
November 2024 Android Security Update Fixes Actively Exploited Vulnerabilities CVE-2024-43093, CVE-2024-43047
[Updated] November 8, 2024: “CISA Adds Android Vulnerability CVE-2024-43093 to KEV Catalog”
Google recently rolled out the November 2024 Android security update, resolving 40 security vulnerabilities. Among these, two zero-day flaws (CVE-2024-43093 and CVE-2024-43047) stand out due to active exploitation in the wild, sparking concerns about potential targeted attacks.
These vulnerabilities impact key parts of the Android system, including the framework and Qualcomm chipsets, making timely patching important for users to defend their devices against compromise.
Active Privilege Escalation Threat in Android Framework (CVE-2024-43093)
The first vulnerability under active exploitation in Google’s November 2024 Android update, CVE-2024-43093, is a privilege escalation flaw within the Android Framework.
This security flaw allows unauthorized access to sensitive directories, such as “Android/data,”“Android/obb,” and “Android/sandbox,” along with their respective subdirectories. By leveraging this vulnerability, attackers can gain elevated privileges, potentially enabling them to perform unauthorized actions or access sensitive data.
Affecting Android versions 12, 13, 14, and 15, this flaw impacts a wide range of devices across the Android ecosystem. Although specific methods of real-world exploitation are not disclosed, Google has confirmed evidence of limited, targeted exploitation. This highlights the critical need for device owners to apply the latest security update to protect against potential attacks.
CISA Adds Android Vulnerability CVE-2024-43093 to KEV Catalog
CISA has issued an alert announcing the addition of CVE-2024-43093 Android Framework Privilege Escalation Vulnerability to its Known Exploited Vulnerabilities (KEV) Catalog. This vulnerability could enable unauthorized privilege escalation, allowing attackers to access sensitive Android directories without user consent. Federal agencies must apply the necessary patch by November 28, 2024 to prevent exploits and remain compliant.
High-Severity Zero-Day Vulnerability in Qualcomm DSP Service (CVE-2024-43047)
CVE-2024-43047 (CVSS 7.8) is a serious Use-After-Free vulnerability impacting Qualcomm’s Digital Signal Processor (DSP) service. This flaw, if exploited, could lead to memory corruption, allowing attackers to escalate privileges and compromise affected devices.
Given the extensive use of Qualcomm chipsets across Android devices, the vulnerability poses a significant security risk for a broad range of devices.
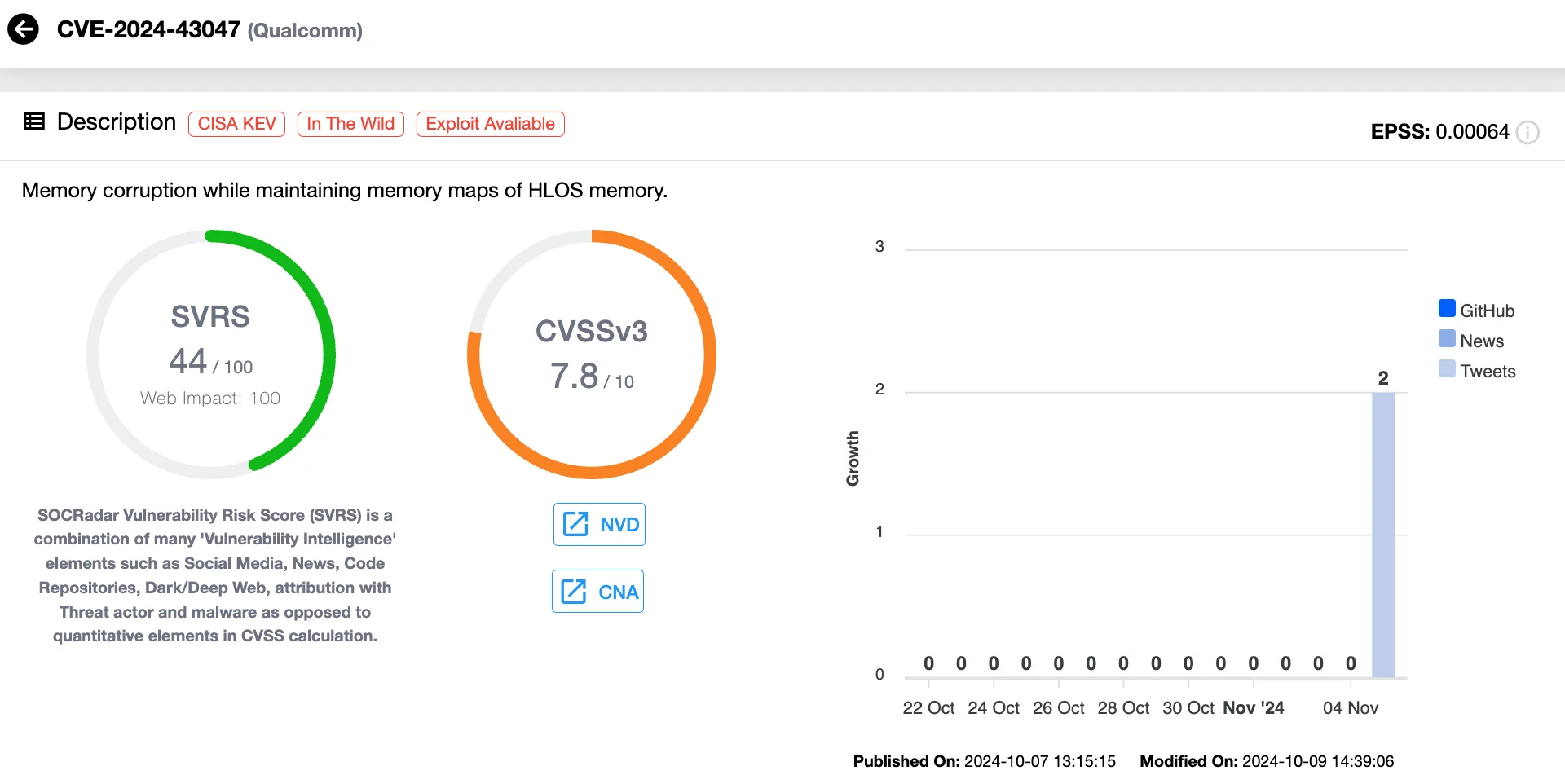
Vulnerability card of CVE-2024-43047 (SOCRadar Vulnerability Intelligence)
