Alleged Check Point Breach: What Happened and What You Need to Know?
[Update] April 2, 2025: “Latest Developments: Dissecting CoreInjection’s Claims and the Alleged Leak”
On March 31, 2025, a threat actor known as CoreInjection claimed responsibility for a breach at Check Point Software Technologies. The hacker posted evidence online and offered what they described as sensitive internal data for sale on the dark web. According to their claims, the dataset includes internal network diagrams, hashed and plaintext credentials, and customer-related access details.
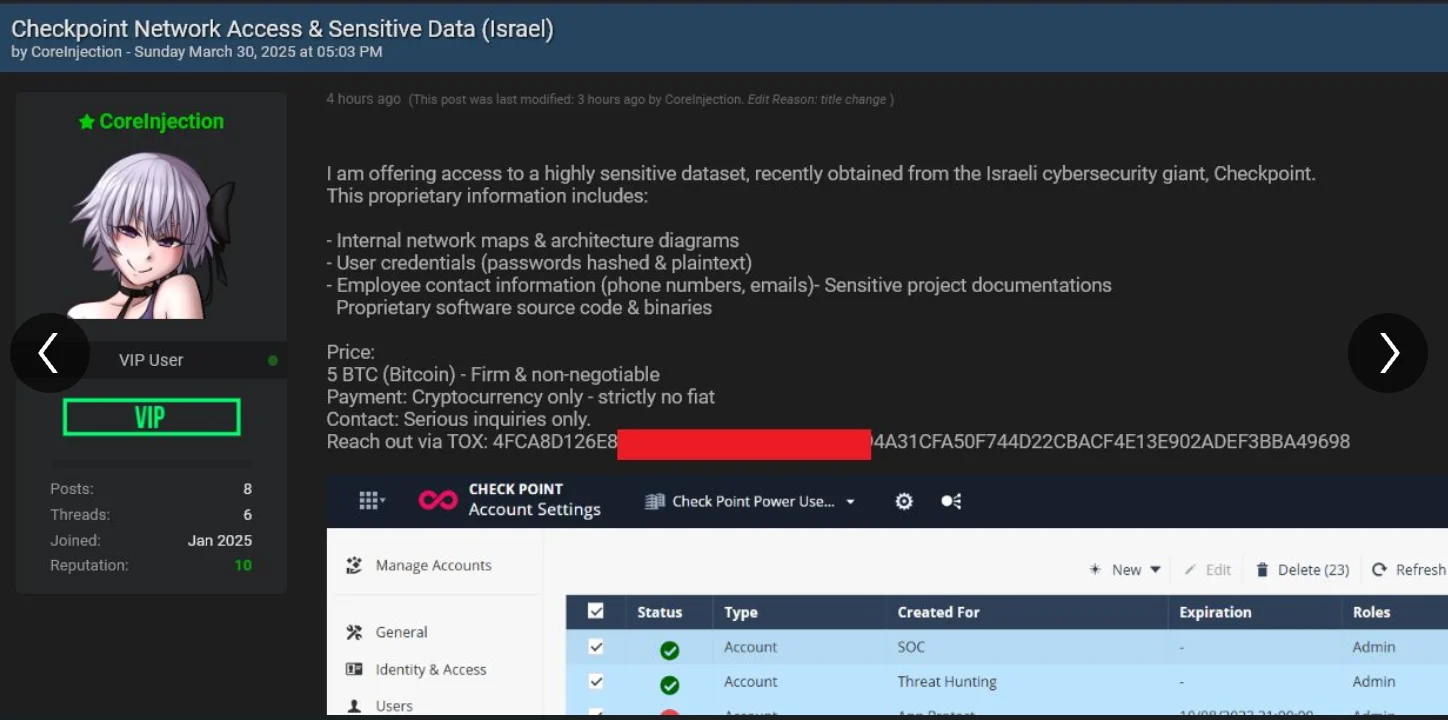
CoreInjection’s post named Checkpoint Network Access & Sensitive Data (Israel)
However, Check Point has since responded, downplaying the incident and describing it as an old, pinpointed and contained issue with no security implications.
