
Android Vulnerabilities That Do Not Get Fixed Function as a Zero-Day
Maddie Stone of Google’s Threat Analysis Group (TAG) authored the fourth annual year-in-review of zero-day vulnerabilities that attackers exploited in the wild. The report builds upon the mid-year 2022 review.
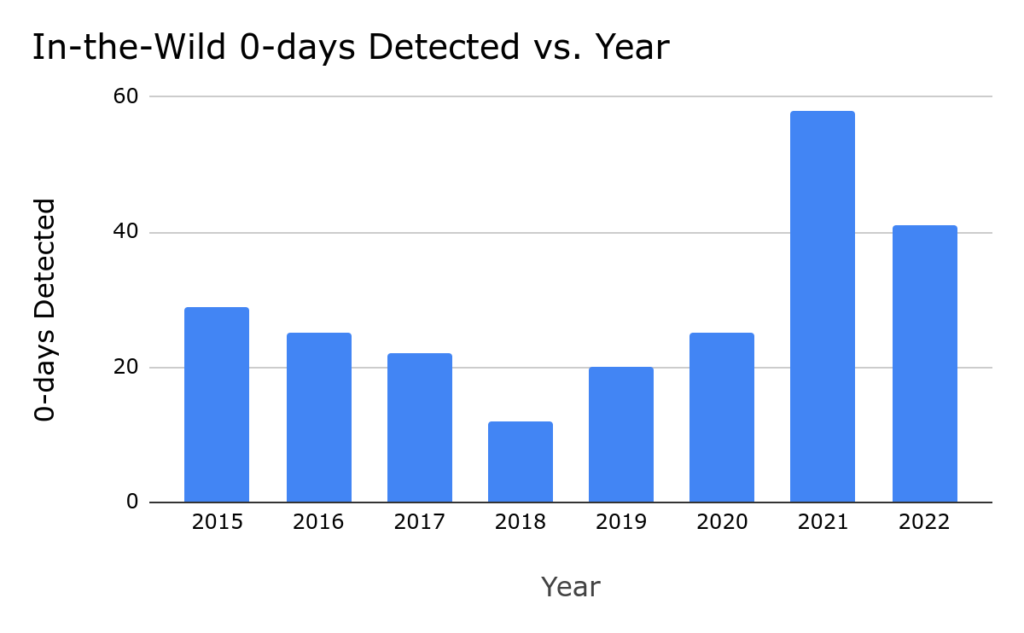
In the course of 2022, a total of 41 in-the-wild zero-day exploits were both identified and disclosed. While this marked the second-highest count since tracking began in mid-2014, it did indicate a decline from the 69 exploits detected in the previous year, 2021.
Although a 40% drop may seem like a clear triumph in the journey toward improved security, the reality of the matter is far more intricate and multifaceted.
Shift in Exploitation Techniques: The Rise of 0-Click Exploits
As highlighted in the report by Google TAG, attackers increasingly favored 0-click exploits over 1-click exploits, which means requiring user interaction to activate exploitation, targeting components beyond the browser. Additionally, major browsers introduced new defenses to thwart vulnerability exploitation, potentially motivating attackers to explore alternative attack surfaces.
However, the researchers emphasized that the 40% reduction in exploits cannot be solely attributed to enhanced security measures implemented by vendors.
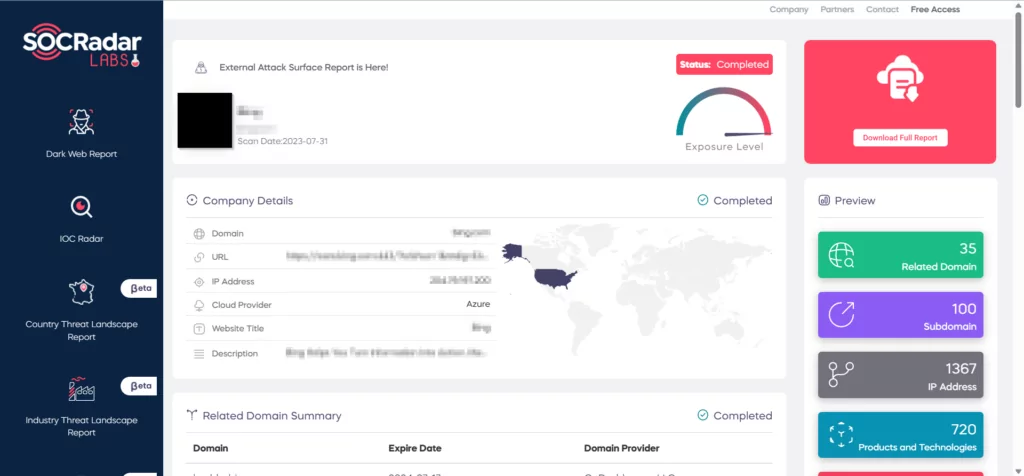
With SOCRadar’s advanced internet-wide tracking algorithms, you gain direct visibility into all technology assets facing the internet. This unique capability allows you to see your organization from the perspective of hackers, providing invaluable insights into potential vulnerabilities and threats. Stay one step ahead with SOCRadar’s comprehensive visibility and protect your digital assets with confidence.
Get started now and request your free report to explore your attack surface.
Previous Vulnerabilities Turned Into Zero-Day Vulnerabilities
The report revealed that more than 40% of the discovered zero-days in 2022 were variations of previously reported vulnerabilities (17 out of the 41 actively exploited zero-days). This trend suggests that developers may be repeating the same mistakes, leading to recurring vulnerabilities.
