
Critical Vulnerabilities in Cisco URWB and HPE Aruba Access Points (CVE-2024-20418, CVE-2024-42509)
In recent security updates, Cisco has addressed a maximum severity vulnerability affecting Unified Industrial Wireless Software for Cisco URWB (Ultra-Reliable Wireless Backhaul) access points—network devices widely used in industrial environments to support wireless connectivity for automation.
Tracked as CVE-2024-20418, this vulnerability is a command injection flaw in Cisco’s Unified Industrial Wireless Software, allowing remote, unauthenticated attackers to execute commands with root privileges.
Alongside Cisco’s vulnerability, HPE Aruba Networking has also released patches for multiple severe vulnerabilities in its access points, which could enable unauthorized access, Remote Code Execution (RCE), and further network compromise.
What is CVE-2024-20418 in Cisco URWB?
CVE-2024-20418 (CVSS 10.0) is a critical command injection vulnerability discovered in Cisco’s Unified Industrial Wireless Software, which manages Ultra-Reliable Wireless Backhaul (URWB) access points. This flaw resides within the web-based management interface, creating a direct avenue for unauthenticated, remote attackers to execute commands with root privileges on affected devices.
The vulnerability’s maximum severity score underscores the serious impact it could have on industrial wireless networks if exploited.
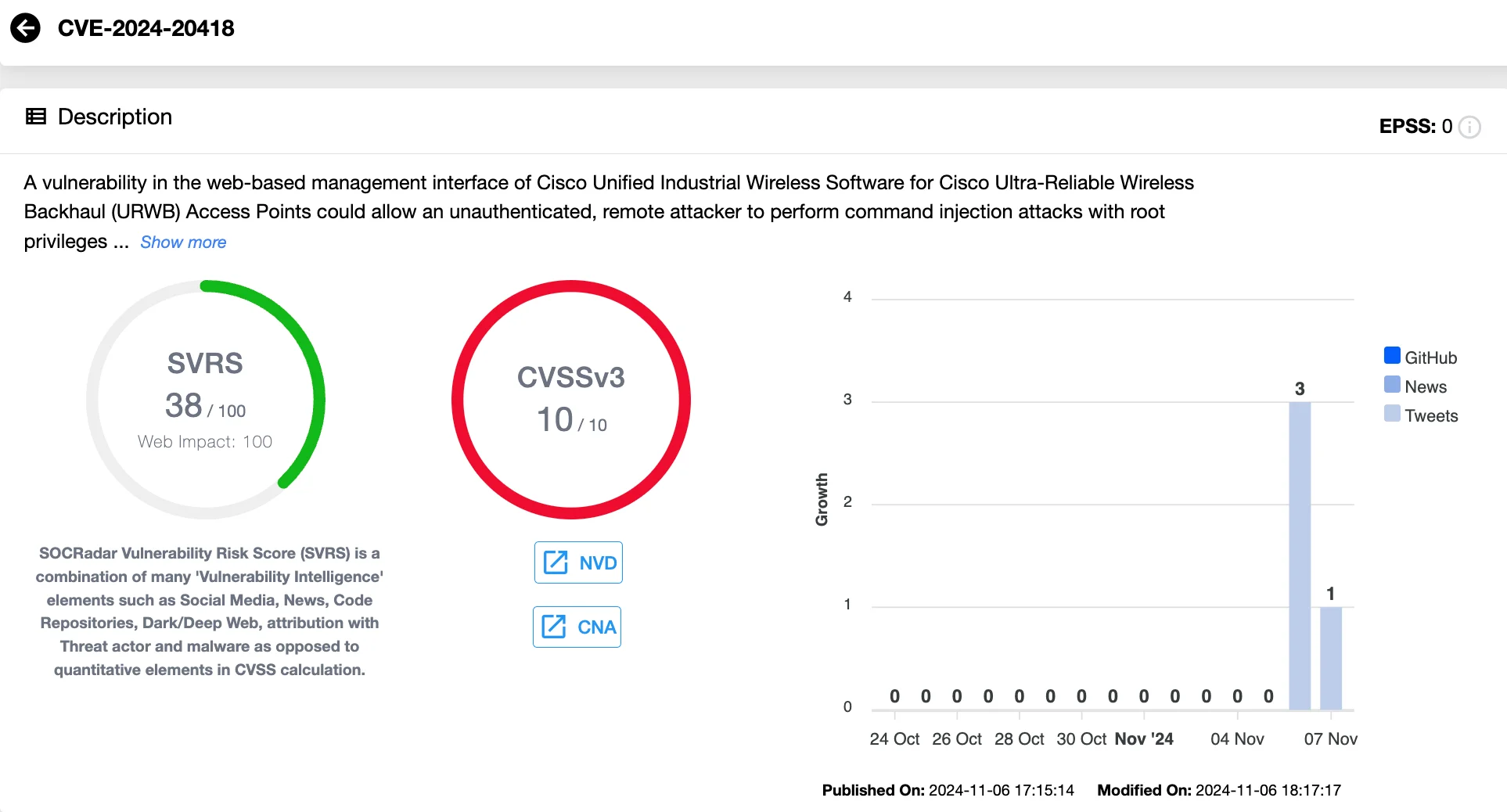
Command injection in Cisco URWB, CVE-2024-20418 (SOCRadar’s Vulnerability Intelligence)
Due to improper validation of inputs, this flaw allows attackers to inject and execute arbitrary commands on the underlying operating system by sending specially crafted HTTP requests to the device. The vulnerability places organizations at risk of unauthorized command execution, data breaches, and even persistent Denial-of-Service (DoS) on essential services.
