Syrus4 IoT Gateway Vulnerability Could Allow Code Execution on Thousands of Vehicles, Simultaneously (CVE-2023-6248)
A significant vulnerability affecting Syrus4 IoT Gateway has emerged, posing a serious threat to the worldwide automotive industry. This vulnerability, capable of giving hackers control over a fleet of vehicles and potentially shutting them down, has been left unattended by the vendor for an extended period.
Despite the gravity of the situation, the vendor, Digital Communications Technologies (DCT), has yet to tackle the identified vulnerability, leaving an open window for malicious actors to exploit and disrupt vehicles. The extent of Syrus4’s prevalence remains shrouded in uncertainty, however, alarmingly, there are over 119,000 DCT devices across more than 49 countries.
Let’s delve into the specifics of this vulnerability, reflecting on the emerging cyber threats within the automotive industry.
Details of the Syrus4 IoT Gateway Vulnerability: CVE-2023-6248
The critical vulnerability, designated as CVE-2023-6248, has been uncovered in Digital Communications Technologies’ (DCT) Syrus4 IoT Telematics Gateway 23.43.2 and carries a maximum CVSS score of 10.0. It was discovered by Yashin Mehaboobe from Xebia.
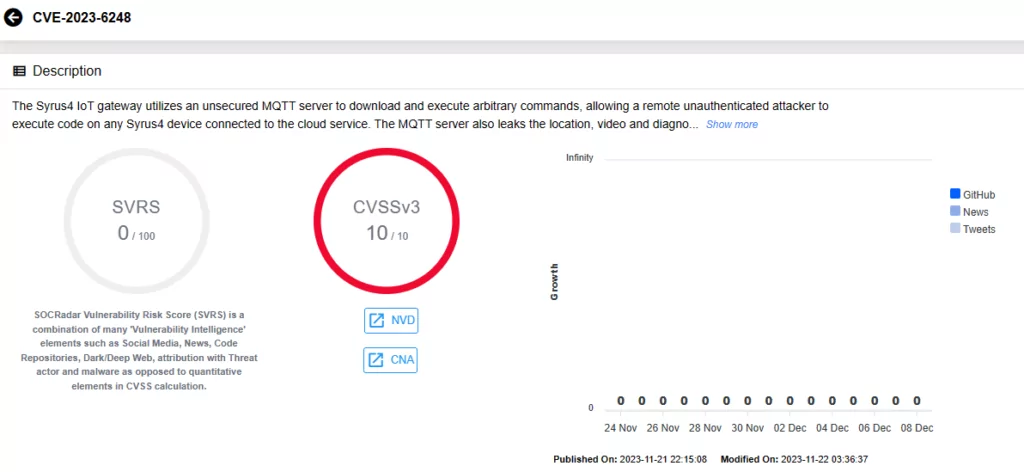
Rather than an exploit confined to individual vehicles, CVE-2023-6248 allows attackers to target software that are used for the management of fleets of vehicles. This elevates the risk, enabling hackers to compromise backend infrastructure and potentially impact thousands of vehicles, simultaneously.
Exploitation Method
The vulnerability permits unauthorized access to the Syrus4 IoT Gateway’s software, providing control over commands managing thousands of vehicles. With just an IP address and a simple Python script, attackers can access the Linux server, gaining control over live locations, engine diagnostics, speakers, airbags, and the ability to execute arbitrary code on vulnerable devices.
In detail, the vulnerability is identified as a very critical flaw in an MQTT Server functionality, compromising confidentiality, integrity, and availability. An unknown input manipulation results in an improper authentication vulnerability, where the product fails to verify an actor’s claimed identity. The unsecured MQTT server becomes an entry point for remote, unauthenticated attackers to execute code on any connected Syrus4 device.
