
Critical Vulnerabilities in Progress WhatsUp Gold (CVE-2024-12108, CVE-2024-12106); PoC Available for Oracle WebLogic Flaw
Three severe vulnerabilities have recently been uncovered in WhatsUp Gold, a well-known network monitoring solution by Progress Software, raising serious security concerns. These flaws could potentially allow unauthorized access to servers, manipulation of configurations, and leakage of sensitive data.
Given the wide usage of WhatsUp Gold in business-critical environments, these vulnerabilities demand immediate attention from affected organizations. Without prompt action, attackers could exploit these weaknesses to compromise security and access sensitive information.
In addition, a Proof-of-Concept (PoC) exploit was released for a high-severity vulnerability in Oracle WebLogic Server, further adding to the growing list of security risks.
In this blog, we will outline these latest threats, providing details about their potential impact and mitigation strategies.
Details of the Recent WhatsUp Gold Vulnerabilities
The most pressing of the vulnerabilities, CVE-2024-12108, carries a CVSS score of 9.6. This flaw allows attackers to fully control WhatsUp Gold servers via its public API. An attacker exploiting this vulnerability could manipulate the server and gain access to sensitive systems and data.
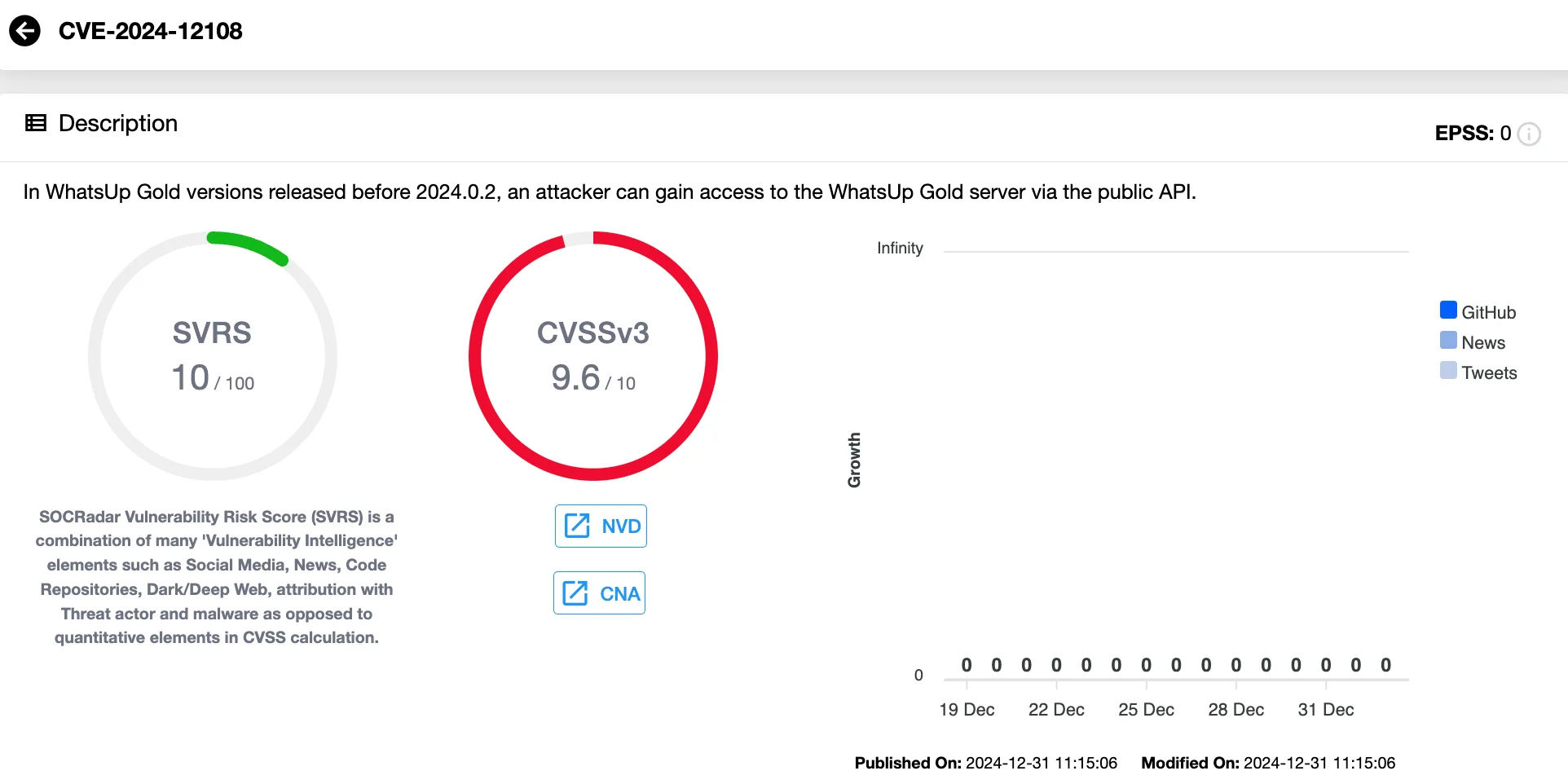
Vulnerability card of CVE-2024-12108 (SOCRadar’s Vulnerability Intelligence)
Next in severity is CVE-2024-12106, with a CVSS score of 9.4. This vulnerability enables unauthenticated attackers to configure the Lightweight Directory Access Protocol (LDAP) settings, potentially granting unauthorized access to servers and leading to data breaches.
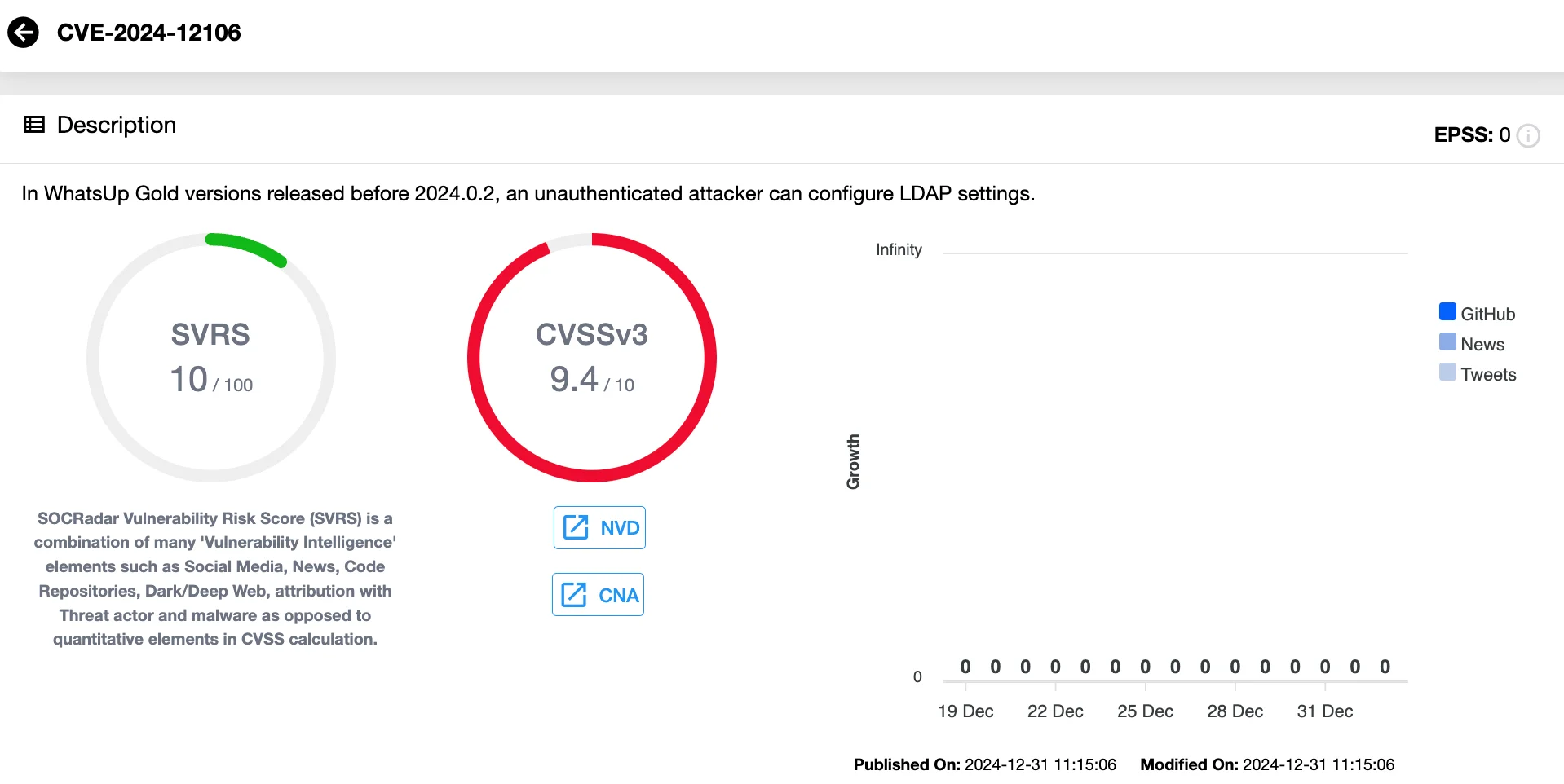
Vulnerability card of CVE-2024-12106 (SOCRadar’s Vulnerability Intelligence)
