
Foxit Reader Vulnerability (CVE-2024-28888): PoC Code Released, Patch to Prevent Attacks
Details and a Proof-of-Concept (PoC) exploit code for a serious vulnerability in Foxit Reader have recently emerged, raising concerns about its potential use in real-world cyberattacks.
Tracked as CVE-2024-28888, researchers first reported this vulnerability in April. Foxit issued a patch on September 26, but the technical details became public just lately, on October 2.
As one of the most popular tools for managing and creating PDF documents, and a widely-used alternative to Adobe Acrobat Reader, Foxit now faces heightened security risks if left unpatched, as this flaw could allow attackers to execute arbitrary code.
What is CVE-2024-28888?
CVE-2024-28888 (CVSS 8.8) is a use-after-free vulnerability in Foxit Reader, resulting from improper handling of a checkbox field object.
Attackers can exploit this vulnerability by embedding malicious JavaScript in a specially crafted PDF, leading to memory corruption and arbitrary code execution. However, user interaction is required. Attackers must deceive the user into opening the malicious file, typically through phishing tactics.
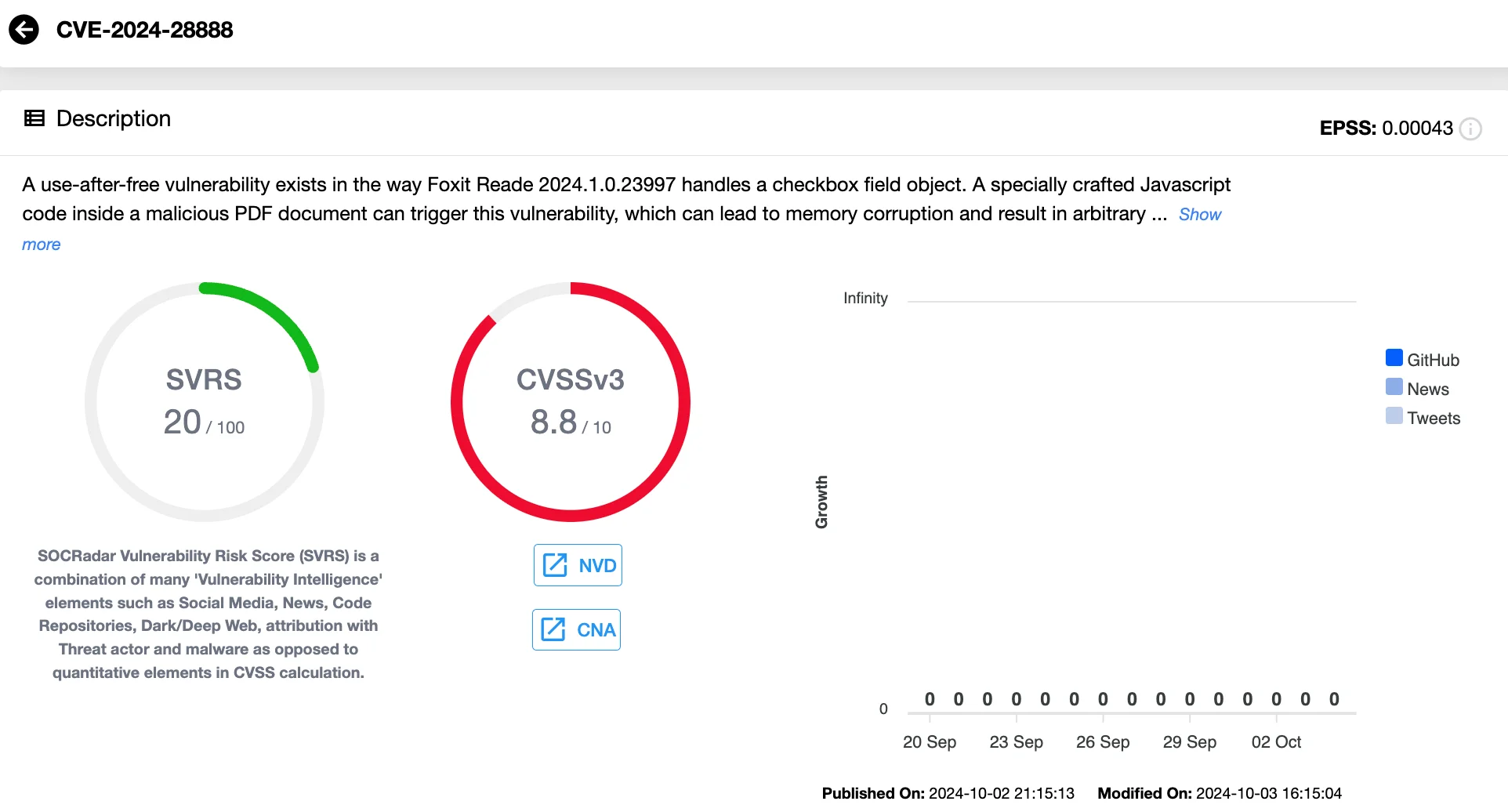
CVE-2024-28888, Use-After-Free vulnerability in Foxit Reader (SOCRadar Vulnerability Intelligence)
If Foxit’s browser plugin is active, simply visiting a compromised website could also launch the attack without directly opening the file.
