Best of Both Worlds: CISA’s Known Exploited Vulnerabilities Integration with SOCRadar External Attack Surface Management
In today’s digital landscape, the threat of cyberattacks looms large, with threat actors constantly seeking to exploit vulnerabilities in software systems. To counter these threats, the Cybersecurity & Infrastructure Security Agency (CISA) plays a crucial role in safeguarding critical infrastructure and enhancing overall cybersecurity. One of the most essential components of CISA’s efforts lies in the Known Exploited Vulnerabilities (KEV) catalog. It is a comprehensive catalog of actively exploited software vulnerabilities.
The CISA KEV catalog is a valuable resource for government entities, businesses, and individuals concerned about cybersecurity. It provides a centralized repository of security flaws and weaknesses that attackers have exploited. Accessible online, the catalog organizes vulnerabilities by vendor, product, date, and description, accompanied by recommended actions to mitigate the risks. This lets users stay informed and apply necessary software updates and patches to protect their systems.
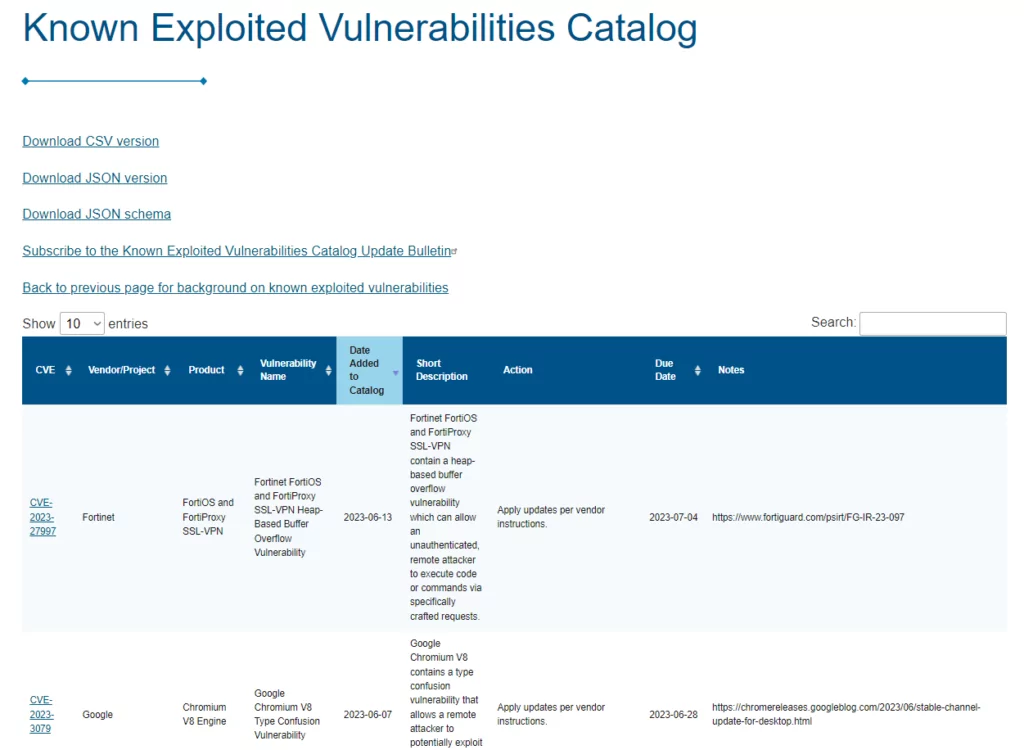
While the ideal scenario would involve software without exploitable flaws, complex code often presents security vulnerabilities. Threat actors, script kiddies to nation-state actors, continually probe for these weaknesses. The CISA KEV catalog remains a trusted resource for exploited software vulnerabilities. Its public availability enables organizations and businesses beyond the government sector to leverage this cybersecurity resource.
We will delve deeper into the capabilities and benefits of CISA’s Known Exploited Vulnerabilities catalog and explore how it integrates with SOCRadar’s External Attack Surface Management. Stay tuned to discover the potential synergies between these two in strengthening your cybersecurity defenses.
