
Critical VMware Vulnerability Patched Again in vCenter Server: CVE-2024-38812
[Updated] November 19, 2024: “VMware vCenter Server Vulnerabilities (CVE-2024-38812 and CVE-2024-38813) Actively Exploited in the Wild”
In a recent security disclosure, VMware has patched a critical vulnerability (CVE-2024-38812) affecting its vCenter Server, the cornerstone of many organizations’ virtualized infrastructures. An attacker with network access to vCenter Server could exploit this flaw by sending a specially crafted network packet, potentially leading to RCE and full system compromise. SOCRadar covered this vulnerability when it was first identified during the 2024 Matrix Cup hacking contest in China.
CVE-2024-38812: A Critical Heap-Overflow Flaw
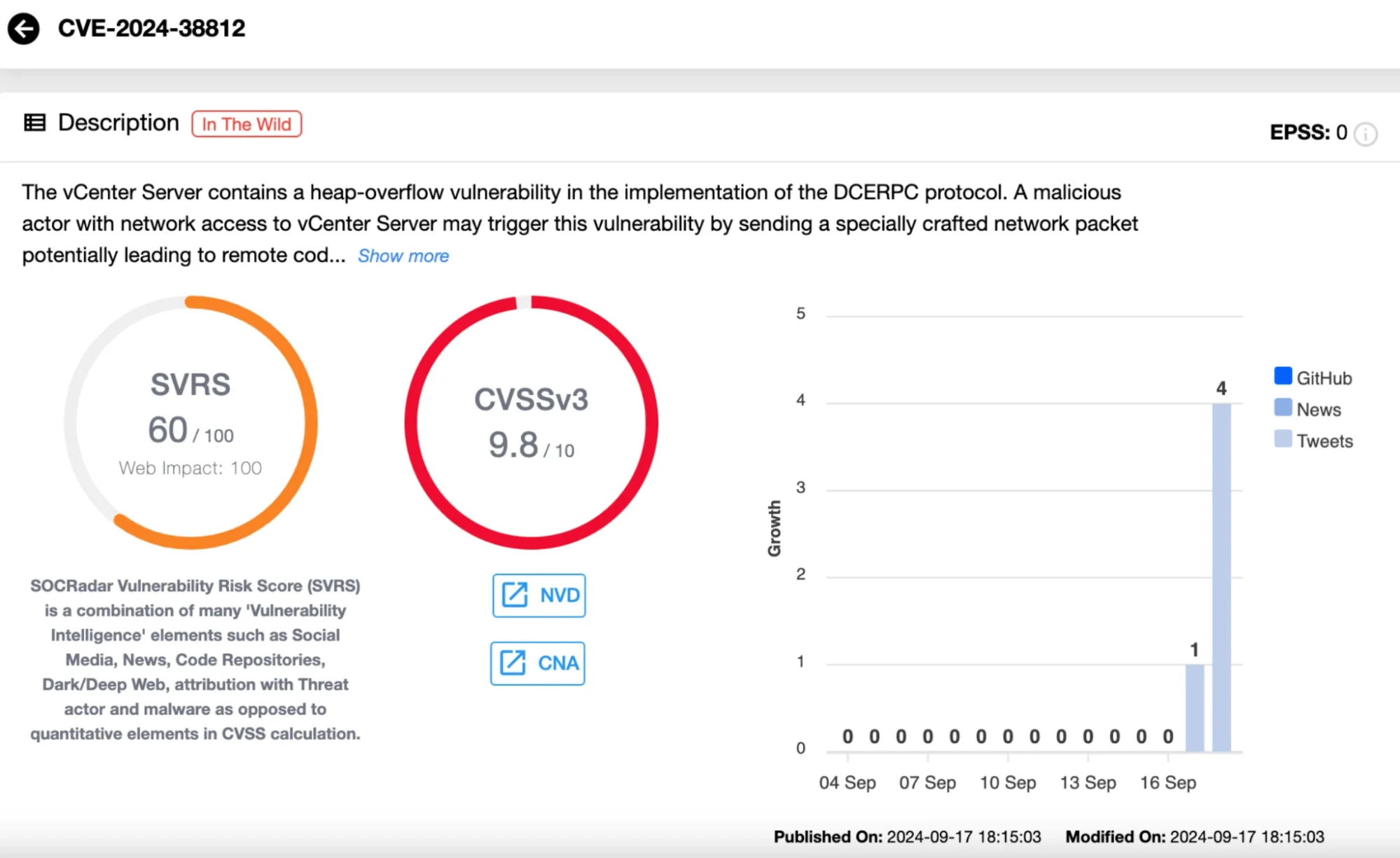
Vulnerability card of the CVE-2024-38812 vulnerability (SOCRadar Vulnerability Intelligence)
CVE-2024-38812 carries a CVSS score of 9.8, placed in the “critical” category. The flaw stems from a heap-overflow issue within the Distributed Computing Environment/Remote Procedure Call (DCERPC) protocol. This protocol allows for distributed computing, a common requirement in enterprise environments, but this vulnerability opens up a potential attack vector.
