
Android’s May 2025 Update Tackles CVE-2025-27363 & More – Langflow & MagicINFO Exploited, Kibana at Risk
Google has rolled out its Android security bulletin for May 2025, addressing a total of 46 vulnerabilities, including a critical Remote Code Execution (RCE) flaw, CVE-2025-27363, which is already being actively exploited.
This month’s patch includes fixes for Android system and framework components and also touches on Google Play system updates and vulnerabilities in third-party drivers and components from Imagination Technologies, Arm, MediaTek, and Qualcomm.
But the Android ecosystem is not the only target. Newly disclosed or actively exploited vulnerabilities have also emerged across other platforms. Recent examples include Langflow, a popular visual programming tool; Samsung MagicINFO, used for content and device management; and a critical, yet-to-be-exploited RCE vulnerability in Kibana, a widely used data visualization tool.
CVE-2025-27363 Exploited in the Wild: Android’s May Update Fixes Critical System Flaw
Google’s May 2025 Android security bulletin spotlights a high-risk vulnerability, CVE-2025-27363 (CVSS 8.1), as the most pressing concern. Found in the Android System component, this flaw enables local code execution without requiring user interaction or elevated privileges. What makes it particularly dangerous is that it can compromise device integrity if platform-level mitigations are bypassed.
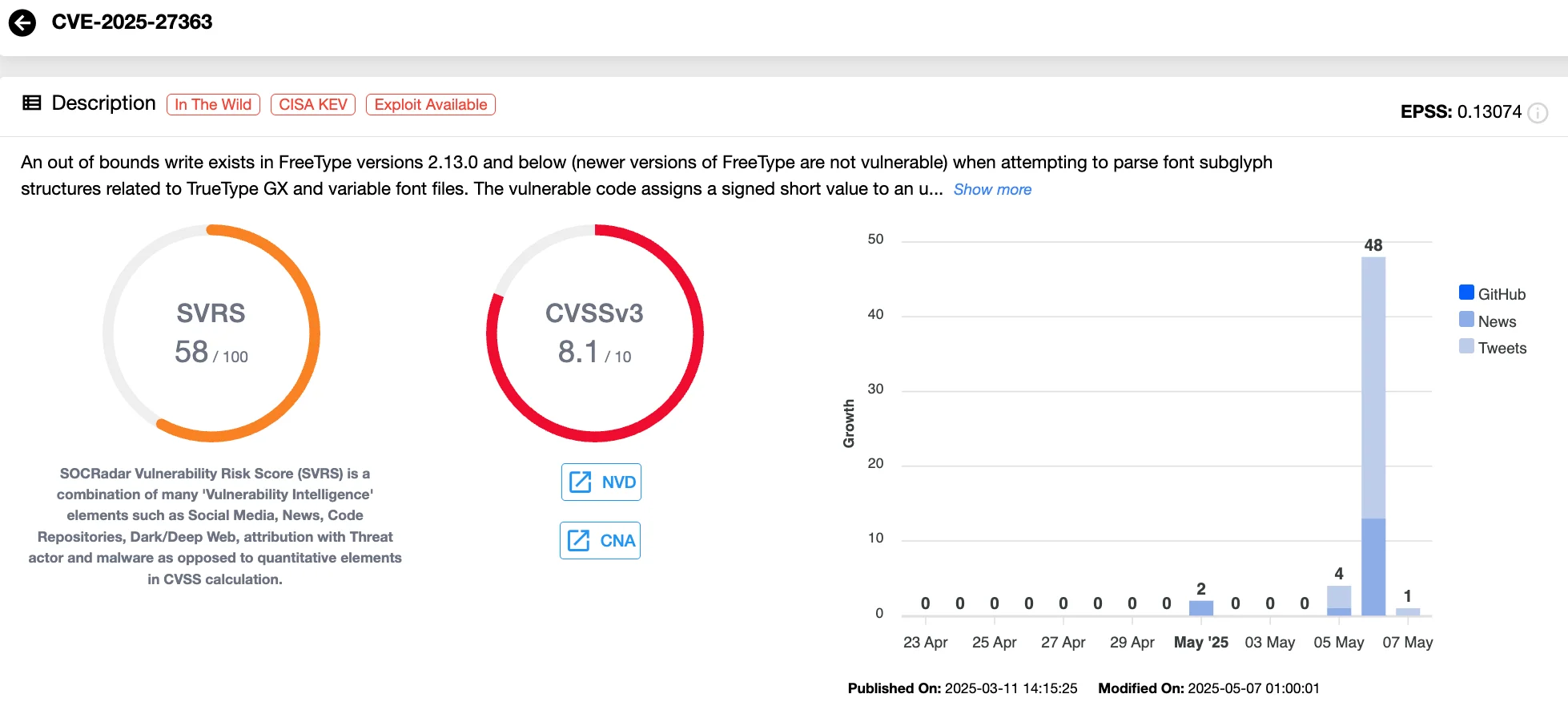
Vulnerability card of CVE-2025-27363 (SOCRadar Vulnerability Intelligence)
This vulnerability stems from FreeType, an open-source font rendering library widely embedded in Android. It was originally flagged by Facebook’s security team back in March and has since been linked to limited, targeted exploitation in the wild.
