
How the FBI Dismantled Raptor Train, a Major China State-Sponsored Botnet
In a major breakthrough, the FBI has recently dismantled “Raptor Train,” an extensive botnet controlled by state-sponsored hackers.
The botnet had a sophisticated three-tier system, and for the past four years, it has relentlessly targeted a wide range of high-profile entities, including government agencies, telecommunications companies, and defense contractors, primarily in the United States and Taiwan. Its inventive structure allowed the botnet to operate continuously and stealthily across international borders, posing challenges to global cybersecurity.
Managed by the PRC-based Integrity Technology Group since mid-2021, Raptor Train infiltrated over 260,000 devices worldwide, such as routers, firewalls, and various Internet of Things (IoT) devices.
The FBI, Cyber National Mission Force (CNMF), and the NSA have jointly released an advisory detailing the operations of the Raptor Train botnet. This blog post aims to outline the critical elements of the advisory, providing insights into the botnet’s technical framework, targeted vulnerabilities, and the implications of its activities.
What is the Raptor Train Botnet? Origins and Development
Discovered by cybersecurity researchers at Black Lotus Labs, Raptor Train is a sophisticated, multi-tiered botnet commandeering hundreds of thousands of IoT devices.
The Raptor Train botnet, operated by the China-based company Integrity Technology Group, has been active since mid-2021, targeting sectors primarily in the U.S. and Taiwan. Significantly, the botnet leveraged IP addresses previously associated with the Chinese espionage group Flax Typhoon (also known as RedJuliett and Ethereal Panda), suggesting possible connections to the group’s activities.
The threat actors behind the botnet make limited use of malware, instead exploiting legitimate software tools to maintain stealth and persistence. Researchers discovered that by mid-2023, the botnet had grown to encompass over 60,000 actively hacked devices, making it one of the largest botnets linked to Chinese state actors.
The botnet went undetected for four years, with a significant number of devices compromised in North American and European homes and offices. Its operations peaked in June 2023, leveraging reputable IP addresses to evade standard network security measures.
Keep track of cyber adversaries with SOCRadar’s Threat Actor Intelligence. This module offers advanced threat actor tracking, providing deep insights into the Tactics, Techniques, Procedures (TTPs), and activities of cyber threat actors, enabling you to anticipate and mitigate potential attacks.
SOCRadar’s Threat Actor Intelligence
Targets and Geographic Focus
Raptor Train has aggressively targeted an extensive range of sectors, reflecting its sophisticated, multi-tier structure that allows for operations on a massive scale.
Over the last four years, the botnet has compromised more than 260,000 devices, which include a wide array of modems, routers, IP cameras, and NAS (Network-Attached Storage) systems from manufacturers like ASUS, TP-LINK, and Synology, among others. Many of these devices were End-of-Life (EoL), lacking security updates, while others appeared newer, suggesting that threat actors may have been exploiting zero-day vulnerabilities to infect them.
Targeting efforts have been especially pronounced in the military, government, higher education, telecommunications, Defense Industrial Base (DIB), and IT sectors, primarily in the U.S. and Taiwan. In December 2023, botnet operators conducted extensive scanning operations aimed at these sectors, including global targets like a government agency in Kazakhstan.
