
Zero-Day RCE Sale, Pizza Hut Access Sale & More
Welcome to the twisted world of the Dark Web, where the illicit trade of cyber weapons and stolen data thrives under the cover of anonymity. In this blog post, we will explore some of the most alarming cyber threat discoveries made by the SOCRadar Dark Web Team.
One such discovery is a threat actor offers a new zero-day RCE exploit for SS7 servers, demanding $80,000 worth of Monero. Also, unauthorized shell access to Pizza Hut, with 300,000 client records, is up for sale.
These discoveries highlight the ever-growing threat landscape and the critical importance of robust cybersecurity measures in our increasingly connected digital world. To know more about the other shocking incidents uncovered by the SOCRadar Dark Web Team, continue reading below.
Find out if your data has been exposed.
New 0-Day RCE is on Sale for a SS7 Server

The SOCRadar Dark Web Team has detected a post that a threat actor is claiming to be selling a new zero-day Remote Code Execution (RCE) exploit for a specific brand of SS7 servers. The exploit allegedly provides root access to the targeted SS7 server. The threat actor is demanding a payment of 80,000 USD worth of Monero (XMR) and insists on using escrow for the transaction.
SS7 (Signaling System 7) is a set of telecommunication protocols used for the exchange of signaling messages between network elements in a public switched telephone network (PSTN).
Unauthorized Shell Access Sale is Detected for Pizza Hut
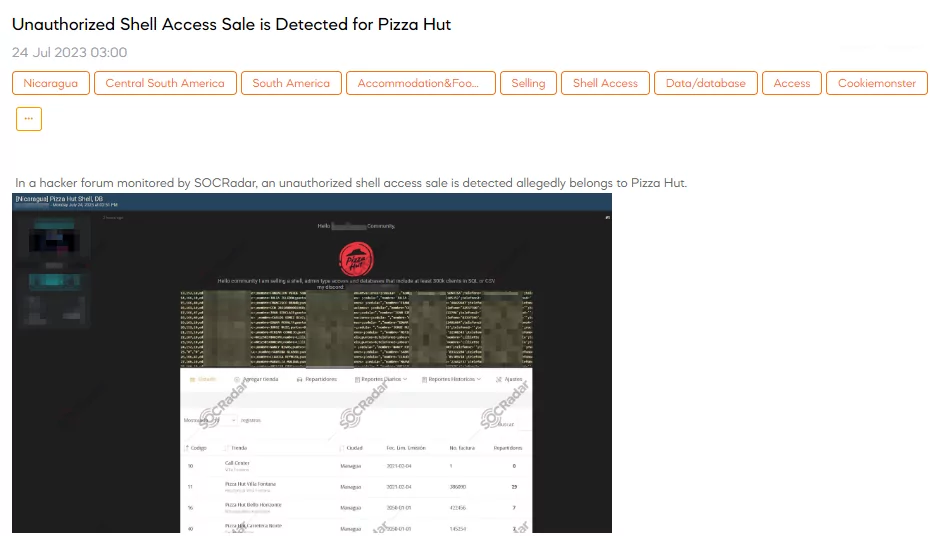
A SOCRadar dark web analyst has detected a post that a threat actor claims to be selling unauthorized shell access allegedly belonging to Pizza Hut. The threat actor states that they have admin access and databases containing at least 300,000 client records in SQL or CSV format.
Unauthorized Network Access Sale is Detected for a Telecommunication Company
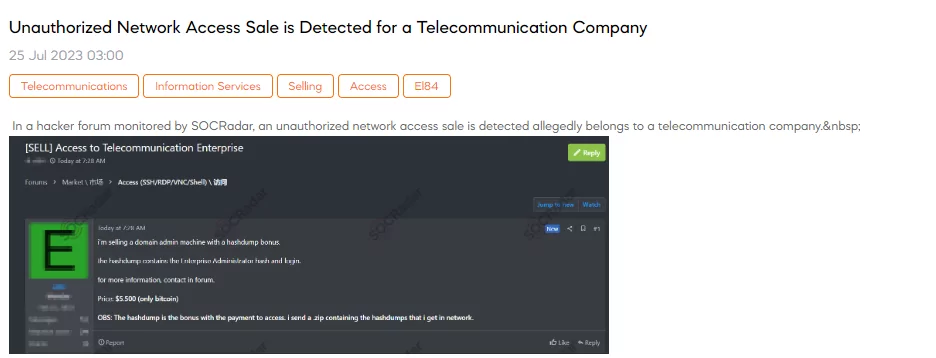
The SOCRadar Dark Web Team has detected a post that a threat actor claims to be selling unauthorized network access allegedly belonging to a telecommunication company. The offer includes a domain admin machine with a bonus of a hashdump, which contains the Enterprise Administrator hash and login credentials. The seller is requesting a payment of $5,500 in Bitcoin for this access, and they mention that the hashdump is provided as a bonus upon payment.
Database of UCHealth is Leaked

A SOCRadar researcher has detected a post that a threat actor claims to have leaked a database of UCHealth. UCHealth is a nonprofit health system that provides care to patients throughout Colorado. The actor states that the UCHealth database has been uploaded for download due to a data breach that occurred in July 2023. According to the claim, 1,341 user accounts were compromised in this breach. The leaked data includes sensitive information such as usernames, names, emails, registered sites, 2FA status, and last login details.
Mobile Database of Kuwait is on Sale

On July 28, SOCRadar detected a post where a threat actor claims to be selling an alleged mobile database for Kuwait. The sale purportedly includes mobile data of 4 million Kuwaiti individuals. The stated price for this data is $1,500. The provided sample contains “Number” and “Name” fields.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