Google’s advisory underscores the severity, and CISA has echoed the concern by adding it to its Known Exploited Vulnerabilities Catalog. U.S. federal agencies are now under directive to apply the patch by May 27, 2025.
Broader Fixes Span Framework, System, and Hardware
Beyond this actively exploited bug, the bulletin resolves several other high-impact issues across Android versions 13 through 15. These include multiple Elevation of Privilege (EoP) flaws affecting both the framework and system components. Among them are CVE-2025-0087 and CVE-2025-26426, both capable of allowing unauthorized privilege gains on vulnerable devices.
Hardware-level vulnerabilities also received attention. Google patched issues across drivers from Arm, Imagination Technologies, MediaTek, and Qualcomm. These include bugs that could affect camera functionality, modem integrity, and even location services – areas where any breach could translate into significant security risks.
Some of the fixes landed via Google Play system updates, enhancing components like the Documents UI, Permission Controller, and the WiFi subsystem. These updates play a crucial role in keeping Android’s modular architecture secure, even outside full OS upgrades.
To reinforce defenses, Google continues to lean on Google Play Protect, which runs by default on most Android devices. It helps flag potentially harmful apps, particularly when users sideload content from outside the Play Store. Combined with newer Android versions’ built-in exploit mitigations, it forms a solid baseline against mobile threats.