What does CISA KEV Provide for Security?
The catalog is designed to benefit the cybersecurity community and help organizations better manage vulnerabilities and keep pace with threat activity. CISA strongly recommends that all organizations review and monitor the KEV catalog and prioritize the remediation of listed vulnerabilities to reduce the likelihood of compromise by known threat actors.
While Federal Civilian Executive Branch (FCEB) agencies are required to remediate vulnerabilities in the KEV catalog under Binding Operational Directive (BOD) 22-01, CISA encourages all organizations, including state, local, tribal, and territorial governments, as well as private industry, to prioritize the remediation of vulnerabilities listed in the KEV catalog to strengthen their security and resilience posture.
The KEV catalog has three criteria for including vulnerabilities:
- Assigned CVE ID: The vulnerability must have an assigned Common Vulnerabilities and Exposures (CVE) ID, a unique identifier for a publicly known cybersecurity vulnerability. The CVE Program, sponsored by CISA and operated by The MITRE Corporation, assigns CVE IDs to vulnerabilities.
- Active Exploitation: The vulnerability must have reliable evidence of being actively exploited in the wild, including successful and attempted exploitation.
- Clear Remediation Guidance: The vulnerability must have an explicit remediation action, such as a vendor-provided update. Organizations should apply updates per vendor instructions or remove the impacted product from their networks if it is end-of-life or cannot be updated.
CISA emphasizes that organizations should prioritize the remediation of vulnerabilities listed in the KEV catalog to strengthen collective resilience across the cybersecurity community. They also encourage organizations and individuals to contact them if they have information about exploited vulnerabilities not currently listed in the KEV catalog.
Statistics Behind the CISA KEV Catalog?
The CISA KEV catalog was established in November 2021. Currently, there are 942 vulnerabilities listed in the catalog. We examined the data according to year, vendor, and vulnerability type. Let us see what lies behind the statistics of the CISA KEV.
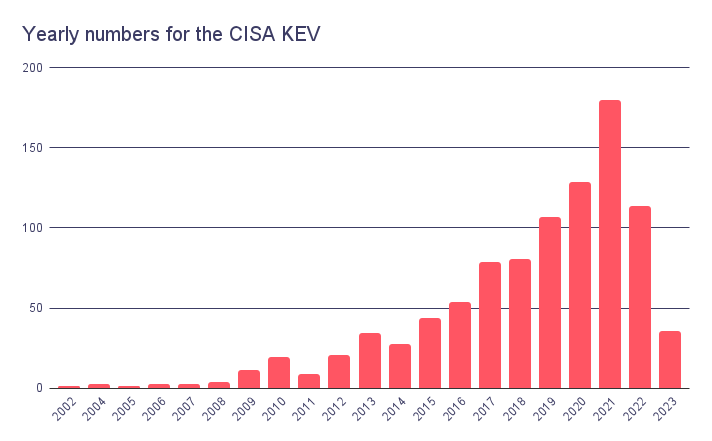
When we look at the above graphics, the vulnerabilities from 2020 onwards have the highest numbers in the catalog. This may suggest that newer vulnerabilities are exploited in more instances than others. The CISA incepted the KEV catalog in 2021. However, the presence of vulnerabilities from earlier years, including 2002, indicates that older vulnerabilities still have the potential to be actively exploited.
It is worth noting that threat actors often exploit known vulnerabilities due to the persistence of unpatched or unmitigated systems. Even if a vulnerability is several years old, it can still be leveraged by attackers if organizations have not taken appropriate steps to remediate it. This highlights the importance of addressing vulnerabilities comprehensively and not solely focusing on the most recent ones.
