
DarkVision RAT: A Persistent Threat Delivered via PureCrypter
The DarkVision RAT malware campaign leverages the PureCrypter loader to infiltrate networks and compromise data across multiple sectors. Distributed through various phishing techniques and utilizing advanced obfuscation, DarkVision RAT exemplifies a highly effective attack strategy.

DarkVision RAT, illustrated by DALL-E
The trojan offers remote access capabilities, keylogging, screen and audio capture, and even allows attackers to manipulate system processes and registry entries for persistence. Organizations worldwide, especially those in critical sectors like finance, healthcare, and government, are vulnerable to this potent malware.
Campaign Overview and Attack Techniques
DarkVision RAT, deployed via PureCrypter, begins its infection chain with the decryption and execution of malware through the loader.
This RAT (Remote Access Trojan) is known for using various techniques to evade detection, including API calls, process injections, and disguising itself as legitimate tasks. Its Command and Control (C2) communications occur over non-standard ports, ensuring that standard firewall policies may not detect its presence.
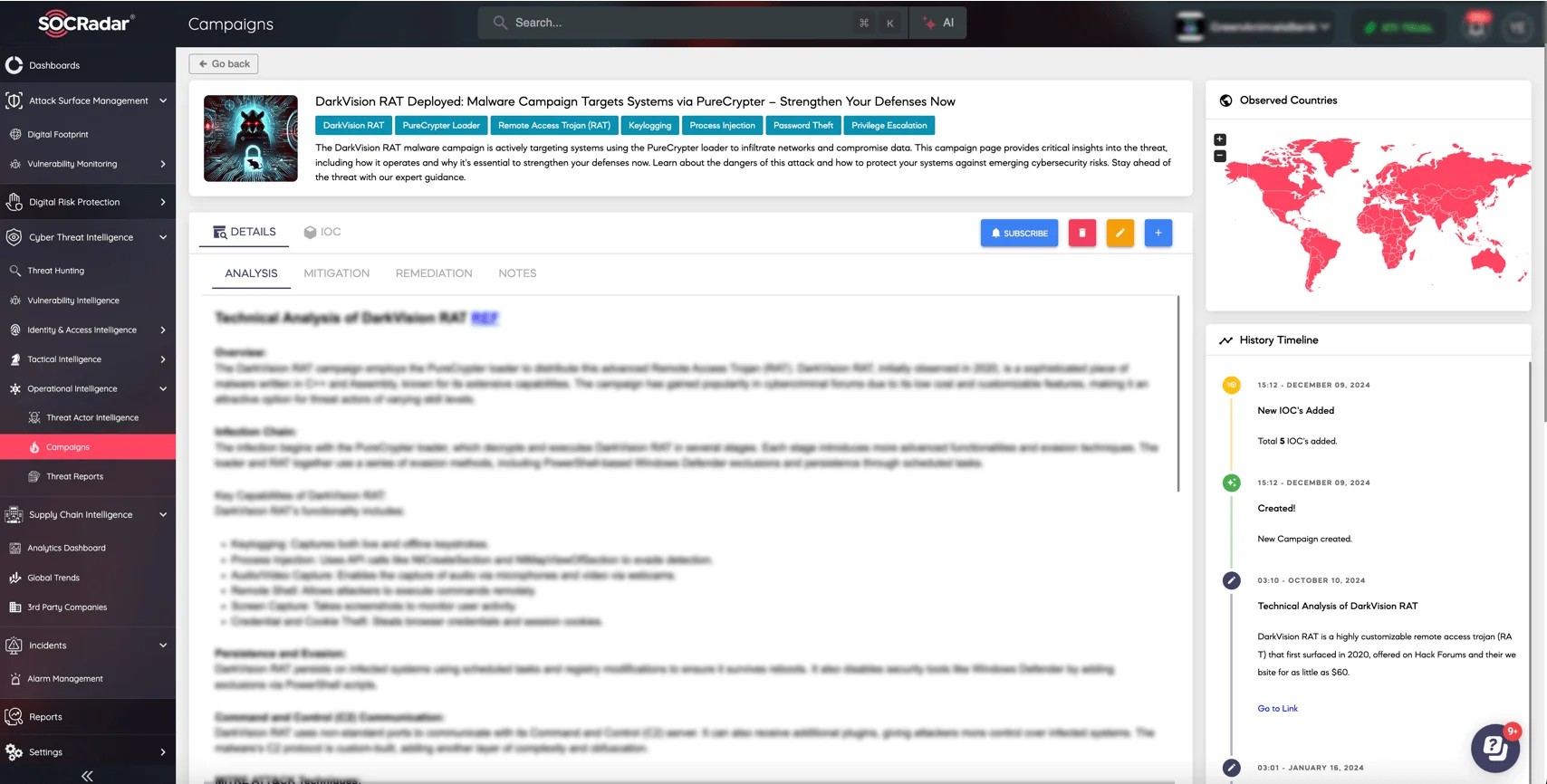
The campaign page for DarkVision RAT on SOCRadar XTI platform
Explore the Campaigns section in SOCRadar LABS for insights into DarkVision RAT and similar threats. Learn how SOCRadar’s XTI platform can enhance your proactive security efforts.