As always, users should check for the latest security patch – either 2025-05-01 or 2025-05-05, depending on the device – and apply it as soon as possible. Regular updates remain the most effective frontline defense.
More details can be found in the Android Security Bulletin for May 2025.
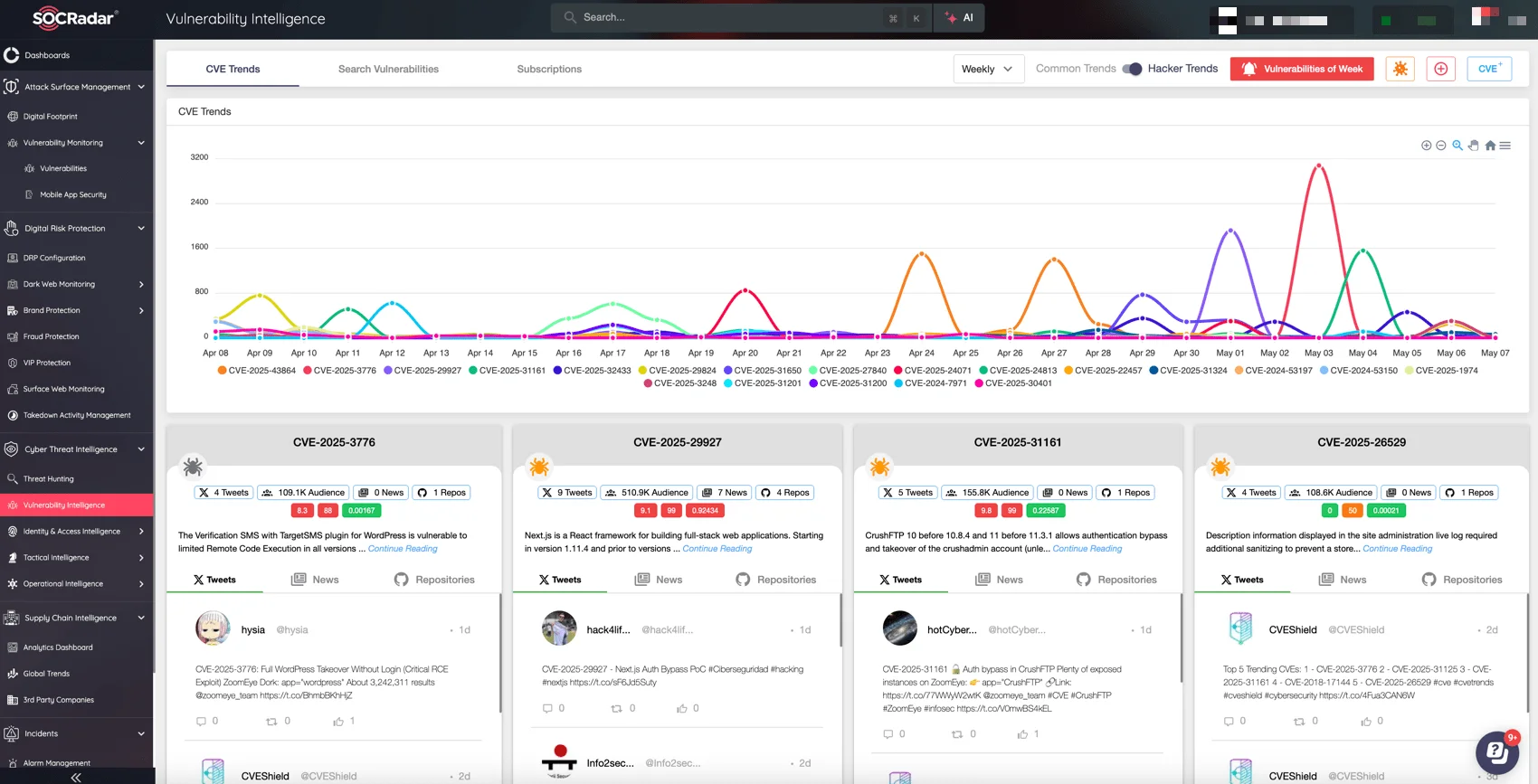
SOCRadar’s Vulnerability Intelligence: Latest CVEs & hacker trends
Timing and actionable insights are critical in preventing vulnerability exploitation. SOCRadar XTI, through its Vulnerability Intelligence capabilities, equips organizations to respond faster and more effectively by providing:
- Real-time threat intelligence on newly published and zero-day vulnerabilities
- Exploit tracking, including threat actor TTPs and in-the-wild indicators
- Prioritization insights, helping you patch what’s actually being targeted
- Enrichment data that connects vulnerabilities to related malware, threat groups, and campaigns
With SOCRadar, security teams can cut through the noise, reduce response times, and focus resources where they matter most.
CVE-2025-3248 in Langflow Actively Exploited, Poses RCE Risk to AI Tool Deployments
Another actively exploited vulnerability recently flagged by CISA is CVE-2025-3248 (CVSS 9.8), affecting Langflow, an open-source web application used to build AI-powered agents. The flaw has been added to the Known Exploited Vulnerabilities (KEV) catalog, and federal agencies have until May 26, 2025, to patch or mitigate the issue.
