
Critical Vulnerabilities in Fortinet and Ivanti Products: Multiple Zero-Day Threats Addressed
Fortinet and Ivanti have each released critical security advisories addressing multiple high-impact vulnerabilities, several of which have been actively exploited in zero-day attacks. These flaws affect a wide range of enterprise systems, from VoIP and mail platforms to IT service management and endpoint management solutions.
Fortinet: CVE-2025-32756 Zero-Day Exploited in the Wild
Fortinet has issued emergency patches to resolve a severe remote code execution (RCE) vulnerability, CVE-2025-32756, affecting FortiVoice Enterprise phone systems. The flaw is a stack-based buffer overflow that allows unauthenticated remote attackers to execute arbitrary commands via specially crafted HTTP requests.
The vulnerability also impacts several other Fortinet products, including:
- FortiMail
- FortiNDR
- FortiRecorder
- FortiCamera
Fortinet’s Product Security Team uncovered the flaw after identifying unusual attacker behaviors, including network scans, deletion of system crash logs, and the use of the fcgi debugging feature to capture system and SSH credentials.
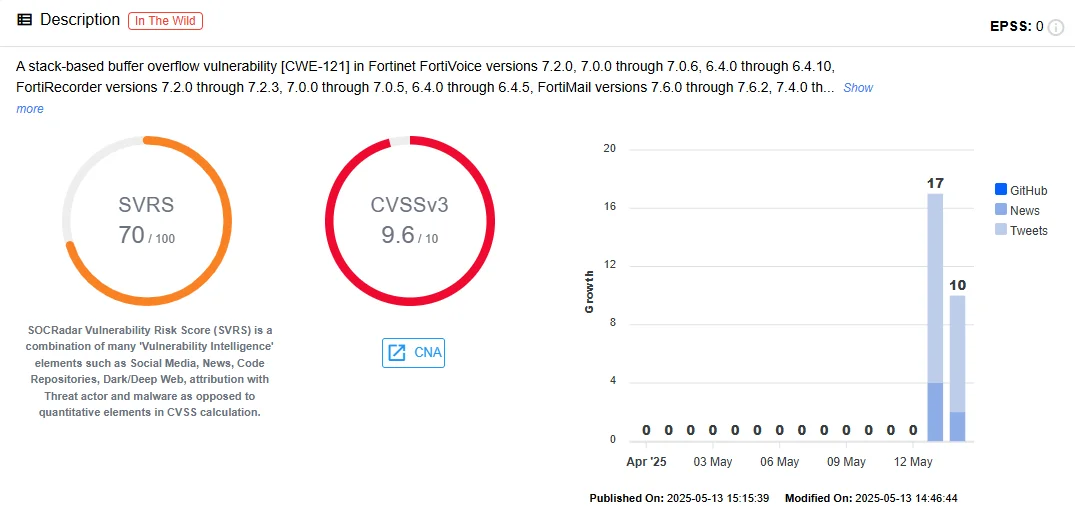
Vulnerability card of CVE-2025-32756 (SOCRadar Vulnerability Intelligence)
Indicators of Compromise (IOCs):
- ‘fcgi debugging’ enabled (disabled by default)
- Suspicious IPs used in attacks:
- 198.105.127[.]124
- 43.228.217[.]173
- 43.228.217[.]82
- 156.236.76[.]90
- 218.187.69[.]244
- 218.187.69[.]59
Attackers have been observed deploying malware, installing cron jobs for credential theft, and running scripts to scan internal networks. For customers unable to patch immediately, Fortinet recommends disabling the HTTP/HTTPS admin interface as a mitigation step.
This follows a wave of exploitation activity last month, when over 16,000 Fortinet devices were found compromised via a symlink backdoor previously addressed by patches.
Track the latest vulnerabilities with SOCRadar’s Vulnerability Intelligence
Ivanti Neurons for ITSM: Authentication Bypass Vulnerability (CVE-2025-22462)
Ivanti has patched a critical authentication bypass vulnerability, CVE-2025-22462, in its Neurons for ITSM on-premise IT service management solution. This flaw could allow unauthenticated attackers to gain administrative access in low-complexity attack scenarios.