With SOCRadar’s Vulnerability Intelligence module, you can access real-time updates on critical vulnerabilities like CVE-2024-28888, including available exploits and patch information.
Search vulnerabilities, see the latest activity, and follow CVE and hacker trends via SOCRadar Vulnerability Intelligence
Search for detailed insights on every identified vulnerability and ensure your systems are secured before attackers take advantage. Stay protected with comprehensive data and actionable intelligence.
Which Foxit Reader Version Is Affected?
The CVE-2024-28888 vulnerability affects Foxit Reader version 2024.1.0.23997. Users of this version are urged to update to the latest release to protect against potential exploits.
Technical Details and Exploit
Cisco Talos recently made the technical details and Proof-of-Concept (PoC) exploit code for CVE-2024-28888 publicly available. The vulnerability, discovered by researcher KPC, stems from how Foxit Reader handles checkbox field objects.
KPC’s write-up highlights that Foxit Reader’s JavaScript support, powered by the V8 engine, while essential for creating interactive forms and dynamic documents, introduces additional attack vectors.
The PoC code is as follows:
function main() {
var aa = app.activeDocs[0].addField("ADD", "checkbox", 2, [17,0,5,14]).defaultIsChecked(0);
getField("txt3").setAction("Calculate", 'delete_pages();');
app.activeDocs[0].addField("ADD", "checkbox", 0, [17,0,5,14]);
function delete_pages(arg1, arg2, arg3) {
app.activeDocs[0].deletePages();
app.activeDocs[0].deletePages();
}
}
The code creates a checkbox field object and assigns a callback function to the Calculate event of a text field. When triggered, the delete_pages function deletes pages in the document. The vulnerability arises when the checkbox field object is freed by deletePages() and then used without proper validation.
During exploitation, functions like addField() and CreateControl manipulate memory addresses and registers; this includes calls to functions like addField() and CreateControl, which are involved in managing the vulnerable buffer.
All in all, this vulnerability emphasizes the risks of JavaScript support in PDF readers and the importance of timely updates to mitigate such security risks.
For further technical details, see the full vulnerability report on Talos Intelligence.
Update Foxit PDF Reader/Editor to Prevent Exploitation
To stay protected, it’s critical to update your Foxit PDF Reader or Editor to the latest versions (v2024.3 and v13.1.4, respectively). These updates fix the CVE-2024-28888 vulnerability, as well as several other critical issues.
In addition to CVE-2024-28888, the update addresses CVE-2024-7722 and other vulnerabilities tied to Use After Free, Out-of-Bounds Read/Write, and Privilege Escalation flaws. These vulnerabilities could allow attackers to execute remote code, escalate privileges, or cause system crashes.
Overall, to reduce the risk of PDF-based attacks:
- Avoid opening PDF files from unfamiliar or untrusted sources.
- Use a reliable security solution to scan files before opening them.
- Ensure software is regularly updated to the latest security patches.
Monitor your digital assets and company vulnerabilities with SOCRadar’s Attack Surface Management
SOCRadar’s Attack Surface Management (ASM) module identifies exposed digital assets, helping you understand potential entry points and gain critical insights for patch management. Continuously monitor for risks and take proactive measures to reduce your attack surface.




