While the threat actor’s screenshots appear to show access to an admin panel, they lack timestamps, raising doubts. Even hacker forum users seem skeptical, and the alleged data is being offered for sale at 5 BTC.
Who Is CoreInjection?
CoreInjection is a threat actor with a history of targeting Israeli companies. The group has previously attacked Clal Insurance and similar high-profile organizations, frequently in Israel, making CoreInjection a relatively credible adversary.
Threat actor’s profile in BeachForums
When the alleged breach surfaced, security professional and CTO at Hudson Rock Alon Gal initially found the screenshots provided by the hacker to be highly convincing. He noted that CoreInjection has a track record of legitimate leaks, and the details in the images looked too real to be faked.
What Data Was Allegedly Stolen?
CoreInjection claims to have accessed Check Point’s internal systems and Infinity Portal, extracting:
- Internal network architecture diagrams
- Hashed and plaintext credentials
- Employee contact details (emails, phone numbers)
- Sensitive project documentation
- Admin-level access to dashboards (including over 121,000 account records, with nearly 19,000 identified as paying customers)
The hacker offered this data for sale on a Dark Web forum for 5 Bitcoins (~$410,000).
Some of the sample screenshots provided by threat actor as follows:
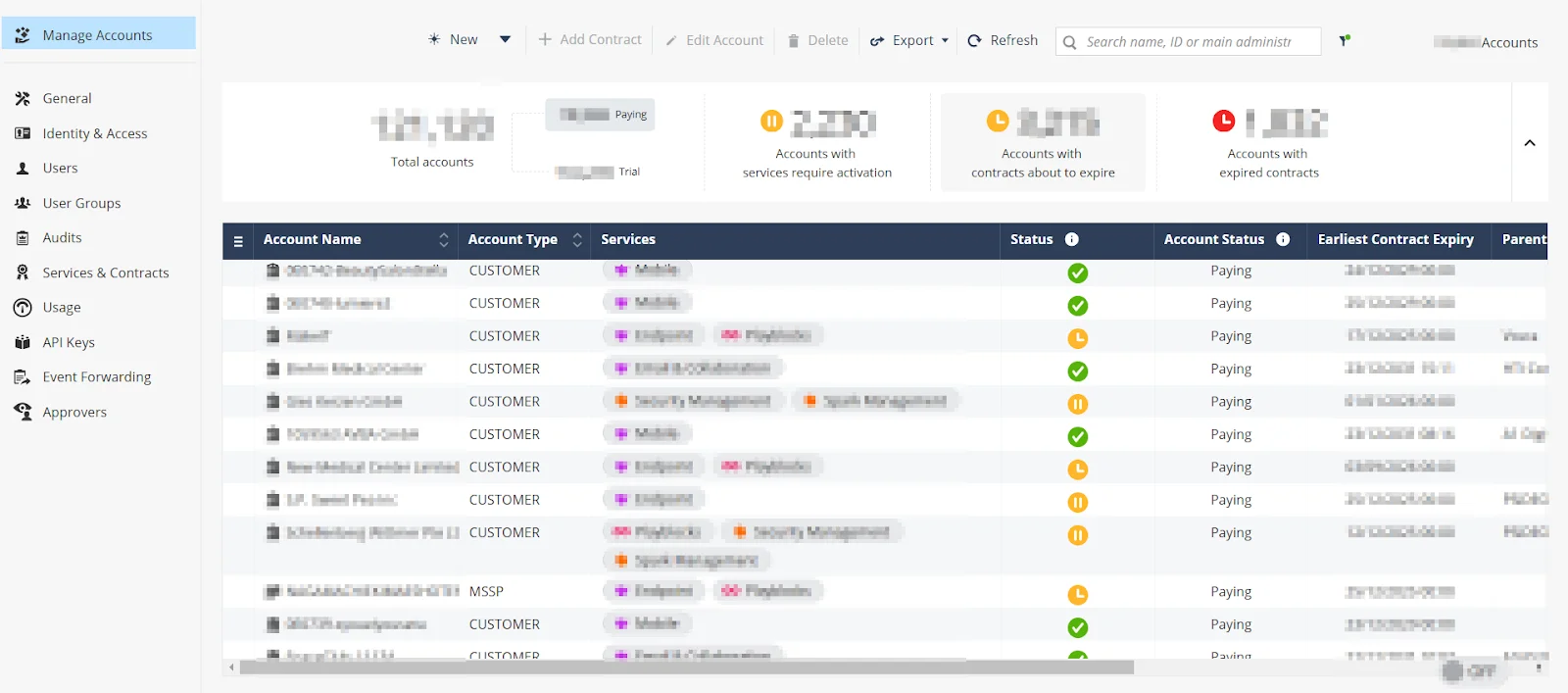
Screenshot of the panel #1
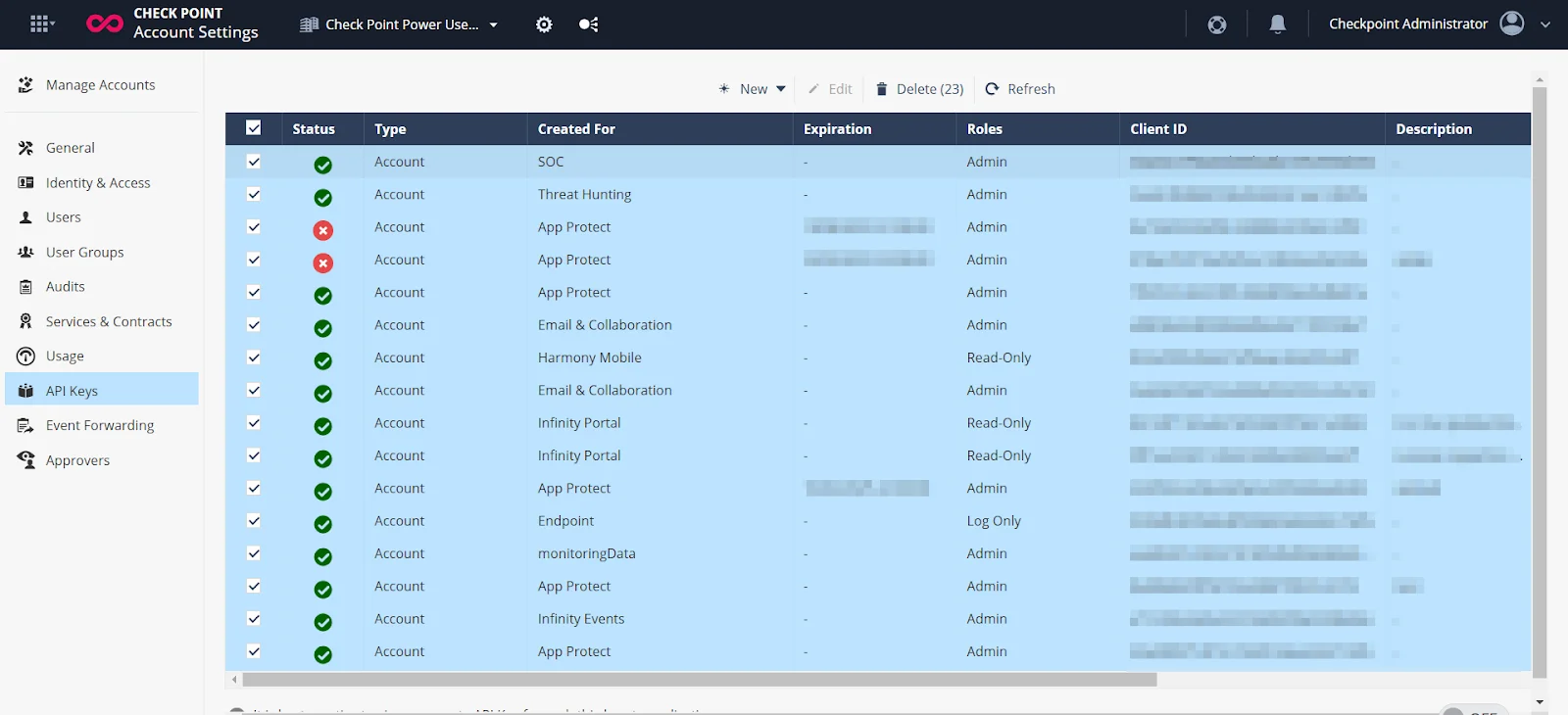
Screenshot of the panel #2
How Did the News Break?
