
Vulnerability in Python’s pandas Library (CVE-2024-42992)
[Update] August 27, 2024: CVE has been marked “REJECT” in the CVE List. Find more information in the blog post.
Python’s popular data analysis and manipulation library, pandas, was recently reported to be vulnerable to a significant security issue, CVE-2024-42992, exposing systems to potential unauthorized file access. This vulnerability didn’t have a patch by the time it was released.
Pandas is a cornerstone tool for data analysis in Python, widely utilized for its powerful capabilities in handling structured data. Given its extensive adoption in data science, finance, academic research, and many other fields, the discovery of CVE-2024-42992 was particularly alarming.
What is CVE-2024-42992?
CVE-2024-42992 is an arbitrary file read vulnerability in the pandas library, potentially allowing an attacker to access any file in the system without restriction, such as “/etc/passwd”, posing a serious security risk.
The issue was reported to stem from the insufficient validation of file paths provided as input, enabling malicious users to specify and read arbitrary files.
The vulnerability allegedly affected all versions of pandas up to and including 2.2.2.
SOCRadar’s Vulnerability Intelligence can help you stay informed about the latest CVE trends and exploitation patterns, offering comprehensive tools for proactive vulnerability management. Learn about the latest vulnerabilities, identify exploits, and gain actionable insights through the module.
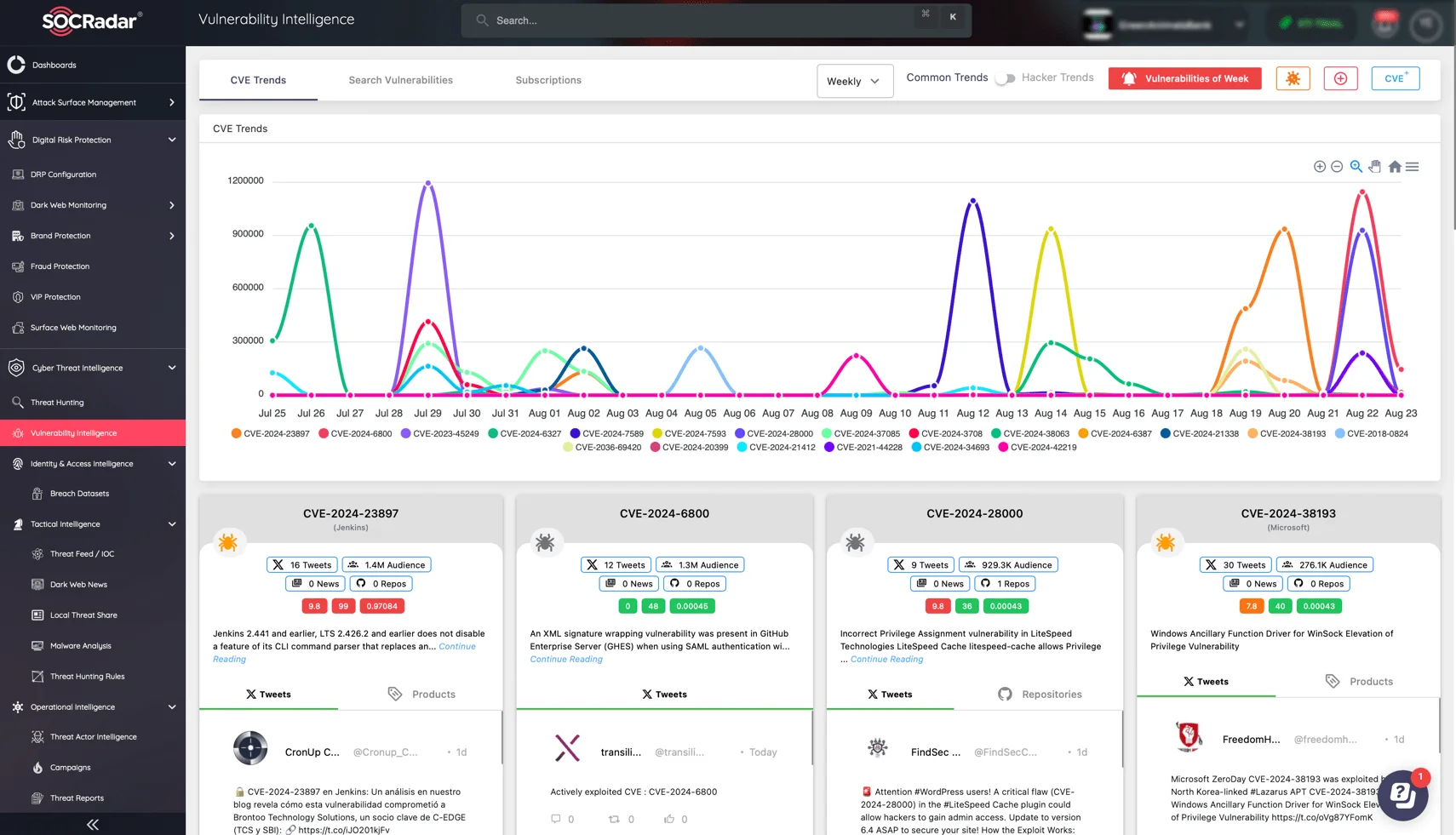
View the latest CVEs and hacker trends via SOCRadar’s Vulnerability Intelligence
Proof-of-Concept for CVE-2024-42992
A Proof-of-Concept (PoC) exploit for CVE-2024-42992 surfaced on GitHub. It demonstrated the vulnerability by attempting to read the “/etc/passwd” file, a critical file on Unix-based systems containing user account information.
According to the exploit GitHub page (which has since been removed), a simple exploit code that could be executed in a variety of environments, including Replit, could print the contents of a targeted sensitive file.
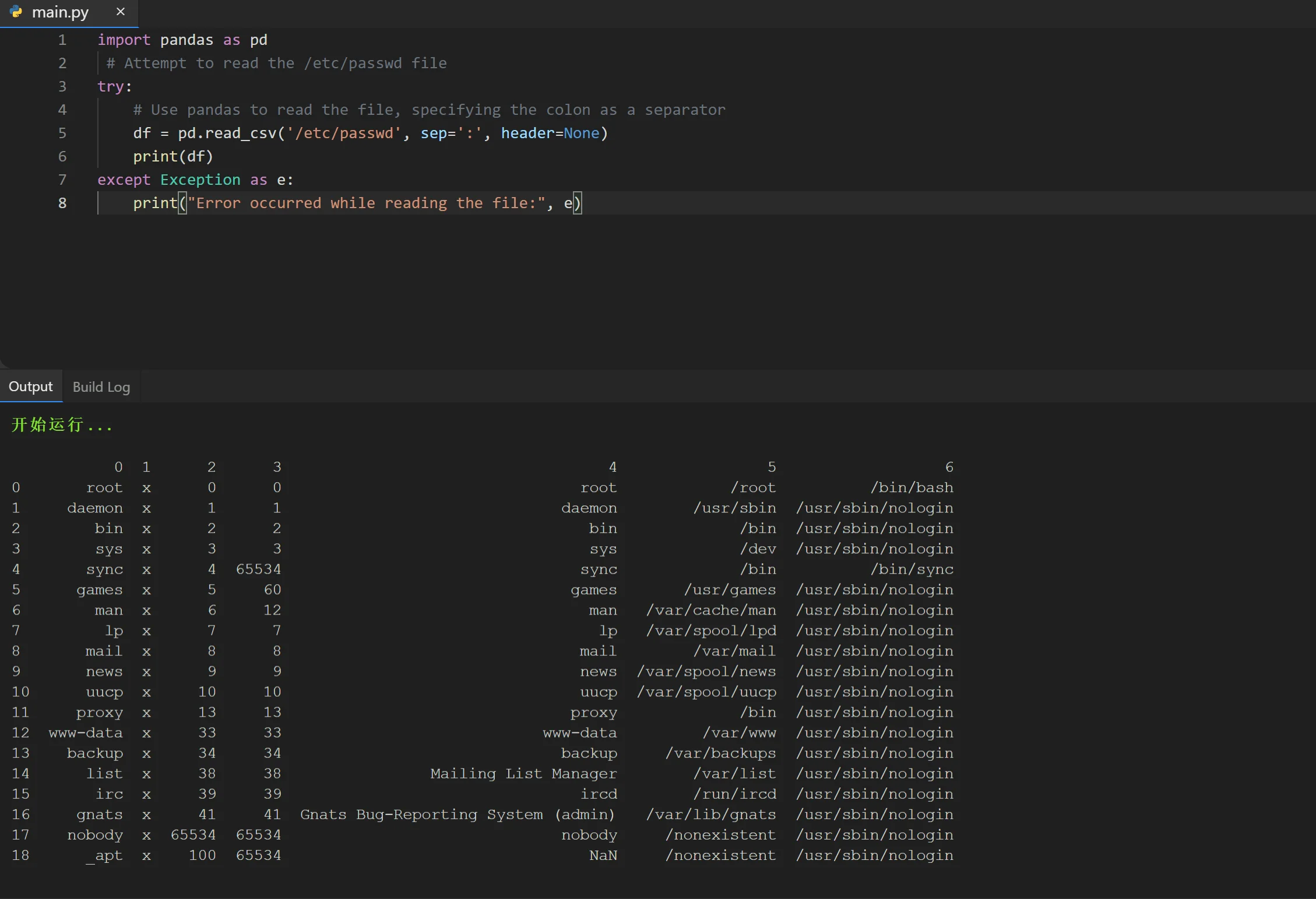
A demonstration of the exploit
Current Status and Recommendations
After noticing the removal of the exploit page from GitHub, we reviewed discussions regarding the vulnerability, particularly on the GitHub thread.