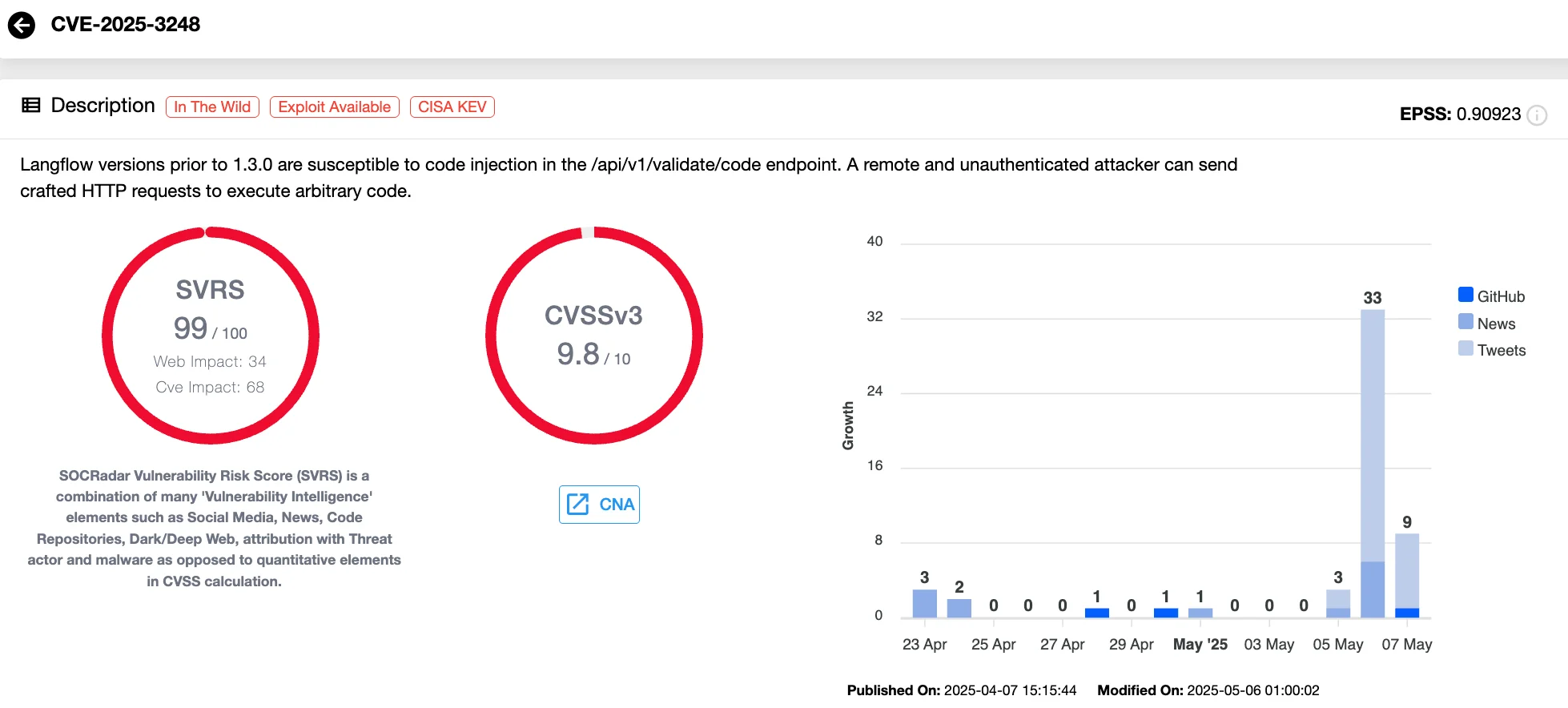
Vulnerability card of CVE-2025-3248 (SOCRadar Vulnerability Intelligence)
The vulnerability lies in an exposed API endpoint (/api/v1/validate/code) which lacks both input validation and authentication. This opens the door for remote attackers to execute arbitrary code simply by sending a malicious HTTP request. Exploiting the vulnerability, an attacker can deploy reverse shells, backdoors, or data exfiltration tools, or even download and execute malware directly on the server.
Although patched in Langflow version 1.3.0, the vulnerability continues to attract attention. Its exploitation escalated after proof-of-concept (PoC) code was made public in April, followed by detailed technical analysis by researchers.