The alleged breach was first reported on X (formerly Twitter) by cybersecurity accounts such as @DarkWebInformer, @Ransom_DB, @UndercodeUpdate, @SecurityJoes, @thedeepintel, and @CyberNews. Alon Gal and other researchers later analyzed the evidence, sharing their insights online.
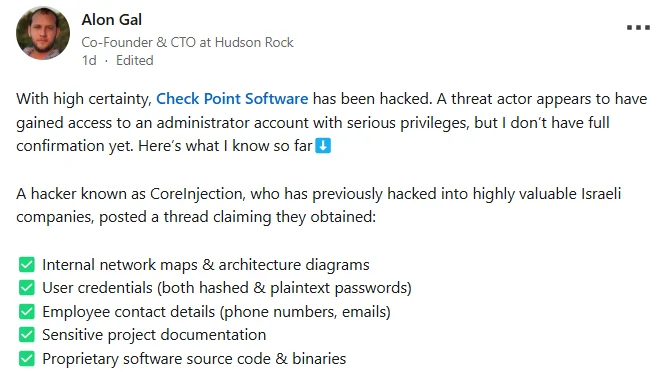
Alon Gal’s LinkedIn post
How Did Check Point Respond?
Yesterday, Check Point released an official statement on their support page, asserting:
- The data leak originated from an old, known event that occurred in December 2024.
- The breach stemmed from compromised credentials belonging to a portal account with limited access.
- The exposure was restricted to a few account names, product names, and some employee contact details.
- No customer systems, production environments, or security architectures were affected.
- The hacker’s claims were exaggerated and misleading.
Is There Evidence of a Major Security Breach?
At this stage, independent verification of the breach remains inconclusive. No other security firms have fully confirmed or debunked.
Alon Gal later noted that while some evidence appeared credible, the actual scope of the breach might be narrower than initially feared. He warned against unnecessary panic, urging the community to differentiate between the hacker’s claims and the actual proof provided.
Latest Developments: Dissecting CoreInjection’s Claims and the Alleged Leak
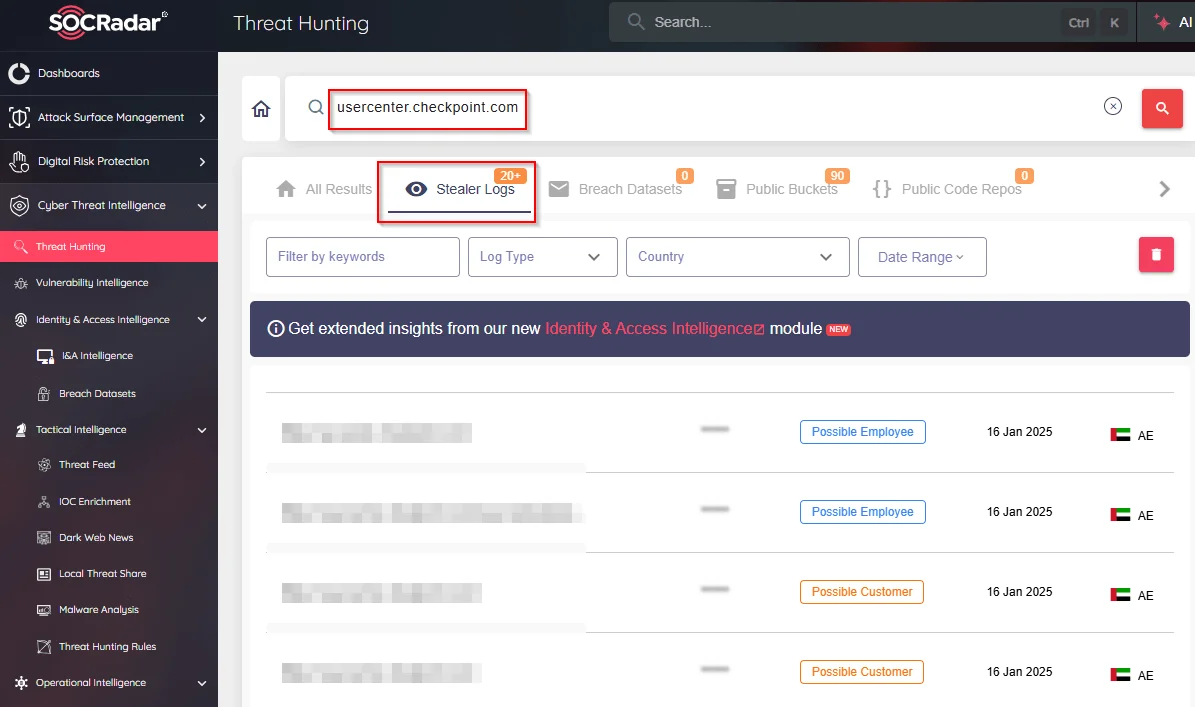
Recent developments have cast doubt on CoreInjection’s role in the Check Point breach. According to Alon Gal’s post, they have analyzed the 350 user records shared by CoreInjection and confirmed that they originate from infostealer logs, not from Check Point’s systems. This suggests that CoreInjection’s so-called “leak” is unrelated to the actual security incident acknowledged by Check Point.