The ability for attackers to gain root-level access through this flaw could also lead to configuration changes and installation of malicious software.
Which Cisco Product and Versions Are Affected by CVE-2024-20418?
CVE-2024-20418 affects the following Cisco Catalyst access points:
- Catalyst IW9165D Heavy Duty Access Points
- Catalyst IW9165E Rugged Access Points and Wireless Clients
- Catalyst IW9167E Heavy Duty Access Points
Only devices running a vulnerable software version with the URWB operating mode enabled are at risk. To check if URWB mode is active, administrators can use the following command in the CLI:
- show mpls-config
If the command is available, it indicates that URWB mode is enabled, and the device may be vulnerable. Devices without URWB mode enabled are not exposed to this vulnerability.
Staying on top of newly discovered vulnerabilities is vital, especially with the pace of today’s threats. When a critical vulnerability surfaces, it can take only hours for attackers to begin exploiting it. Are you confident your organization can respond in time?
Track CVE trends and search vulnerability information via SOCRadar’s Vulnerability Intelligence
SOCRadar’s Vulnerability Intelligence provides real-time, tailored alerts and in-depth analysis of high-risk vulnerabilities, giving you immediate insight into emerging threats that may impact your digital assets. It delivers actionable intelligence, so you’re always prepared to respond swiftly.
Mitigation and Patch Guidance
Cisco advises users of affected URWB access points to upgrade to a fixed software release as soon as possible to mitigate CVE-2024-20418. Due to the critical nature of this command injection vulnerability, Cisco underscores that prompt patching is essential, as there are no available workarounds.
Furthermore, according to Cisco’s Product Security Incident Response Team (PSIRT), there is currently no evidence that this vulnerability is being actively exploited in the wild.
For further details on the fixed releases and instructions, refer to Cisco’s security advisory.
Multiple Critical Vulnerabilities in Aruba Access Points
In addition to the critical flaw in Cisco’s URWB access points, recent updates from HPE Aruba Networking have also tackled multiple severe vulnerabilities affecting their access points. With CVSS scores reaching as high as 9.8, these security flaws pose significant risks, including Remote Code Execution (RCE), unauthorized access, and the potential for full system compromise on affected devices.
The vulnerabilities impact various models running Aruba’s Instant AOS-8 and AOS-10 firmware:
- AOS-10.4.x.x: 10.4.1.4 and prior
- Instant AOS-8.12.x.x: 8.12.0.2 and prior
- Instant AOS-8.10.x.x: 8.10.0.13 and prior
For enterprises utilizing Aruba’s wireless infrastructure, timely patching is essential to protect against unauthorized access and ensure the integrity of their network environments.
Unauthenticated Command Injection in Aruba Access Points (CVE-2024-42509)
Among the vulnerabilities in HPE Aruba’s access points, the most severe is an unauthenticated command injection flaw tracked as CVE-2024-42509 (CVSS 9.8). This vulnerability allows attackers to exploit the PAPI protocol’s UDP port (8211), which is commonly used by Aruba’s management services, to remotely execute privileged code on impacted devices.