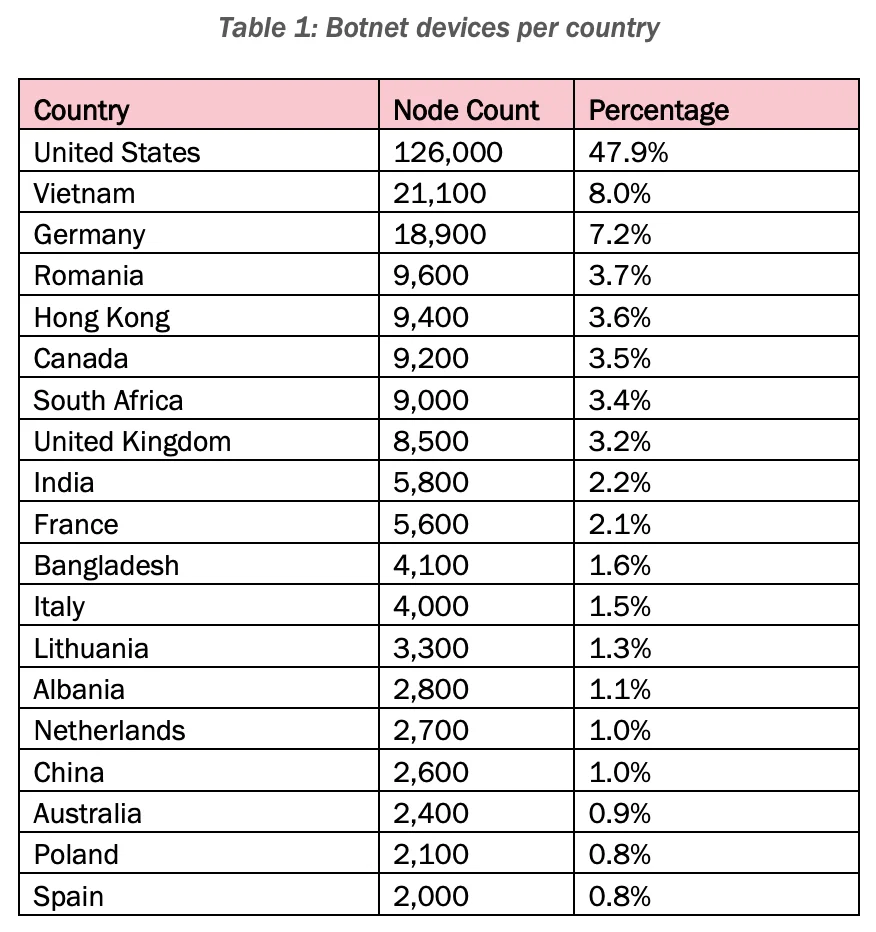
Distribution of Raptor Train botnet devices across countries, according to the joint advisory.
These efforts focused on potentially vulnerable software, notably Atlassian Confluence servers and Ivanti Connect Secure appliances, likely leveraging vulnerabilities such as CVE-2024-21887.
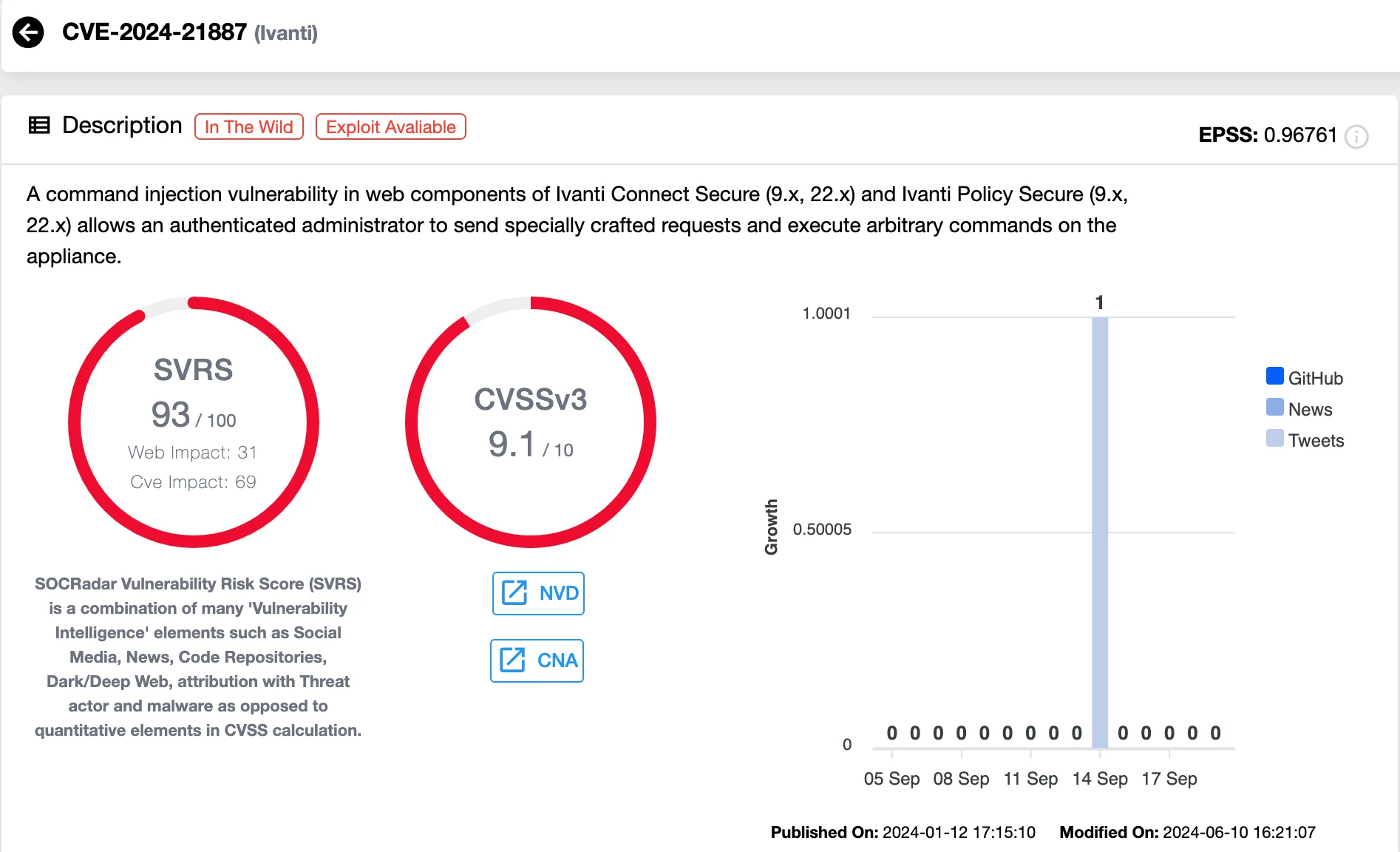
Details of the Ivanti Connect Secure command injection vulnerability, CVE-2024-21887 (SOCRadar Vulnerability Intelligence)
This strategic focus on critical infrastructure underscores the botnet’s potential not only for surveillance and data exfiltration but also for significant disruptive capabilities, such as DDoS attacks. Although no DDoS attacks were observed, the maintenance of such capabilities suggested a reserved potential for future offensive cyber operations.
Secure your digital frontier with SOCRadar’s Attack Surface Management (ASM) module – Discover, monitor, and secure every digital asset across your extended perimeter. Stay ahead of threats with continuous scanning and insightful risk assessments. SOCRadar ASM identifies exposed assets and vulnerabilities that affect your organization, while also ensuring better patch management, reducing the window of opportunity for attackers.
SOCRadar’s ASM module, Digital Footprint
Infrastructure of the Raptor Train Botnet
Raptor Train features a complex, multi-tiered Command and Control (C2) infrastructure with a centralized Node.js backend and a cross-platform application named “Sparrow.” This setup supports functionalities like remote command execution, file transfers, vulnerability management, and Distributed Denial-of-Service (DDoS) capabilities, though no DDoS attacks have been observed.
The botnet’s architecture is divided into three tiers:
- Tier 1: Comprises compromised devices such as modems, routers, IP cameras, and NAS systems. These devices are actively rotated, with an average operational period of 17 days.
- Tier 2: Houses exploitation servers and C2 nodes that coordinate the botnet’s operations.
- Tier 3: Managed through the “Sparrow” platform, this tier oversees the overall command and control of the network.