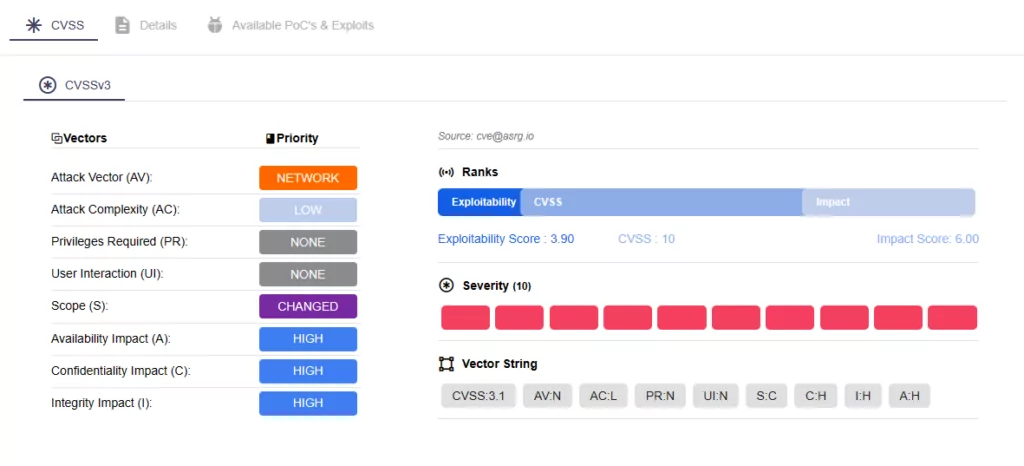
You can access the latest updates about the vulnerability effortlessly through SOCRadar’s Vulnerability Intelligence, staying informed as more details emerge, such as news on exploitations and the availability of Proof-of-Concept exploits (POCs).
Scope of the Vulnerability
The Syrus4 software’s most concerning feature is its ability to remotely turn off a vehicle. While the extent of potential harm remains untested, Mehaboobe’s discovery on the Shodan search engine revealed over 4,000 real-time vehicles connected to the server across the United States and Latin America.
As of now, there are no known exploitation activity regarding CVE-2023-6248. Urgent action is required from DCT to address and rectify this critical flaw, mitigating the risk of unauthorized access, control over fleets, and the potential to immobilize vehicles.
Silent Response to Critical Syrus4 IoT Gateway Vulnerability Raises Concern
Yashin Mehaboobe and Ramiro Pareja Veredas reported the vulnerability affecting the Syrus4 IoT Gateway in April, but the company’s response has been notably absent.
Efforts with the CERT Coordination Center to connect with the vendor were unfruitful, and the researchers previously refrained from naming the company due to the potential risks posed by malicious actors. The delayed disclosure, approved by CERT/CC and the Automotive Security Research Group, still awaits to be addressed by Digital Communications Technologies (DCT).
CyberScoop’s attempts to solicit a response from DCT met a similar fate. Their support ticket was closed, with an emailed response stating that the company had “escalated the matter internally,” promising further feedback if later available.
Gain Insights Into Industry-Specific Cyber Threats with SOCRadar
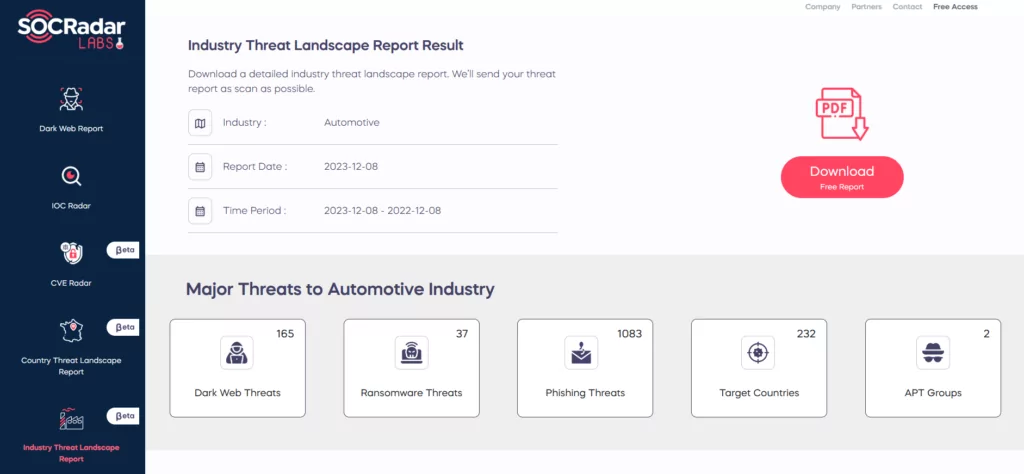
Explore the SOCRadar Labs’ Industry Threat Landscape Report for a comprehensive overview of cyber threats tailored to your industry. The feature, available for free on SOCRadar Labs, covers diverse industries, including the automotive sector, offering rapid insights into the latest cyber threats affecting your field.
With SOCRadar’s AI-powered monitoring capabilities, empower your cybersecurity defenses against potential threats; download your copy of the Industry Threat Landscape Report today for quick insights and fortify your organization’s resilience in seconds.