The revelation raises key questions about attribution. While Check Point has confirmed that the screenshots circulating online do depict legitimate platform access, it remains unclear how CoreInjection obtained them. Given the reliance on stolen credentials from infostealer malware—often harvested by trojans like Lumma or Redline—it’s increasingly plausible that CoreInjection did not execute the breach themselves but instead sourced these materials from underground forums or merely attempting to exaggerate the extent of its limited breach.
This tactic, where threat actors inflate their role by blending legitimate evidence with misleading claims, is common in cybercrime circles. By using publicly available breach materials alongside unrelated data, actors can fabricate a stronger narrative to gain credibility or influence negotiations.
What is the Timeline of Events?
- December 2024: A limited breach occurred due to compromised credentials of a portal account with restricted access. Check Point did not publicly disclose this at the time, but in their March 31 advisory, they clarified that the breach did not involve customer systems, production environments, or security architecture.
- March 30, 2025 (16:51 EDT): The threat actor “CoreInjection” claims responsibility for the breach on a hacker forum named BreachForums, alleging access to internal systems and customer data.
- Evening of March 30: Posts and screenshots shared by threat actor circulate on social media, showing what appears to be admin panel access. However, the images lack timestamps, raising doubts among hacker forum users about their authenticity.
- March 31, 2025 (03:49 – 09:11 EDT): Cybersecurity analysts and researchers react. While some initially found the screenshots convincing, further analysis suggests the breach’s scope is likely narrower than first feared.
- March 31, 2025: Check Point publishes an official advisory, confirming the breach in December but emphasizing that it was limited, previously addressed, and involved no customer systems or sensitive security data. They also noted that the claims being circulated are exaggerated.
What Should CISOs and Security Teams Do?
- Monitor the Situation Closely
Stay updated by following credible sources, including our blog and Check Point’s official communications. While the breach seems to be from a previously identified and contained event, it’s important to remain informed about any new developments. - Assess Internal Risk Exposure
If your organization uses Check Point products (such as Harmony, Quantum, CloudGuard, or Infinity Portal), consider conducting the following:- A review of internal systems
- A credential audit
- Access log analysis to detect any potential anomalies
- Strengthen Security Defenses
While Check Point has clarified that the breach did not involve customer systems, it’s always wise to reassess your organization’s defenses. Strengthen your phishing resilience, enable MFA and ensure that edge devices are patched.
You may also want to consider temporary IP whitelisting for Check Point logins as a precaution. - Prepare Communication Strategies
Draft internal and external messaging in case customers or stakeholders reach out with concerns. Be sure to emphasize Check Point’s clarification that this was a previously addressed, contained event and that there’s no immediate threat to customer data or security.
Summary
While initial concerns about the alleged breach were high, further analysis suggests the impact may be much narrower than first thought. Check Point maintains that there is no risk to customers, and even researchers who initially found the screenshots convincing now acknowledge that the scope appears limited.
That said, ongoing scrutiny is needed as more details emerge. Security teams should remain vigilant by reviewing access logs and following best practices, but there’s no immediate cause for alarm. Stay tuned for updates as the situation develops.