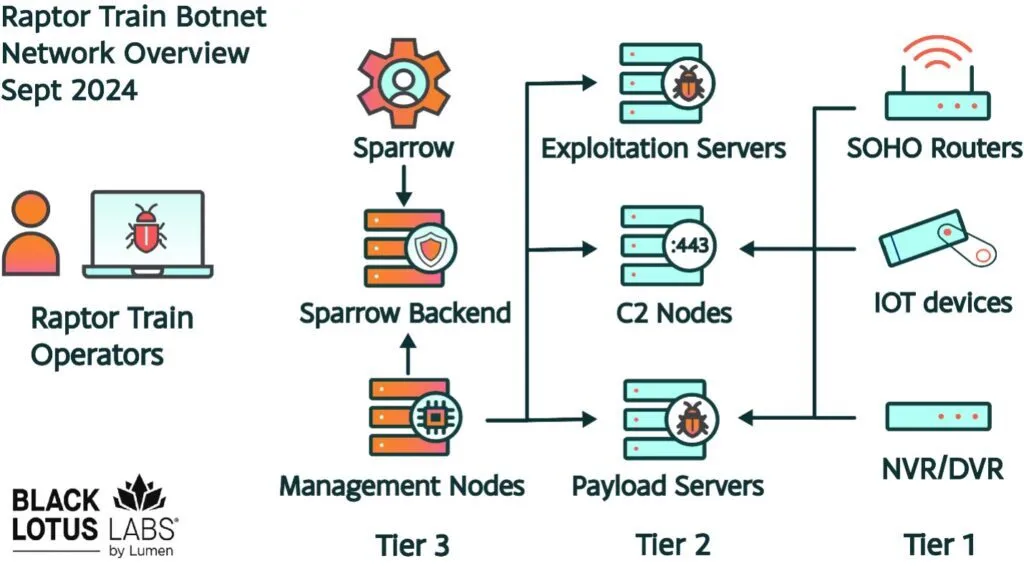
The architecture of Raptor Train (Lumen)
The primary malware, “Nosedive,” used in Tier 1, is a customized version of the notorious Mirai malware, designed for a wide range of devices and architectures including MIPS and ARM. It spreads through specially encoded URLs and domain injections and operates entirely in memory to evade detection.
Which Vulnerabilities Did Raptor Train Exploit?
The FBI has identified over 70 vulnerabilities targeted by the Raptor Train botnet’s operators, Integrity Tech, from 2019 to 2024, to expand the botnet’s reach across various sectors. These likely include the CVE-2024-21887 vulnerability Ivanti Connect Secure appliances, and other critical vulnerabilities such as:
- CVE-2024-5217: RCE in ServiceNow’s Now Platform.
- CVE-2024-4577: OS Command Injection in PHP.
- CVE-2024-29973: OS Command Injection in Zyxel NAS346 and NAS542 firmware.
- CVE-2024-21762: RCE in FortiOS and FortiProxy.
The vulnerabilities employed by the botnet represent a mix of zero-day and known issues, illustrating the botnet operators’ comprehensive approach to exploiting security gaps across a wide spectrum of device types and software environments.
Stay ahead of exploitation threats with SOCRadar’s Vulnerability Intelligence. The SOCRadar Extended Threat Intelligence (XTI) platform provides early warnings and actionable insights into emerging vulnerabilities, and exploitation activity, helping you secure your systems against potential exploits before they’re targeted. Protect your digital landscape with proactive, intelligence-driven defense.
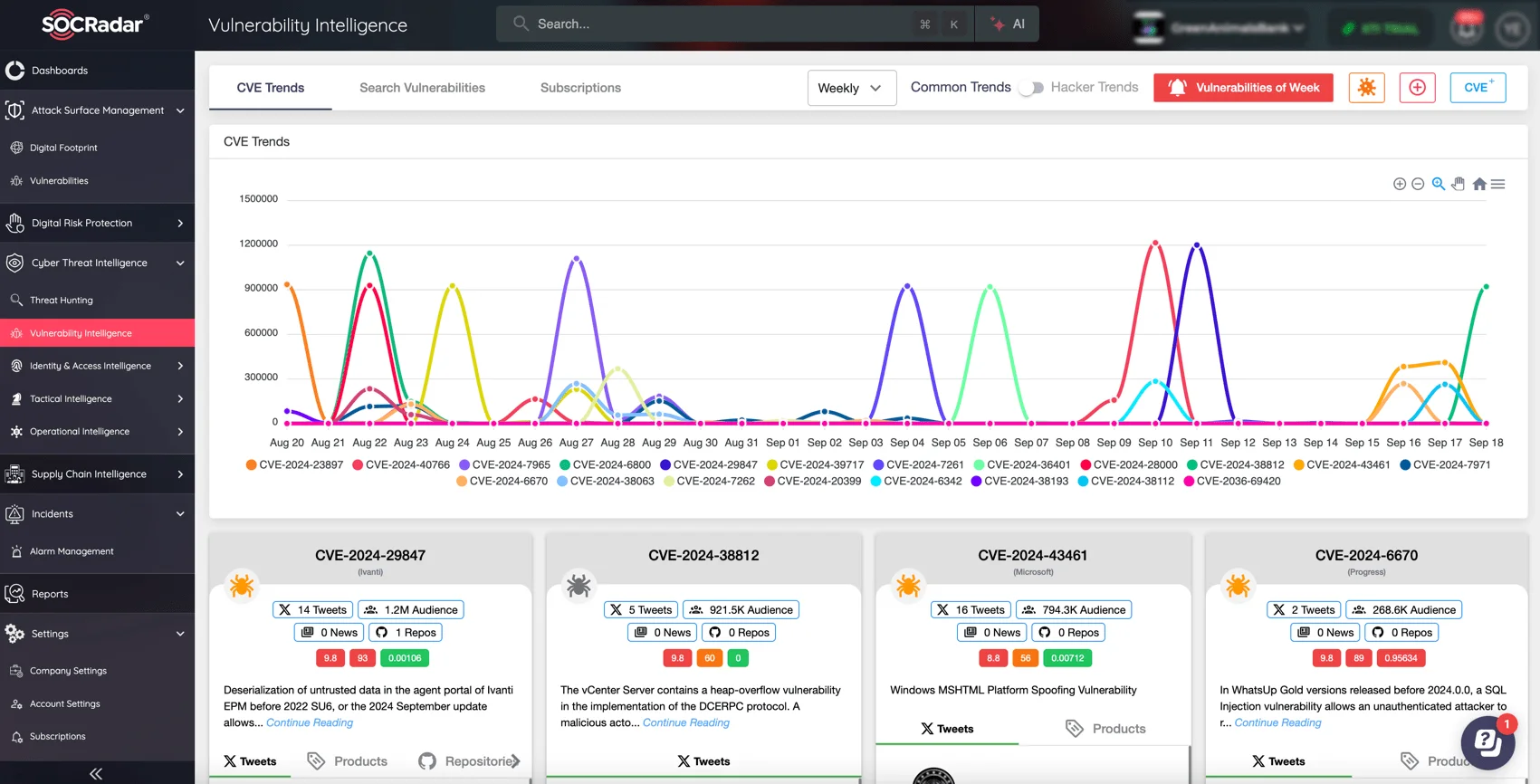
SOCRadar’s Vulnerability Intelligence
Reporting and Analysis from Authorities Regarding Raptor Train Botnet
The U.S. government attributes the Raptor Train botnet operations to Integrity Technology Group, a Chinese entity linked to the PRC government.
