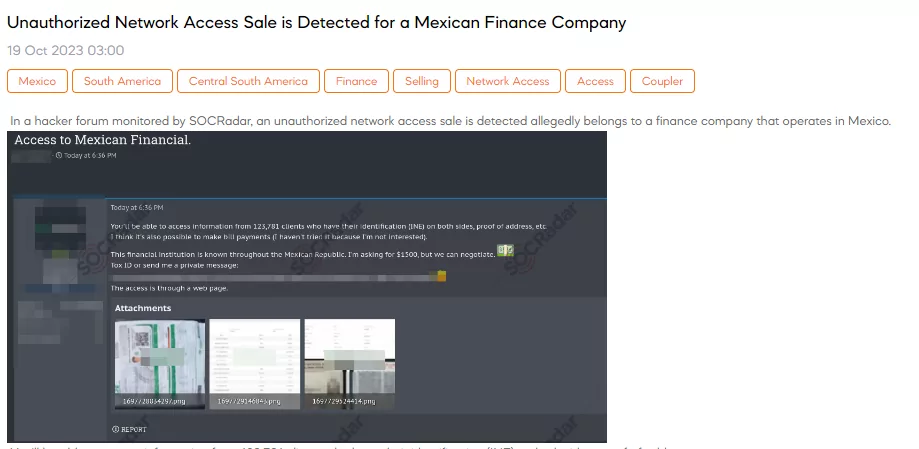
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claimed to be offering unauthorized network access to a finance company operating in Mexico. The threat actor asserts that the access would enable the retrieval of sensitive information from 123,781 clients, including their identification (INE) on both sides and proof of address. Additionally, there’s a suggestion that it might be possible to make unauthorized bill payments through this access. The threat actor requests $1,500 for this illegal access but is willing to negotiate.
1M Credit Cards are Leaked
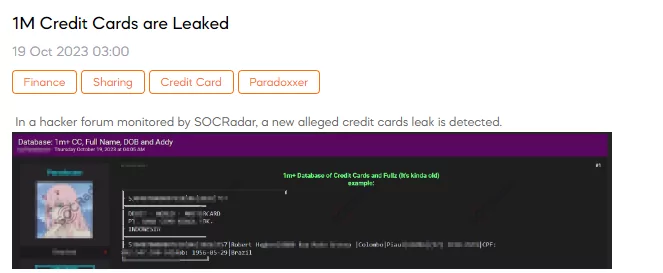
The SOCRadar Dark Web Team has identified a post where a threat actor claims to have a database of over 1 millioncredit card information. The data allegedly includes credit card numbers, expiration dates, CVV codes, cardholder names, addresses, phone numbers, and dates of birth.
2 Billion Lines of Stealer Logs are on Sale
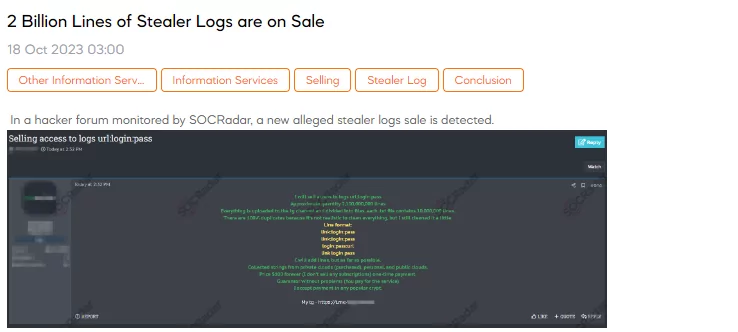
The SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor claims to be selling access to an enormous quantity of stolen data. The data consists of 2 billion lines of stealer logs, each containing URL, login, and password information. These logs have been uploaded to a Telegram channel and are divided into .TXT files, each containing 10 million lines.
The threat actor acknowledges that there are duplicates within the data, and while some cleaning has been attempted, it’s impossible to remove all duplicates completely. The line formats vary but include link combinations, login, and password information. The data appears to have been collected from various sources, including private clouds (which were likely purchased), personal accounts, and public clouds. The threat actor is offering this stolen data for a one-time payment of $100.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