Almost immediately after the PoC release, SANS ISC’s honeypots picked up scanning activity targeting the flaw. Some of these probes were attempts to extract sensitive files like password lists, pointing to reconnaissance behavior and possible exploitation attempts. Many of the scans were routed through TOR exit nodes, indicating a desire to remain hidden.
Horizon3.ai, who originally discovered the flaw, noted that while the patch now places the endpoint behind authentication.
Real-World Impact and Mitigation Guidance
About 500 Langflow instances remain exposed to the internet. Alarmingly, many of these may not be updated. Even more concerning, authentication on these instances does not prevent exploitation of this specific vulnerability, making patching the only real safeguard.
For teams using Langflow, particularly in cloud environments, upgrading to version 1.3.0 or newer is critical. It is also advised to isolate deployments in virtual private networks and use single sign-on (SSO) for added security.
CVE-2024-7399 in Samsung MagicINFO Abused to Deliver Mirai Bot Malware
Another vulnerability making waves is CVE-2024-7399 (CVSS 7.5), a path traversal flaw in Samsung MagicINFO, a platform used to manage commercial displays and also enables remote diagnostics, firmware updates, and system-wide content control.
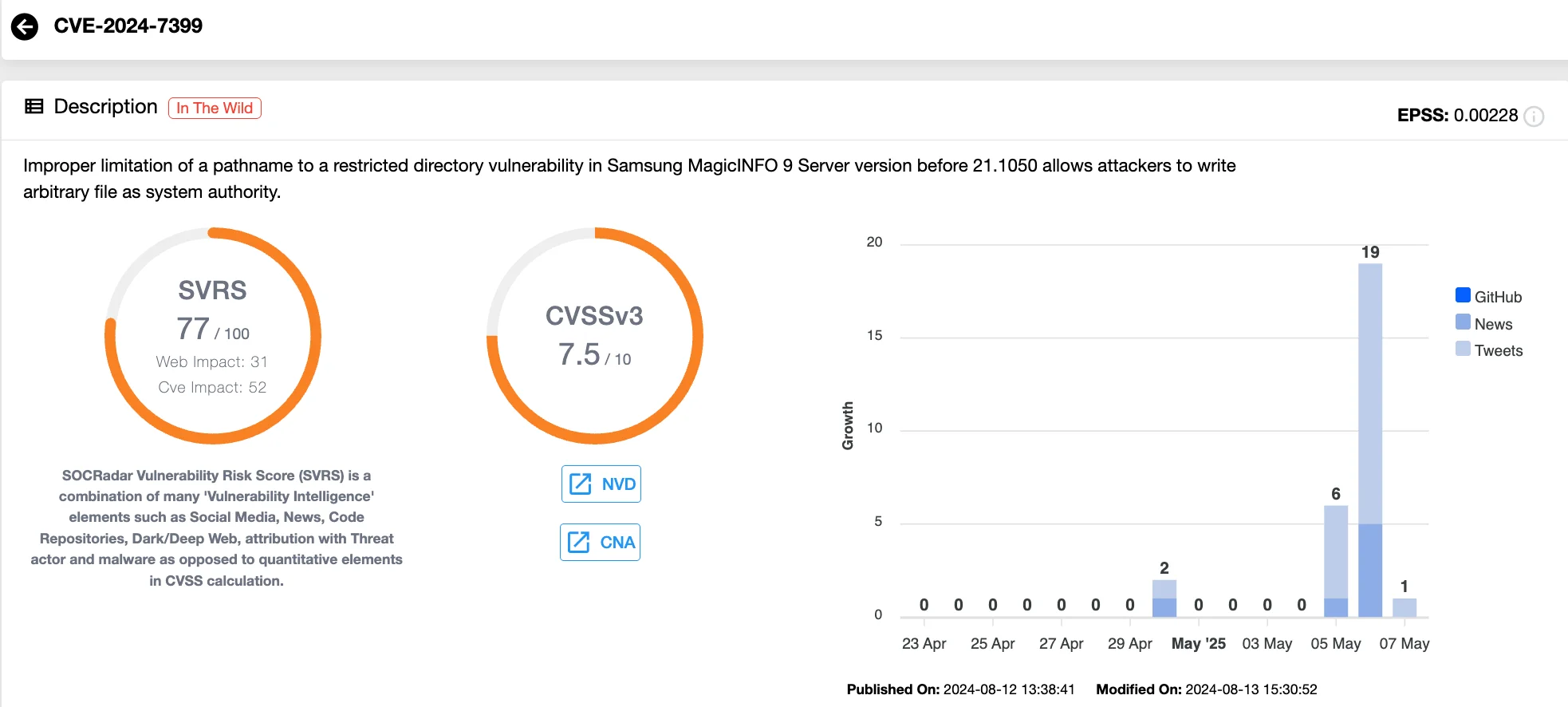
Vulnerability card of CVE-2024-7399 (SOCRadar Vulnerability Intelligence)
Attackers have begun actively exploiting the vulnerability, leveraging it to upload and execute malicious scripts that install Mirai botnet malware. The attackers are targeting the server component of MagicINFO, specifically, version 21.1050 and earlier, where improper sanitization of uploaded filenames allows them to bypass authentication checks and run arbitrary code.
