
Critical QNAP Vulnerabilities in Notes Station 3 and QuRouter Demand Immediate Patching (CVE-2024-38645, CVE-2024-38643, CVE-2024-48860)
QNAP recently released multiple security advisories addressing a range of vulnerabilities, including three critical flaws with CVSS scores above 9.0. These vulnerabilities could enable unauthorized access, remote command execution, and exposure of sensitive data if left unpatched. The critical flaws impact widely-used products such as Notes Station 3 and QuRouter, placing systems at significant risk of compromise.
Given the potential for attackers to exploit these vulnerabilities for data theft, malware deployment, or disrupting critical operations, QNAP users are strongly urged to apply the available patches immediately.
QNAP Notes Station 3 Affected by Critical Missing Auth and SSRF Vulnerabilities (CVE-2024-38645 & CVE-2024-38643)
Notes Station 3, an essential app that provides collaborative editing and note-taking features for QNAP NAS systems, has been discovered to be vulnerable to a number of high-severity flaws, including two critical vulnerabilities. These flaws pose significant risks, potentially allowing unauthorized access to sensitive data or the execution of harmful commands.
Key Critical Vulnerabilities
- CVE-2024-38645 (CVSS 9.4): A Server-Side Request Forgery (SSRF) vulnerability that enables remote attackers to manipulate server behavior by sending crafted requests, exposing sensitive application data.
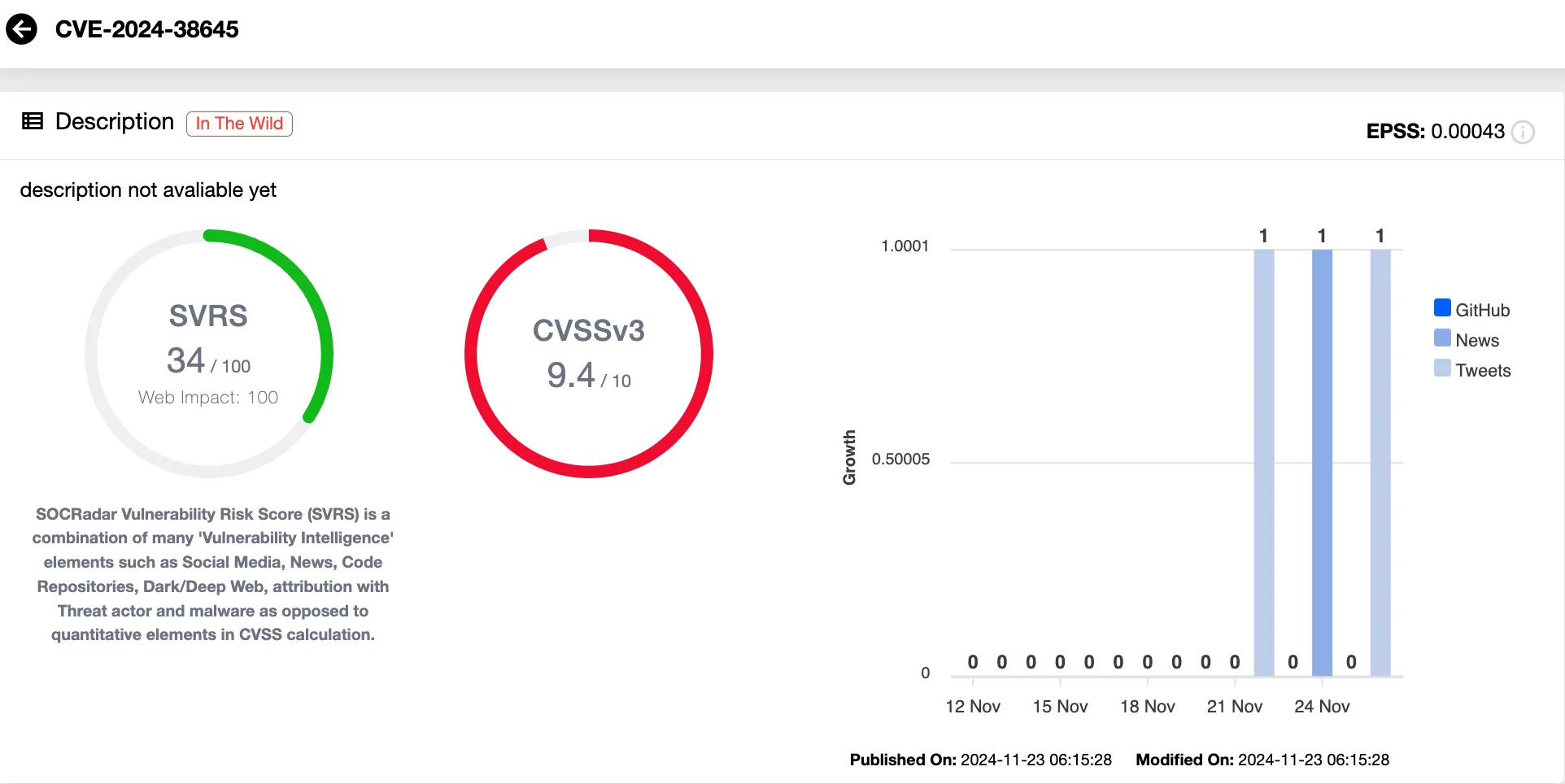
Vulnerability card of CVE-2024-38645 (SOCRadar Vulnerability Intelligence)
- CVE-2024-38643 (CVSS 9.3): A missing authentication flaw for critical functions, allowing remote attackers to access the system without any credentials.