Mitigation Measures
To protect against DarkVision RAT, organizations should adopt strict security protocols, strengthen endpoint defenses, and maintain constant vigilance to detect unauthorized tasks and registry changes. Below are recommended mitigation strategies to prevent the RAT from establishing a foothold:
| ID | Technique | Recommended Mitigation |
| T1053.005 | Scheduled Task | Limit task creation to authorized users and use Group Policies to restrict task scheduling. |
| T1547.001 | Registry Run Keys / Startup Folder | Monitor registry keys and startup folder changes with endpoint detection tools, restricting registry modifications. |
| T1055 | Process Injection | Deploy behavior-based detection tools to monitor NtCreateSection and NtMapViewOfSection API calls, and use application whitelisting. |
| T1140 | Deobfuscate/Decode Files or Information | Use monitoring tools to detect obfuscation attempts, and implement DLP to block encoded data transfers. |
| T1562.001 | Disable or Modify Tools | Protect antivirus settings with tamper protection, auditing Windows Defender exclusions regularly. |
| T1539 | Steal Web Session Cookie | Harden browser settings and enforce Multi-Factor Authentication (MFA) for login sessions, while blocking unauthorized plugins. |
These strategies focus on the most commonly used techniques by DarkVision RAT, and implementing them will significantly reduce the risk of compromise.
Remediation Steps
To effectively remediate systems infected by DarkVision RAT, organizations must take proactive steps to detect and remove it, focusing on system logs, endpoint detection tools, and continuous auditing. Below are the key remediation actions:
| ID | Data Source | Data Component | Detection and Remediation Method |
| DS0017 | Command | Command Execution | Monitor command-line activity for unauthorized PowerShell or script execution that performs system modifications. |
| DS0009 | Process | OS API Execution | Track unusual API usage linked to screen, audio, and keylogging operations. |
| DS0022 | File | File Modification | Analyze suspicious changes in sensitive files, especially in system or startup folders. |
| DS0024 | Windows Registry | Registry Key Creation | Monitor registry keys for suspicious additions or modifications tied to persistence. |
| DS0011 | Module | Module Load | Watch for unauthorized module loads in high-sensitivity processes. |
| DS0029 | Network Traffic | Network Connection Creation | Use network monitoring to detect encrypted, non-standard C2 traffic. |
Indicators of Compromise (IoCs)
The following IoCs are associated with DarkVision RAT and are critical for early detection. Integrate these into threat intelligence systems to bolster defenses against this campaign.
| Category | Indicator | Description |
| Hashes | cd64122c8ee24eaf02e6161d7b74dbe79268f3b7ffb7a8b0691a61ff409f231d | Malicious payload hash linked to DarkVision RAT. |
| 27ccb9f336282e591e44c65841f1b5bc7f495e8561349977680161e76857be5d | Associated with PureCrypter loader components. | |
| 7aa49795bbe025328e0aa5d76e46341a95255e13123306311671678fdeabb617 | Hash indicating C2 and persistence functionalities. | |
| URLs | http://nasyiahgamping[.]com/yknoahdrv.exe | Malicious URL hosting DarkVision RAT payload. |
| IP Addresses | severdops.ddns[.]net:8120 | C2 server used in the campaign with non-standard port. |
Conclusion
The DarkVision RAT campaign underscores the dangers posed by advanced Remote Access Trojans, particularly those distributed via loaders like PureCrypter. With its extensive capabilities – keylogging, process injection, video capture, and more – DarkVision RAT allows threat actors to gain deep control over infected systems. Preventing these attacks demands a multifaceted approach, including endpoint protection, application whitelisting, and real-time monitoring.
To enhance your organization’s defenses, SOCRadar’s Extended Threat Intelligence (XTI) platform provides powerful solutions to detect and respond to campaigns like DarkVision RAT. Protect your systems proactively with SOCRadar and strengthen your overall security posture.


































