All You Need To Know About Open Source Threat Intelligence Sharing Platform: MISP
Threat intelligence platforms (TIP) are critical security tools that use global security data to help proactively identify, mitigate, and remediate security threats. Every day there are unique and ever-changing challenges. Whilst security experts know that the solution to keeping up with these risks is analyzing data, the challenge is how to capture high data volumes effectively and thus obtain an aggressive perspective in order to deter potential attacks proactively. That is why security departments, especially SOC teams, depend on threat intelligence platforms (TIPs) in order to protect their organizations against cyber attacks.
What’s threat intelligence sharing and how it can improve security?
Threat intelligence sharing is going beyond IP addresses, hackings, and other key identifiers, includes the essential contexts around threat behavior, including indicators of compromise (IoC), indicators of attack (IoA), the tactics, techniques, and procedures (TTPs) used and, likely, the motive and identification of an adversary.
Industries need to exchange more intelligence data with business partners to help protect themselves against evolving threats and to adapt more quickly. Especially nowadays, sharing threat intelligence is critically important to foster greater collaboration and share best practices.
In fact, it is very straightforward to share some simple knowledge that is genuinely helpful and important to peer organizations while not revealing you as much as you thought.
What’s threat intelligence?

Cyber threat intelligence (CTI) is a type of intelligence that is used to determine the tactics, techniques, and procedures (TTPs) of the attackers as a result of analyzing the collected and enriched data that could damage the business elements at any level. CTI is the field of cybersecurity that focuses on collecting and analyzing information about current and potential attacks that threaten the security of an organization. The benefit of cyber threat intelligence is that it can prevent data leaks and especially save on financial costs.
Why threat intelligence is important?
To put it briefly, threat intelligence is required primarily to prevent data loss. Collecting and analyzing data can act as a precaution for possible attacks.
Another important point is that data breaches can be detected. The earlier a data breach that has occurred, the less harmful impact it will have on the organization.
Thirdly, with Incident Response, the information on which devices the data loss or breach is happening helps to identify the compromised systems.
What’s MISP?
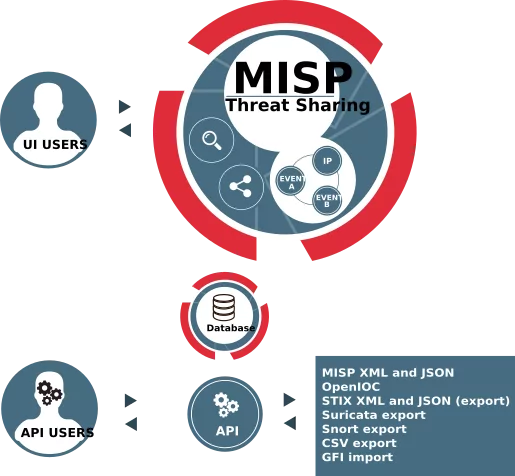
The MISP is a threat sharing platform for gathering, sharing, storing, and correlating Indicators of Compromise of targeted attacks, threat intelligence, financial fraud information, vulnerability information, or even counter-terrorism information. It is a free and open-source software helping information sharing of threat intelligence including cybersecurity indicators.
The project is developed by a team of developers from CIRCL, Belgian Defence, NATO, and NCIRC and funded by the European Union (through the Connecting Europe Facility) and the Computer Incident Response Center Luxembourg.
MISP assists security teams in the collection and review of vulnerability data for identified malware threats, dynamically linking and saving data in a centralized format with the malware and its assets.
The purpose of MISP is to create a platform of trust by locally storing threat information and enhancing malware detection to encourage information exchange among organizations.
Where is MISP used and what are its features?
MISP is used by different organizations in diverse sectors, each using threat feeds from the public, proprietary or local sources. If an instance is set up, organizations can add events to their own feeds viewable by either only organization.
MISP is mostly used by cybersecurity analysts, incident analysts, security experts, and malware analysts, and SOC teams. In addition to information exchange, network intrusion detection systems, log-based intrusion detection systems by MISP can be used by SIEMs. By integrating with APIs into SIEM products, the information obtained can also be correlated with the MITER ATT&CK framework.
Some of the top MISP features can be listed as follows;
- An efficient IoC and indicators database allowing to store technical and non-technical information about malware samples, incidents, attackers, and intelligence.
- Automatic correlation finding relationships between attributes and indicators from malware attacks campaigns or analysis. The correlation engine includes a correlation between attributes and more advanced correlations like Fuzzy hashing correlation (e.g. ssdeep) or CIDR block matching. Correlation can be also enabled or event disabled per attribute.
- A flexible data model where complex objects can be expressed and linked together to express threat intelligence, incidents, or connected elements.
- Built-in sharing functionality to ease data sharing using different models of distributions. MISP can synchronize automatically events and attributes among different MISP. Advanced filtering functionalities can be used to meet each organization’s sharing policy including a flexible sharing group capacity and attribute level distribution mechanisms.
- An intuitive user-interface for end-users to create, update, and collaborate on events and attributes/indicators. A graphical interface to navigate seamlessly between events and their correlations. An event graph functionality to create and view relationships between objects and attributes. Advanced filtering functionalities and warning list to help the analysts to contribute events and attributes.