According to researchers, the flaw originates from weak input validation logic. The server does not check whether a file being uploaded is safe or whether the user is even logged in. That gives attackers a clear path to upload a malicious .jsp file and execute it with system-level privileges. A patch was released by Samsung back in August 2024, but exploitation did not ramp up until a public Proof-of-Concept (PoC) exploit was released recently, dramatically lowering the barrier for threat actors.
Mirai Botnet Expands Through GeoVision and Legacy IoT Devices
Samsung MagicINFO is not the only system being conscripted into botnets. Security researchers have also observed Mirai-linked activity targeting GeoVision IoT devices, many of which have reached End-of-Life (EoL) status. With patching off the table, upgrading to newer, actively supported models is the only reliable way for users to stay protected.
Attackers are exploiting two severe OS command injection vulnerabilities, CVE-2024-6047 and CVE-2024-11120, to gain remote control over these devices. The attacks are designed to compromise outdated firmware and inject commands into vulnerable endpoints like /DateSetting.cgi, enabling the download and execution of a custom Mirai variant called LZRD.
The campaign appears to overlap with tactics used in previous botnet efforts, including exploits for older vulnerabilities like CVE-2018-10561 (Hadoop YARN) and flaws affecting DigiEver devices.
A set of indicators of compromise (IOCs), YARA rules, and technical insights is available here.
CVE-2025-25014: Critical Code Execution Flaw in Kibana Threatens Self-Hosted and Cloud Deployments
A newly disclosed vulnerability, CVE-2025-25014 (CVSS 9.1), poses a critical risk to Kibana, the popular data visualization and management interface for Elasticsearch. This flaw, stemming from prototype pollution, enables attackers to achieve arbitrary code execution by sending specially crafted HTTP requests to exposed machine learning and reporting endpoints.
