Atlassian Patches RCE Vulnerabilities in Bamboo & Crowd Data Center and Server: CVE-2023-22516, CVE-2023-22521
Atlassian has urgently issued security advisories for two separate products: Bamboo Data Center and Server, and Crowd Data Center and Server. The announcement states that they have addressed the CVE-2023-22516 vulnerability, which has a CVSS score of 8.5, affecting Bamboo Data Center and Server. Additionally, they have fixed the CVE-2023-22521 vulnerability with a CVSS score of 8.0, impacting Crowd Data Center and Server. Both vulnerabilities enable authenticated attackers to execute arbitrary code, significantly impacting confidentiality, integrity, and availability, and require no user interaction.
Which Versions of Atlassian Bamboo & Crowd Data Center and Server Are Affected, What Are the Fixed Versions?
A high-severity RCE (Remote Code Execution) vulnerability, CVE-2023-22516, in Bamboo Data Center and Server affects versions 8.1.0 to 9.3.0. Atlassian advises customers using these versions to update to the latest release or to the following fixed versions:
- Bamboo Data Center and Server 9.2: Upgrade to version 9.2.7 or later.
- Bamboo Data Center and Server 9.3: Upgrade to version 9.3.4 or later.
Vulnerability card in the SOCRadar Vulnerability Intelligence Module, where the related vulnerability (CVE-2023-22516) is examined in more detail within the timeline, is given below.
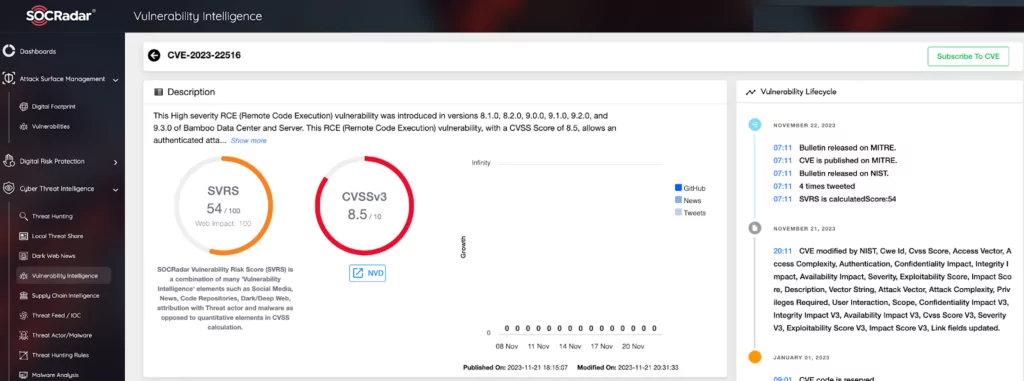
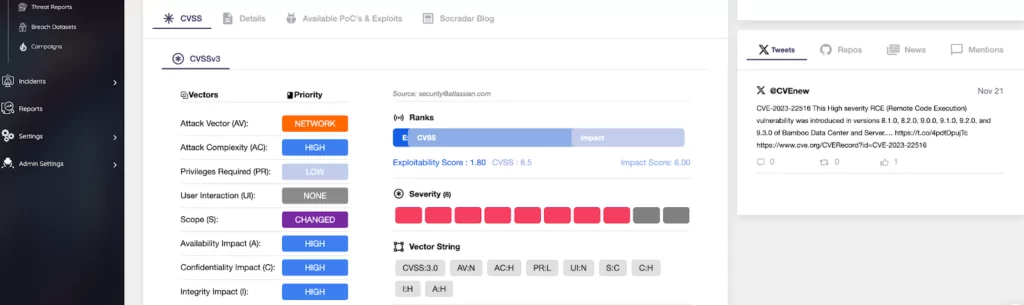
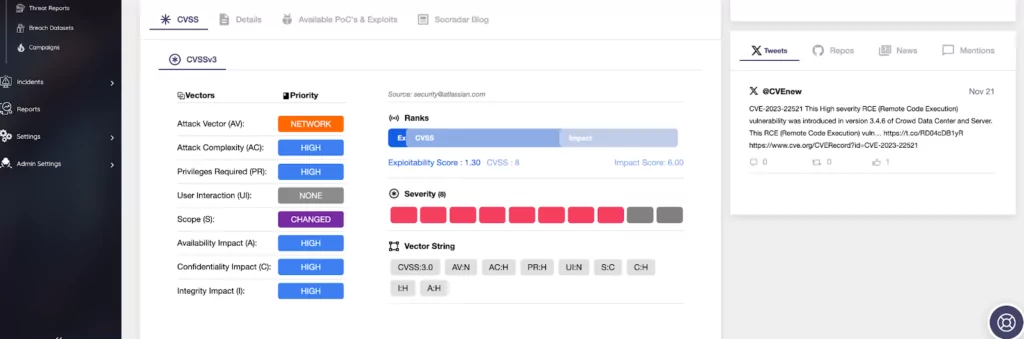
Furthermore, the vulnerability is detailed in the SOCRadar Vulnerability Intelligence Module, which includes a comprehensive analysis of attack vectors, impact factors, CVSS metrics, and exploitability. The module is updated with Proof-of-Concept or exploits as they become publicly available or are exploited in the wild by threat actors.
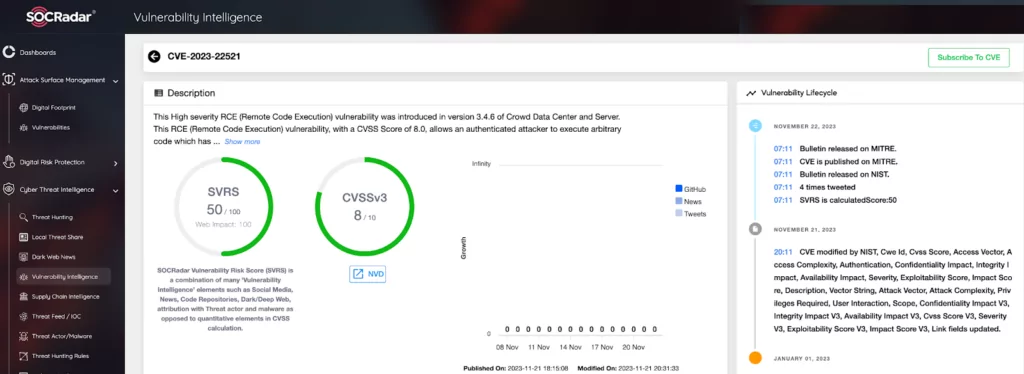
Another high-severity RCE vulnerability, CVE-2023-22521, affects versions 3.4.6 and 5.2 of Crowd Data Center and Server. Atlassian recommends upgrading to the latest version or to the following fixed versions:
- Crowd Data Center and Server 3.4: Upgrade to version 5.1.6 or later.
- Crowd Data Center and Server 5.2: Upgrade to version 5.2.1 or later.
Details of the CVE-2023-22521 vulnerability are also available in the SOCRadar Vulnerability Intelligence Module. The module provides insights into the vulnerability’s characteristics.
Are There Any Available PoC or Exploits?
As of now, SOCRadar researchers have not detected any Proof-of-Concept (PoC) or exploit code for CVE-2023-22521 being used by threat actors in either clear or dark web sources. Nevertheless, given the speed at which threat actors can identify and exploit vulnerabilities, it is crucial to monitor these vulnerabilities through the SOCRadar Vulnerability Intelligence module during the update period.