CVE-2024-12105 (CVSS 6.5), the third vulnerability, is less severe but still poses a threat. It allows authenticated users to extract sensitive information through specially crafted HTTP requests, creating a significant risk of information disclosure.
SOCRadar’s Vulnerability Intelligence
Identify high-risk vulnerabilities in your environment with SOCRadar’s Vulnerability Intelligence module. By providing timely, actionable insights, the module helps you safeguard your network and mitigate risks before they escalate. Here’s what it offers:
- Comprehensive vulnerability data: Continuously updated information on CVEs, including exploits.
- Actionable insights: Tailored recommendations to prioritize fixes.
- Threat actor activity tracking: Stay informed about attack trends.
Affected Versions and Potential Exposure
These recent vulnerabilities affect Progress WhatsUp Gold versions earlier than 24.0.2. Users with these versions are at risk of security breaches, as the vulnerabilities can lead to unauthorized access and potential data leaks.
Results from ZoomEye suggest that nearly 110,000 WhatsUp Gold instances are exposed, thereby at risk of being targeted. Most of these instances are located in the U.S., followed by China. Other countries, including Japan, India, Canada, and Germany, and Australia also show significant exposure.
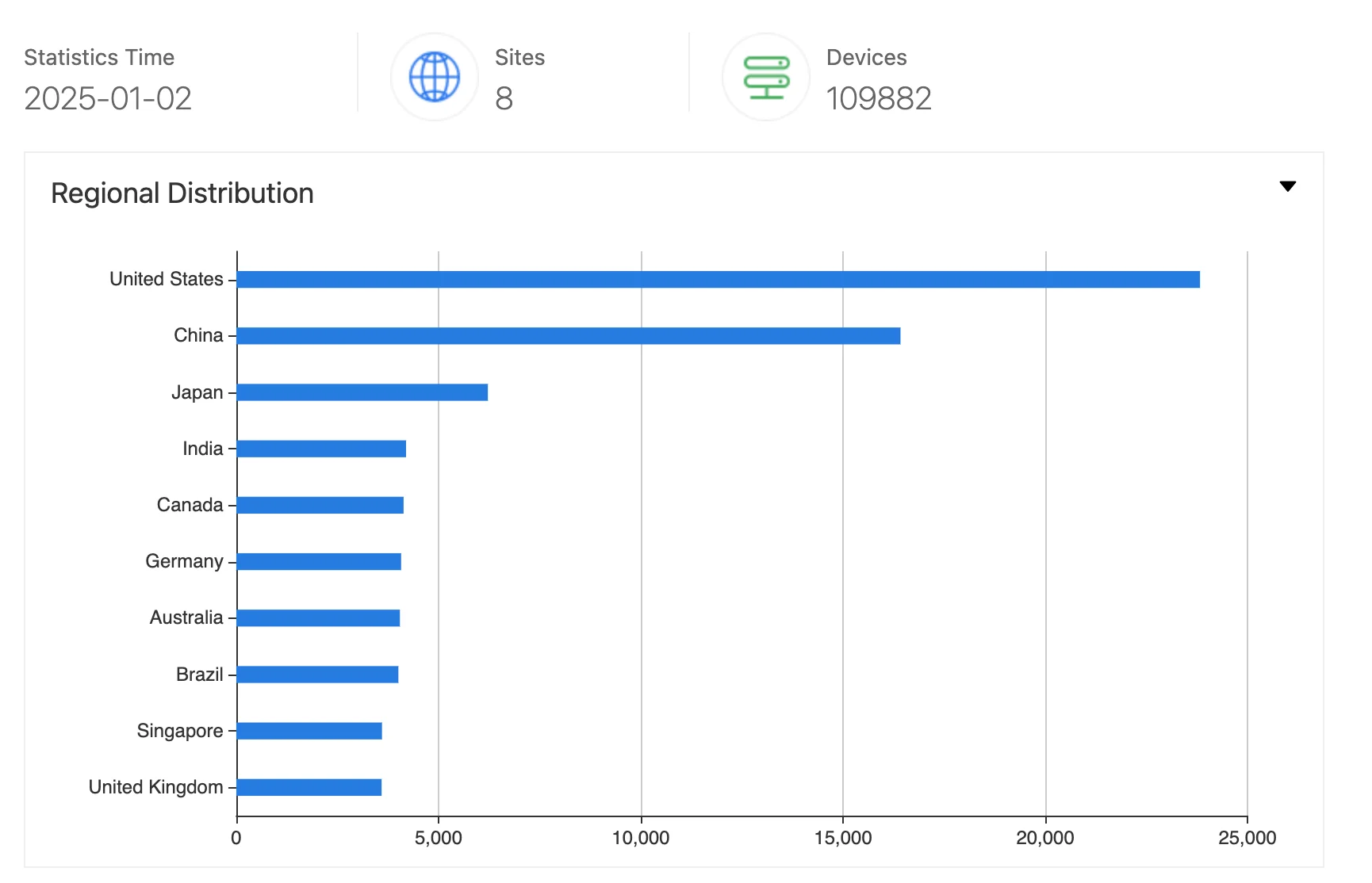
ZoomEye search results for WhatsUp Gold
Security Patch Available
Timely patching is crucial to prevent exploitation and safeguard vulnerable systems. To mitigate the risks posed by these vulnerabilities, upgrade to version 24.0.2 of WhatsUp Gold. This version includes patches for CVE-2024-12108, CVE-2024-12106, and CVE-2024-12105, addressing the security flaws effectively.
Severe Vulnerability in Oracle WebLogic Server (CVE-2024-21182) Receives a PoC Exploit
In other developments in the vulnerability landscape, Proof-of-Concept (PoC) exploits for the high-severity Oracle WebLogic Server vulnerability CVE-2024-21182 (CVSS 7.5) have recently been made available on GitHub.
