
All You Need to Know About SandBreak Vulnerability in VM2
What is the SandBreak Vulnerability?
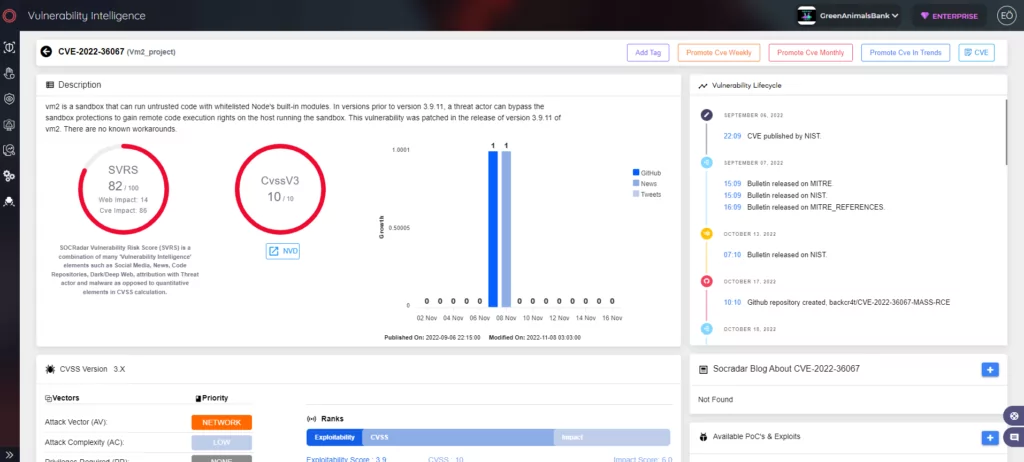
The SandBreak vulnerability in vm2 is identified as CVE-2022-36067. A remote attacker could exploit the vulnerability to bypass the sandbox environment, which could enable them to execute shell commands on the host device.
The vulnerability impacts Backstage, an open platform for creating developer portals. If this vulnerability is exploited, it could seriously affect a targeted enterprise.
Spotify created Backstage and gave it to the Cloud Native Computing Foundation. It offers a catalog for keeping track of all the user’s software, project-creation templates, and open-source plugins that can be used to increase the system’s customizability and functionality.
How Critical is the SandBreak Vulnerability?
When CVE-2022-36067 was discovered in August 2022, security researchers from Oxeye assigned it a CVSS score of 10. As of now, the vulnerability has a CVSS score of 9.8.
Its effects could be wide-ranging, as numerous well-known companies use Backstage, including Netflix, Spotify, American Airlines, Doordash, Palo Alto Networks, HP, Siemens, LinkedIn, Trendyol, and Booz Allen Hamilton.
You can find a more detailed list on Backstage’s GitHub.
Which Versions are Vulnerable?
Backstage versions before 1.5.1 are vulnerable to CVE-2022-36067.
By taking advantage of a vm2 sandbox escape in the Scaffolder core plugin, a threat actor can run arbitrary system commands on a Backstage application without being authenticated.
How Does the SandBreak Vulnerability Work?
To run in the VM environment rather than the Nunjucks, override the renderString function to include a customized implementation. This is necessary to take advantage of the vulnerability.
Invoke an undefined function to cause an error (triggerException). This causes NunjucksWorkflowRunner.render to make a second call to the SecureTemplater.render function and can be found in this code.
Read more about the exploitation of the vulnerability in SOCRadar’s previous blog.
Is the SandBreak Vulnerability Actively Exploited in the Wild?
In Oxeye’s simulation of an in-the-wild exploit, over 500 instances of Backstage were found exposed to the internet. The number has decreased since.

No threat groups actively exploited this vulnerability recently, but it is advised to apply necessary security measures.
Is There Any Mitigation or Patch Available?
Backstage has been patched against the vulnerability in version 1.5.1.
How to Protect Against the Vulnerability?
If you must use a sandbox, separating the microservice that runs the sandbox code from the logically sensitive part of your application is best.
Vm2 version 3.9.11 was released in late August to address the SandBreak vulnerability; make sure to use a safe version or the latest version.
If your organization uses Backstage, it is recommended that you update to the most recent version of Backstage and use secure templates to avoid introducing server-side template injection vulnerabilities into your application.




































