
B1txor20 Malware Exploiting Log4J Vulnerability
Since the Log4J vulnerability was discovered, some other malware showed up and exploited it. B1txor20 seems to take its place among the participants in this malware cluster.
Let’s take a closer look at B1txor20, which affects Linux systems and is thought to be still in development.
What is B1txor20?
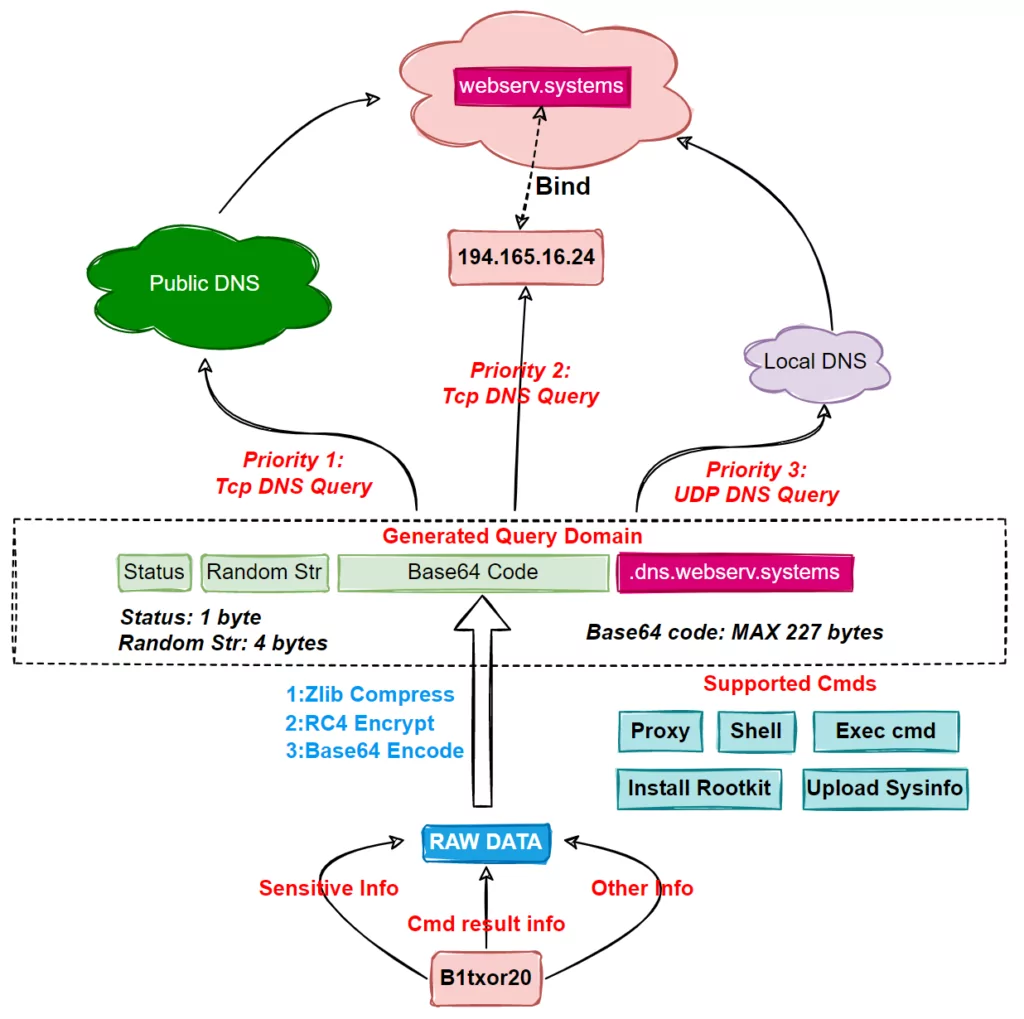
Discovered by Netlab, B1xtor20 is predicted to be from a new botnet family. Found that due to a DNS Tunnel warning triggered in the system, the malware opened a Linux backdoor to create C2 communication channels. It also has functions such as turning on Socket3 proxy, downloading and installing Rootkit remotely.
B1txor20 Generates Attack Vectors Using DNS Tunneling
Netlab’s article draws attention to the detail that four different B1xtor20 samples were detected. They all have more or less the same functions and work the same way. It establishes the C2 channel using DNS Tunnel, enables direct connection and relaying, and uses ZLIB compression, RC4 encryption, and BASE64 encoding to protect the traffic of the backdoor Trojan.
What are the IoCs?