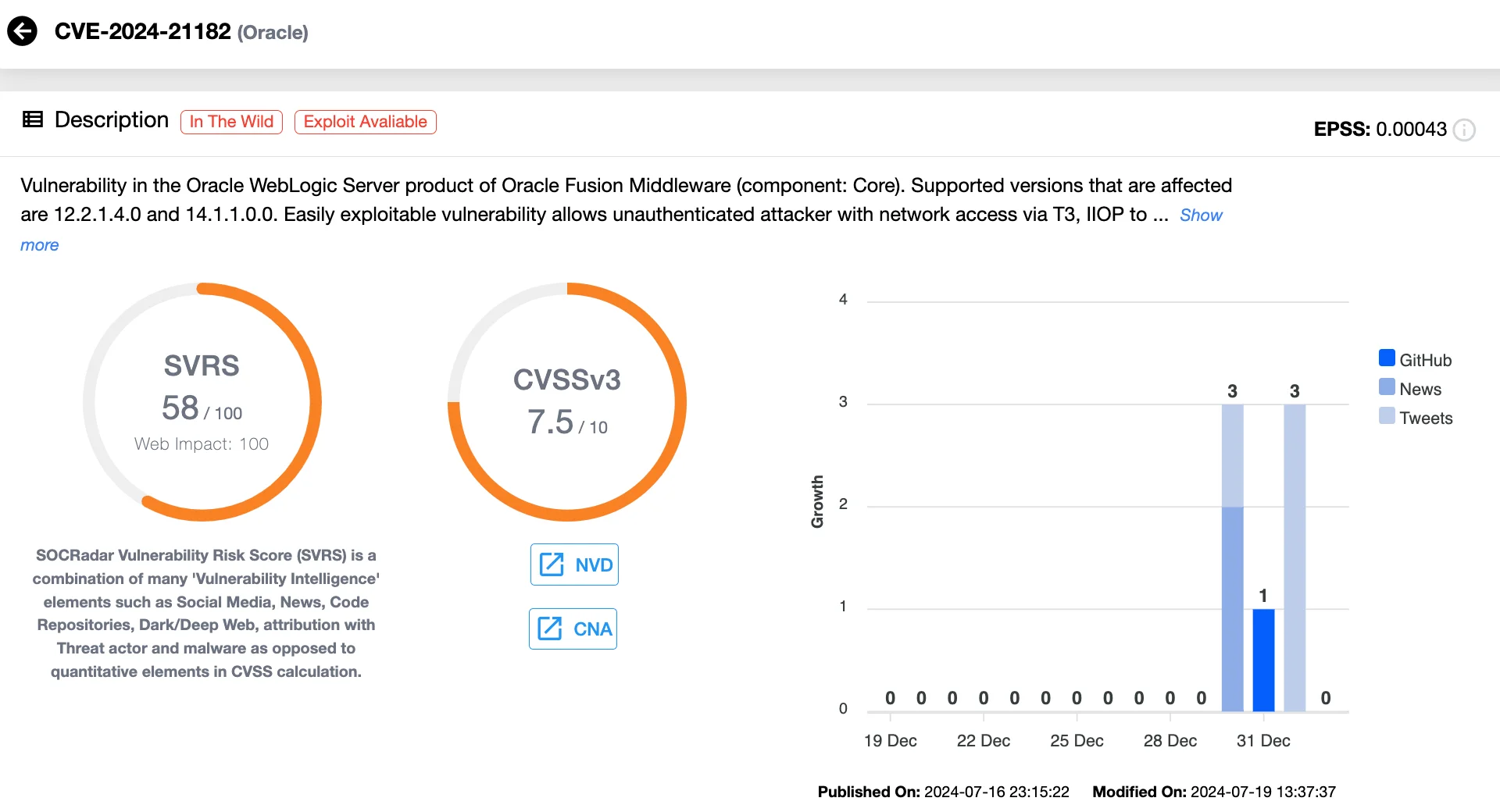
Vulnerability card of CVE-2024-21182 (SOCRadar’s Vulnerability Intelligence)
First disclosed in July 2024, the flaw affects versions 12.2.1.4.0 and 14.1.1.0.0 of WebLogic Server, residing within the Core component. When exploited through T3 or IIOP protocols by unauthenticated attackers, it can lead to unauthorized access to critical data.
