
A New RAT Tool, Unauthorized VPN-RDP Access Sale, and New Database Leaks
Brace yourself for this week’s thrilling snapshot of the dark web, where secrets are the common currency, and anonymity reigns. We’re delving deep into the cyber shadows, where databases of several Spanish and United Arab Emirates companies are leaked.
But that’s not all. Get ready to discover the unauthorized shell access sale for an Australian ISP company.
This week, we pull back the veil on the hidden web where danger lurks and innovation thrives in the most unexpected ways.
Are you curious yet? Keep reading because the dark web never sleeps.
Find out if your data has been exposed.
Data of the United Arab Emirates are Leaked
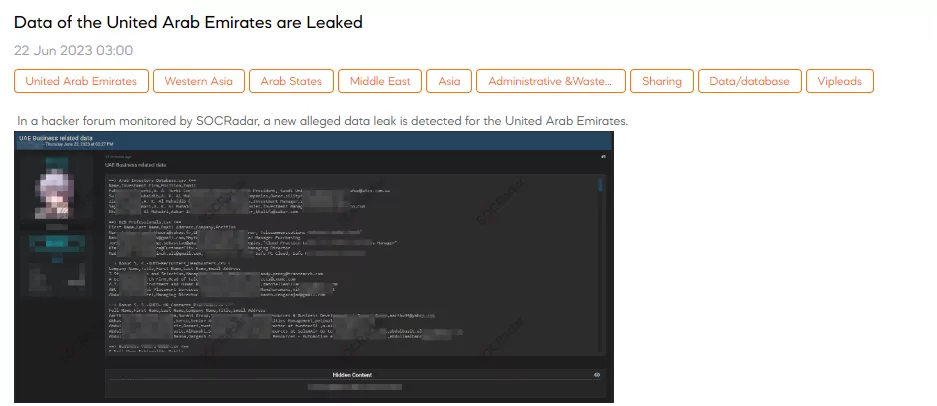
The SOCRadar dark web team recently discovered a threat actor’s claim regarding a new alleged data leak affecting the United Arab Emirates. The threat actor asserts that the leaked data includes UAE business-related information such as names, email addresses, company details, positions, nationalities, and phone numbers. However, inconsistencies were observed upon analyzing the sample data, suggesting the possibility that the data may have been collected from older sources or fabricated. This discovery raises concerns about the potential misuse of personally identifiable information (PII) for unauthorized activities such as fraud, social engineering, and identity theft.
Unauthorized Shell Access Sale is Detected for an Australian ISP Company

The SOCRadar dark web team has detected that a threat actor claims to sell unauthorized shell access. The access allegedly belongs to an Australian ISP company, which operates as an Internet Service Provider and generates a reported revenue of $122.9 million. The threat actor is offering this access for sale for 10,000 Monero (XMR). This unauthorized sale of shell access raises serious concerns as it gives the threat actor significant control and privileges within the compromised network.
Databases of Several Spanish Companies are Leaked
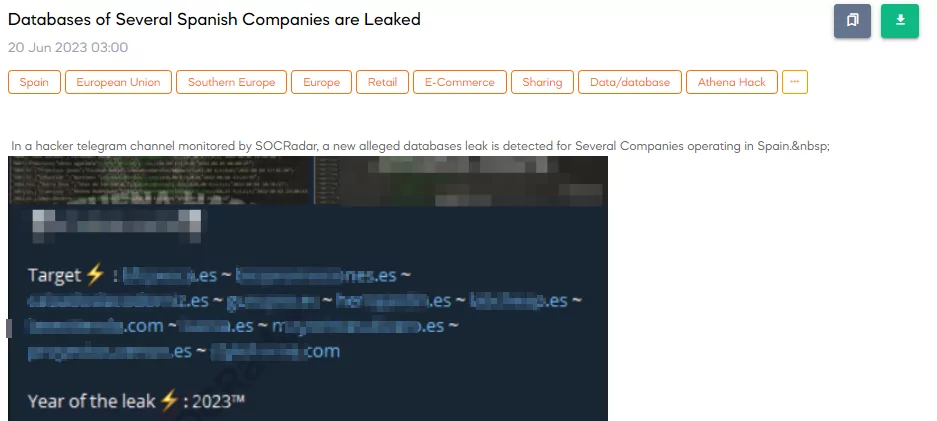
A SOCRadar analyst monitoring a Telegram channel has detected a claim by a threat actor stating that they have leaked databases of several companies operating in Spain, resulting in a new alleged database leak affecting several companies operating in the country. According to the threat actor, they have successfully captured all the data from these compromised stores.
