
Cacti Patched CVE-2022-46169 Critical RCE Vulnerability
Cacti patched a critical security flaw to prevent arbitrary code execution on Cacti-running servers.
Cacti is an open-source, web-based network monitoring and graphing tool that offers users a framework for fault management and operational monitoring.
What is CVE-2022-46169?
Suppose a specific data source was chosen for any monitored device. In that case, a command injection vulnerability, CVE-2022-46169, with a CVSS score of 9.8, allows an unauthenticated user to execute any code on a server running Cacti.
The remote_agent.php file contains the flaw. This file can be accessed without requiring authentication. The function remote_client_authorized is used to check whether the client has permission.
The client’s IP address is retrieved by this function, which then resolves it to the corresponding hostname.
The existence of an entry in the poller table with a hostname that matches the resolved hostname is then confirmed. The function returns true, and the client is authorized if a match for such an entry was made.
An attacker can launch various actions after bypassing the remote_agent.php file’s authorization. Polldata is one of these actions:
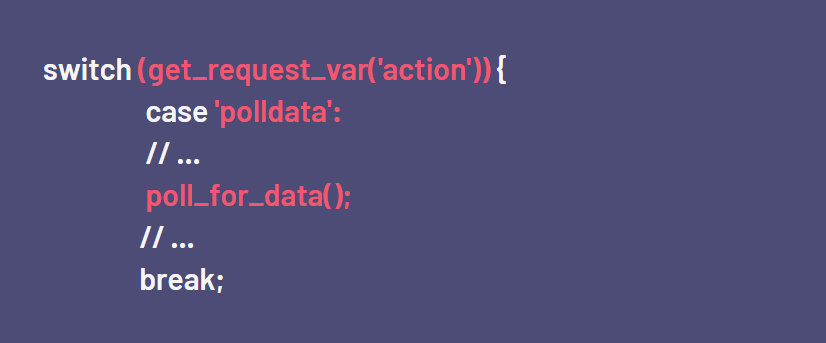
The called function poll_for_data retrieves a few request parameters, and the relating poller_item entries are then loaded from the database. Using the function proc_open, a PHP script is run when the action of a poller_item equals POLLER_ACTION_SCRIPT_PHP.
The function get_nfilter_request_var, which accepts arbitrary strings, retrieves the attacker-controlled parameter $poller_id.
A command injection vulnerability results from the later insertion of this variable into the string provided to proc_open. For instance, the id command is executed when poller_id=;id is specified.
When the action of the corresponding poller item is set to POLLER_ACTION_SCRIPT_PHP, the attacker needs to supply the host_id and local_data_id in order to access the vulnerable call.
The host_id and local_data_id can both be easily brute-forced. The only prerequisite is the presence of a poller_item with a POLLER_ACTION_SCRIPT_PHP action.
Given that some predefined templates add this action, this is likely on a production instance.
Impacted products by CVE-2022-46169
All installations of Cacti version 1.22.2 are affected by the vulnerability. Updating to the fixed versions 1.2.23 or 1.3.0 is advised for Cacti users.
Are there any exploits in the wild for CVE-2022-46169?
Although Cacti has not yet made a PoC announcement, a PoC code has been made available in this GitHub repository.
How to detect CVE-2022-46169?
To safeguard yourself from zero-day vulnerabilities and dangerous exploits, you must immediately become aware of critical vulnerabilities on your attack surface. To learn how to protect yourself, use the SOCRadar EASM Free Edition.
How to mitigate CVE-2022-46169?
You can look at Cacti’s advisory to learn how to avoid exploiting the vulnerability.
How Can SOCRadar Help With Critical Vulnerabilities?
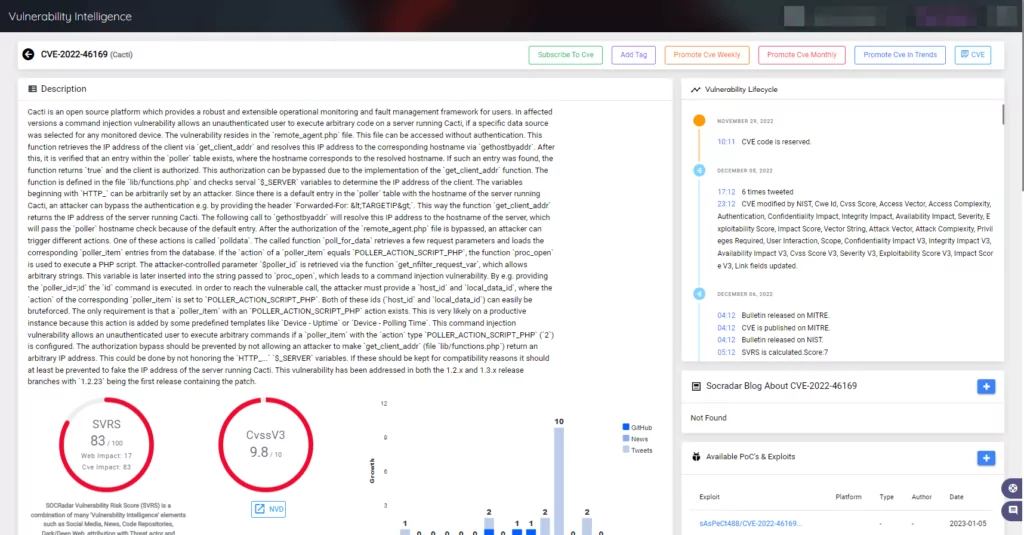
To help speed up the assessment and verification procedures, use SOCRadar to obtain actionable insights and context on potentially vulnerable technologies.
On the SOCRadar Platform’s Vulnerability Intelligence module, you can access a wide range of information, including available PoCs & exploits, Sigma & Yara rules, news about the vulnerability, GitHub Repositories, and many more.




































