
Critical Vulnerabilities in Pure Storage & Aruba Access Points Pose Unauthorized Access, RCE Risks
Security updates were released addressing critical vulnerabilities in both Pure Storage and Aruba Access Point systems.
The Pure Storage updates include two vulnerabilities with the highest possible CVSS score of 10, indicating severe risks such as privilege escalation and unauthorized access in Pure Storage’s FlashArray systems. Meanwhile, Aruba Access Points were also found to have critical vulnerabilities, potentially leading to remote code execution.
These products are vital for enterprise-level data storage and network management, making timely patching essential to avoid severe disruptions or cyberattacks.
Critical Vulnerabilities in Pure Storage Allow Privilege Escalation and Unauthorized Access
Pure Storage recently disclosed multiple high-severity vulnerabilities impacting their FlashArray storage systems, two of which have been given a maximum CVSS score of 10. These flaws could allow malicious actors to escalate privileges and gain unauthorized access, severely compromising the security of affected systems.
- CVE-2024-0001 (CVSS 10): A vulnerability exists in FlashArray’s Purity software, where a local account intended for initial array configuration remains active. This could allow attackers to gain elevated privileges and perform unauthorized actions within the system.
- CVE-2024-0002 (CVSS 10): Another critical flaw in FA Purity allows a privileged account to be exploited for remote access, enabling malicious users to control the array and modify its settings remotely.
In addition to these critical vulnerabilities, the following are also of significant concern with CVSS scores of 9.1:
- CVE-2024-0003 (CVSS 9.1): This flaw could allow an attacker to create an unauthorized privileged account through a remote administrative service, potentially compromising system integrity.
- CVE-2024-0004 (CVSS 9.1): A user with administrator access to the array can execute arbitrary commands remotely, escalating their privileges within the system.
- CVE-2024-0005 (CVSS 9.1): This vulnerability enables remote command execution through a specially crafted SNMP configuration, affecting both FlashArray and FlashBlade systems.
Given the severity of these vulnerabilities, immediate action is required to prevent unauthorized access, privilege escalation, and potential disruptions to critical operations.
Which Versions of Pure Storage FlashArray and FlashBlade Are Affected?
The recent vulnerabilities affect specific versions of Pure Storage’s FlashArray and FlashBlade systems. Below is a breakdown of the affected versions by vulnerability:
CVE-2024-0001 (CVSS 10):
- Affects FlashArray versions: 6.3.0 – 6.3.14, 6.4.0 – 6.4.10.
CVE-2024-0002 (CVSS 10), CVE-2024-0003 (CVSS 9.1):
- Affects FlashArray versions: 5.3.17 – 5.3.21, 6.0.7 – 6.0.9, 6.1.8 – 6.1.25, 6.2.0 – 6.2.17, 6.3.0 – 6.3.14, 6.4.0 – 6.4.10, 6.5.0.
CVE-2024-0004 (CVSS 9.1):
- Affects FlashArray versions: 5.0.0 – 5.0.11, 5.1.0 – 5.1.17, 5.2.0 – 5.2.7, 5.3.0 – 5.3.21, 6.0.0 – 6.0.9, 6.1.0 – 6.1.25, 6.2.0 – 6.2.17, 6.3.0 – 6.3.14, 6.4.0 – 6.4.10, 6.5.0.
CVE-2024-0005 (CVSS 9.1):
- Affects FlashArray versions: 5.0.0 – 5.0.11, 5.1.0 – 5.1.17, 5.2.0 – 5.2.7, 5.3.0 – 5.3.21, 6.0.0 – 6.0.9, 6.1.0 – 6.1.25, 6.2.0 – 6.2.17, 6.3.0 – 6.3.14, 6.4.0 – 6.4.10, 6.5.0 and 6.6.0.
- Affects FlashBlade versions: 3.0.0 – 3.0.9, 3.1.0 – 3.1.15, 3.2.0 – 3.2.10, 3.3.0 – 3.3.11, 4.0.0 – 4.0.6, 4.1.0 – 4.1.10, 4.2.0 – 4.2.3, 4.3.0 – 4.3.1.
