April 2025 Android Update: Actively Exploited Kernel Bugs and Remote Privilege Escalation Threat
Google has just released its April 2025 Android security bulletin, addressing a broad spectrum of vulnerabilities across its mobile operating system. Among the 62 issues patched, two kernel-level vulnerabilities – CVE-2024-53150 and CVE-2024-53197 – are under active exploitation, drawing significant attention from both users and cybersecurity experts.
In addition to fixing kernel bugs, the update also tackles flaws in major third-party components from vendors like Arm, MediaTek, Qualcomm, and Imagination Technologies. Also notably, one of the critical patches for the System component, CVE-2025-26416, could allow remote privilege escalation with no user interaction, raising the stakes for unpatched devices.
Critical Kernel Vulnerabilities Actively Exploited (CVE-2024-53150 & CVE-2024-53197)
The Android kernel vulnerabilities CVE-2024-53150 and CVE-2024-53197 are among the most pressing issues in this month’s update.
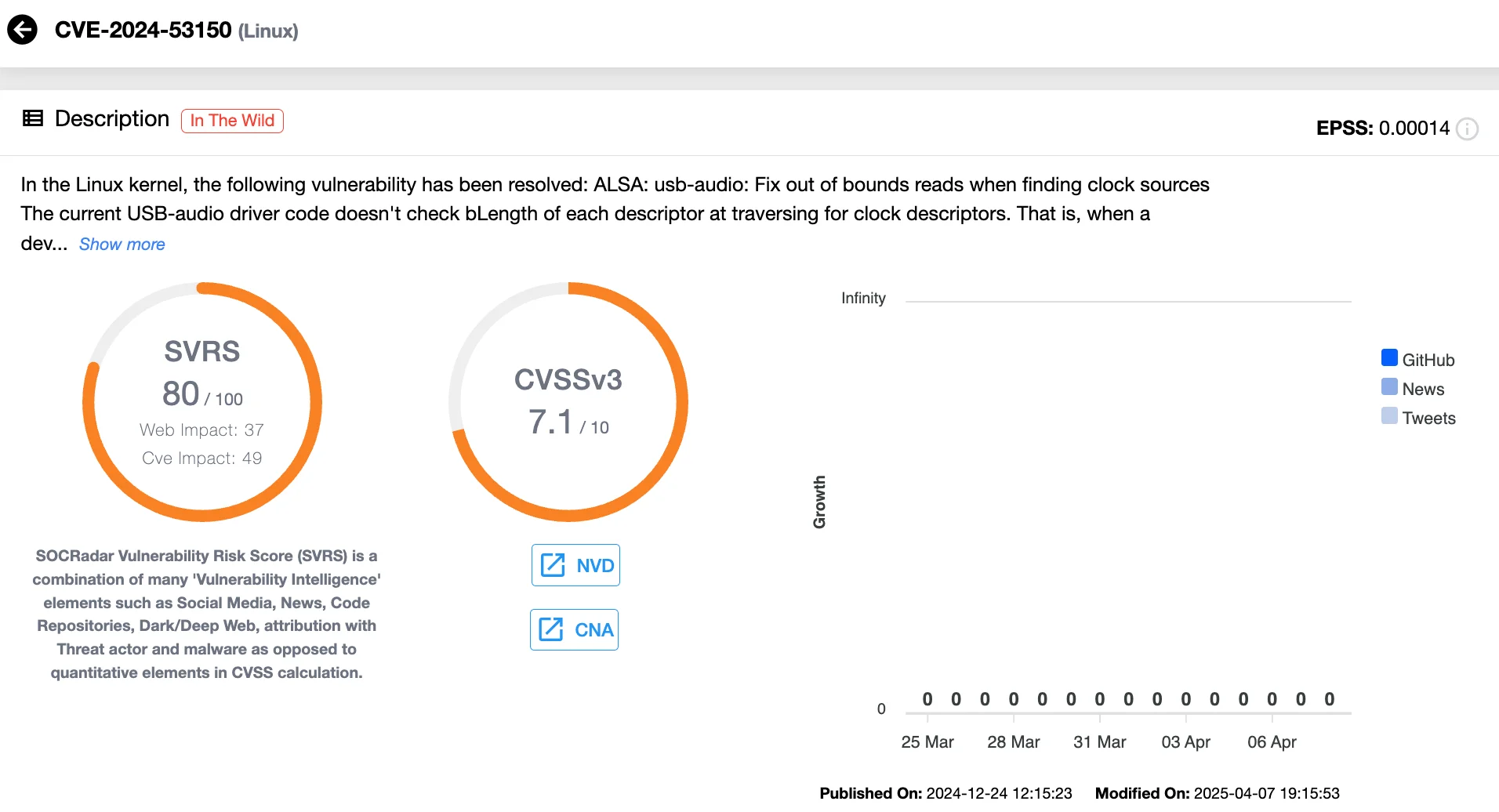
- CVE-2024-53150 (CVSS 7.1): This is an out-of-bounds read vulnerability located in the USB subsystem of the Linux kernel. Attackers exploiting this flaw could potentially extract sensitive data from affected devices.