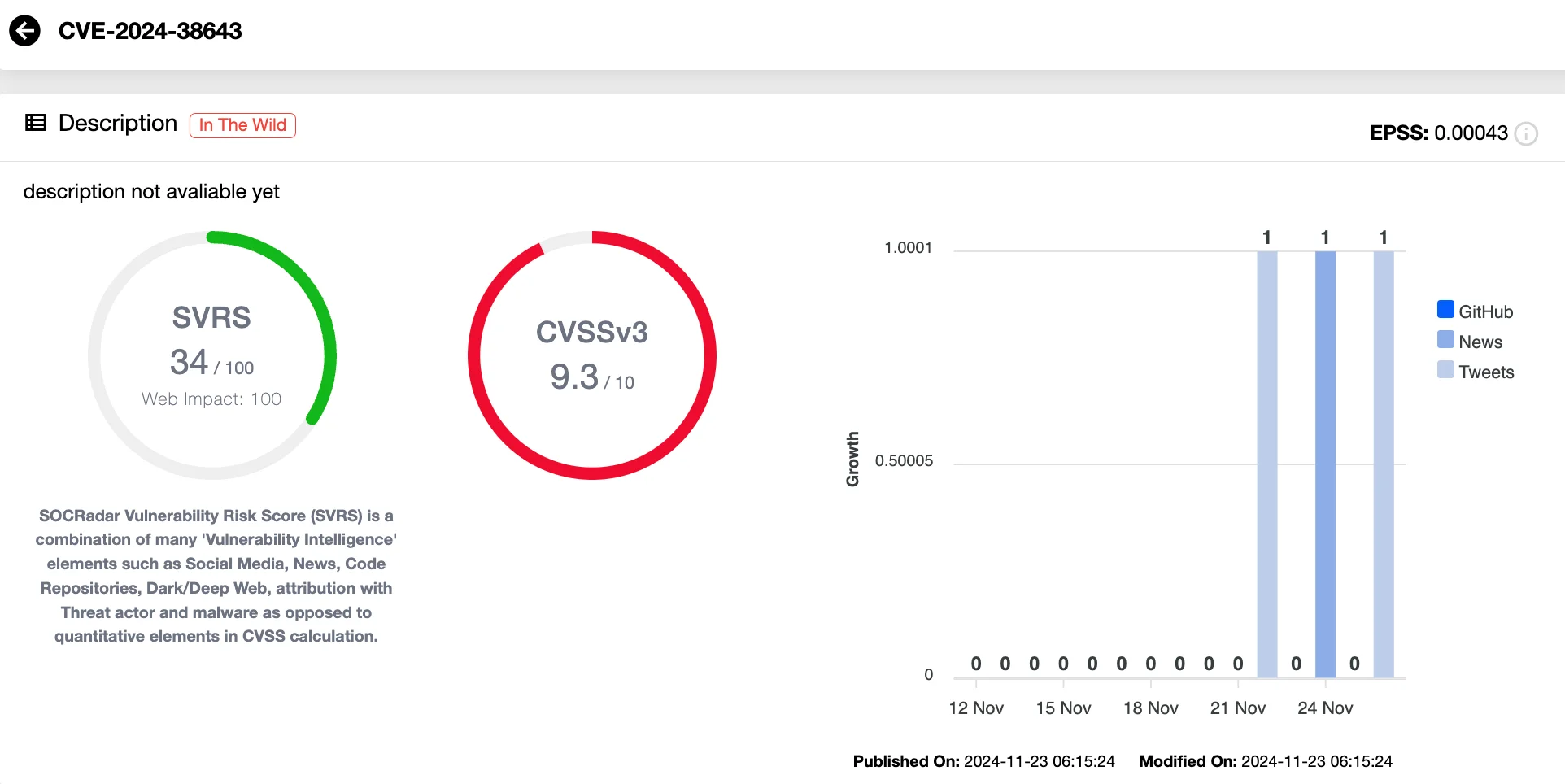
Vulnerability card of CVE-2024-38643 (SOCRadar Vulnerability Intelligence)
QNAP also resolved two additional high-severity vulnerabilities in the same advisory: CVE-2024-38644 and CVE-2024-38646. CVE-2024-38644 (CVSS 8.7) is a command injection flaw that can be exploited by attackers with user-level access, while CVE-2024-38646 (CVSS 8.4) arises from incorrect permission assignments, potentially allowing local attackers with administrative privileges to access sensitive data without proper authorization.