A malicious actor with network access to vCenter Server could exploit this flaw by sending a specially crafted network packet. This could lead to Remote Code Execution (RCE), allowing the attacker to compromise the entire system. While there have been no known instances of this vulnerability being exploited in the wild, the threat is significant.
VMware’s Response and Patching
VMware initially released patches for this vulnerability on September 17, 2024, but soon found that the patches did not fully address the issue. The latest update came on October 21, 2024, via the Broadcom Support page where another vulnerability, CVE-2024-38813 was also patched alongside CVE-2024-38812. The company issued additional patches to fully mitigate the risk. Affected versions include VMware Cloud Foundation and VMware vCenter Server, with specific fixed versions listed in VMware’s Response Matrix.
To remediate CVE-2024-38812, organizations should apply the following patches based on their VMware product versions:
- VMware Cloud Foundation 4.x – Update to 7.0 U3t
- VMware Cloud Foundation 5.1.x – Update to 8.0 U2e
- VMware Cloud Foundation 5.x – Update to 8.0 U3d
- VMware vCenter Server 7.0 – Update to 7.0 U3t
- VMware vCenter Server 8.0 – Update to 8.0 U2e or 8.0 U3d
While in-product workarounds were investigated, VMware determined that no viable alternatives exist, making patching the only effective resolution.
Organizations need real-time insights to avoid being blindsided by exploits that can compromise their systems and data. SOCRadar’s Vulnerability Intelligence provides comprehensive, up-to-date information on vulnerabilities across various platforms and technologies. It offers detailed analysis, alerts on emerging threats, and helps you prioritize which vulnerabilities to address first.
Stay updated on the latest CVEs and hacker activities with SOCRadar’s Vulnerability Intelligence
By integrating SOCRadar’s Vulnerability Intelligence into your security strategy, you gain proactive defenses, timely notifications, and actionable insights to keep your systems secure and resilient.
How Many VMware vCenter Server Instances Remain Vulnerable?
Shadowserver monitors this threat, and as of October 21, 2024, there are still numerous instances potentially vulnerable to CVE-2024-38812. Over 200 of these instances are located within the United States.