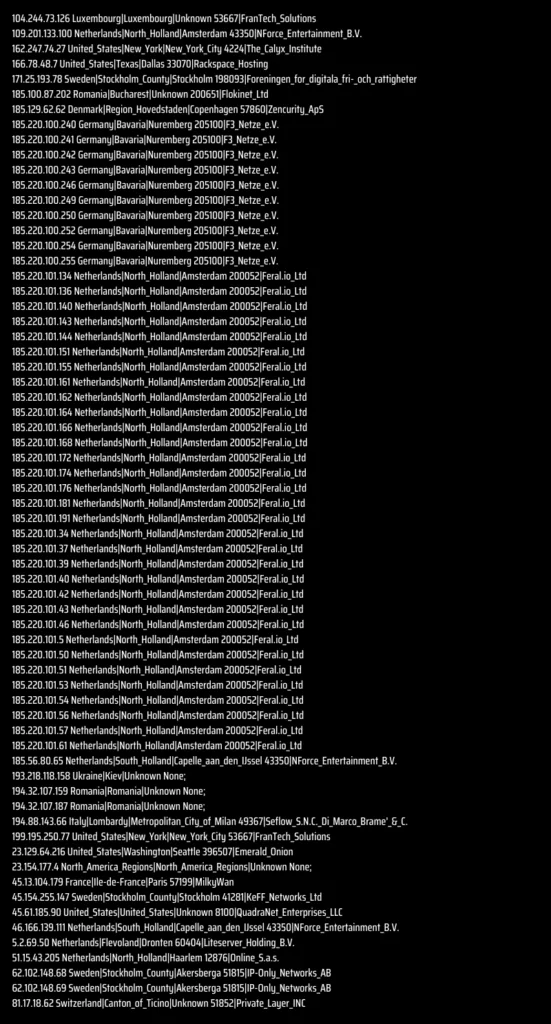
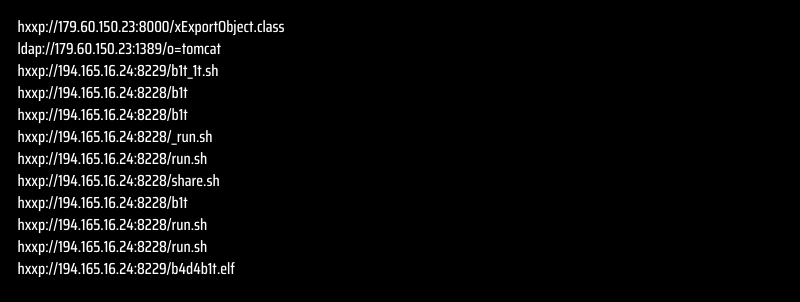
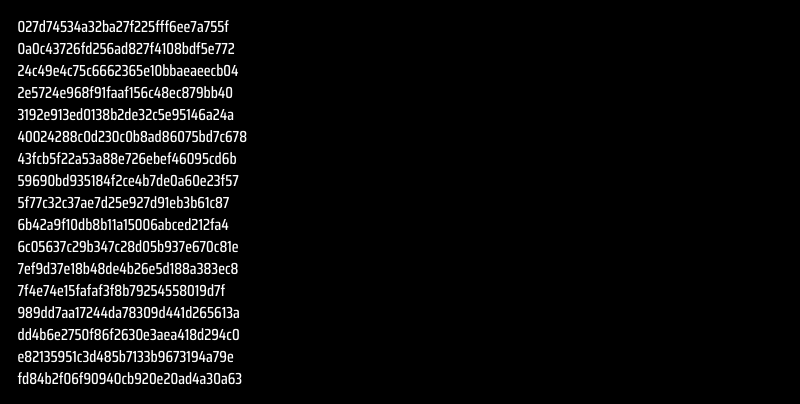
How to Protect Yourself from Malware with SOCRadar?
SOCRadar’s holistic understanding of threat intelligence offers many modules to protect you from malware. With the SOCRadar’s Threat Intelligence Feed, you can monitor IoCs, and with Malware Analysis, you can perform automatic or manual file analysis.
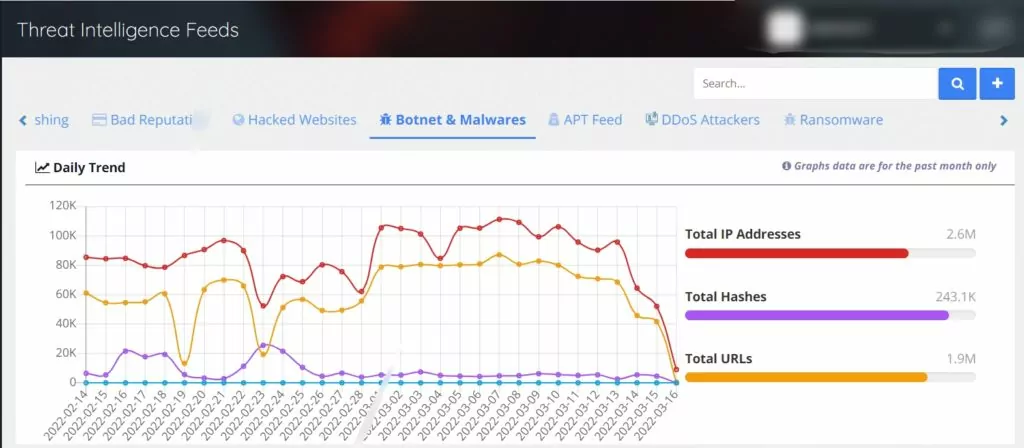
The Threat Intelligence Feed provides regular feeds about malware, botnets, APTs, and attacks like DDoS and ransomware.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access



