These vulnerabilities affect Notes Station 3 version 3.9.x.
Severe Flaw in QuRouter Devices Could Allow Remote Command Execution (CVE-2024-48860)
QuRouter, QNAP’s advanced router solution, simplifies the management of high-speed LAN and WAN networks, ensuring secure and efficient connectivity. However, recent findings have revealed critical vulnerabilities within QuRouter devices.
- CVE-2024-48860 (CVSS 9.5): As an OS command injection flaw, CVE-2024-48860 could allow remote attackers to execute arbitrary commands on the host system. This can lead to unauthorized control over the device, posing significant risks to network security.
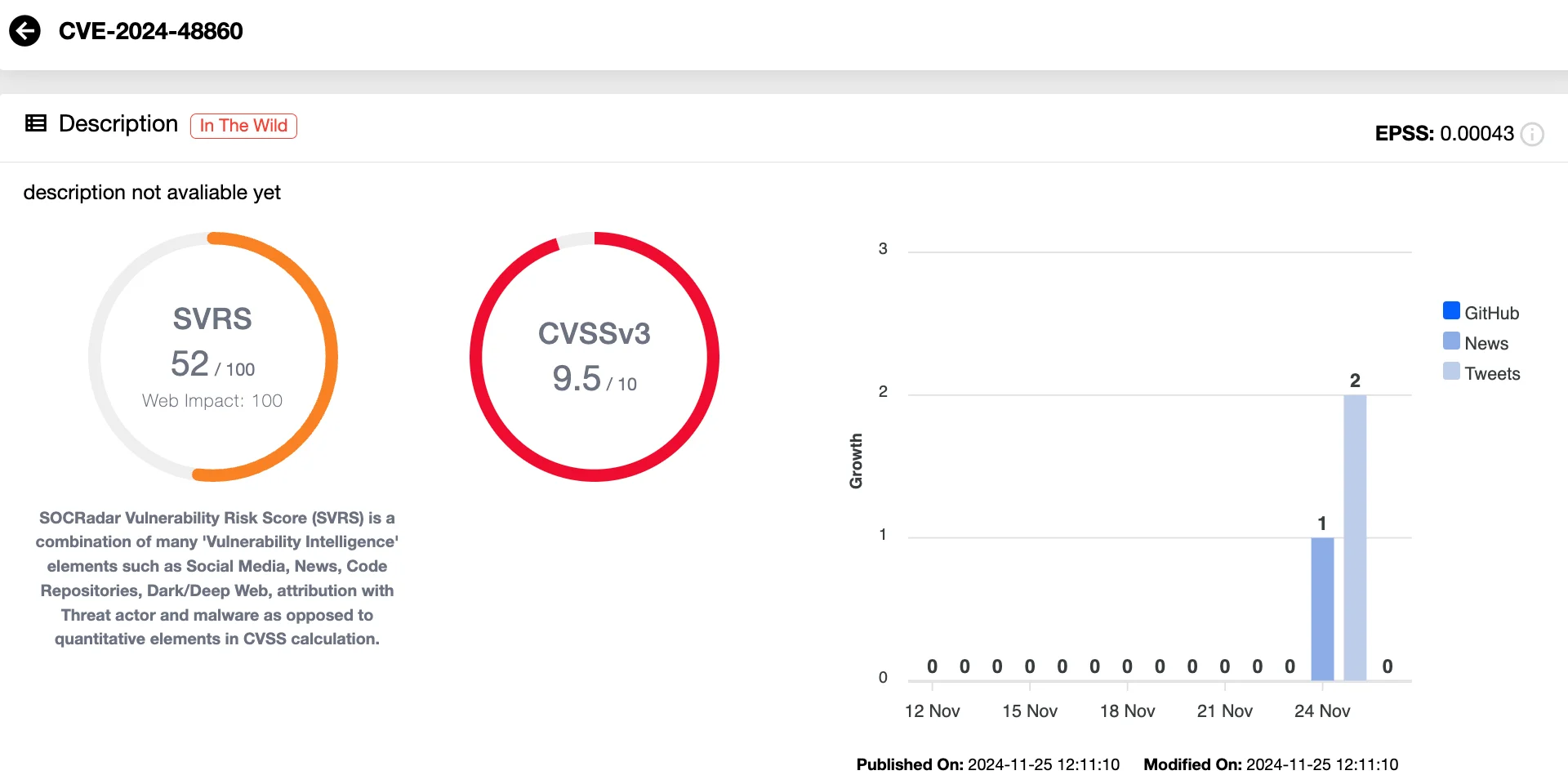
Vulnerability card of CVE-2024-48860 (SOCRadar Vulnerability Intelligence)
In addition to CVE-2024-48860, QuRouter addresses a less severe command injection vulnerability (CVE-2024-48861, CVSS 7.3). It remains a high risk and requires immediate patching to avoid potential misuse.
These two vulnerabilities affect QuRouter versions under 2.4.x.
QNAP’s QuLog Center, AI Core, QTS, and QuTS Hero Also Receive Important Fixes
In addition to the critical vulnerabilities, QNAP addressed several high-severity flaws in other key products, which pose risks such as information leaks, file system access, and memory manipulation:
- CVE-2024-48862 (CVSS 8.7): A link following flaw in QuLog Center could enable unauthorized file access or modifications.
- CVE-2024-38647 (CVSS 7.9): An information exposure issue in QNAP AI Core could allow attackers to access sensitive data.
- CVE-2024-50396 and CVE-2024-50397 (CVSS 7.7): Format string handling vulnerabilities in QTS and QuTS Hero could lead to memory corruption and data access.
How to Address the Latest QNAP Vulnerabilities
Here’s what you should do to mitigate the risks posed by QNAP’s recently disclosed vulnerabilities:
- Update Your Devices: Ensure your QNAP products are running the latest firmware. Fixed versions for each affected product are detailed in the next section, along with links to official advisories for guidance.
- Secure Your Network: Avoid connecting QNAP devices directly to the internet. Instead, use secure configurations to limit exposure.
- Enable VPN Access: Protect your devices by routing remote access through a VPN, reducing the likelihood of exploitation by threat actors.
To stay ahead of security vulnerabilities, SOCRadar’s Vulnerability Intelligence module delivers you real-time updates on newly disclosed CVEs, providing actionable insights into their potential impact. With SOCRadar, you can easily prioritize patching and monitor evolving exploit trends, ensuring your defenses are always a step ahead.