These are the vulnerable versions, and updating to the latest unaffected versions is critical to maintaining the security of your Pure Storage FlashArray and FlashBlade systems.
Versions Addressing Pure Storage Vulnerabilities
Pure Storage has released patches to address the critical vulnerabilities affecting FlashArray and FlashBlade systems. Users are strongly advised to update their systems to the following versions to mitigate the risks of unauthorized access and privilege escalation:
- For FlashArray vulnerabilities (CVE-2024-0001, CVE-2024-0002, CVE-2024-0003, CVE-2024-0004, CVE-2024-0005), upgrading to versions 6.3.15, 6.5.1, 6.6.1, or later is recommended.
- For the FlashBlade vulnerability (CVE-2024-0005), upgrading to versions 4.1.2, 4.3.2, or later is recommended.
Visit the official security bulletin by Pure Storage for more information.
SOCRadar’s Vulnerability Intelligence module can help organizations assess vulnerabilities, monitor exploit trends, and stay updated on patch management requirements. By using this tool, your security teams gain real-time insights into newly discovered vulnerabilities, ensuring timely patching and reducing exposure to potential exploits.
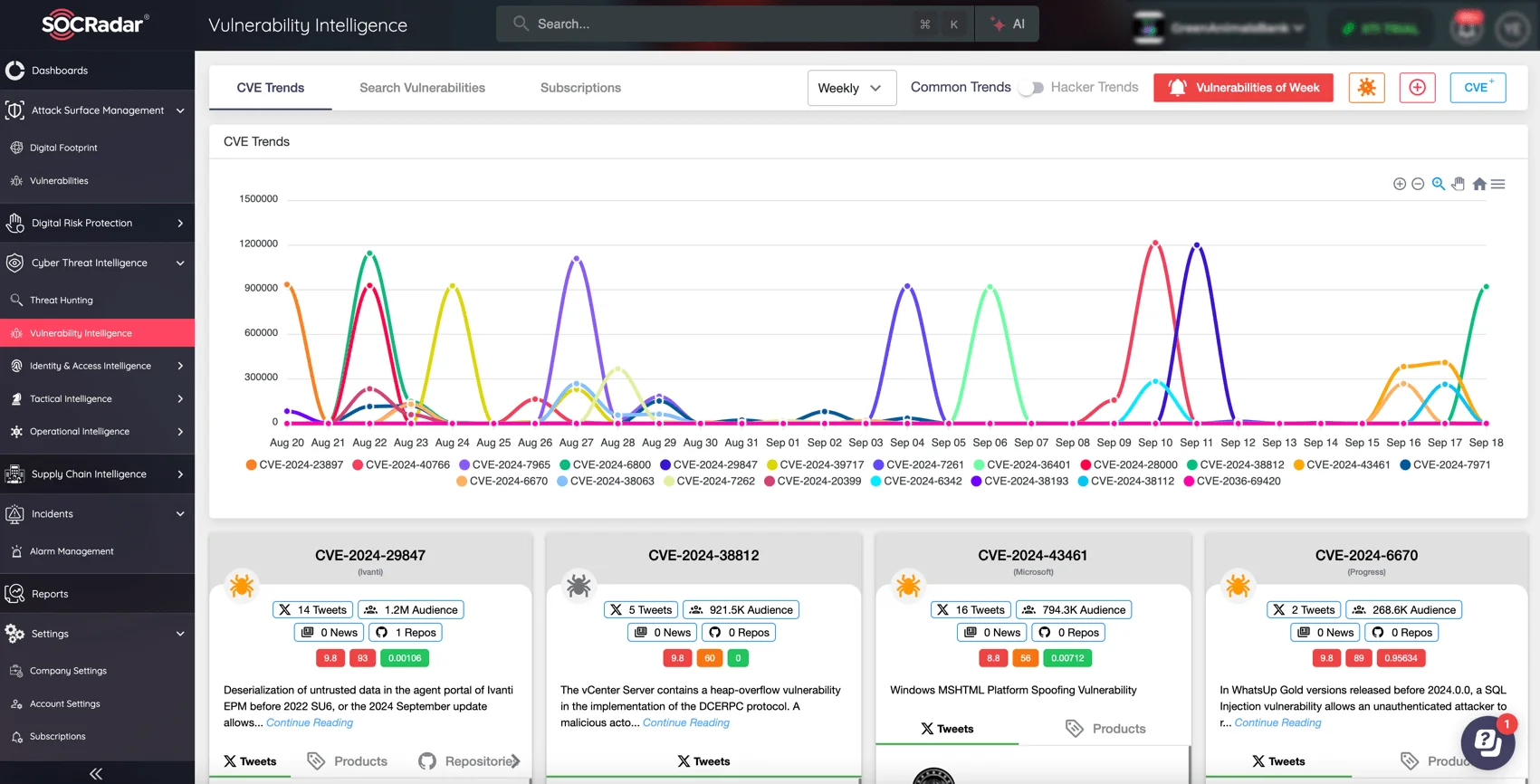
SOCRadar Vulnerability Intelligence: Easily track CVE and exploitation updates
Critical Security Flaws Found in Aruba Access Points, Allowing RCE
Alongside Pure Storage, Hewlett Packard Enterprise (HPE) has also recently rolled out critical updates, addressing several critical vulnerabilities in Aruba Access Points.
The updates for HPE Aruba Networking Access Points particularly address vulnerabilities that pose a significant risk of Remote Code Execution (RCE) with privileged access.
Critical Command Injection Vulnerabilities in Aruba Access Points (CVE-2024-42505, CVE-2024-42506, CVE-2024-42507)