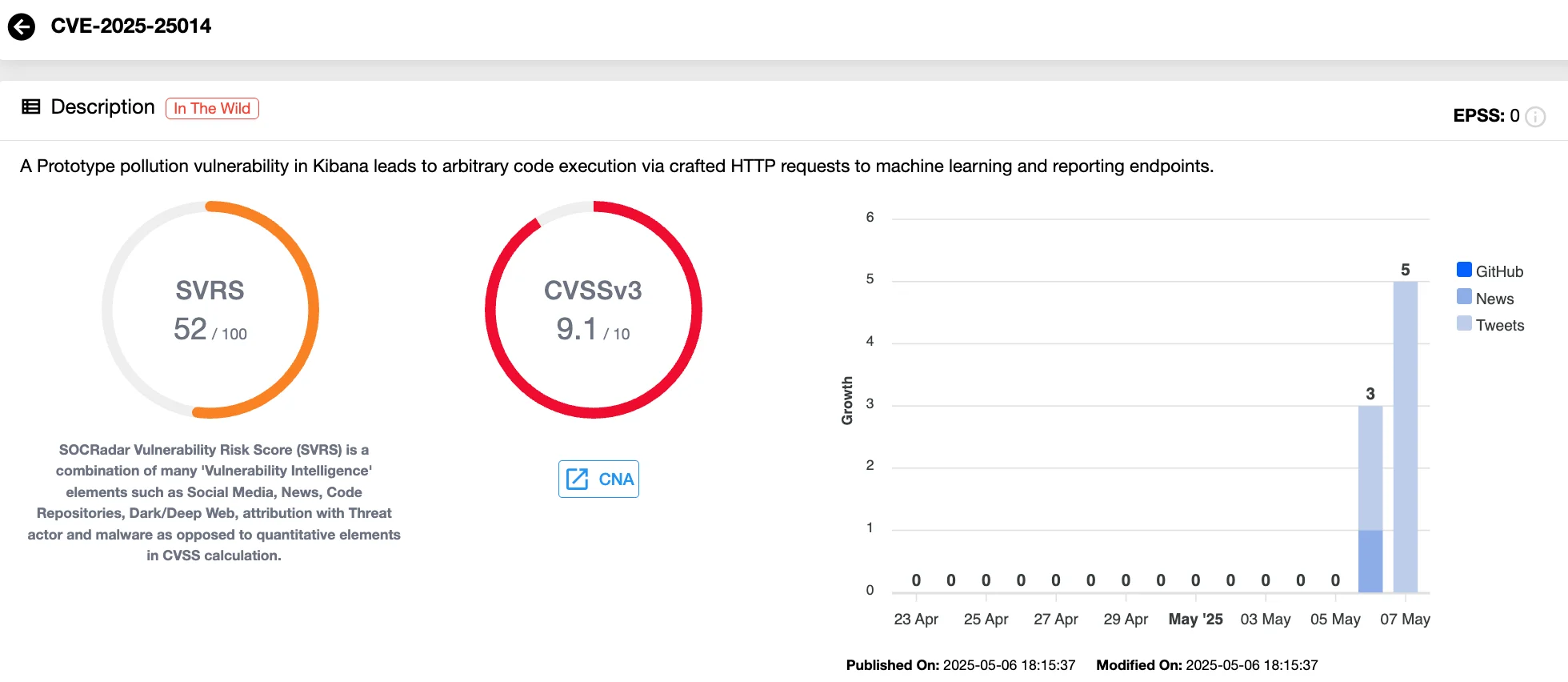
Vulnerability card of CVE-2025-25014 (SOCRadar Vulnerability Intelligence)
The issue affects Kibana versions 8.3.0 through 8.17.5, 8.18.0, and 9.0.0, and deployments are vulnerable if both Machine Learning and Reporting features are enabled, which is often the default in both self-hosted environments and Elastic Cloud configurations.
The most straightforward mitigation is to upgrade to a patched version:8.17.6, 8.18.1, or 9.0.1.
For teams unable to update right away, a workaround exists: disabling either the Machine Learning or Reporting feature will neutralize the vulnerability.
- To disable Machine Learning, add xpack.ml.enabled: false to your kibana.yml file.
- Self-hosted users can alternatively disable only anomaly detection with xpack.ml.ad.enabled: false.
- To disable Reporting, add xpack.reporting.enabled: false to the same configuration file.
For more information, refer to the official Kibana security advisory.
Track Company Vulnerabilities with SOCRadar’s Attack Surface Management (ASM) module
From internet-facing deployments to forgotten IoT devices, your attack surface is bigger than you think. SOCRadar Attack Surface Management (ASM) offers:
- Continuous discovery of all internet-facing assets across your organization—even those outside your known inventory
- Risk-based visibility, showing which exposures matter most
- Shadow IT detection, so you’re not blindsided by rogue deployments
- Automated alerts on misconfigurations, expired certificates, outdated software, and more
Whether you are dealing with fast-evolving platforms or legacy systems, SOCRadar ASM helps you monitor, manage, and harden your external presence before attackers exploit it.



