Affected versions:
- 2023.4
- 2024.2
- 2024.3
Patched versions:
- May 2025 Security Patches for all affected versions
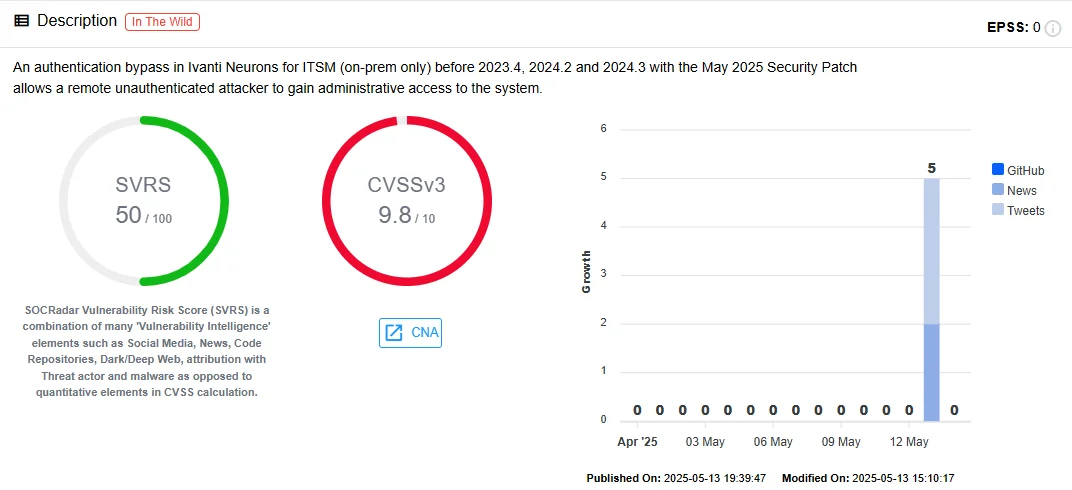
Vulnerability card of CVE-2025-22462 (SOCRadar Vulnerability Intelligence)
Ivanti confirmed that customers who followed prior security hardening guidance, such as restricting access via IIS settings and implementing DMZ configurations, are less exposed to this threat. The company has found no signs of exploitation in the wild so far.
Ivanti Endpoint Manager Mobile (EPMM): Zero-Day RCE Chain (CVE-2025-4427 & CVE-2025-4428)
In a separate advisory, Ivanti disclosed two vulnerabilities in Endpoint Manager Mobile (EPMM) that have been exploited in a limited number of attacks:
- CVE-2025-4427: Authentication bypass in the EPMM API
- CVE-2025-4428: Remote code execution via crafted API requests
When chained, these vulnerabilities can allow unauthenticated attackers to execute arbitrary code on exposed systems.
Mitigated in:
- EPMM 11.12.0.5
- EPMM 12.3.0.2
- EPMM 12.4.0.2
- EPMM 12.5.0.1
While the full extent of exploitation is still being assessed, Ivanti is urging all on-prem EPMM customers to update immediately. These issues do not affect cloud-based Neurons for MDM, Ivanti Sentry, or other Ivanti solutions.
Ivanti also noted that the vulnerabilities are linked to open-source libraries used by EPMM but did not disclose further details. According to the Shadowserver Foundation, hundreds of EPMM instances remain exposed online, with the highest numbers in Germany and the United States.
In Conclusion
These disclosures from Fortinet and Ivanti highlight an ongoing trend of attackers exploiting enterprise software flaws to gain deep access into critical systems. While Ivanti’s vulnerabilities have seen limited exploitation so far, Fortinet’s zero-day RCE flaw has already been actively weaponized.
Organizations using any of the affected products should prioritize patching and consider implementing available mitigations if immediate updates are not possible. Continuous monitoring and strict access controls remain key components of defense against evolving threat activity.
SOCRadar’s Attack Surface Management (ASM) module, Company Vulnerabilities
Stay one step ahead by managing what’s visible to threat actors. SOCRadar’s Attack Surface Management (ASM) module continuously maps your digital footprint, helping you find and fix weaknesses before they are exploited.
- Discover internet-facing assets, forgotten subdomains, and misconfigured services
- Monitor third-party risks and shadow IT
- Detect impersonating domains and exposed ports



