These vulnerabilities, tracked as CVE-2024-42505, CVE-2024-42506, and CVE-2024-42507, have CVSS scores of 9.8. If successfully exploited, attackers could remotely execute arbitrary code by sending specially crafted packets to the PAPI management protocol on UDP port 8211, potentially giving them privileged access to the affected systems and compromising the entire network.
These flaws are critical and need urgent patching to prevent attackers from gaining unauthorized access and disrupting network operations.
The command injection vulnerabilities affecting Aruba Access Points primarily target devices running Instant AOS-8 and AOS-10 software versions. Below are the specific versions impacted by these flaws:
- AOS-10 versions 10.6.0.2, 10.4.1.3 and prior
- Instant AOS-8 versions 8.12.0.1, 8.10.0.13 and prior
The End-of-Life (EoL) versions of the product are also impacted by these vulnerabilities and will not receive these or any further patches.
Fixed Versions and Mitigation for Aruba Access Point Vulnerabilities
To address the command injection vulnerabilities in Aruba Access Points, Hewlett Packard Enterprise (HPE) has released updated software versions that fully mitigate these flaws. Organizations should upgrade to the following versions to ensure protection:
- AOS-10 versions 10.4.1.4, 10.6.0.3, 10.7.0.0 and later
- Instant AOS-8 versions 8.10.0.14, 8.12.0.2 and later
If updating to a patched version isn’t possible right away, you can temporarily mitigate the risk factors; for Instant AOS-8.x devices, enabling cluster-security can block exploitation. For AOS-10 devices, since cluster-security isn’t available, blocking UDP port 8211 from untrusted networks is necessary to prevent attacks. Refer to the HPE advisory for further information.