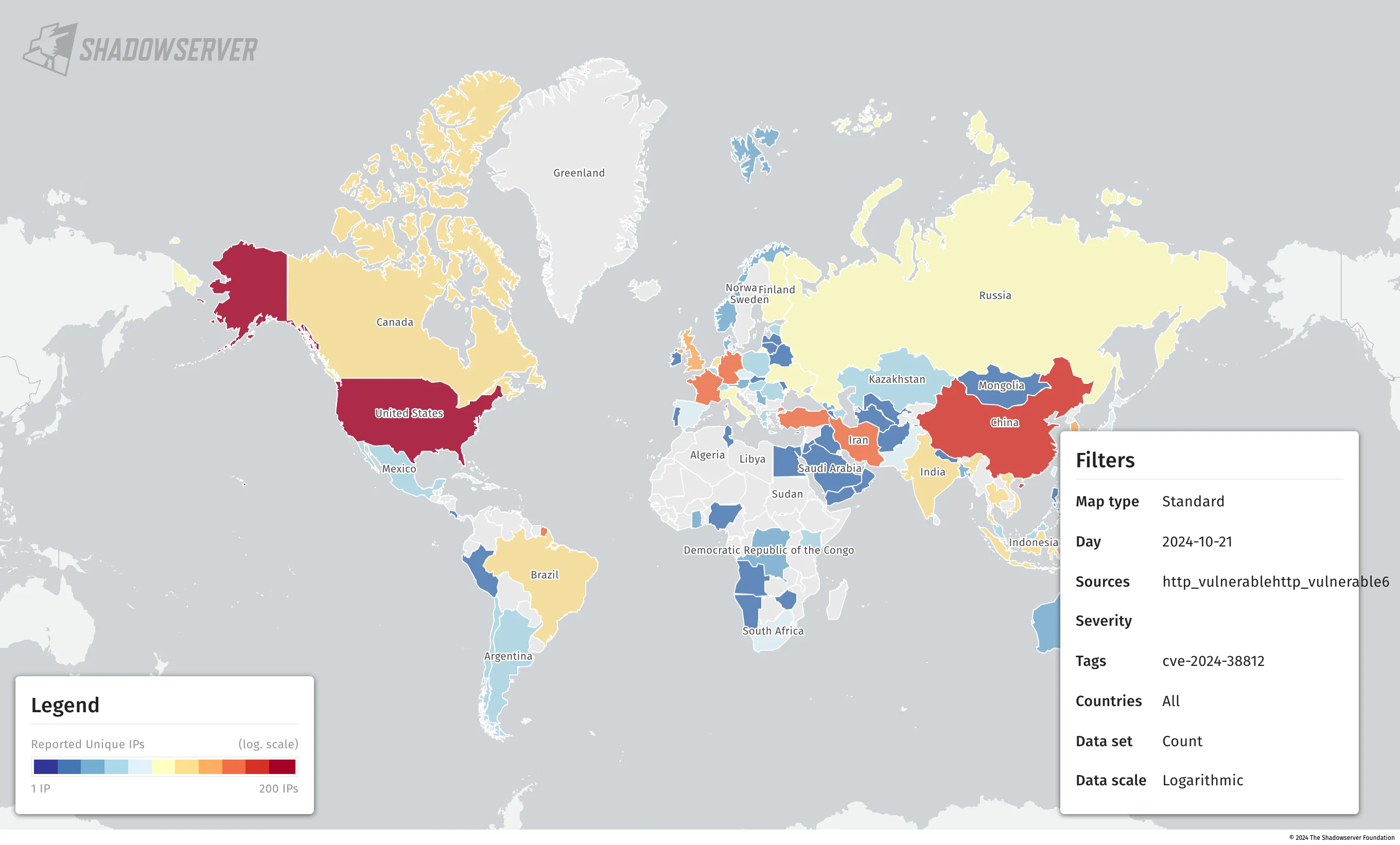
Instances potentially vulnerable to CVE-2024-38812, based on Shadowserver data as of October 21, 2024
VMware vCenter Server Vulnerabilities (CVE-2024-38812 and CVE-2024-38813) Actively Exploited in the Wild
Broadcom has confirmed active exploitation of the two critical VMware vCenter Server vulnerabilities, CVE-2024-38812 and CVE-2024-38813.
The company initially released patches in September but later updated its advisory, warning that the first fix for CVE-2024-38812 was incomplete. Now, Broadcom strongly recommends administrators apply the latest updates immediately, as no workarounds are available, and attackers are actively exploiting these flaws.
For further support, Broadcom has published another advisory, “VMSA-2024-0019: Questions & Answers”, offering detailed guidance on deploying the patches and addressing known issues. You can access it here.
Organizations relying on VMware’s vCenter Server platform should act urgently to secure their infrastructure.
Conclusion
The vulnerabilities in VMware’s vCenter Server, particularly CVE-2024-38812, underscore the importance of proactive cybersecurity measures. Even though no exploitation has been detected yet, organizations must act swiftly to patch affected systems, ensuring that their virtual infrastructures remain secure.

































