
Fixed Critical Severity Vulnerabilities (CVE-2022-45788) in Schneider Electric EcoStruxure Products, Modicon PLCs, and PACs
In the realm of industrial control systems (ICS), vulnerabilities pose significant risks to critical infrastructure sectors worldwide. There are recently fixed critical severity vulnerabilities discovered in Schneider Electric’s EcoStruxure Products, Modicon PLCs, and Programmable Automation Controllers (PACs).
Understanding the Risks
The identified vulnerabilities, come from relatively old CVE-2022-45788, categorized as Improper Check for Unusual or Exceptional Conditions (CWE-754), present severe risks to organizations utilizing Schneider Electric’s ICS solutions. These risks include unauthorized access to components, arbitrary code execution, Denial-of-Service incidents, and compromises to confidentiality and integrity.
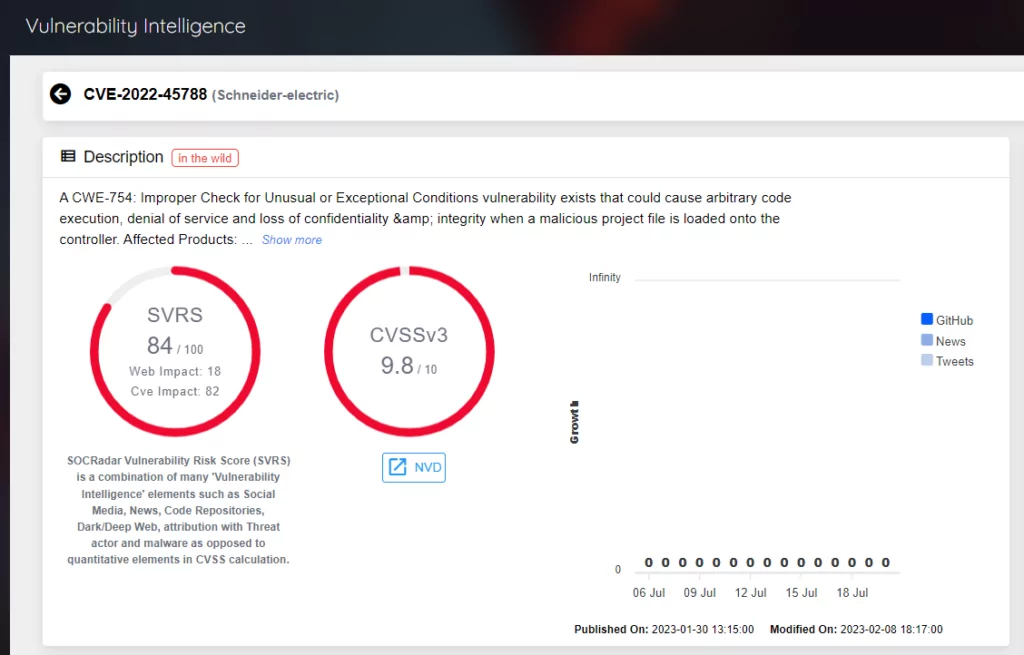
The severity of these vulnerabilities is evident from the base score assigned by different organizations. According to the Common Vulnerability Scoring System (CVSS), the vulnerabilities have a base score of 7.5 (High) from the vendor, indicating their significant impact. However, it’s important to note that the National Institute of Standards and Technology (NIST) assigns a higher base score of 9.8 (Critical) for these vulnerabilities. This distinction highlights the critical nature of the risks posed by these vulnerabilities and emphasizes the urgency of implementing remediation measures to prevent potential exploitation.
Adding to the concern, the Cybersecurity and Infrastructure Security Agency (CISA) has published a warning and an advisory regarding these vulnerabilities. This shows the importance of addressing these issues promptly to protect critical infrastructure and prevent potential cyber threats. Organizations should pay close attention to CISA’s guidance and follow the recommended mitigations provided to safeguard their ICS environments.
Affected Products and Technical Details
The vulnerabilities impact various Schneider Electric products, including EcoStruxure Control Expert, EcoStruxure Process Expert, Modicon M340 CPU, Modicon M580 CPU, Modicon M580 CPU Safety, Modicon Momentum Unity M1E Processor, Modicon MC80, Legacy Modicon Quantum, and Premium CPUs. Each of these products has specific versions that are vulnerable to exploitation.
Mitigations and Remediation
Schneider Electric has promptly responded to these vulnerabilities by releasing remediations that organizations should implement. The recommended actions include upgrading to secure versions, applying available software and firmware patches, and adhering to best practices for network hardening. By following these guidelines, organizations can significantly reduce the risk of exploitation and ensure the secure operation of their ICS infrastructure.
SOCRadar Vulnerability Intelligence and Extended Surface Management
SOCRadar’s Vulnerability Intelligence plays a crucial role in helping organizations stay informed about current security issues, vulnerabilities, and exploits. By continuously monitoring sources such as CISA alerts and the National Vulnerability Database (NVD), SOCRadar provides up-to-date information to support proactive vulnerability management. This intelligence enables organizations to prioritize remediation efforts based on the severity and impact of vulnerabilities.
Moreover, SOCRadar’s Extended Surface Management approach expands visibility beyond traditional network boundaries. It helps organizations identify vulnerabilities across all assets, including industrial control systems, and provides a comprehensive understanding of the potential attack surface. By integrating vulnerability intelligence, asset discovery, and continuous monitoring, SOCRadar empowers organizations to proactively manage and remediate vulnerabilities before they can be exploited.
Conclusion
The recent discovery and subsequent remediation of high severity vulnerabilities in Schneider Electric EcoStruxure Products, Modicon PLCs, and PACs underscore the critical importance of proactive vulnerability management. SOCRadar’s Vulnerability Intelligence and Extended Surface Management solutions play a vital role in helping organizations navigate the complex landscape of ICS security. By staying informed about vulnerabilities and adopting comprehensive vulnerability management practices, organizations can effectively protect their critical infrastructure and ensure the secure operation of their systems.




