In the joint advisory by the FBI, Cyber National Mission Force (CNMF), and NSA, it is reported that the company used China Unicom Beijing Province Network IP addresses for remote control. Managed since mid-2021, the botnet included over 260,000 compromised devices across North America, Europe, and other regions.
The advisory extensively details the botnet’s use and tactics, serving as a resource for device vendors and operators to secure devices against such compromises.
What Can Organizations Do to Protect Against Botnets?
To counter the threats posed by botnets like Raptor Train, organizations must implement robust cybersecurity measures:
- Routine Device Maintenance: Regular security updates and device reboots can remove malware like Nosedive, which does not persist after a restart, reducing the risk of compromise.
- Disable Unused Services: Turn off unnecessary services like UPnP, remote management, and file-sharing to prevent malware access and spread.
- Network Segmentation and Monitoring: Segment networks to limit IoT device connectivity and monitor traffic for unusual volumes to detect potential DDoS attacks.
- Updates and Patching: Apply software and firmware updates regularly from trusted sources to close security gaps.
- Strong Password Policies: Replace default passwords with strong, unique credentials.
- Scheduled Device Reboots: Use scheduled reboots to minimize disruptions and clear potential malware.
- Hardware Updates: Replace outdated equipment no longer supported by vendors to avoid exploitation of known vulnerabilities.
Get real-time alerts on security anomalies and potential breaches with SOCRadar XTI. Customize your response framework and reduce incident resolution time, keeping your network safe and operational.
SOCRadar’s Alarm Management
For detailed strategies and a full list of Indicators of Compromise, refer to the U.S. government’s advisory on “Raptor Train,” available here.




