- Storing data in a structured format (allowing automated use of the database for various purposes) with the extensive support of cybersecurity indicators along with fraud indicators as in the financial sector.
- Export: generating IDS (Suricata, Snort, and Bro are supported by default), OpenIOC, plain text, CSV, MISP XML, or JSON output to integrate with other systems (network IDS, host IDS, custom tools)
- import: bulk-import, batch-import, free-text import, import from OpenIOC, GFI sandbox, ThreatConnect CSV, or MISP format.
- Flexible free text import tool to ease the integration of unstructured reports into MISP.
- A gentle system to collaborate on events and attributes allowing MISP users to propose changes or updates to attributes/indicators.
- Data-sharing: automatically exchange and synchronization with other parties and trust-groups using MISP.
- Feed import: A flexible tool to import and integrate MISP feed and any threat intel or OSINT feed from third parties. Many default feeds are included in standard MISP installation.
- Delegating of sharing: allows a simple pseudo-anonymous mechanism to delegate publication of events/indicators to another organization.
- Flexible API to integrate MISP with your own solutions. MISP is bundled with PyMISP which is a flexible Python Library to fetch, add or update events attributes, handle malware samples, or search for attributes.
- Adjustable taxonomy to classify and tag events following your own classification schemes or existing taxonomies. The taxonomy can be local to your MISP but also shareable among MISP instances. MISP comes with a default set of well-known taxonomies and classification schemes to support standard classification as used by ENISA, Europol, DHS, CSIRTs, or many other organizations.
- Intelligence vocabularies called MISP galaxy and bundled with existing threat actors, malware, RAT, ransomware, or MITRE ATT&CK which can be easily linked with events in MISP.
- Expansion modules in Python to expand MISP with your own services or activate already available misp-modules.
- Sighting support to get observations from organizations concerning shared indicators and attributes. Sighting can be contributed via MISP user-interface, API as MISP document, or STIX sighting documents. Starting with MISP 2.4.66, Sighting has been extended to support false-negative sighting or expiration sighting.
- STIX support: export data in the STIX format (XML and JSON) including export/import in STIX 2.0 format.
- Integrated encryption and signing of the notifications via PGP and/or S/MIME depending on the user preferences.
- The real-time publish-subscribe channel within MISP to automatically get all changes (e.g. new events, indicators, sightings, or tagging) in ZMQ (e.g. misp-dashboard) or Kafka.
How does MISP work?
Events, feeds, groups, and users are included in the MISP structure. An incident is a threat entry that includes details on the threat and related IOCs. When an event is created, a user assigns it to a particular feed which acts as a centralized list of events of a certain organization and includes certain events or grouping requirements.
Via a web interface or REST API, MISP consists of trusted independent users and organizational threat submissions, both ingested by the respective user base. Organizations can subscribe to feeds linked to risks in their respective sectors by entering MISP groups. Users will start ingesting API pull requests on SIEM sites, identification protocols, firewall blacklists, and so on after signing up for the feeds. In addition, organizations may contribute to the community by incorporating feeds and activities that can be shared with others.
How can SOC teams use MISP more effectively?

Because members of MISP run the community, there is no central authority to tell users what to do. Each member association chooses independently how much information to exchange, how to use usable MISP information, etc.
SOC analysts use MISP to view how a specific campaign can be applied to various IP addresses and associated attributes because of the set of data shown by MISP. This amount of knowledge about threats gives you a richer image of a particular threat than any company itself would produce. SOC teams are fuelled by the combined force of MISP intelligence, creating a greater reaction that normally decreases the meantime to the resolution of an attack (MTTR).
MISP also offers an enrichment with risks as well as threats exchange. The MISP dashboard offers information that allows users to gain insight into the threat and what it could do with their environment. For example, MISP may illustrate that the indicator seen by a member of the group in the attack campaign forms part of a series of indicators.
What is the difference between MISP and a threat intelligence platform (TIP)?
MISP is a centralized platform for threat analysis with many features, but unfortunately, there is no real threat intelligence available via the platform.
For instance, the following features of a typical TIP aren’t available in MISP;
- A true TIP can collect tactical and technical intelligence from multiple external sources, including threat intel providers, hacker forums, chat rooms, the dark web, and more.
- Most TIPs provide scoring of IOCs and suggest certain actions.
- To perform real-time correlation, deduplication, analysis, and indicator deprecation, a TIP enriches details on threats by using different sources or platforms.
- Many advanced TIPs provide a human threat analyst in order to minimize false-positive results who also keeps in touch with the organization in order to protect the operation of the business.
A true threat intelligence platform can protect you from adversaries
A real TIP such as SOCRadar can protect you from cybercriminals by providing premium level TIP experience;
- Power of automation: Skyrocket security team efficiency by reducing mundane tasks.
- 360° visibility: Gain in-depth visibility into your external-facing digital assets.
- Precise API integration: Smooth integration with existing security stack and SIEM solutions.
- Immediate start: Hitting the ground in hours, discovering, monitoring, and alerting without requiring any input.
- Optimized costs: Choose from the discovered assets only you want to monitor to reconcile license costs with real needs.
- CTIA support: Ready to work with clients to identify and remediate threats, helping them build in-house skills and expertise.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.