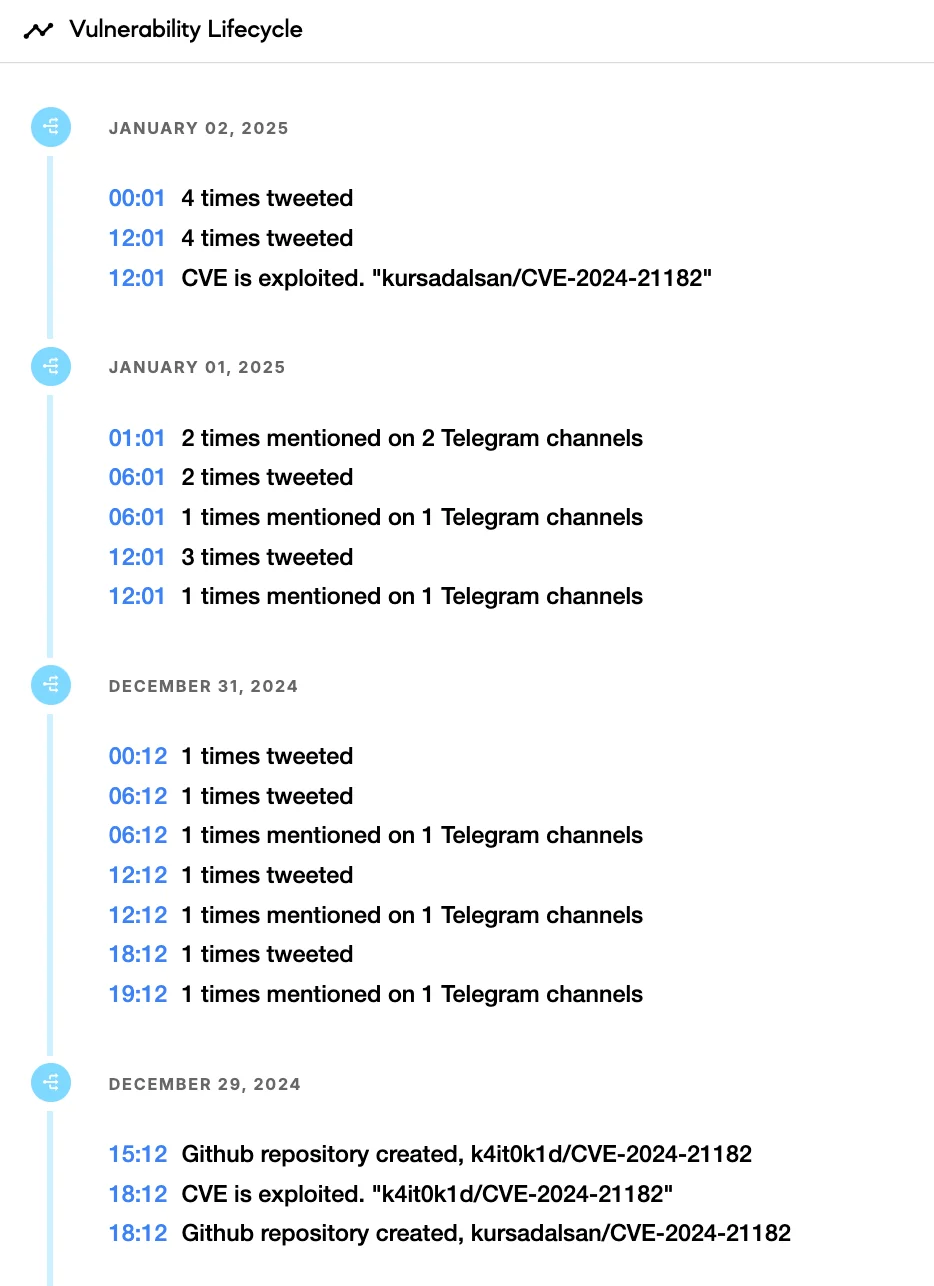
Lifecycle information for CVE-2024-21182 (SOCRadar Vulnerability Intelligence)
With PoCs for CVE-2024-21182 now in the public domain, there is an increased risk of real-world attacks on unpatched systems. Organizations relying on WebLogic for their operations must act swiftly to mitigate the risk.
How to Address CVE-2024-21182?
Oracle has already released patches for CVE-2024-21182 in the July 2024 Critical Patch Update. For those unable to immediately apply the patch, temporary mitigation measures are also available, including restricting T3 protocol access through WebLogic’s default connection filter and disabling the IIOP protocol.
Leverage SOCRadar’s Attack Surface Management (ASM) module to reduce your exposure to cyber attacks and gain full visibility into your attack surface. Secure your organization’s perimeter before vulnerabilities are exploited.
Track Company Vulnerabilities with SOCRadar’s ASM module
Key capabilities of ASM include:
- Continuous discovery of exposed assets across your attack surface.
- Risk-based prioritization of vulnerabilities and threats.
- Actionable intelligence on external threats targeting your organization.
- Real-time monitoring for better threat response.




