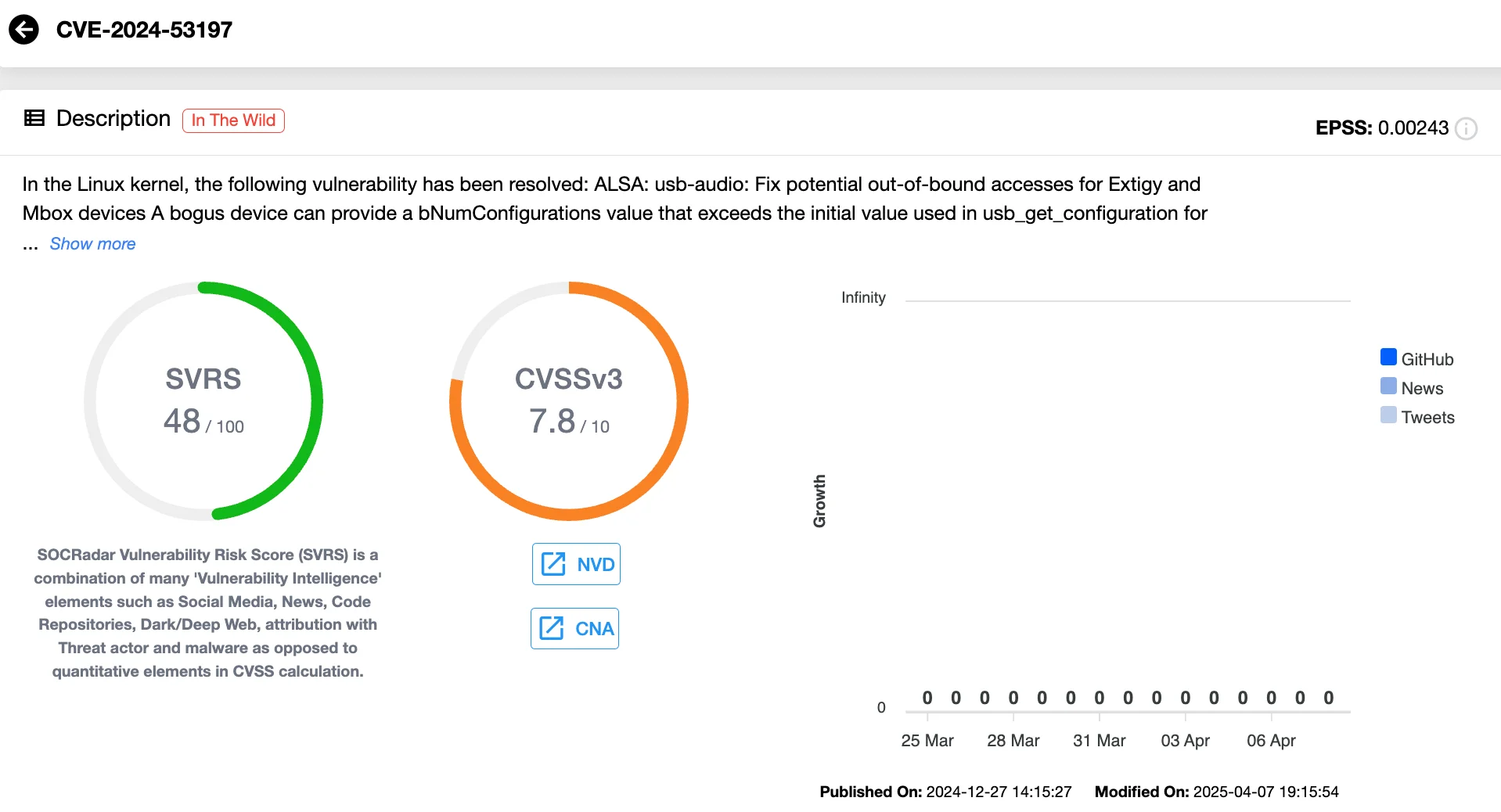
- CVE-2024-53197 (CVSS 7.8): A more severe privilege escalation issue, this flaw also resides in the USB subsystem and allows attackers to gain elevated access to the system.
According to Google’s security bulletin, these vulnerabilities impact the Linux kernel’s USB audio driver. What makes CVE-2024-53197 particularly noteworthy is its connection to a broader exploit chain previously uncovered by Amnesty International. In their February 2025 report, the organization revealed that Serbian intelligence services used a zero-day chain, including CVE-2024-53197, to compromise the device of a youth activist via a Cellebrite forensic tool.
The other components of this exploit chain, CVE-2024-53104 and CVE-2024-50302, were patched in earlier Android updates. As of April 2025, Google has now addressed all three vulnerabilities in the chain, effectively blocking this attack vector.
While the nature of attacks leveraging CVE-2024-53150 remains undisclosed, Google urges users to apply security updates as soon as their device manufacturers release them.
CVE-2025-26416: Critical System Vulnerability That Requires No User Action
According to the April 2025 Android security bulletin, the most critical flaw addressed in this update is CVE-2025-26416, residing in the Android System component. This flaw enables remote privilege escalation without requiring user interaction or additional execution privileges.
This type of vulnerability is particularly dangerous because it can be weaponized in remote attacks, potentially compromising large numbers of devices without users’ interaction, enabling a silent exploitation if the system is unpatched.