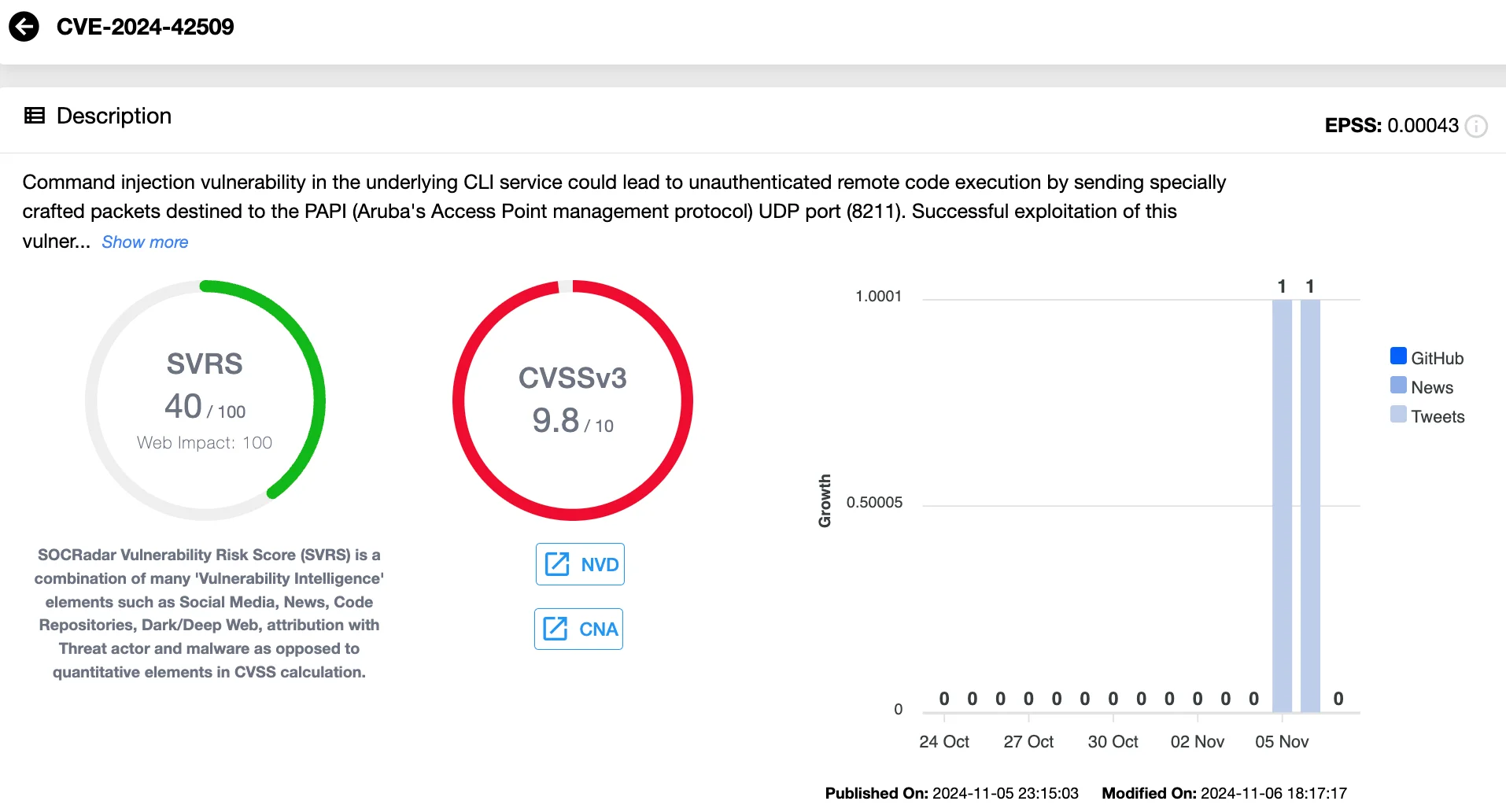
Command injection in Aruba, CVE-2024-42509 (SOCRadar Vulnerability Intelligence)
Additionally, HPE Aruba addressed CVE-2024-47460 (CVSS 9.0), another command injection vulnerability that could enable attackers to execute arbitrary code by sending specially crafted packets to the PAPI protocol.
The company also mitigated three authenticated Remote Code Execution (RCE) issues—CVE-2024-47461, CVE-2024-47462, and CVE-2024-47463—which allow attackers with CLI access to run privileged commands or create specific files for RCE.
Lastly, a medium-severity vulnerability, CVE-2024-47464, permits attackers to access files on affected systems via path traversal. While not as critical, it could expose sensitive information if exploited, highlighting the need for prompt remediation.
HPE Aruba Patch Recommendations
For users of HPE Aruba’s access points, the company strongly recommends applying the latest patches to mitigate the vulnerabilities affecting AOS-10 and AOS-8 versions. Aruba’s guidance advises all impacted devices to update to a secure release.
For environments where immediate patching isn’t feasible, Aruba suggests implementing network segmentation or applying firewall restrictions to control access to management interfaces. Limiting access to these interfaces adds a layer of security, reducing exposure to external threats while awaiting patches. Aruba’s advisory also emphasizes that restricting management interface access to a dedicated VLAN or setting firewall policies at Layer 3 and above can further mitigate risk, especially in critical network infrastructures.
Visit the official advisory on HPE’s Support Center for more information.
Your organization’s digital footprint expands daily, increasing your attack surface and exposing potential entry points for attackers. Are you aware of every asset that could be a gateway to risk? To help you address any vulnerabilities that arise, SOCRadar’s Attack Surface Management (ASM) continuously monitors your external digital footprint, identifying exposed assets and potential security gaps.
Monitor your Company Vulnerabilities easily with SOCRadar’s ASM module
By using SOCRadar’s ASM, you gain 24/7 monitoring and visibility, automated alerts, and insights into the state of your assets—empowering your team to proactively secure and manage your attack surface.




