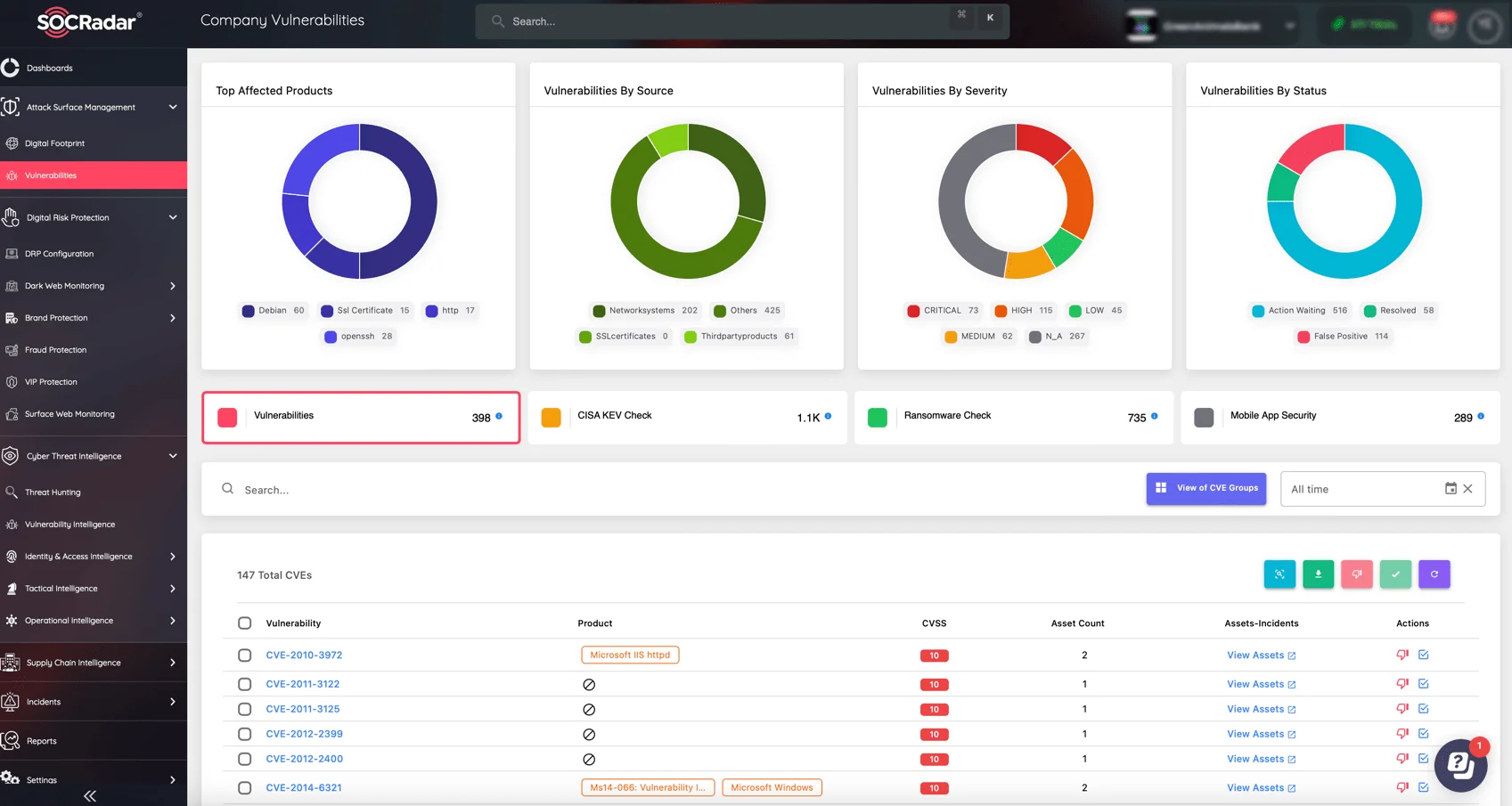
Monitor Company Vulnerabilities with SOCRadar’s Attack Surface Management (ASM) module
In addition to applying patches and mitigations, using SOCRadar’s Attack Surface Management (ASM) module can provide continuous monitoring and visibility into your organization’s network. ASM helps detect exposed assets, monitor for vulnerabilities, and ensure proactive defense against potential exploits.




