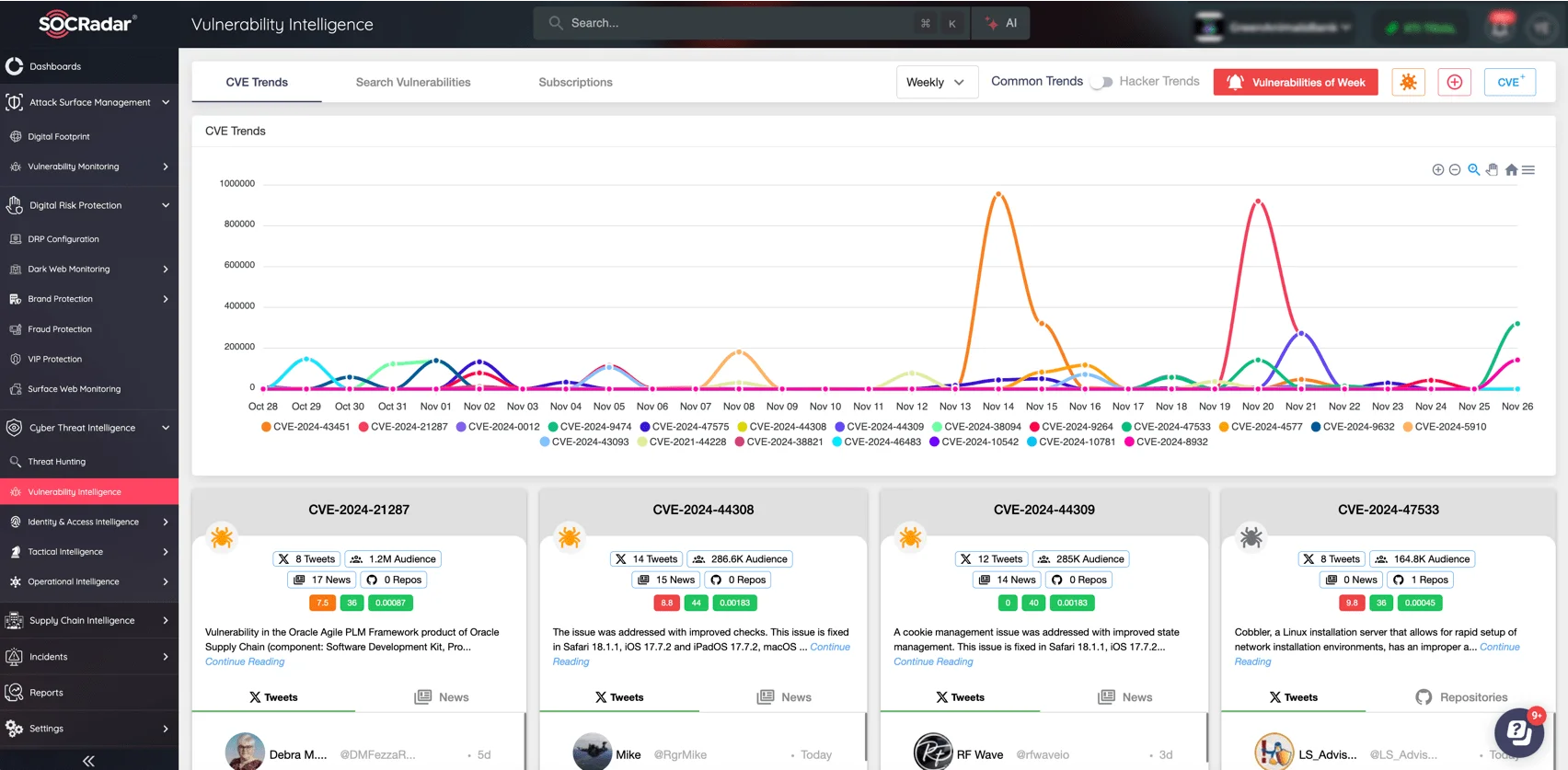
SOCRadar Vulnerability Intelligence: hacker trends and newest CVEs
In addition, SOCRadar’s Attack Surface Management (ASM) helps you identify and manage exposed assets across your network. By mapping your attack surface and highlighting vulnerabilities, ASM ensures you stay informed about potential entry points attackers might exploit, giving you the tools to secure them effectively.
Monitor your digital assets and company vulnerabilities with SOCRadar ASM module
Fixed QNAP Product Versions to Patch Now
To protect against the vulnerabilities discussed, QNAP users are strongly urged to apply the following updates immediately. Below is a reference table for affected products and fixed versions:
| Product | Fixed Versions |
| Notes Station 3 | 3.9.7 and later |
| QuRouter | 2.4.3.106 and later |
| QuLog Center | 1.7.0.831 and 1.8.0.888 |
| QNAP AI Core | 3.4.1 and later |
| QTS | 5.2.1.2930 and later |
| QuTS hero | h5.2.1.2929 and later |
Ensuring your systems are updated to these fixed versions will mitigate the risks associated with the identified vulnerabilities.
For further technical details, you can refer to QNAP’s official advisories for flaws in Notes Station 3, QuRouter, QuLog Center, QNAP AI Core, and QTS and QuTS Hero.




