The criticality rating assumes that mitigation features are either disabled for testing or successfully bypassed, emphasizing the urgency of deploying the patch even for development environments.
How to Ensure Your Device Is Protected: Apply April 2025 Android Security Patches
Google has issued two security patch levels for April 2025:
- 2025-04-01 Patch Level: Covers core Android vulnerabilities.
- 2025-04-05 Patch Level: Includes all the earlier fixes plus patches for device-specific drivers and proprietary components.
Users with Pixel devices usually receive these patches immediately, while those with devices from other manufacturers may experience delays as vendors test and optimize the patches for their hardware. You can verify your device’s security patch level in the settings under System > Security.
For full details, refer to the official Android security bulletin.
Stay Ahead of Exploits With Real-Time Threat Intelligence
With cyber threats growing in both volume and sophistication, staying secure means acting quickly and intelligently. Google’s April 2025 Android update addresses a total of 62 vulnerabilities, including two actively exploited kernel flaws and a critical system bug that allows remote access without user interaction.
Beyond updates, proactive threat monitoring is essential. SOCRadar’s Vulnerability Intelligence module simplifies this by automating the tracking and analysis of new vulnerabilities. It delivers real-time alerts and in-depth insights, enabling organizations to evaluate risks and prioritize their response based on real-world threats rather than hypothetical scenarios.
Complementing this is SOCRadar’s Attack Surface Management (ASM) module, which provides continuous visibility into digital assets. By identifying vulnerabilities before attackers can exploit them, it enables your security team to take preventive action.