Additionally, the Android ecosystem’s challenges came to light: N-days functioned similarly to zero-day vulnerabilities due to delayed patches. This delay in patching is caused by various factors, including storage space, Wi-Fi connectivity, and battery status, all of which affect update implementation and provide attackers with more opportunities to exploit vulnerabilities.
Researchers also brought attention to how bug collisions increased in 2022, with attackers and security researchers utilizing the same vulnerabilities. When an in-the-wild zero-day targeting a popular consumer platform was identified and fixed, it often disrupted another attacker’s exploit.
Zero-Day Security: Key Points for Future Improvements
Based on the analysis of 2022 zero-day vulnerabilities, the industry should concentrate on the following areas:
- Implementing more comprehensive defense in depth approach and timely patching to address the use of variants and N-days as zero-days.
- Following browsers’ lead in releasing broader mitigations to make whole classes of vulnerabilities less exploitable on various platforms.
- Promoting transparency and collaboration between vendors and security defenders to share technical details and work together in detecting exploit chains that span multiple products.
Factors Influencing Detected and Disclosed Zero-Days:
- Improved security demands more zero-days for attackers.
- Faster discovery and fixing of zero-days limit their exploitation.
- Publicly disclosing zero-days helps mitigate threats.
- Incorporating security boundaries hinders vulnerability exploitation.
Factors Reducing Detected and Disclosed 0-Days:
- Developing zero-days becomes more costly and time-consuming.
- Enhanced security results in fewer exploitable zero-day vulnerabilities.
- Creating new exploitation techniques for each zero-day becomes more challenging.
- Discovering vulnerabilities in new attack surfaces becomes increasingly difficult.
- Slower detection extends the lifetime of exploitable bugs.
- Longer patching time provides attackers with more opportunities.
- Attackers find success with less sophisticated attack methods.
Prioritize Patches and Monitor Digital Assets with SOCRadar
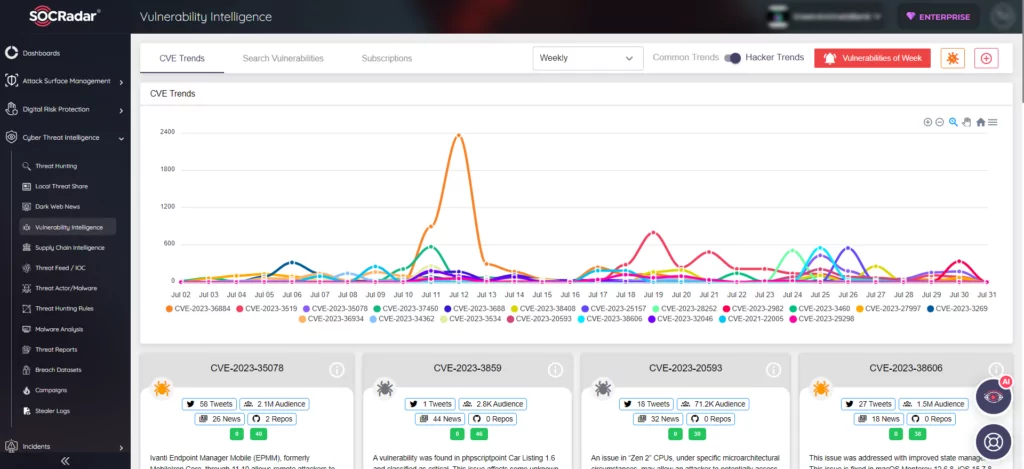
At SOCRadar, our Vulnerability Intelligence offers comprehensive assistance in managing vulnerabilities and prioritizing essential patches. With our platform, effortlessly search and access detailed vulnerability information to stay ahead of potential threats.
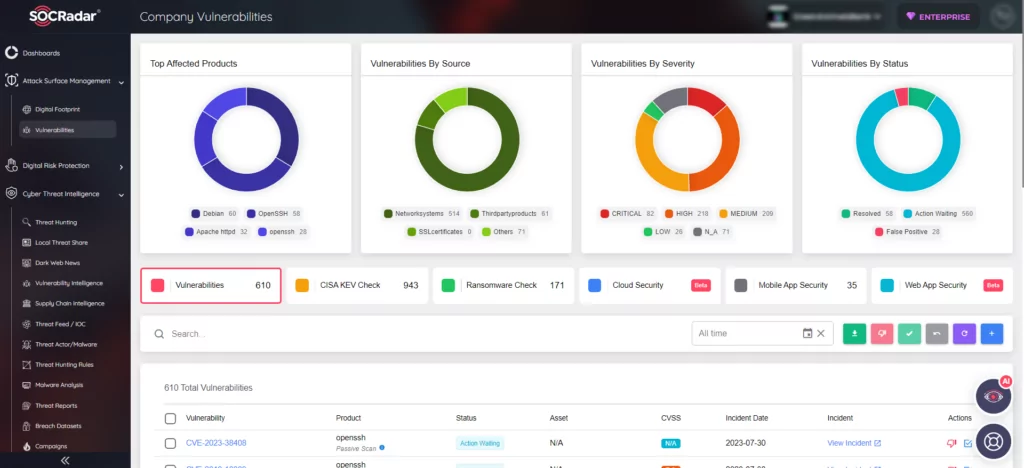
Additionally, our External Attack Surface Management (EASM) safeguards your digital assets. Through this advanced system, we diligently discover and monitor your digital landscape, providing prompt alerts on emerging issues that could jeopardize your security. Trust SOCRadar for proactive protection and fortify your online presence.
Sign up for a free edition of the SOCRadar XTI platform to learn more and stay up to date on the latest vulnerabilities.




