This vulnerability was initially reported by researchers from Google Project Zero, and its active exploitation was documented by Amnesty International’s Security Lab. While Qualcomm released a patch for this flaw in October, Google’s inclusion of CVE-2024-43047 in the November security update ensures that it reaches a wide range of Android devices, helping users protect their devices with this critical fix.
Google’s advisory also highlights possible targeted exploitation of CVE-2024-43047, though details of the activity are currently not reported.
We covered CVE-2024-43047 and additional vulnerabilities addressed in Qualcomm’s October 2024 Security Bulletin in a previous blog post, which you can read here.
Stay Protected with SOCRadar’s Real-Time Vulnerability Intelligence
To protect against security threats like CVE-2024-43093 and CVE-2024-43047, staying informed about new vulnerabilities and active exploits is essential. As Android devices increasingly serve as key tools for business and personal use, addressing flaws quickly can prevent significant security incidents. While Google’s regular updates help mitigate risks, organizations benefit from an added layer of proactive threat intelligence to keep pace with evolving threats.
SOCRadar’s Vulnerability Intelligence, offered under the Cyber Threat Intelligence module, is designed to support this need by offering real-time monitoring of high-risk vulnerabilities, including those with active exploitation trends.
SOCRadar’s Vulnerability Intelligence
With timely alerts, comprehensive vulnerability details, and actionable insights, this tool enables your organization to prioritize critical patches and reinforce its security posture, safeguarding your assets before vulnerabilities are widely exploited.
Secure Your Device with November 2024 Android Security Updates
The November 2024 Android security update is divided into two patch levels to address a broad spectrum of vulnerabilities.
The November 1 patch level targets core Android components, including the framework and system, ensuring foundational protections. The November 5 patch level specifically addresses vulnerabilities in hardware components provided by vendors like Qualcomm, MediaTek, and Imagination Technologies, among others.
Given the active exploitation of critical vulnerabilities like CVE-2024-43093 and CVE-2024-43047, it’s critical for users to install this update promptly. Delaying patches leaves devices exposed to security risks, especially as threat actors are already exploiting these flaws in targeted attacks.
For additional details on these updates and further advisories, refer to the Android Security Bulletin for November 2024.




