The comments suggested that the CVE should not have been assigned, as the so-called PoC was akin to a local user executing a basic command like `cat /etc/passwd`, which only demonstrated local access with existing user privileges.
The discussion clarified that the ability to read files via pandas was not a vulnerability in the library itself but rather a broader issue related to securing services that execute user-provided code.
As of the latest development, it appears that the CVE has been rejected.
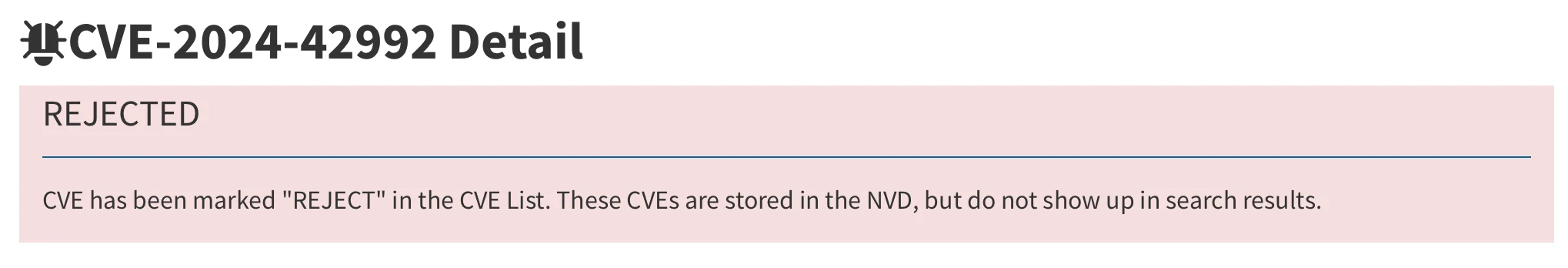
Notification at the top of the CVE-2024-42992 vulnerability page on the National Vulnerability Database (NVD)
Since the vulnerability has been deemed not an actual vulnerability, no further action is required on the users’ behalf. However, to maintain continuous monitoring of your digital assets against the vulnerabilities emerging every day, you can leverage SOCRadar’s Attack Surface Management (ASM) module.
SOCRadar’s ASM module, Company Vulnerabilities
The SOCRadar platform, with ASM, provides alerts for new security vulnerabilities affecting your assets, allowing for more efficient patch management and a stronger security posture.




