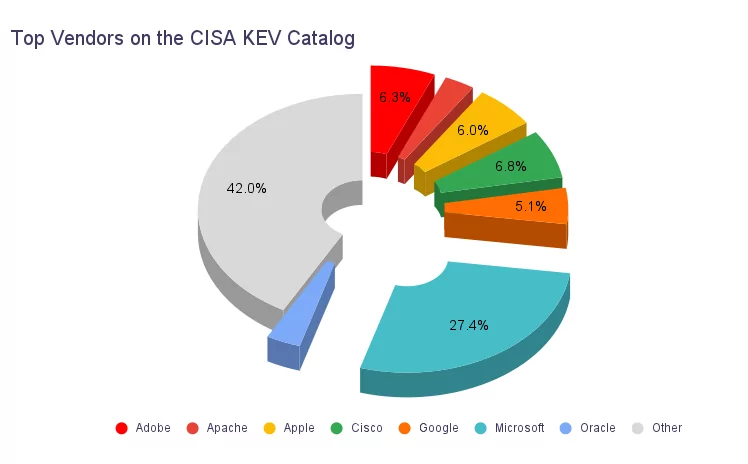
The graphic above regarding the top vendors and their respective percentages in the CISA KEV catalog reflects these vendors’ significant presence and impact in the cybersecurity landscape. With the highest percentage of 27.4%, Microsoft holds a dominant position in the software industry, providing operating systems, productivity software, and a range of other products. Due to the widespread adoption of Microsoft products, vulnerabilities affecting their software can have a significant impact on a large number of organizations and individuals.
Cisco, Adobe, Apple, Google, Oracle, and Apache also feature prominently in the catalog, demonstrating their significance in their respective domains. These vendors and Microsoft comprise more than half of the vulnerabilities in the CISA KEV catalog.
The variety of vendors in the CISA KEV catalog underscores the importance of the need for organizations to closely monitor and address vulnerabilities in every aspect of their systems.
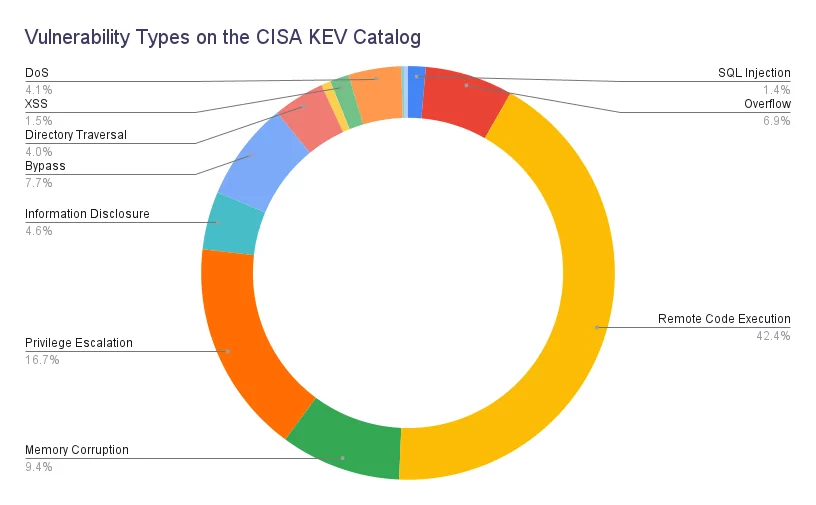
The data above regarding the top vulnerability types and percentages in the CISA KEV catalog highlights the significance of specific vulnerability types in cybersecurity. Among these, Remote Code Execution (RCE) stands out as the most prevalent vulnerability type, with a percentage of 42.4%.
Threat actors highly seek after RCE vulnerabilities because they allow unauthorized attackers to execute arbitrary code on a target system or network. This vulnerability grants attackers significant control and can lead to various malicious activities, such as taking over systems, spreading malware, or stealing sensitive data. The high count and percentage of RCE vulnerabilities in the catalog indicate that this vulnerability is actively exploited and poses a significant risk to organizations.
However, organizations should not overlook the other vulnerability types in the catalog. Each vulnerability type represents a unique risk and requires appropriate measures for mitigation. A comprehensive cybersecurity strategy should address a wide range of vulnerabilities, considering their potential impact and the likelihood of exploitation.
Privilege Escalation, with a percentage of 16.7%, is another major vulnerability type. Privilege Escalation vulnerabilities occur when an attacker gains higher access or privileges than the system’s intended design. By exploiting such vulnerabilities, attackers can bypass security controls and gain administrative privileges, allowing them to perform unauthorized actions and potentially compromise the integrity and confidentiality of systems and data.