A New RAT Tool is Shared
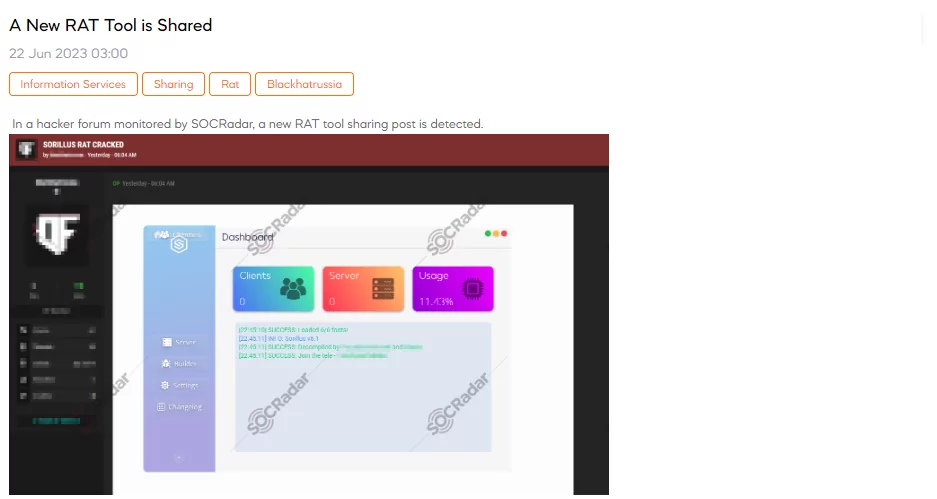
SOCRadar has detected a post sharing a new RAT tool called Sorillus RAT. It is a platform-independent Remote Access Trojan written in Java, allowing remote access to Java devices, including Windows, Linux, and Mac. The tool offers pop-up messages, clipboard access, remote desktop viewing, webcam access, and keylogging. The threat actor behind the tool plans to expand its capabilities to target Android devices.
Unauthorized VPN-RDP Access Sale is Detected for a Japanese Credit Cards & Transaction Processing Company
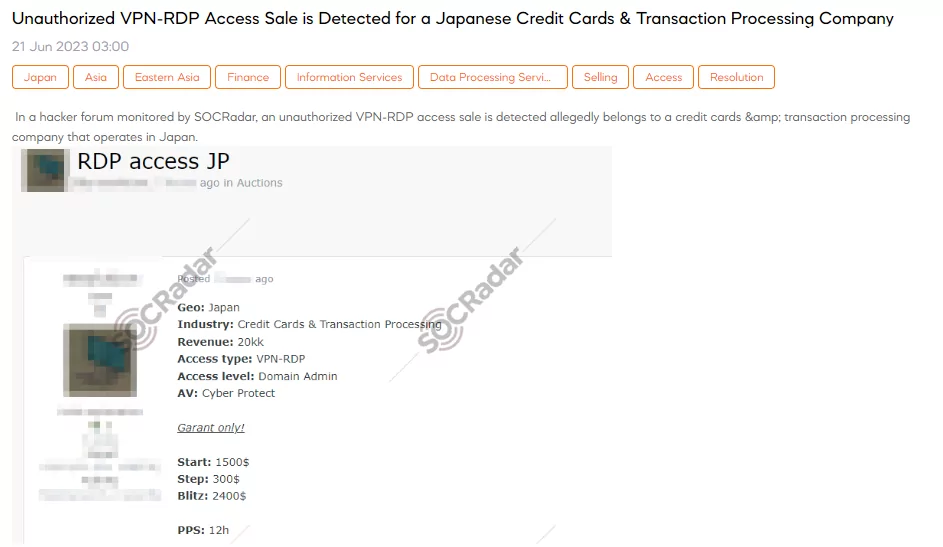
On June 21, SOCRadar noticed an alleged unauthorized sale of VPN-RDP access. The access is claimed to belong to a credit card and transaction processing company operating in Japan. The details provided indicate that the access level is set to Domain Admin, granting extensive privileges within the network. Cyber Protect is the antivirus software mentioned in the message installed on the alleged target system. The pricing for this unauthorized access sale is outlined, starting at $1,500 with a step increase of $300 and a blitz option available at $2,400.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































