
All You Need to Know About the Latest OpenLiteSpeed Web Server Vulnerabilities
Researchers have discovered three different vulnerabilities, two of which are assigned a high severity rating and respectively used in the attack chain in the OpenLiteSpeed web server. According to some sources, it could be ranked #4, #5, or #6 as the well-known web server and the best alternative to Nginx and Apache, chosen open-source web server among the most popular ones in the world. An analysis from Palo Alto Networks has shown that 1.9 million LiteSpeed unique servers are facing the internet accordingly.
Below we briefly explain the attack stages;
The first attack phase involves finding a vulnerable admin dashboard and command injection vulnerability.
After gaining remote code execution via External App Command, it is acquired the unprivileged user “nobody” that exists in the Linux machine. (CVE-2022-0073)
Finally, privilege escalation is accomplished from “nobody” to “root,” exploiting CWE untrusted search path in the OpenLiteSpeed Docker due to the misconfiguration of the path environment variable. (CVE-2022-0074)
It is noted that these vulnerabilities cannot be exploited for initial access by attackers; on the other hand, necessary patches should be made against attackers who try to have credentials via brute force or social engineering techniques and internal threats.
What are the CVE details and severity status of vulnerabilities?
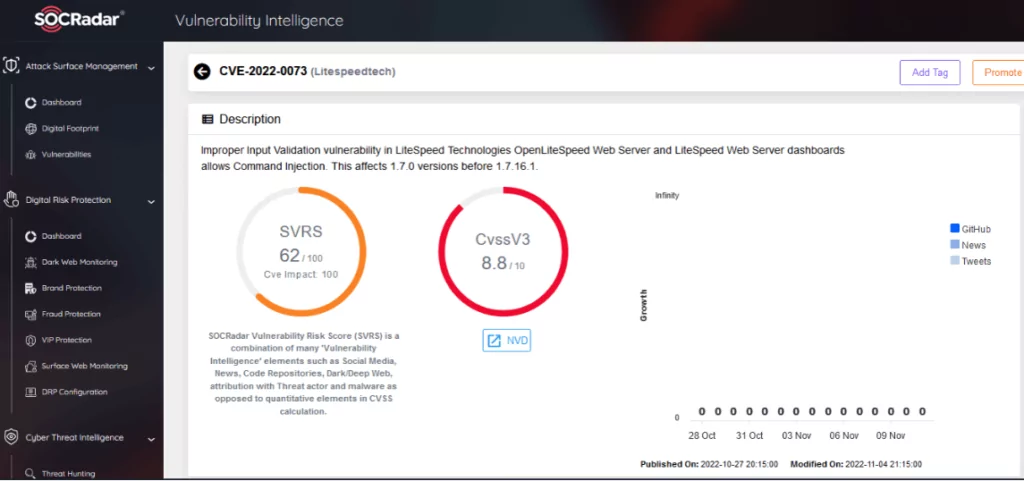
- Remote Code Execution (CVE-2022-0073) Rated High severity (CVSS 8.8): An attacker who seizes the admin dashboard credentials of the OpenLiteSpeed Web Server can execute remote code. This vulnerability can bypass these mitigations even if measures are taken against remote code execution in the External App Command section.
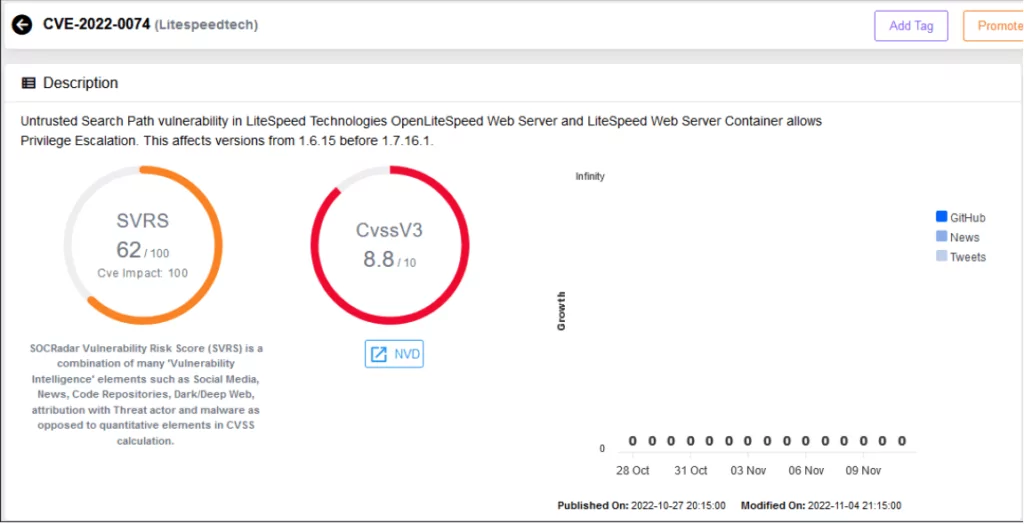
- Privilege Escalation (CVE-2022-0074) Rated High severity (CVSS 8.8): In this vulnerability, which can be abused after Remote Code Execution, an attacker can access root-level privileges by exploiting a misconfiguration vulnerability existing in older versions.
- Directory Traversal (CVE-2022-0072) Rated Medium severity (CVSS 5.8): Exploiting this vulnerability allows adversaries to access any file in the web root directory but is limited only to that directory.
Which OpenLiteSpeed Web Server versions are vulnerable?
|
OpenLiteSpeed Web Server |
|
|
|
|
LiteSpeed Web Server |
|
|
|
Has the security patch update currently been published?
LiteSpeed Technologies released the remediation patch for OpenLiteSpeed on October 18, 2022.
OpenLiteSpeed Docker Container was also recently updated.
Organizations using LiteSpeed Technologies Web Server applications should patch up to OpenLiteSpeed 1.7.16.1 and LiteSpeed 6.0.12 versions to avoid being affected by the vulnerabilities mentioned.



