Memory Corruption, Bypass, and Overflow vulnerabilities also feature prominently in the catalog, with percentages of 9.4%, 7.7%, and 6.9%, respectively. These vulnerabilities often involve manipulating the memory or bypassing security mechanisms, enabling attackers to execute malicious code, bypass security controls, or cause system crashes.
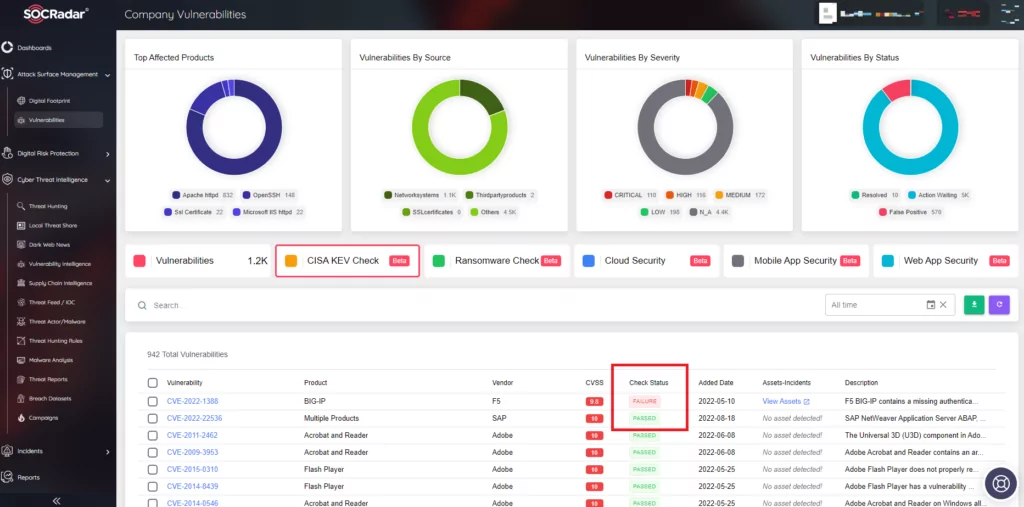
What Can SOCRadar Provide with CISA KEV Check Module?
The CISA KEV catalog contains a comprehensive list of known exploited vulnerabilities, and manually tracking this catalog can be challenging. This is where SOCRadar’s CISA KEV Check Module, integrated into its External Attack Surface Management solution, can provide significant value.
SOCRadar’s CISA KEV Check Module offers an automated and efficient way to check if your system is vulnerable to any CVEs listed in the CISA KEV catalog. By periodically scanning your system and comparing it against the catalog, SOCRadar can identify potential vulnerabilities that threat actors could target.
The module detects the presence of vulnerabilities and provides reports and notifications to ensure that organizations are aware of their exposure. These reports can highlight the specific vulnerabilities identified, allowing organizations to prioritize their remediation efforts and take necessary actions to address the vulnerabilities promptly.
Organizations can benefit from proactive vulnerability management by leveraging SOCRadar’s CISA KEV Check Module. Instead of relying solely on manual checks, which can be time-consuming and prone to oversight, the module automates the process. It ensures that organizations stay updated with the latest information from the CISA KEV catalog.
In addition to the CISA KEV Check module, in the event of multiple vulnerability detections, you can use SOCRadar Vulnerability Risk Score (SVRS) to sort and prioritize. SVRS is a unique scoring system developed by SOCRadar that considers a combination of qualitative elements from various sources, such as Social Media, News, Code Repositories, Dark/Deep Web, and attribution with Threat actors and malware. This differs from the traditional quantitative approach used in calculating the Common Vulnerability Scoring System (CVSS).
Overall, SOCRadar Cyber Threat Intelligence, with the integration of the CISA KEV catalog, can enhance an organization’s security posture by providing continuous monitoring, timely vulnerability detection, and actionable insights to mitigate potential risks associated with known exploited vulnerabilities.